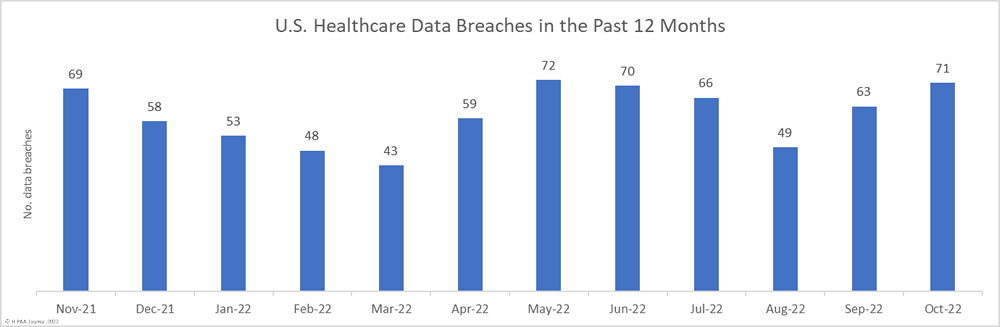
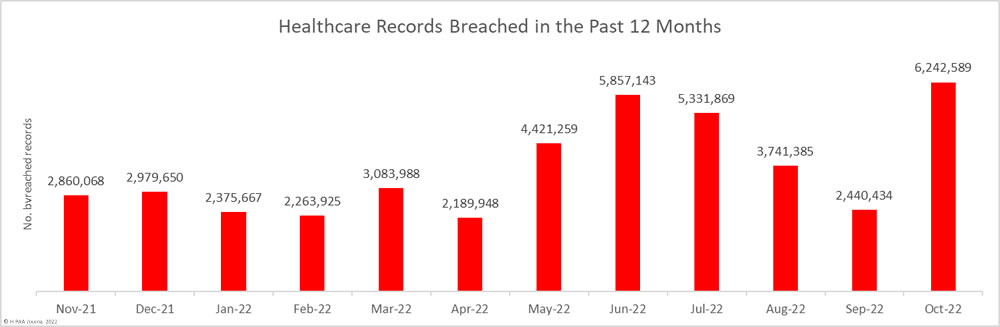
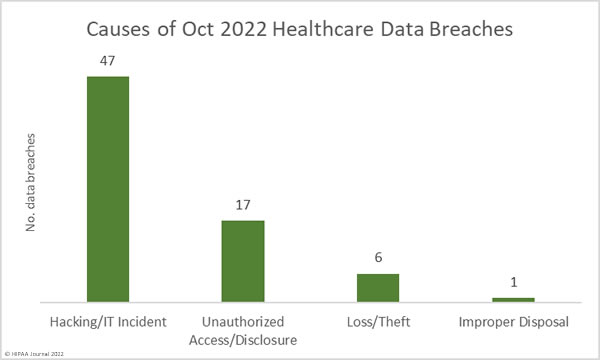
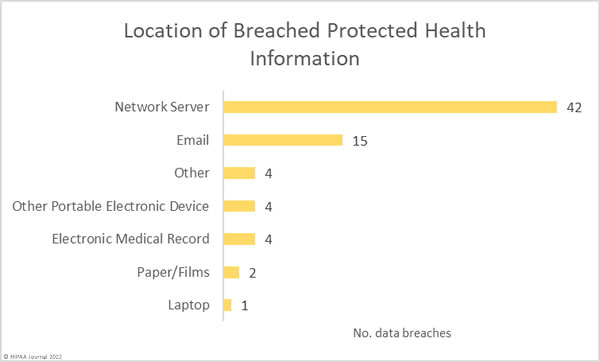
Sen. Mark Warner (D-Va) recently published a white paper framing cybersecurity as a patient safety issue. The paper suggested several policy updates that could help improve healthcare cybersecurity and encourage healthcare organizations to invest more in cybersecurity, such as the introduction of an incentive program similar to the Meaningful Use program that rewards healthcare providers that make cybersecurity improvements.
Healthcare cybersecurity has never been as important as it is today and, as Warner explained, cybersecurity in healthcare “is exponentially growing in importance.” Warner says the white paper is a starting point to open up a discussion about changes that can be implemented to improve cybersecurity in the sector, rather than a blueprint for change.
At the heart of the white paper are three major challenges – The first is to improve federal oversight and appoint a leader with overall control or authority, rather than the current mishmash of agencies that have responsibilities related to healthcare cybersecurity. Then a change in mindset is required, where cybersecurity is viewed as a patient safety issue rather than a secondary concern. Cybersecurity needs to be baked into healthcare, not bolted on as an afterthought. Finally, and perhaps the biggest challenge to overcome is the current staffing shortage. There are simply not enough skilled workers to fill the cybersecurity roles in healthcare, so investment is needed in training and retention, especially since salaries in healthcare are typically lower than in other sectors. Together, solving these issues will be a major challenge.
