The eagerly anticipated Verizon 2023 Data Breach Investigations Report (DBIR) has been published – An annual report that provides insights into the current threat landscape and data breach trends. This year, the report is based on an analysis of 16,312 security incidents, where the integrity, confidentiality, or availability of an information asset was compromised, and 5,199 data breaches, where there was a confirmed disclosure of sensitive data to an unauthorized third party. All incidents included in the report occurred between November 1, 2021, and October 31, 2022.
Last year, the report indicated the human element was involved in 82% of all breaches, down from 85% in 2021. That downward trend has continued with the human element involved in 74% of breaches in 2022. These include mistakes by employees such as misconfigurations and responses to pretexting attacks, as well as deliberate actions by malicious insiders. In around half of all incidents (49%), initial access to victims’ networks was gained through stolen credentials, with phishing the next most common method, accounting for 12% of breaches, and the exploitation of vulnerabilities, which accounted for 5% of breaches. The Log4j vulnerability was the most cited exploited vulnerability and was stated as the exploited vulnerability in 90% of exploit incidents, although only 20.6% of incidents stated the vulnerability that was exploited in the attack.
Social Engineering Attacks Continue to Increase
This year’s report highlights a continuing upward trend in pretexting incidents, which are a type of social engineering attack where the victim is manipulated into divulging sensitive information. These attacks typically involve impersonation and include business email compromise attacks, which almost doubled in a year and now account for more than 50% of social engineering incidents, overtaking phishing for the first time, although phishing remains the most common social engineering method in confirmed data breaches. Losses to BEC attacks have been steadily increasing, jumping from a little over $30,000 in 2018 to a median of $50,000 in 2022. 98% of social engineering attacks involved email as the initial vector, with the remainder involving telephone-based incidents (vishing) and SMS and instant messaging (smishing).
One of the problems highlighted in the report is the lack of protection against social engineering attacks, especially the accounts of senior leadership. These individuals are often targeted as they have the most valuable accounts with extensive access to systems and data, as the accounts of senior leadership are often excepted from standard security controls. Detecting these attacks can be difficult and blocking them requires a combination of measures including email security solutions, end-user training, and multifactor authentication, with greater protections implemented for the most valuable accounts with the highest levels of privileges.
Ransomware Attacks Remain Steady
Ransomware attacks continue to be conducted in high numbers but the number of attacks has remained steady, accounting for 24% of incidents and 15.5% of data breaches – a slight increase in ransomware incidents from last year and a slight decrease in ransomware-related data breaches. Verizon reports that ransomware is used in 62% of cyberattacks by organized crime actors and 59% of financially motivated incidents. Email, desktop-sharing software, and web applications were the most common attack vectors in ransomware attacks.
Figures from the FBI indicate 10% of ransomware attacks covered in the 2021 DBIR involved financial losses, with a median loss of $11,500. This year, only 7% of attacks involved financial losses, but the median loss has doubled to $26,000, with the maximum loss jumping from $1.2 million to $2.25 million. The overall cost of remediating ransomware attacks continues to increase despite a continuing fall in median ransom payments.
Other Causes of Security Incidents and Data Breaches
While the majority of attacks were hacking incidents, insider breaches continue to occur. 602 insider incidents were included in the report, out of which 512 involved confirmed data disclosures. The most common cause of these incidents was misdeliveries, which accounted for 43% of insider incidents, followed by misconfigurations (23%) and publishing errors (21%). Social engineering, phishing, and ransomware attacks dominate the headlines, but by far the most common type of attack is denial-of-service, which was behind 6,248 of the 16,312 security incidents. While these attacks do not tend to carry the same costs as data breaches, they can still cause considerable disruption to business operations as they prevent access to the Internet and business-critical systems.
2,091 incidents involved lost and stolen assets, with loss incidents accounting for the vast majority of these incidents. typically lost mobile phones, laptops, and printed documents. These incidents were numerous but often did not figure in the breach data, as the data on lost devices was not confirmed as being breached, only being at risk. These incidents have remained at a similar level to last year, accounting for around 10% of all data breaches.
