For the first time since 2015, there was a year-over-year decline in the number of data breaches reported to the Department of Health and Human Services’ Office for Civil Rights (OCR), albeit only by 1.13% with 707 data breaches of 500 or more records reported. Even with that reduction, 2022 still ranked as the second-worst-ever year in terms of the number of reported breaches.
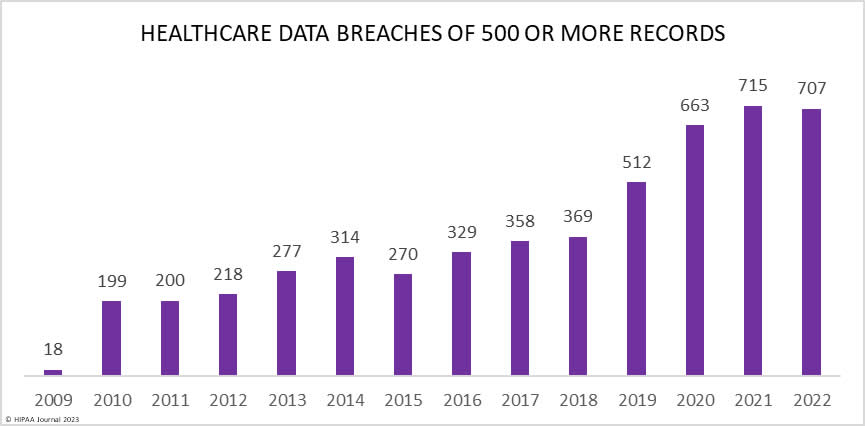
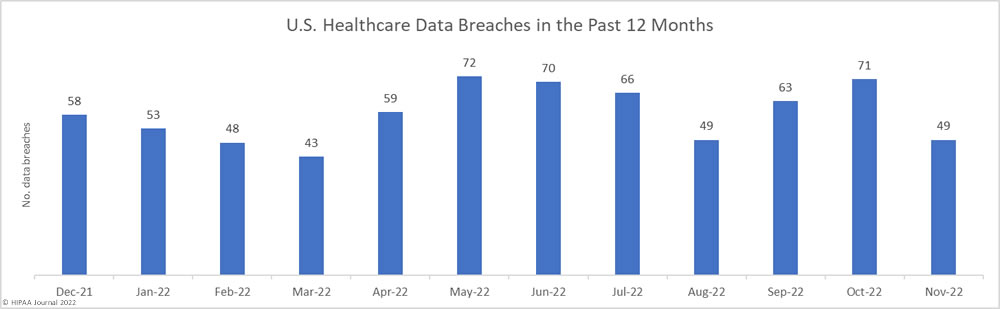
As the year drew to an end, data breach numbers started to decline from a high of 75 data breaches in October. Time will tell whether this trend will continue in 2023, although the lull in data breaches appears to have continued so far this year with an atypically low number of breaches currently showing on the OCR data breach portal this month.
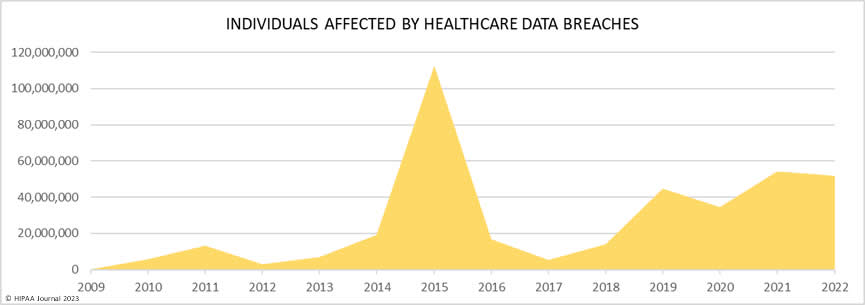
In addition to the slight reduction in reported data breaches, there was also a drop in the number of breached records, which fell by 13.15% from 54.09 million records in 2021 to 51.9 million records in 2022.
