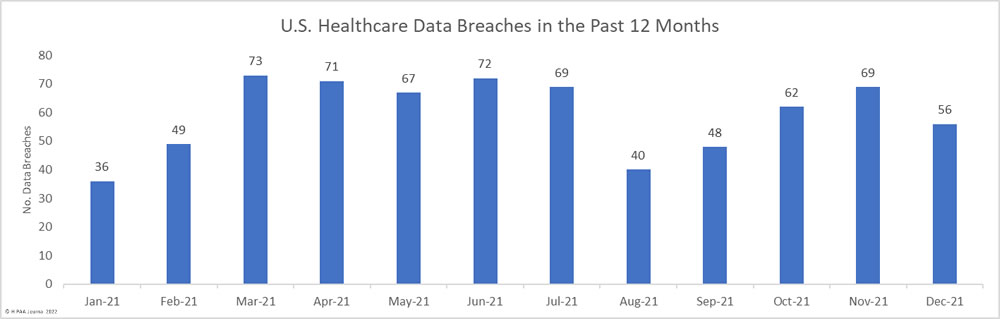
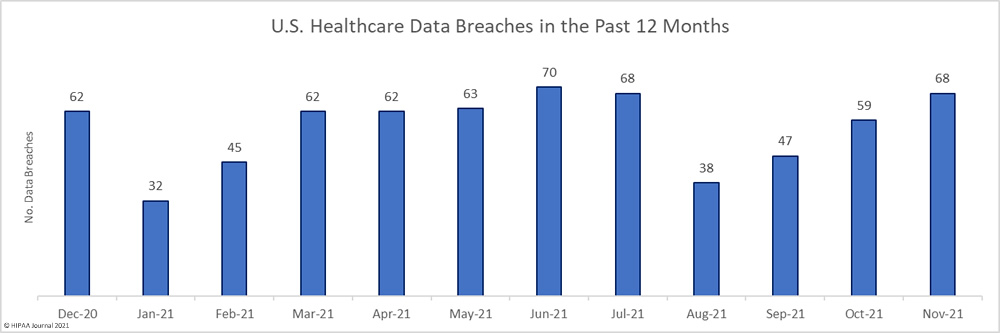
56 data breaches of 500 or more healthcare records were reported to the HHS’ Office for Civil Rights (OCR) in December 2021, which is a 17.64% decrease from the previous month. In 2021, an average of 59 data breaches were reported each month and 712 healthcare data breaches were reported between January 1 and December 31, 2021. That sets a new record for healthcare data breaches, exceeding last year’s total by 70 – An 10.9% increase from 2020.
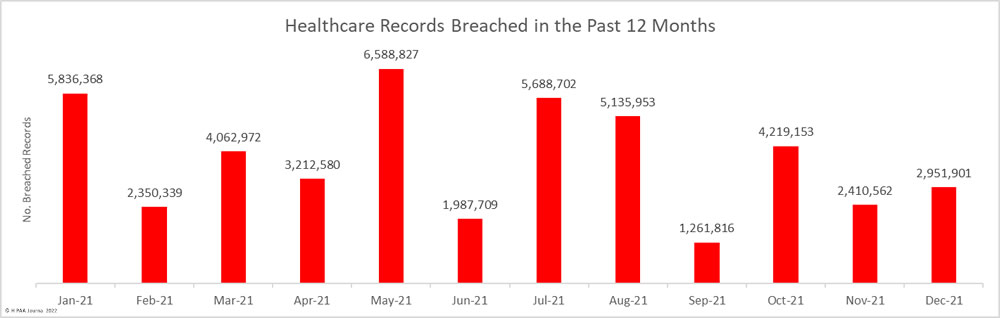
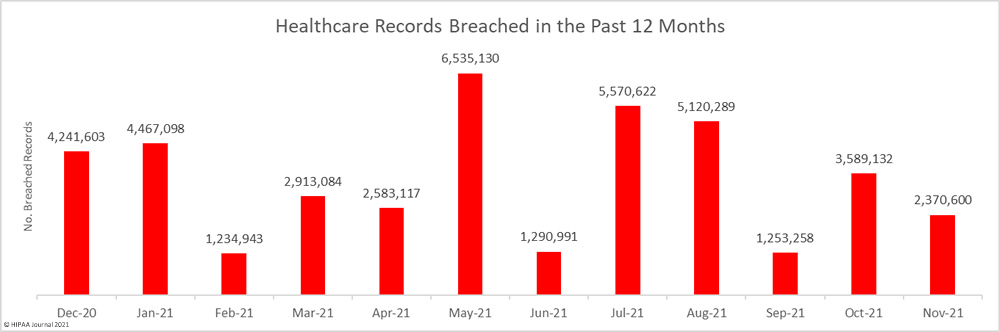
Across December’s 56 data breaches, 2,951,901 records were exposed or impermissibly disclosed – a 24.52% increase from the previous month. At the time of posting, the OCR breach portal shows 45,706,882 healthcare records were breached in 2021 – The second-highest total since OCR started publishing summaries of healthcare data breaches in 2009.