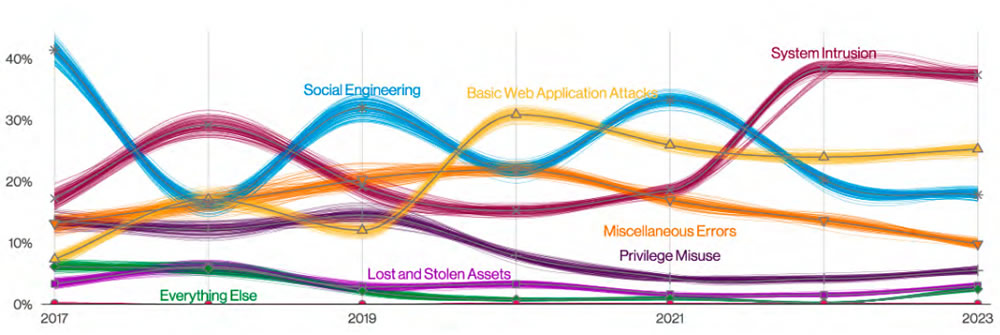
Patterns in Data Breaches. Source: 2023 Verizon Data Breach Investigations Report.
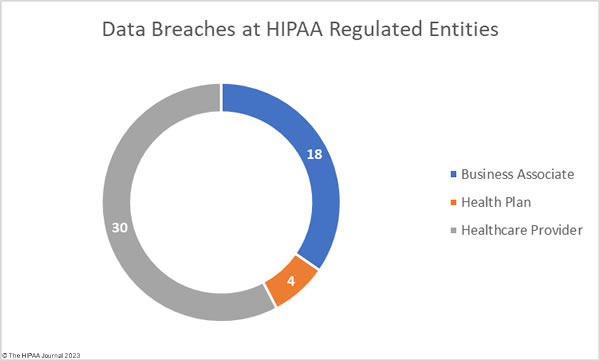
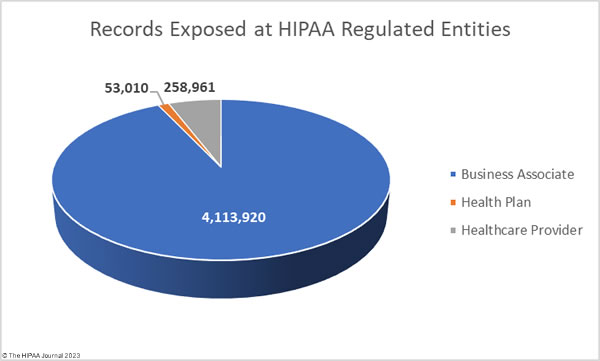
Causes of Healthcare Attacks and Data Breaches
Healthcare was represented in 525 incidents and 436 of those incidents involved confirmed data disclosures. The most common cause of healthcare data breaches was basic web application attacks (164), miscellaneous errors (153), system intrusions (121), privilege misuse (57), social engineering (65), and lost/stolen assets (18). As Verizon points out, many healthcare data breach notification letters state the breach was the result of a highly sophisticated cyberattack; however, basic web application attacks were the most common, which typically involve brute-forcing weak passwords and credential stuffing, which are certainly not complex.
Many of the incidents in healthcare were due to mistakes by employees. Misdelivery – the sending emails or mailing letters to incorrect individuals – was the second biggest cause of data breaches. Privilege misuse, which includes snooping by employees, has been decreasing but is still more prevalent than in many other industries. Protecting against these attacks is difficult, so the focus must be on fast detection to limit the potential for harm, and that means monitoring logs for unusual data access patterns and automating that process as far as possible.
The post Verizon 2023 DBIR: Social Engineering Attacks Increase; Ransomware Plateaus appeared first on HIPAA Journal.