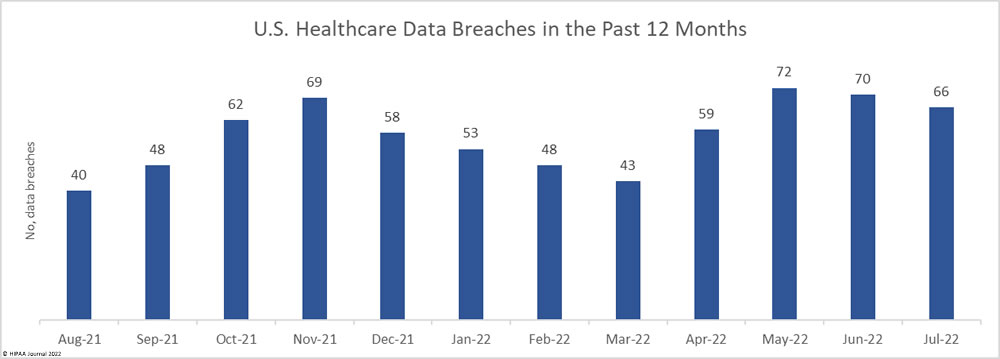
In July 2022, 66 healthcare data breaches of 500 or more records were reported to the Department of Health and Human Services’ Office for Civil Rights, which is a 5.71% reduction from the 70 data breaches reported in June 2022 and July 2021. While the number of data breaches fell slightly from last month, data breaches are being reported at well over the average monthly rate of 57 breaches per month.
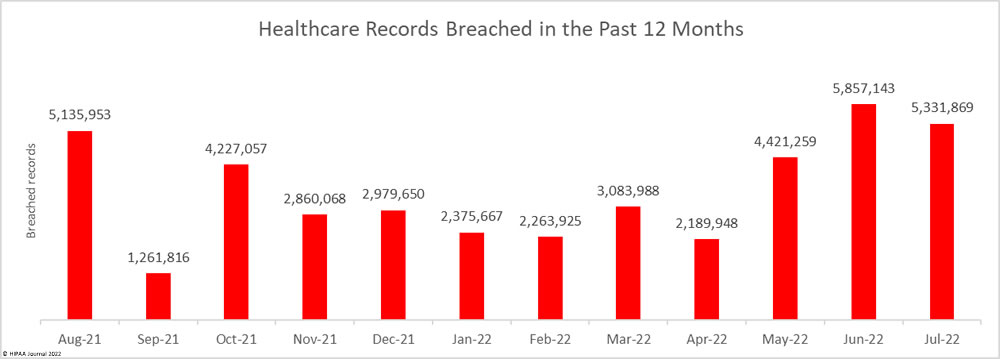
For the second consecutive month, the number of exposed or impermissibly disclosed healthcare records topped 5 million. 5,331,869 records were breached across the 66 reported incidents, which is well above the 12-month average of 3,499,029 breaches a month. July saw 8.97% fewer records breached than June 2022 and 7.67% fewer than July 2021.
Largest Healthcare Data Breaches in July 2022
In July, 25 data breaches of 10,000 or more records were reported, 15 of which occurred at business associates of HIPAA-covered entities. The largest data breach was a ransomware attack on the accounts receivable management agency, Professional Finance Company. Cyberattacks on business associates can affect many different HIPAA-covered entities, as was the case with the PFC breach, which affected 657 HIPAA-covered entities. The breach was reported by PFC as affecting more than 1.9 million individuals, although some of those clients have reported the breach separately. It is unclear how many records in total were compromised in the ransomware attack.
The second largest data breach occurred at the Wisconsin mailing vendor, OneTouchPoint. This was also a ransomware attack and was reported by OneTouchPoint as affecting more than 1 million individuals, but as was the case with the PFC ransomware attack, some of its healthcare provider clients self-reported the data breach, including Aetna ACE Health Plan. Goodman Campbell Brain and Spine also suffered a major ransomware attack. The Indiana-based healthcare provider confirmed that the threat actors had uploaded the stolen data to their data leak site.
