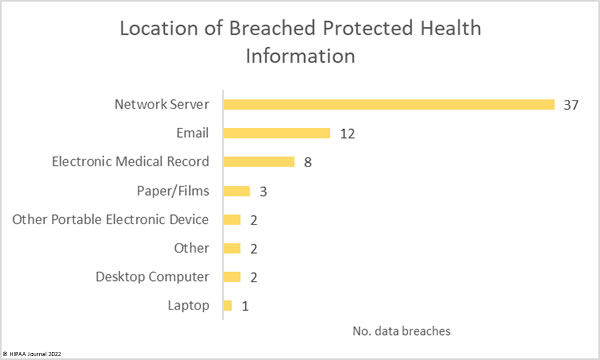
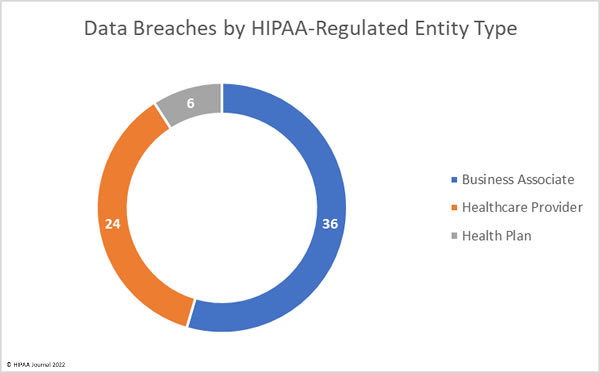
The Government Accountability Office (GAO) recently conducted a review of Medicare telehealth services provided during the COVID-19 pandemic, when a waiver was in place that greatly expanded access to telehealth and virtual visits. The review covered the utilization of telehealth services, how the CMS identified and monitored risks under the Medicare waivers, and how the HHS’ Office for Civil Rights (OCR) changed its enforcement of HIPAA compliance with respect to telehealth during the COVID-19 public health emergency.
Under normal circumstances, telehealth services are covered by Medicare, but only in limited circumstances, such as when patients live in rural locations and do not have easy access to healthcare services. The increased need for telehealth due to the COVID-19 pandemic saw waivers issued by the HHS’ Centers for Medicare and Medicaid Services (CMS) that expanded Medicare telehealth services and allowed virtual visits to be provided in a much broader range of circumstances. A notice of enforcement discretion was also issued by OCR stating enforcement actions would not be taken against healthcare providers over the good faith provision of telehealth services, even if non-public-facing technology was used that would not normally have been compliant with the HIPAA Rules.
Between April and December 2019, 5 million Medicare telehealth visits were conducted. During the same period in 2020, the number increased to 53 million. According to the GAO report, the CMS has not been able to comprehensively assess the quality of care provided to patients through telehealth visits, and there is concern that patients may not have been made fully aware of the privacy risks involved, which could have resulted in their sensitive health information being overheard or inappropriately disclosed.
OCR encouraged covered providers to inform patients about the potential privacy and security risks associated with telehealth services; however, OCR did not advise providers of the specific language to use when explaining those risks nor give direction to help providers explain the risks. “Providing such information to providers could help ensure that patients understand potential effects on their protected health information in light of the privacy and security risks associated with telehealth technology,” explained GAO in the report.
Under normal circumstances, a healthcare provider and a vendor of a communications platform must have a business associate agreement in place; however, that requirement was not enforced during the public health emergency. That could potentially increase the risk of a patient’s PHI being disclosed without their knowledge and patients may not have been aware that such a change had occurred under OCR’s telehealth policy, and that their privacy was not protected.
GAO explained in the report that also noted in the report that complaints had been filed about potential HIPAA Privacy and Security Rule violations with respect to telehealth visits. 5 separate complaints were filed by patients over the use of technology for telehealth visits that was not compliant with the HIPAA Security Rule, and 37 privacy complaints were filed over matters such as the presence of third parties during appointments and instances where providers shared PHI without obtaining patient consent.
GAO has recommended that OCR provide additional education and outreach to help providers explain the privacy and security risks to patients associated with telehealth to make sure that those risks are fully understood. GAO emphasized the importance of providing patients with easy-to-understand information to allow them to carefully weigh the risks to their personal information, and improved communication about telehealth vendors’ privacy policies and HIPAA compliance to allow patients to better understand the privacy risks.
OCR concurred with the recommendations and said it will be providing additional guidance for healthcare providers on the provision of telehealth services, including help on how best to explain the privacy and security risks to patients in plain language.
GAO found there was incomplete data on audio-only and video telehealth visits conducted between April and December 2020. This was determined to be due to the lack of accurate billing codes used by insurance companies to track telehealth and virtual appointments and to identify when telehealth services were delivered to beneficiaries in their homes.
GAO recommended the CMS develop an additional billing modifier to allow the accurate tracking of audio-only office visits, to require providers to use service codes that indicate when Medicare telehealth services are delivered to beneficiaries in their homes, and for the Administrator of the CMS to comprehensively assess the quality of Medicare services, including audio-only services, delivered using telehealth during the public health emergency.
The post GAO: HHS Should Strengthen Oversight of Medicare Telehealth and Help Providers Communicate Privacy Risks appeared first on HIPAA Journal.