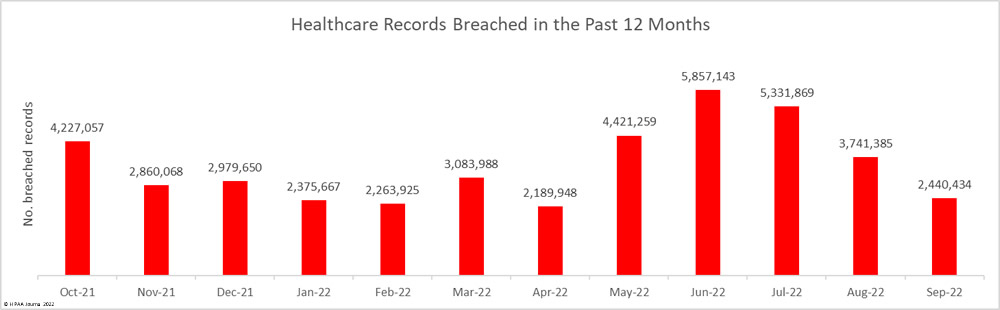
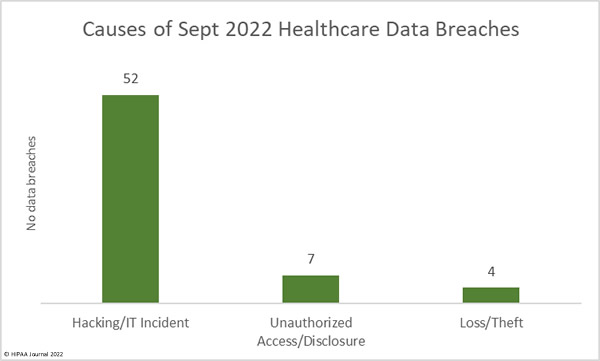
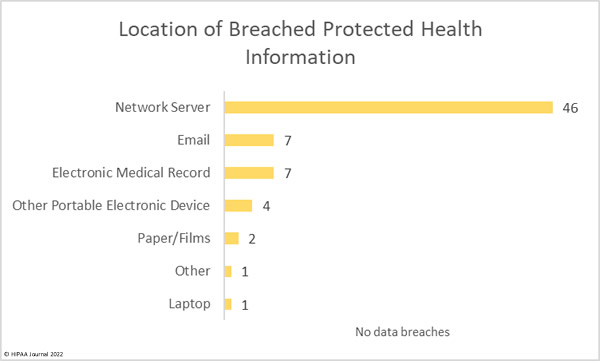
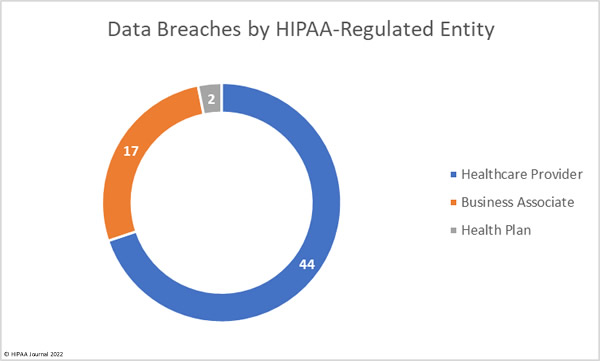
The healthcare industry is an attractive target for cybercriminals and data thieves. Healthcare organizations store vast amounts of sensitive data that can be easily monetized. Large health systems are often targeted due to the high ransoms that can be demanded, as the recent attack on CommonSpirit Health demonstrated; however, attacks are conducted on healthcare organizations of all sizes. The ransomware remediation firm, Coveware, reported earlier this year that 82% of ransomware attacks in 2021 occurred at firms with fewer than 1,000 employees.
Healthcare providers are heavily reliant on access to data, which makes them a prime target for ransomware gangs. When data is rendered unavailable, that naturally has an impact on business operations and causes considerable financial losses, and threatens patient safety. Without access to EHRs and medical histories, healthcare organizations are left with little alternative but to cancel appointments. Fast recovery of data is essential, which is why many healthcare organizations choose to pay the ransom to try to accelerate the data recovery process.