The theft of protected health information places patients and health plan members at risk of identity theft and fraud, but by far the biggest concern is the threat to patient safety. Cyberattacks on healthcare providers often cause IT system outages, which in many cases have lasted several weeks causing considerable disruption to patient care. While there have not been any known cases of cyberattacks directly causing fatalities, the lack of access to patient data causes diagnosis and treatment delays that affect patient outcomes. Multiple studies have identified an increase in mortality rates at hospitals following ransomware attacks and other major cyber incidents.
These cyberattacks and data breaches result in huge financial losses for healthcare organizations. The 2022 IBM cost of a data breach report indicates the average cost of a healthcare data breach increased to an all-time high of $10.1 million in 2023, although data breaches can be significantly more expensive. In addition to the considerable breach remediation costs, security must be improved, cyber insurance premiums increase, and it is now common for multiple class action lawsuits to be filed following data breaches. There is also a risk of financial penalties from regulators.
The largest ever healthcare data breach, suffered by Anthem Inc in 2015, affected 78.8 million members and cost the health insurer around $230 million in clean-up costs, $115 million to settle the lawsuits, $39.5 million to settle the state attorneys general investigation, and $16 million to resolve the OCR investigation. Even much smaller data breaches can prove incredibly costly. Scripps Health suffered a data breach of 1.2 million records in 2021 due to a ransomware attack. The attack caused losses in excess of $113 million due to lost business ($92 million) and the clean-up costs ($21 million). There are also several lawsuits outstanding and there could be regulatory fines.
Largest Healthcare Data Breaches in 2022
There were 11 reported healthcare data breaches of more than 1 million records in 2022 and a further 14 data breaches of over 500,000 records. The majority of those breaches were hacking incidents, many of which involved ransomware or attempted extortion. Notable exceptions were several impermissible disclosure incidents that resulted from the use of pixels on websites. These third-party tracking technologies were added to websites to improve services and website functionality, but the data collected was inadvertently transmitted to third parties such as Meta and Google when users visited the websites while logged into their Google or Facebook accounts. The extent to which these tracking technologies have been used by healthcare organizations prompted OCR to issue guidance on these technologies, highlighting the considerable potential for HIPAA violations.
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Type of Breach |
| OneTouchPoint, Inc. |
WI |
Business Associate |
4,112,892 |
Ransomware attack |
| Advocate Aurora Health |
WI |
Healthcare Provider |
3,000,000 |
Pixel-related impermissible disclosure via websites |
| Connexin Software, Inc. |
PA |
Business Associate |
2,216,365 |
Hacking incident and data theft |