Sen. Warner sought feedback from healthcare industry stakeholders on the white paper, with the comment period officially coming to an end on December 1, 2022; however, since the white paper covers such important issues, the deadline has been extended.
The white paper has received considerable praise from industry leaders, with the American Hospital Association and CHIME and AEHIS agreeing with many of the suggestions. Both have written to Sen Warner and have provided feedback and recommendations to better support their members.
AHA Feedback on Cybersecurity is Patient Safety White Paper
The AHA said “hospitals and health systems have prioritized protecting patients and defending their networks from cyberattacks. However, they need support from the federal government as the field continues to face targets from sophisticated cyber adversaries and nation-states.”
With respect to leadership, the AHA supports the appointment of a senior cybersecurity leadership role within the HHS and recommends better coordination between the HHS and the Cybersecurity and Infrastructure Security Agency (CISA), such as by improving delineation of specific authorities, roles, and responsibilities. The AHA confirmed it supports the Healthcare Cybersecurity Act, which authorizes cybersecurity training for the Healthcare and Public Health (HPH) sector, and calls for an analysis of cybersecurity risks faced by the HPH sector, especially regarding the impacts to rural hospitals, vulnerabilities of medical devices, and cybersecurity workforce shortages. The AHA has also strongly recommended financial incentives and qualifying grants to be made available to healthcare providers to support the implementation of cybersecurity technology and best practices, such as those detailed in the NIST guidelines and the HICP.
Greater support is required from the federal government for victims of cyberattacks
The AHA points out that many cyberattacks on the healthcare industry are either associated with or supported by nation-states, and as such, they are a national security issue, so the burden of defending against these attacks should not be shouldered solely by private sector organizations. The AHA has called for the federal government to consider ways to provide additional guidance and support to healthcare organizations that are victims of cyberattacks, especially to help them recover quickly, just like the federal government provides support to victims of terrorist attacks.
Help protect healthcare R&D and related intellectual property
The AHA supports tackling threats to healthcare IP through the existing Department of Justice Task Force on Intellectual Property, and for guidance to be released for industry and academia on evaluating the potential economic impact, reputational damage, loss of intellectual property, and other cybersecurity risks for health care research and development, and recommendations should be provided on how to best combat these threats. The AHA has also recommended small and rural research institutions be considered when drafting new guidance. The AHA has previously proposed a methodology that should be considered, which is based on four steps: educate, catalog, classify, and control.
NIST should release healthcare-specific guidance
The AHA says the NIST Cybersecurity Framework has been hugely beneficial for the healthcare industry but has recommended NIST further integrate healthcare cybersecurity subject matter experts into the development of its work products, and to release products and guidance focused on the healthcare industry. Since many healthcare organizations lack the financial resources to implement the NIST CSF, the AHA recommends offering financial incentives and qualifying grants to help them implement appropriate cybersecurity technology and the best practices outlined in the NIST CSF.
Modernize HIPAA to better address healthcare cybersecurity
While a new regulatory framework could be implemented to improve healthcare cybersecurity, the AHA says this is likely to be problematic. Instead, the AHA recommends modernizing HIPAA to address the current cyber threat landscape. The AHA has also called for the HHS to provide model language that can be used to help healthcare providers explain to patients the risks associated with accessing their health data through an app and to expand HIPAA to cover software applications and consumer devices that collect health information, to ensure they comply with the same privacy and security standards.
Support for workforce development programs and student loan forgiveness
The AHA supports the development and promotion of workforce training programs in cybersecurity and the funding of targeted internships or other programs to place cybersecurity professionals in small and rural facilities. The AHA supports student loan forgiveness and suggests that in order to qualify, workers should serve consistently for at least three years in a primary cybersecurity role in small and rural hospitals.
Create an incentive program to improve healthcare providers’ cybersecurity capabilities
AHA has expressed support for ensuring appropriate minimum cyber hygiene practices are adopted but says the Medicare Conditions of Participation (CoPs) and Conditions of Coverage (CoCs) are not the ideal places for monitoring minimum cybersecurity practices. While CoPs and CoCs are enforced by surveyors from either state agencies or contracted accrediting bodies, the surveyors are not necessarily cybersecurity experts. Further, the CoPs and CoCs are not updated frequently enough to reflect changes in cyber hygiene practices, and making frequent changes would require extensive resources and could result in confusion and distrust of the integrity of the CoPs.
Address the issue of insecure legacy systems
The AHA has called for manufacturers of legacy devices to provide a secure environment to ensure safe patient care, including wrapping security precautions around these devices and adding security tools and auditing capabilities. Regular updates and patches should be provided for all software, and vulnerabilities should be communicated rapidly. The FDA should also make it clear that security updates are required, not optional. The AHA also supports the provision of a software bill of materials to help healthcare organizations manage the security of their devices and confirmed it supports the PATCH Act, which Congress should pass.