Ransomware gangs encrypt data and also seek to encrypt or delete backups to ensure that important data cannot be recovered without paying the ransom. In 2020, the University of California, San Francisco (UCSF) was targeted by the NetWalker ransomware gang – a ransomware-as-a-service (RaaS) operation that has no qualms about conducting attacks on medical and healthcare targets.
In the attack, the gang succeeded in encrypting data on the servers used by its School of Medicine. UCSF had data protection measures in place, but they proved to be inadequate and did not allow data to be recovered. UCSF was left with little alternative other than paying a $1.14 million ransom for the keys to recover their data.
In order to be able to recover quickly from a ransomware attack, healthcare organizations need to be proactive and develop, implement and test a security incident response plan. The HHS’ Office for Civil Rights recently communicated the importance of security incident planning and an effective data backup strategy in its October 2022 Cybersecurity Newsletter.
Only One in Five Organizations Follow the 3-2-1 Rule for Data Backups
Following a ransomware attack, a decision will need to be made about whether to pay the ransom. There is no guarantee that paying the ransom will see stolen data deleted and not further disclosed, and in 2021, only 8% of companies were able to recover all of their data after paying the ransom. The decision whether or not to pay the ransom will be based on several factors, but what limits options more than anything else is not having access to backups.
Healthcare organizations must ensure backups are made of all data to ensure that in the event of any disaster, a viable backup is available that allows data to be restored. However, many organizations fail to follow best practices for data backups and only discover after an attack that their backup procedures are insufficient. Backups naturally need to be made and stored on systems that are not accessible from the systems on which the data resides, as if that system is compromised, the attackers will also have access to the backups. Many healthcare organizations rely on the cloud for storing backup data securely offsite. Using the cloud for storing backups has its advantages; however, it is important not to rely totally on cloud storage. Backing up data in one place leaves organizations vulnerable to data breaches and data loss, and ransomware gangs often target cloud storage services.
When it comes to backing up data, the best practice is to follow the 3-2-1 rule, which involves creating a minimum of three backups of data, in at least 2 different locations, with one of those copies stored securely off-site. The three backups consist of the primary backup and at least two copies. Despite this being the best practice, a recent survey conducted by Apricorn for its 2022 Global IT Security Report has revealed many organizations are failing to follow this best practice. The survey revealed fewer than one in five organizations were following the 3-2-1 rule.
The survey revealed only 18% of organizations were following the 3-2-1 rule for backups, with only one in three organizations backup data in the cloud and on an encrypted hardware storage device. While 72% of respondents said they back up data daily, only 18% said they back up data in real time. Even if backups can be used to restore data, up to a day’s worth of that data will be lost without real-time backups.
“Currently less than one in five organizations follow the 3-2-1 rule. Yet it is vital that online and offline storage go hand in hand. Of course, the benefits of creating backups are significantly diminished if you can’t leverage them effectively in critical moments,” said Kurt Markley, U.S. Managing Director at Apricorn. “A playbook should therefore be developed that outlines the process of performing data backup – who is involved, which programs and products need to be used, and the location of the backups. It should also include the procedure for testing, reviewing, and updating the process. Should any staff be absent in the event of an attack, or critical cogs in the recovery chain leave the company, the firm will still retain a step-by-step guide enabling them to respond effectively”
The survey also explored how the move to remote working has affected security. According to the survey, 80% of surveyed organizations said they developed remote working policies in response to the pandemic, with four out of five organizations having now revised the security policies and practices that were hastily put in place to quickly accommodate the move to remote working.
56% of respondents said they have reinvested in reinforcing education about security practices, yet worryingly, out of the IT professionals surveyed, 72% said their employees fail to view themselves as a target that cybercriminals would try to exploit to gain access to company data. The most common reasons given were a perception that they were either too small a target or that they were adequately protected.
The post Only One in Five Organizations Follow the 3-2-1 Rule for Data Backups appeared first on HIPAA Journal.