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Business Associate Breach |
Cause of Breach |
| Professional Finance Company, Inc. |
CO |
Business Associate |
1,918,941 |
Yes |
Ransomware attack |
| OneTouchPoint, Inc. |
WI |
Business Associate |
1,073,316 |
Yes |
Ransomware attack |
| Goodman Campbell Brain and Spine |
IN |
Healthcare Provider |
362,833 |
No |
Ransomware attack – Data leak confirmed |
| Aetna ACE |
CT |
Health Plan |
326,278 |
Yes |
Ransomware attack on mailing vendor (OneTouchPoint) |
| Synergic Healthcare Solutions, LLC dba Fast Track Urgent Care Center |
FL |
Healthcare Provider |
258,411 |
Yes |
Hacking incident at billing vendor (PracticeMax) |
| Avamere Health Services, LLC |
OR |
Business Associate |
197,730 |
Yes |
Hacking incident – Data theft confirmed |
| BHG Holdings, LLC dba Behavioral Health Group |
TX |
Healthcare Provider |
197,507 |
No |
Hacking incident – Data theft confirmed |
| Premere Infinity Rehab, LLC |
OR |
Business Associate |
183,254 |
Yes |
Hacking incident at business associate (Avamere Health Services) – Data theft confirmed |
| Carolina Behavioral Health Alliance, LLC |
NC |
Business Associate |
130,922 |
Yes |
Hacking incident |
| Family Practice Center PC |
PA |
Healthcare Provider |
83,969 |
No |
Hacking incident |
| Kaiser Foundation Health Plan, Inc. (Southern California) |
CA |
Health Plan |
75,010 |
No |
Theft of device in a break-in at a storage facility |
| Magie Mabrey Hughes Eye Clinic, P.A. dba Arkansas Retina |
AR |
Healthcare Provider |
57,394 |
Yes |
Ransomware attack on EHR vendor (Eye Care Leaders) |
| McLaren Port Huron |
MI |
Healthcare Provider |
48,957 |
Yes |
Hacking incident at business associate (MCG Health) – Data theft confirmed |
| Southwest Health Center |
WI |
Healthcare Provider |
46,142 |
No |
Hacking incident – Data theft confirmed |
| WellDyneRx, LLC |
FL |
Business Associate |
43,523 |
Yes |
Email account compromised |
| Associated Eye Care |
MN |
Healthcare Provider |
40,793 |
Yes |
Ransomware attack on EHR vendor (Eye Care Leaders) |
| Zenith American Solutions |
WA |
Business Associate |
37,146 |
Yes |
Mailing error |
| Benson Health |
NC |
Healthcare Provider |
28,913 |
No |
Hacking incident |
| Healthback Holdings, LLC |
OK |
Healthcare Provider |
21,114 |
No |
Email accounts compromised |
| East Valley Ophthalmology |
AZ |
Healthcare Provider |
20,734 |
Yes |
Ransomware attack on EHR vendor (Eye Care Leaders) |
| Arlington Skin |
VA |
Healthcare Provider |
17,468 |
No |
Hacking incident at EHR management company (Virtual Private Network Solutions) |
| The Bronx Accountable Healthcare Network |
NY |
Healthcare Provider |
17,161 |
No |
Email accounts compromised |
| Granbury Eye Clinic |
TX |
Healthcare Provider |
16,475 |
Yes |
Ransomware attack on EHR vendor (Eye Care Leaders) |
| CHRISTUS Spohn Health System Corporation |
TX |
Healthcare Provider |
15,062 |
No |
Ransomware attack – Data leak confirmed |
| Central Maine Medical Center |
ME |
Healthcare Provider |
11,938 |
Yes |
Hacking incident at business associate (Shields Healthcare Group) |
Causes of July 2022 Healthcare Data Breaches
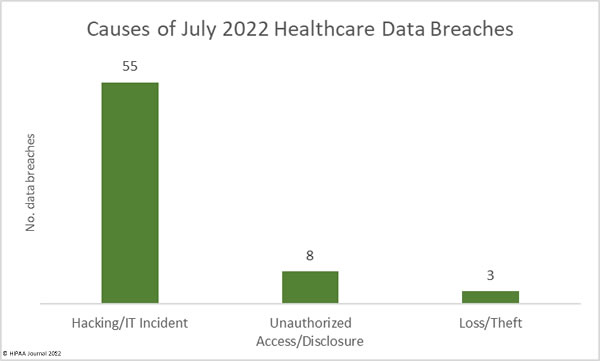
Hacking/IT incidents dominated the breach reports in July with 55 data breaches classed as hacking/IT incidents, with ransomware attacks continuing to be a problem for the healthcare industry. 9 of the top 25 breaches were reported as ransomware attacks, although HIPAA-regulated often do not disclose the exact nature of cyberattacks and whether ransomware was involved. Across the hacking incidents, the records of 5,195,024 individuals were breached, which is 97.43% of all records breached in July. The average breach size was 94,455 records and the median breach size was 4,447 records. The median breach size is less than half the median breach size in June due to a large number of relatively small data breaches.
There were 8 unauthorized access/disclosure incidents reported involving 59,784 records. The average breach size was 7,473 records and the median breach size was 1,920 records. There were 3 incidents reported involving the loss of devices/physical documents containing PHI, and one reported theft. 77,061 records were exposed across those 3 incidents. The average breach size was 25,687 records and the median breach size of 1,201 records.
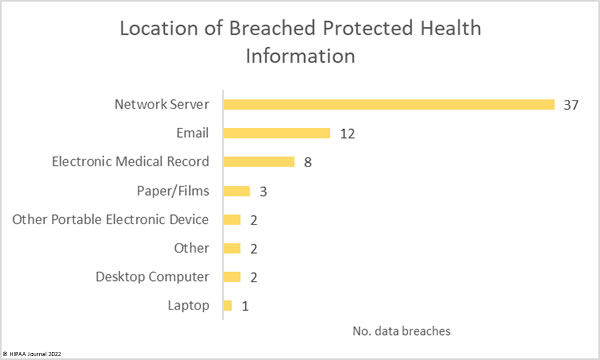
Unsurprisingly given the large number of hacking incidents, 56% of the month’s breaches involved PHI stored on network servers. 12 incidents involved unauthorized access to email accounts, caused by a mix of phishing and brute force attacks.