| Shields Health Care Group, Inc. |
MA |
Business Associate |
2,000,000 |
Hacking incident and data theft |
| Professional Finance Company, Inc. |
CO |
Business Associate |
1,918,941 |
Ransomware attack |
| Baptist Medical Center |
TX |
Healthcare Provider |
1,608,549 |
Malware infection |
| Community Health Network, Inc. as an Affiliated Covered Entity |
IN |
Healthcare Provider |
1,500,000 |
Pixel-related impermissible disclosure via websites |
| Novant Health Inc. on behalf of Novant Health ACE & as contractor for NMG Services Inc. |
NC |
Business Associate |
1,362,296 |
Pixel-related impermissible disclosure via websites |
| North Broward Hospital District d/b/a Broward Health (“Broward Health”) |
FL |
Healthcare Provider |
1,351,431 |
Hacking incident and data theft |
| Texas Tech University Health Sciences Center |
TX |
Healthcare Provider |
1,290,104 |
Hacking incident and data theft |
| Doctors’ Center Hospital |
PR |
Healthcare Provider |
1,195,220 |
Ransomware attack |
| Practice Resources, LLC |
NY |
Business Associate |
942,138 |
Hacking incident and data theft |
| Wright & Filippis LLC |
MI |
Healthcare Provider |
877,584 |
Ransomware attack |
| Partnership HealthPlan of California |
CA |
Health Plan |
854,913 |
Hacking incident and data theft |
| MCG Health, LLC |
WA |
Business Associate |
793,283 |
Hacking incident and data theft |
| Yuma Regional Medical Center |
AZ |
Healthcare Provider |
737,448 |
Ransomware attack |
| SightCare, Inc. |
AZ |
Health Plan |
637,999 |
Hacking incident and data theft |
| CommonSpirit Health |
IL |
Business Associate |
623,774 |
Ransomware attack |
| Metropolitan Area EMS Authority dba MedStar Mobile Healthcare |
TX |
Healthcare Provider |
612,000 |
Ransomware attack |
| Wolfe Clinic, P.C. |
IA |
Healthcare Provider |
542,776 |
Ransomware attack |
| Morley Companies, Inc. |
MI |
Business Associate |
521,046 |
Ransomware attack |
| Adaptive Health Integrations |
ND |
Healthcare Provider |
510,574 |
Adaptive Health Integrations |
| Christie Business Holdings Company, P.C. |
IL |
Healthcare Provider |
502,869 |
Hacking incident and data theft |
| Health Care Management Solutions, LLC |
WV |
Business Associate |
500,000 |
Hacking incident and data theft |
| OakBend Medical Center / OakBend Medical Group |
TX |
Healthcare Provider |
500,000 |
Ransomware attack |
While 2022 saw some very large data breaches reported, the majority of reported data breaches were relatively small. 81% of the year’s data breaches involved fewer than 50,000 records, and 58% involved between 500 and 999 records.
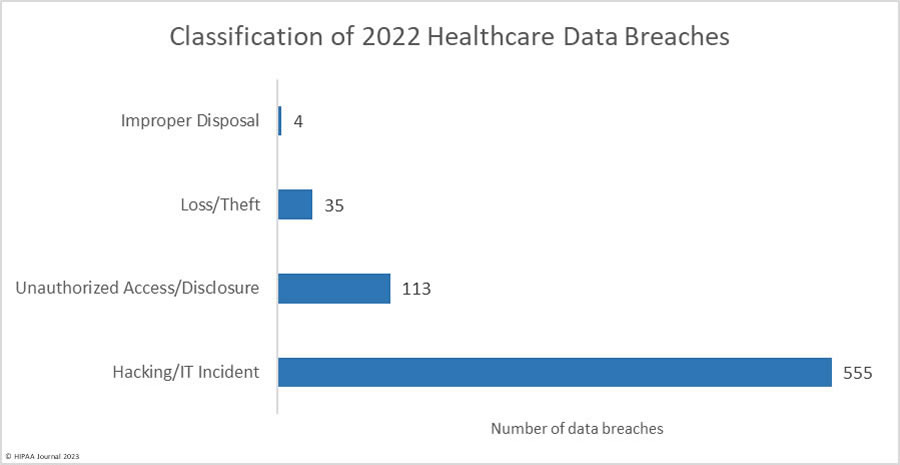
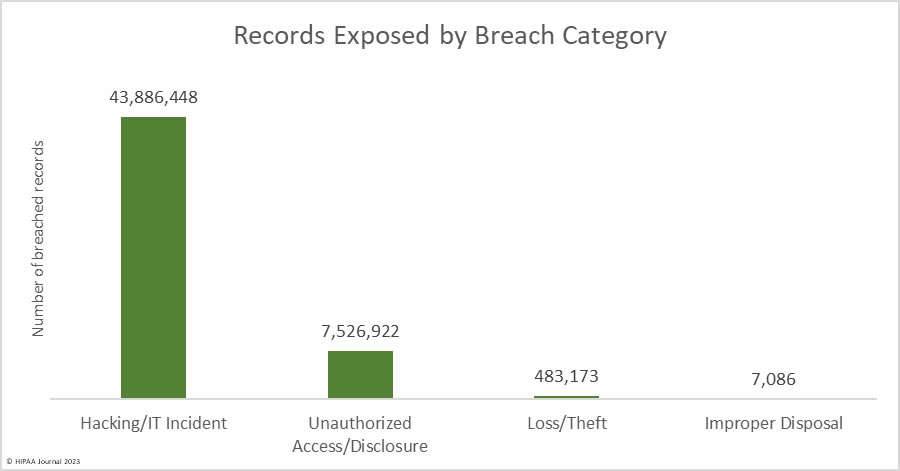
Hacking incidents dominated the breach reports with 555 of the 707 reported breaches (71.4%) classified as hacking/IT incidents, which accounted for 84.6% of all breached records in 2022. The average breach size was 79,075 records and the median breach size was 8,871 records. There were 113 reported unauthorized access/disclosure breaches reported in 2022, accounting for 14.5% of the breached records. The average breach size was 66,610 records due to some large pixel-related data breaches, and the median breach size was 1,652 records.
