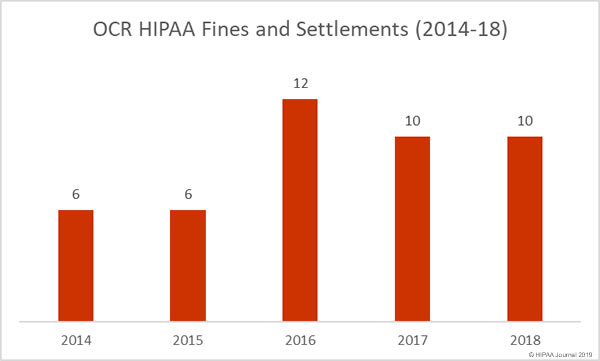
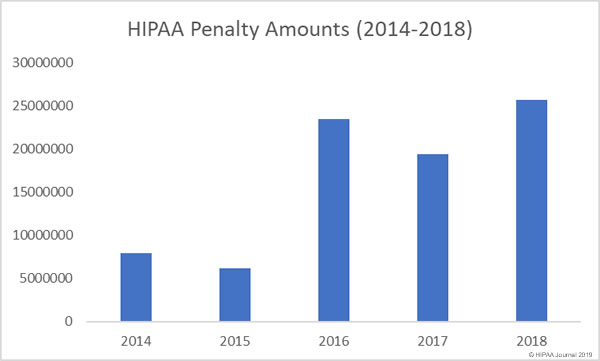
An investigation into a healthcare data breach has shown how the failure to implement basic cybersecurity measures leaves the door wide open to hackers. Healthcare organizations can invest in the latest cybersecurity technology but failing to adopt standard cybersecurity best practices and assess and maintain defenses can easily lead to an incredibly costly data breach.
The breach in question occurred not in the United States, but Singapore. However, the findings of the investigation have relevance in the United States where many healthcare data breaches have been experienced due to similar cybersecurity failures.
In June 2018, hackers attacked Singapore’s largest health network, SingHealth. The records of 1.5 million people were stolen, including the health records of the country’s Prime Minister, Lee Hsien Loong. To put the scale of the breach into perspective, Singapore has a population of 5.6 million.
Following the breach, the Committee of Inquiry (COI) was formed to conduct a detailed investigation, the results of which were made public this week.
While it is not possible to prevent every data breach – determined and well-resourced hackers could, given enough time, break through most organizations’ defenses – adhering to cybersecurity best practices and implementing appropriate cybersecurity solutions can reduce the risk of a breach to a reasonable and acceptable level. In the case of SingHealth, that did not happen.
The cyberattack was believed to have been conducted by nation-state sponsored hacking group, but the attack could have been performed by far less skilled hackers.
The investigation revealed that had SingHealth applied a patch to correct a single vulnerability, the attack could have been thwarted, although that was just one of many failures detailed in a 453-page report of the investigation.
SingHealth relied solely on a third-party IT management company, Integrated Health Information Systems (IHiS), to assess and manage cyber risk. Numerous failures were detected at the firm.
While the attack was somewhat stealthy, the signs of a breach were identified by the IT management company, yet action was not taken to stop the hackers from achieving their main aim – to obtain the health information and prescription details of the Prime Minister.
A middle manager was misguided about what constituted a reportable cybersecurity incident and failed to report network intrusions out of fear that it would result in additional pressure on his team. A key member of staff at the firm displayed “an alarming lack of concern” about the fact that systems had apparently been breached. As a result of this lack of concern and the firm’s failure to take prompt action over the breach, the hackers had time to exfiltrate patient data. Had the incident been escalated to the Singapore’s Cyber Security Agency, the theft of data could have been prevented.
The investigation revealed staff at iHiS lacked adequate levels of cybersecurity awareness and had not been sufficiently trained to recognize an attack in progress and respond effectively.
At SingHealth, cybersecurity was viewed as an IT management issue rather than a risk management issue and too much reliance was placed on the IT management firm to ensure that its systems were protected.
There was a failure to assess all cybersecurity protections and procedures and ensure they were sufficient to prevent and respond to APT attacks. Routine checks were not performed to assess vulnerabilities and penetration tests had not been conducted.
Two-factor authentication had not been implemented, and there was a lack of control over administrative accounts. Password policies enforcing the use of strong passwords had not been implemented on domain and local accounts. IT security risk assessments were not sufficiently thorough and were not conducted with sufficient regularity. Insufficient safeguards had been implemented to protect the EHR database and incident response procedures were not effective.
In total, 16 recommendations were made by the investigators to improve security, seven of which were rated critical.
The critical recommendations are:
- An enhanced security structure and readiness must be adopted by IHiS and Public Health Institutions
- The cyber stack must be reviewed to assess if it is adequate to defend and respond to advanced threats
- Staff awareness on cybersecurity must be improved to enhance capacity to prevent, detect, and respond to security incidents
- Enhanced security checks must be performed, especially on Critical Information Infrastructure (CII) systems
- Privileged administrator accounts must be subject to tighter control and greater monitoring
- Incident response processes must be improved for more effective response to cyber attacks
- Partnerships between industry and government to achieve a higher level of collective security
The post SingHealth Breach Investigation Reveals Catalogue of Cybersecurity Failures appeared first on HIPAA Journal.