There has been a marked increase in hybrid phishing attacks on the healthcare industry in recent months, where non-malicious emails are sent that include a phone number manned by the threat actor. According to Agari, Q2, 2022 saw a 625% increase in hybrid phishing attacks, where initial contact was made via email with the scam taking place over the phone. Several ransomware groups have adopted this tactic as the main way of gaining initial access to victims’ networks. The lures used in the emails are typically notifications about upcoming charges that will be applied if the recipient does not call the number to stop the payment for a free trial of a software solution or service that is coming to an end or the renewal of a subscription for a product. In these attacks, the victim is tricked into opening a remote access session with the threat actor.
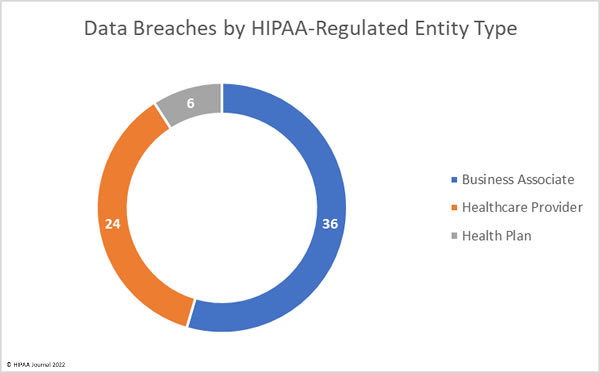
HIPAA Regulated Entities Affected by Data Breaches
Every month, healthcare providers are the worst affected HIPAA-regulated entity type, but there was a change in July with business associates of HIPAA-regulated entities topping the list. 39 healthcare providers reported data breaches but 15 of those breaches occurred at business associates. 10 health plans reported breaches, with 4 of those breaches occurring at business associates. 17 business associates self-reported breaches. The chart below shows the month’s data breaches based on where they occurred, rather than the reporting entity.
July 2022 Healthcare Data Breaches by State
Data breaches of 500 or more records were reported by HIPAA-regulated entities in 29 states, with Texas the worst affected with 10 data breaches.
| State |
No. Breaches |
| Texas |
10 |
| Pennsylvania & Virginia |
5 |
| California, Florida, North Carolina & Wisconsin |
4 |
| Arizona, Connecticut, Georgia, Illinois, New Hampshire, Ohio, Oklahoma, & Oregon |
2 |
| Alabama, Arkansas, Colorado, Indiana, Iowa, Maine, Massachusetts, Michigan, Minnesota, Missouri, New York, Rhode Island, Washington, & Wyoming |
1 |
HIPAA Enforcement Activity in July 2022
From January to June, only 4 enforcement actions were announced by the HHS’ Office for Civil Rights; however, July saw a further 12 enforcement actions announced that resulted in financial penalties to resolve HIPAA violations. OCR has continued with its HIPAA Right of Access enforcement initiative, with 11 of the penalties imposed for the failure to provide patients with timely access to their medical records. 10 of those investigations were settled, and one was resolved with a civil monetary penalty.
July also saw one investigation settled with OCR that resolved multiple alleged violations of the HIPAA Rules that were uncovered during an investigation of a 279,865-record data breach at Oklahoma State University – Center for Health Sciences.
No HIPAA enforcement actions were announced by state attorneys general in July.
| Covered Entity |
Amount |
Settlement/CMP |
Reason |
| ACPM Podiatry |
$100,000 |
Civil Monetary Penalty |
HIPAA Right of Access failure |
| Oklahoma State University – Center for Health Sciences (OSU-CHS) |
$875,000 |
Settlement |
Risk analysis, security incident response and reporting, evaluation, audit controls, breach notifications, & the impermissible disclosure of the PHI of 279,865 individuals |
| Memorial Hermann Health System |
$240,000 |
Settlement |
HIPAA Right of Access failure |
| Southwest Surgical Associates |
$65,000 |
Settlement |
HIPAA Right of Access failure |
| Hillcrest Nursing and Rehabilitation |
$55,000 |
Settlement |
HIPAA Right of Access failure |
| MelroseWakefield Healthcare |
$55,000 |
Settlement |
HIPAA Right of Access failure |
| Erie County Medical Center Corporation |
$50,000 |
Settlement |
HIPAA Right of Access failure |
| Fallbrook Family Health Center |
$30,000 |
Settlement |
HIPAA Right of Access failure |
| Associated Retina Specialists |
$22,500 |
Settlement |
HIPAA Right of Access failure |
| Coastal Ear, Nose, and Throat |
$20,000 |
Settlement |
HIPAA Right of Access failure |
| Lawrence Bell, Jr. D.D.S |
$5,000 |
Settlement |
HIPAA Right of Access failure |
| Danbury Psychiatric Consultants |
$3,500 |
Settlement |
HIPAA Right of Access failure |
The post July 2022 Healthcare Data Breach Report appeared first on HIPAA Journal.