Theft (23 breaches) and loss (12 breaches) incidents were reported in relatively low numbers, continuing a downward trend from these once incredibly common data breaches. The downward trend is due to better control of devices and the use of encryption. The average breach size was 13,805 records and the median breach size was 1,704 records. There were four incidents involving the improper disposal of devices containing PHI and physical records. The average breach size was 1,772 records and the median was 1,021 records.
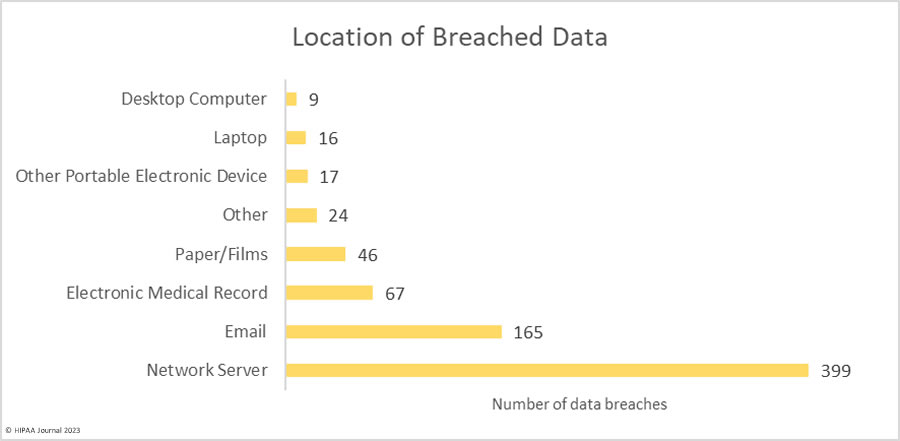
The high number of hacking incidents is reflected in the chart below, which shows the location of breached protected health information. Compromised email accounts remain a major source of data breaches, highlighting the importance of multi-factor authentication and training employees on how to recognize the signs of phishing.
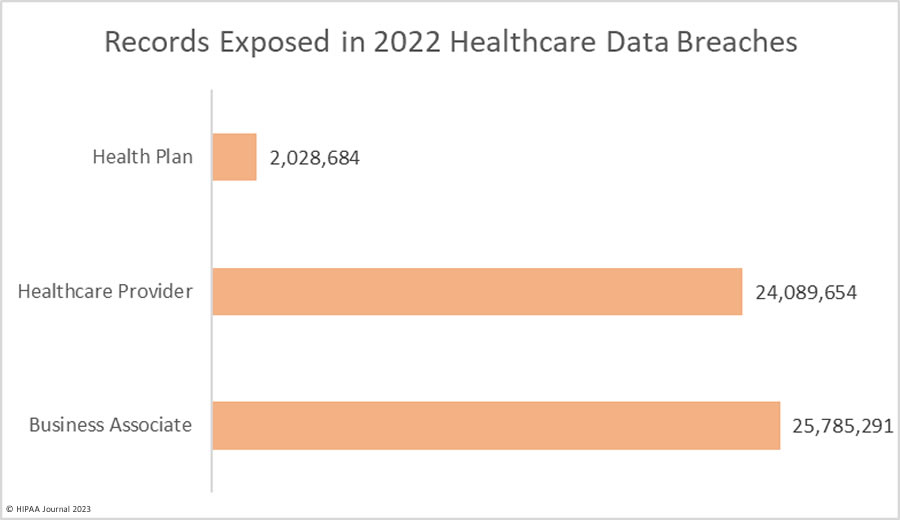
Which Entities Suffered the Most Data Breaches?