Largest Healthcare Data Breaches in December 2021
| Name of Covered Entity | State | Covered Entity Type | Individuals Affected | Breach Cause |
| Oregon Anesthesiology Group, P.C. | OR | Healthcare Provider | 750,500 | Ransomware |
| Texas ENT Specialists | TX | Healthcare Provider | 535,489 | Ransomware |
| Monongalia Health System, Inc. | WV | Healthcare Provider | 398,164 | Business Email Compromise/Phishing |
| BioPlus Specialty Pharmacy Services, LLC | FL | Healthcare Provider | 350,000 | Hacked network server |
| Florida Digestive Health Specialists, LLP | FL | Healthcare Provider | 212,509 | Business Email Compromise/Phishing |
| Daniel J. Edelman Holdings, Inc. | IL | Health Plan | 184,500 | Business associate hacking/IT incident |
| Southern Orthopaedic Associates d/b/a Orthopaedic Institute of Western Kentucky | KY | Healthcare Provider | 106,910 | Compromised email account |
| Fertility Centers of Illinois, PLLC | IL | Healthcare Provider | 79,943 | Hacked network server |
| Bansley and Kiener, LLP | IL | Business Associate | 50,119 | Ransomware |
| Oregon Eye Specialists | OR | Healthcare Provider | 42,612 | Compromised email accounts |
| MedQuest Pharmacy, Inc. | UT | Healthcare Provider | 39,447 | Hacked network server |
| Welfare, Pension and Annuity Funds of Local No. ONE, I.A.T.S.E. | NY | Health Plan | 20,579 | Phishing |
| Loyola University Medical Center | IL | Healthcare Provider | 16,934 | Compromised email account |
| Bansley and Kiener, LLP | IL | Business Associate | 15,814 | Ransomware |
| HOYA Optical Labs of America, Inc. | TX | Business Associate | 14,099 | Hacked network server |
| Wind River Family and Community Health Care | WY | Healthcare Provider | 12,938 | Compromised email account |
| Ciox Health | GA | Business Associate | 12,493 | Compromised email account |
| A New Leaf, Inc. | AZ | Healthcare Provider | 10,438 | Ransomware |
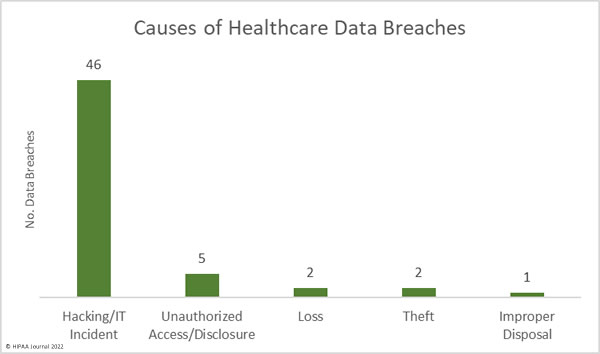
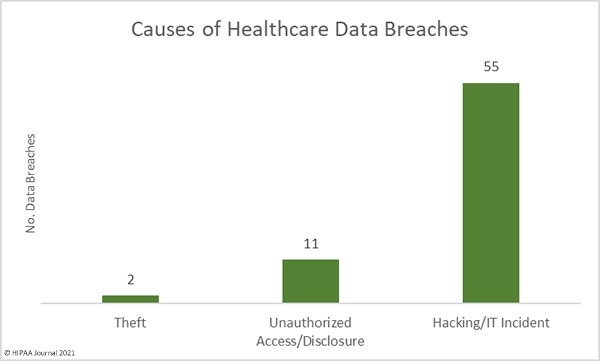
Causes of December 2021 Healthcare Data Breaches
18 data breaches of 10,000 or more records were reported in December, with the largest two breaches – two ransomware attacks – resulting in the exposure and potential theft of a total of 1,285,989 records. Ransomware continues to pose a major threat to healthcare organizations. There have been several successful law enforcement takedowns of ransomware gangs in recent months, the most recent of which saw authorities in Russia arrest 14 members of the notorious REvil ransomware operation, but there are still several ransomware gangs targeting the healthcare sector including Mespinoza, which the HHS’ Health Sector Cybersecurity Coordination Center (HC3) issued a warning about this month due to the high risk of attacks.