Address the cost of cybersecurity improvements
Updating technology to improve cybersecurity comes at a considerable cost to healthcare providers. One way to support healthcare organizations financially would be to make sure that Medicare and Medicaid fixed payments accurately reflect the cost of care. Many hospitals rely on these payments, but they are often less than the cost of providing care. The AHA warns that now is not the time to make cuts to these payments.
Support recovery from cyberattacks and establish a disaster relief program
The AHA has called for the strategic national stockpile (SNS) to be augmented with common equipment needed by hospitals facing cyberattacks and to include specialized cybersecurity resources for cyberattacks in the SNS for healthcare organizations, as hospitals are considered part of the critical infrastructure of the nation. The AHA also supports the creation of a cyber disaster relief program that provides financial, technical, and human resources during and post-attack, and for the government to create a reinsurance program to assist victims of high-impact cyberattacks, akin to victims of international terrorist attacks.
CHIME & AEHIS Feedback on Cybersecurity is Patient Safety White Paper
CHIME and AEHIS have applauded the efforts of Sen. Warner and his commitment to highlighting and ameliorating the patient safety and national security risks posed to the healthcare sector by cyberattacks and calls for Congress to act now to improve the security of the healthcare sector. Feedback has been provided on several issues and policy changes outlined in the white paper, the key suggestions are detailed below.
Address funding challenges
CHIME/AEHIS recommend Congress increase funding for the HHS for cybersecurity for each of ASPR, HC3, and the 405(d) program, create a grant program specifically for small, medium, and under-resourced providers to help them make rapid improvements to cybersecurity, and to create a voluntary incentive program for healthcare providers to offset investments in cybersecurity. CHIME/AHGIS agree with the suggested ‘cash for clunkers’ program, but says this should be for healthcare providers, not device manufacturers.
405(d) program
CHIME/AEHIS believe the ASPR should remain the SRMA and the 405(d) program should continue to support the sector’s joint public-private partnership in developing best practices and other tools to improve the sector’s cybersecurity posture, and recommends the HHS engage in more education efforts and use the CMS as an outreach channel to improve awareness and education about 405(d) and other free federal resources on cybersecurity.
Penalties and incentives
CHIME/AEHIS have made several suggestions about penalties and incentives, recommending the latter is a better strategy than punitive actions. Like the AHA, CHIME/AEHIS advise against using CoPs to drive the adoption of cybersecurity best practices, saying this should be avoided at all costs. CHIME/AEHIS also propose a reduction in OCR penalties for victims of cyberattacks, and not to force under-resourced providers to shoulder the entire burden of cybercrimes.
There should also be a greater emphasis on unmasking, charging, and prosecuting cybercriminals, and punishments for individuals who attack the healthcare sector should be increased. CHIME/AEHIS also suggest a broadening of the types of technology eligible for donation under Stark and Antikickback policies, and prohibit donor recipients from taking legal action against their donor in the event of a cyber incident.
Incentives should include establishing a cybersecurity incentive program to the 405(d) Program’s best practices as detailed in HICP, to recognize and reward HCIP best practices, and for funding to be prioritized for small, medium, and under-resourced providers, as well as providers who were not eligible for electronic health record (EHR) incentives. CHIME suggests the CMS should oversee the cybersecurity incentive programs.
Medical device security
CHIME/AEHIS are supporters of the PATCH Act and strongly recommend Congress pass this legislation to give the FDA greater oversight of medical device manufacturers, they also suggest the FDA should be authorized to issue legally binding regulations and that the 2017 Task Force should be reconvened to develop a plan to prioritize the medical devices that are eligible for a replacement program.
Several recommendations have been made concerning medical device manufacturers, including prohibiting the sale of devices with software that is no longer supported or at end-of-life, supporting devices to ensure they are not sunsetted, directly notifying providers about software updates, vulnerabilities, and patches, and as per the PATCH Act, to ensure a software bill of materials is provided.
Patient privacy
CHIME/AEHIS recommend the FDA and OCR better align their guidance and enforcement activities, specifically to ensure that medical device manufacturers are meeting their obligations as HIPAA business associates. While the AHA recommends an update to HIPAA, CHIME/AEHIS suggest a new national privacy law be created covering non-HIPAA-covered health data, and until such a privacy law is passed, app developers must inform consumers about how their health data is being used. They also call for the FTC to be provided with sufficient funding to enforce the Health Breach Notification Rule.
Cyber insurance
CHIME/AEHIS suggest greater insight is needed for private cyber insurance carriers, and the government should establish a catastrophic cyber insurance program to help healthcare providers offset the extremely high costs of cyberattacks. That program would also serve as a backstop for providers that have been unable to obtain cyber insurance coverage on the open market.
Workforce shortages
To address the current workforce shortage in cybersecurity, a federal workforce development program should be created, access should be given to free cyber training under the Regional Extension Centers (RECs) model, and student loan forgiveness programs should be established for individuals taking on cybersecurity roles in healthcare.
The post Industry Groups Provide Feedback on Sen. Warner’s ‘Cybersecurity is Patient Safety’ White Paper appeared first on HIPAA Journal.