The raw data on the OCR breach portal does not accurately reflect the extent to which business associate data breaches are occurring. When you factor in business associate involvement it is possible to gain a more accurate gauge of the extent to which data breaches are occurring at business associates. In 2022, 127 data breaches were self-reported by business associates, but there were 394 reported data breaches where business associates were involved – That’s a 337% increase since 2018. Last year, data breaches at business associates outnumbered data breaches at healthcare providers for the first time.

Several major business associate data breaches were reported to OCR in 2022, with some of the data breaches affecting several hundred healthcare organizations. A data breach at the debt collections company, Professional Finance Company, affected 657 of its healthcare clients and involved more than 1.91 million healthcare records. Eye Care Leaders, a provider of electronic health records to eye care providers, suffered a cyberattack that affected at least 41 eye care providers and exposed the data of almost 3.65 million patients.
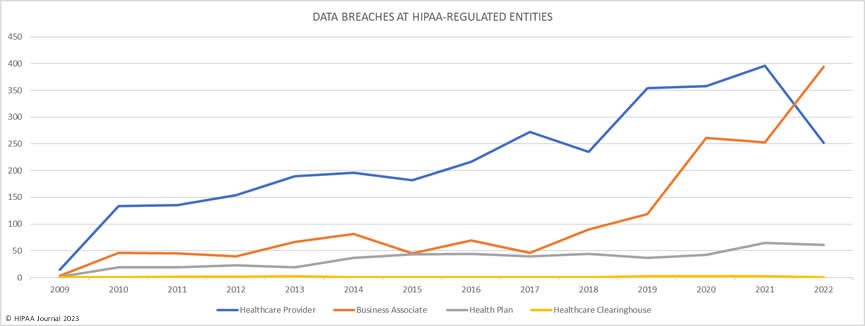
The graph below shows the sharp increase in data breaches at business associates in recent years. There are several reasons for the increase. Hackers have realized the value of conducting attacks on business associates. One successful attack can provide access to the data, and sometimes networks, of all of the vendor’s clients. Healthcare organizations are now using more vendors to manage administrative functions and risk increases in line with the number of vendors. As more vendors are used, it becomes harder to monitor cybersecurity at the vendors. Managing third-party risk is one of the biggest challenges for healthcare organizations in 2023.
Where Did the Data Breaches Occur?
Healthcare data breaches were reported by HIPAA-regulated entities in 49 states, Washington D.C., and Puerto Rico in 2022. Alaska was the only state to survive the year with no reported data breaches. In general, the most populated states suffer the most data breaches. In 2022, the 10 most populated U.S. states all ranked in the top 15 worst affected states, although it was New York rather than California that topped the list with 68 reported breaches.
