Losses to phishing attacks increased by 76% last year, with almost one-third of companies losing money to successful phishing attacks according to Proofpoint’s recently published 2023 State of the Phish Report. In 2022, more than 4 out of 5 surveyed organizations experienced at least one successful phishing attack, with more than half of those organizations experiencing at least three successful phishing attacks. The data for the report came from a global survey of 7,500 working adults, 1,050 IT security professionals, and the results of more than 135 million simulated phishing emails over 12 months.
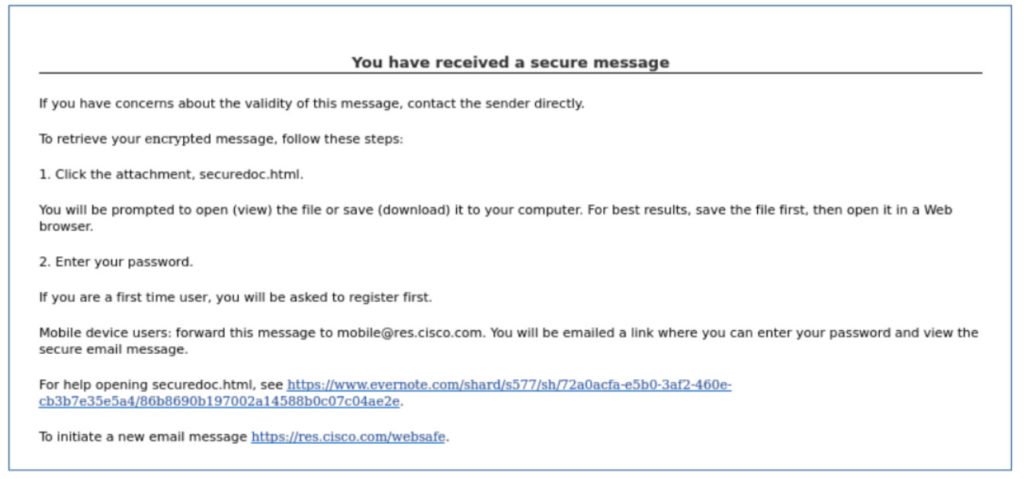
Phishing is one of the most commonly used initial access vectors in cyberattacks, commonly leading to costly account compromises, data breaches, and ransomware attacks. Phishing is usually associated with email, but 2022 saw a marked increase in telephone-oriented attack delivery (TOAD). These attacks typically involve emails urging the recipient to call a customer service hotline to resolve a security or account issue. Call centers are established – often in India – and the operators convince victims to install remote access software, install malware, or instruct them to transfer money. Proofpoint says during peak times, more than 6000,000 TOAD messages were sent per day last year, with message volume averaging between 300,000 and 400,000 per day. TOAD attacks have increased steadily since 2021 due to the success of this technique. Since the initial contact occurs via email with no hyperlinks or attachments, email security solutions fail to quarantine or reject the messages ensuring a high delivery rate.
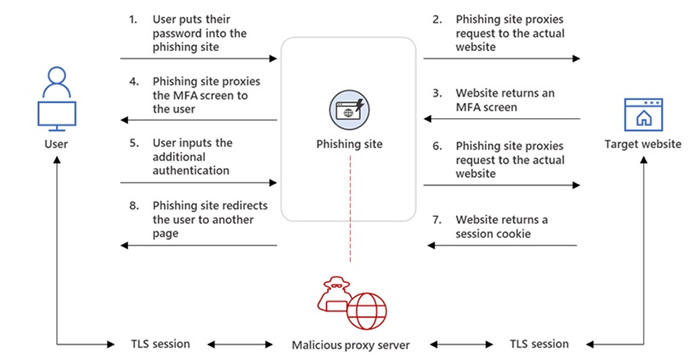
In response to the move by Microsoft to disable macros in Internet-delivered Office documents and increasing adoption of multi-factor authentication, cyber threat actors have had to get more creative and develop new techniques for malware delivery and phishing methods capable of bypassing MFA are being adopted at scale. Proofpoint reports an increase in MFA bypass by phishing-as-a-service providers, who now offer that capability in their off-the-shelf phishing kits. Rather than directing users to phishing websites, these adversary-in-the-middle attacks allow threat actors to present legitimate websites to victims and capture credentials and MFA codes/session cookies, allowing access to accounts that are protected by MFA. These attacks were conducted at scale in 2022 and pose a significant threat to organizations of all sizes.
The phishing simulation data highlights continued problems in human defenses and a lack of security awareness among employees. Teaching security best practices and training employees how to recognize threats such as phishing can significantly improve security posture and while more organizations are investing in training for employees, only 55% of organizations have a security awareness program for all employees and despite the benefits of conducting phishing simulations, only 35% of organizations use phishing simulations as part of the training process.
Awareness of cyber threats is improving but there is still a long way to go. For instance, 44% of people think emails are safe if they contain familiar branding, and even basic cybersecurity concepts are still poorly understood. One-third of working adults were unable to define malware, phishing, and ransomware, and there has been little change in understanding since 2021. One-third of people took risky actions such as clicking links in emails, opening attachments, or downloading malware, and alarmingly, 63% of the adults surveyed thought links in emails always direct them to the matching website or brand. Poor password practices also persist. 28% of users admit to reusing passwords for multiple work-related accounts, 26% save work passwords in their browsers, 16% manually rotate 1-4 passwords, and only 18% of respondents use a password manager.
The majority of surveyed organizations said they have implemented at least some form of security awareness training, but many are struggling to make those programs effective. 27% of respondents said failure rates to phishing emails have largely remained unchanged, even after conducting security awareness training. That suggests more time and effort needs to be put into training, especially as 80% of organizations admitted to providing only 2 hours or less of training each year. The full findings and recommendations are available in the Proofpoint report.
The post Losses to Phishing Attacks Increased by 76% in 2022 appeared first on HIPAA Journal.