| State |
Breaches |
| New York |
68 |
| California & Texas |
52 |
| Florida & Pennsylvania |
38 |
| New Jersey |
27 |
| Georgia |
26 |
| Michigan, Virginia & Washington |
24 |
| Ohio |
23 |
| Illinois & North Carolina |
22 |
| Tennessee |
17 |
| Arizona & Maryland |
16 |
| Massachusetts & Wisconsin |
15 |
| Colorado |
14 |
| Connecticut, Indiana & Missouri |
13 |
| Alabama |
11 |
| Kansas, Oklahoma & South Carolina |
9 |
| Arkansas, New Hampshire & West Virginia |
8 |
| Nebraska & Oregon |
7 |
| Minnesota |
6 |
| Utah |
5 |
| Delaware, Nevada & Rhode Island |
4 |
| Hawaii, Kentucky, Louisiana, Mississippi, Montana, South Dakota, % Vermont |
3 |
| Iowa, Idaho, Maine, New Mexico, and Washington D.C. |
2 |
| North Dakota & Wyoming |
1 |
| Alaska |
0 |
HIPAA Enforcement in 2022
HIPAA is primarily enforced by OCR, with state attorneys general also assisting with HIPAA enforcement. OCR imposed more financial penalties for HIPAA violations in 2022 than in any other year to date, with 22 investigations resulting in settlements or civil monetary penalties.
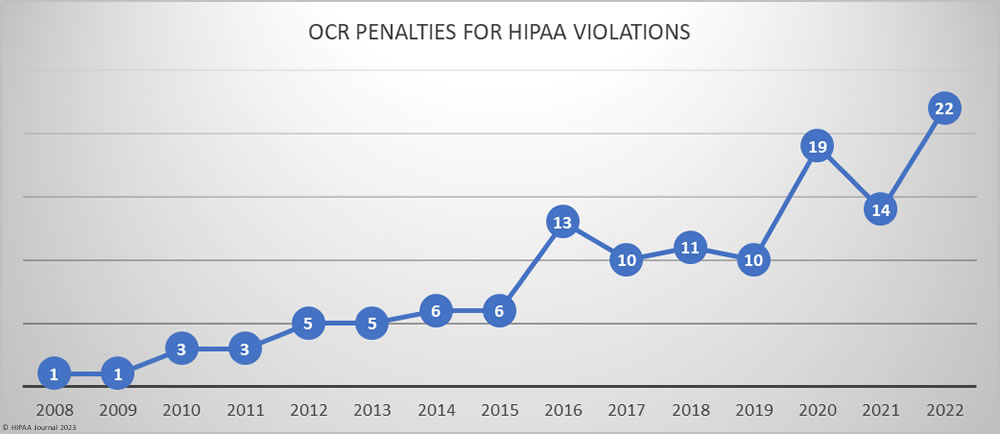
OCR has limited resources for investigations but does investigate all breaches of 500 or more records. That task has become increasingly difficult due to the increase in data breaches, which have tripled since 2010. Despite the increase in data breaches, OCR’s budget for HIPAA enforcement has hardly increased at all, aside from adjustments for inflation. As of January 17, 2022, OCR had 882 data breaches listed as still under investigation. 97% of all complaints and data breach investigations have been successfully resolved.
Some investigations warrant financial penalties, and while the number of penalties has increased, the penalty amounts for HIPAA violations have been decreasing. Most of the financial penalties in 2022 were under $100,000.
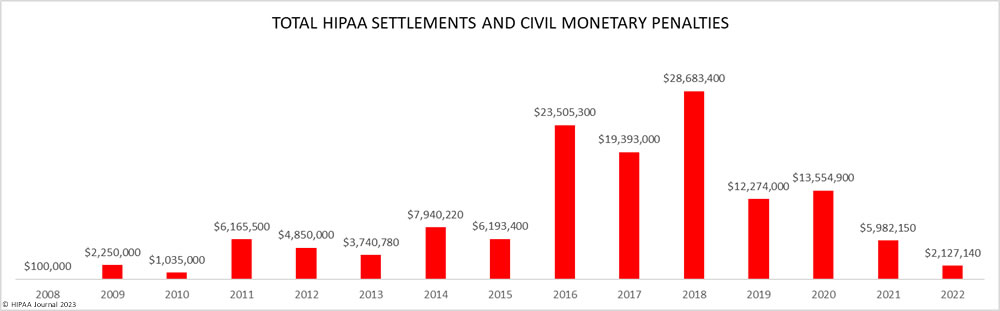
Since 2019, the majority of financial penalties imposed by OCR have been for HIPAA right of access violations, all of which stemmed from complaints from individual patients who had not been provided with their medical records within the allowed time frame. OCR continues to pursue financial penalties for other HIPAA violations, but these penalties are rare.
2022 HIPAA Settlements and Civil Monetary Penalties
| Regulated Entity |
Penalty Amount |
Type of Penalty |
Reason |
| Health Specialists of Central Florida Inc |
$20,000 |
Settlement |
HIPAA Right of Access failure |
| New Vision Dental |
$23,000 |
Settlement |
Impermissible PHI disclosure, Notice of Privacy Practices, releasing PHI on social media. |
| Great Expressions Dental Center of Georgia, P.C. |
$80,000 |
Settlement |
HIPAA Right of Access failure (time/fee) |
| Family Dental Care, P.C. |
$30,000 |
Settlement |
HIPAA Right of Access failure |
| B. Steven L. Hardy, D.D.S., LTD, dba Paradise Family Dental |
$25,000 |
Settlement |
HIPAA Right of Access failure |
| New England Dermatology and Laser Center |
$300,640 |
Settlement |
Improper disposal of PHI, failure to maintain appropriate safeguards |
| ACPM Podiatry |
$100,000 |
Civil Monetary Penalty |
HIPAA Right of Access failure |
| Memorial Hermann Health System |
$240,000 |
Settlement |
HIPAA Right of Access failure |
| Southwest Surgical Associates |
$65,000 |
Settlement |
HIPAA Right of Access failure |
| Hillcrest Nursing and Rehabilitation |
$55,000 |
Settlement |
HIPAA Right of Access failure |
| MelroseWakefield Healthcare |
$55,000 |
Settlement |
HIPAA Right of Access failure |
| Erie County Medical Center Corporation |
$50,000 |
Settlement |
HIPAA Right of Access failure |
| Fallbrook Family Health Center |
$30,000 |
Settlement |
HIPAA Right of Access failure |
| Associated Retina Specialists |
$22,500 |
Settlement |
HIPAA Right of Access failure |
| Coastal Ear, Nose, and Throat |
$20,000 |
Settlement |
HIPAA Right of Access failure |
| Lawrence Bell, Jr. D.D.S |
$5,000 |
Settlement |
HIPAA Right of Access failure |
| Danbury Psychiatric Consultants |
$3,500 |
Settlement |
HIPAA Right of Access failure |
| Oklahoma State University – Center for Health Sciences (OSU-CHS) |
$875,000 |
Settlement |
Risk analysis, security incident response and reporting, evaluation, audit controls, breach notifications, & the impermissible disclosure of the PHI of 279,865 individuals |
| Dr. Brockley |
$30,000 |
Settlement |
HIPAA Right of Access |
| Jacob & Associates |
$28,000 |
Settlement |
HIPAA Right of Access, notice of privacy practices, HIPAA Privacy Officer |
| Dr. U. Phillip Igbinadolor, D.M.D. & Associates, P.A., |
$50,000 |
Civil Monetary Penalty |
Impermissible disclosure on social media |
| Northcutt Dental-Fairhope |
$62,500 |
Settlement |
Impermissible disclosure for marketing, notice of privacy practices, HIPAA Privacy Officer |
HIPAA enforcement by state attorneys general is relatively rare. Only three financial penalties were imposed in 2022 by state attorneys general. In these cases, penalties were imposed for violations of the HIPAA Rules and state laws.
| State |
Regulated Entity |
Penalty |
Penalty Type |
Reason |
| Oregon/Utah |
Avalon Healthcare |
$200,000 |
Settlement |
Lack of safeguards and late breach notifications |
| Massachusetts |
Aveanna Healthcare |
$425,000 |
Settlement |
Lack of safeguards against phishing |
| New York |
EyeMed Vision Care |
$600,000 |
Settlement |
Multiple security failures |
The post 2022 Healthcare Data Breach Report appeared first on HIPAA Journal.