Phishing attacks continue to result in the exposure of large amounts of healthcare data. In December, email accounts were breached that contained the ePHI of 807,984 individuals. The phishing attack on Monongalia Health System gave unauthorized individuals access to email accounts containing 398,164 records.
8 of the largest breaches of the month involved compromised email accounts, two of which were business email compromise attacks where accounts were accessed through a phishing campaign and then used to send requests for changes to bank account information for upcoming payments.
Throughout 2021, hacking and other IT incidents have dominated the breach reports and December was no different. 82.14% of the breaches reported in December were hacking/IT incidents, and those breaches accounted for 91.84% of the records breached in December – 2,711,080 records. The average breach size was 58,937 records and the median breach size was 4,563 records. The largest hacking incident resulted in the exposure of the protected health information of 750,050 individuals.
The number of unauthorized access and disclosure incidents has been much lower in 2021 than in previous years. In December there were only 5 reported unauthorized access/disclosure incidents involving 234,476 records. The average breach size was 46,895 records and the median breach size was 4,109 records.
There were two reported cases of the loss of paper/films containing the PHI of 3,081 individuals and two cases of theft of paper/films containing the PHI of 2,129 individuals. There was also one breach involving the improper disposal of a portable electronic device containing the ePHI of 934 patients.
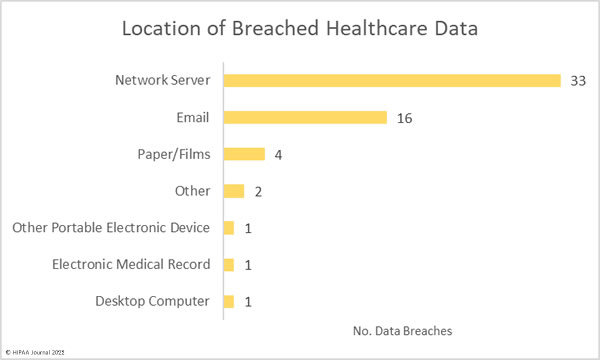
As the chart below shows, the most common location of breached PHI was network servers, followed by email accounts.
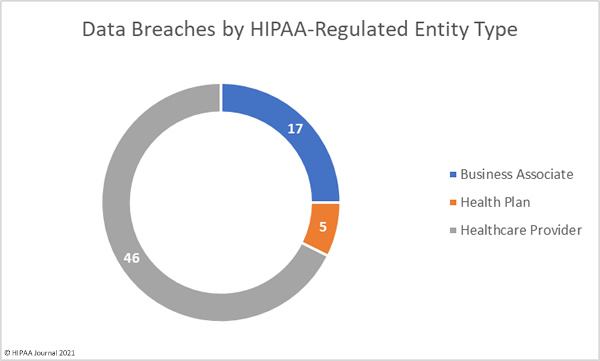
HIPAA Regulated Entities Reporting Data Breaches in December 2021
Healthcare providers suffered the most data breaches in December, with 36 breaches reported. There were 11 breaches reported by health plans, and 9 breaches reported by business associates. Six breaches were reported by healthcare providers (3) and health plans (3) that occurred at business associates. The adjusted figures are shown in the pie chart below.
December 2021 Healthcare Data Breaches by U.S. State
Illinois was the worst affected state with 11 data breaches, four of which were reported by the accountancy firm Bansley and Kiener and related to the same incident – A ransomware attack that occurred in December 2020. the firm is now facing a lawsuit over the incident and the late notification to affected individuals – 12 months after the attack was discovered.
| State | Number of Breaches |
| Illinois | 11 |
| Indiana | 5 |
| Florida, Oklahoma, and Texas | 4 |
| Arizona | 3 |
| California, Georgia, Kansas, Michigan, New York, Oregon, Utah, and Virginia | 2 |
| Alabama, Colorado, Kentucky, Maryland, North Carolina, Rhode Island, Wisconsin, West Virginia, and Wyoming | 1 |
HIPAA Enforcement Activity in December 2021
There were no further HIPAA penalties imposed by the HHS’ Office for Civil Rights in December. The year closed with a total of 14 financial penalties paid to OCR to resolve violations of the HIPAA Rules. 13 of the cases were settled with OCR, and one civil monetary penalty was imposed. 12 of the OCR enforcement actions were for violations of the HIPAA Right of Access.
The New Jersey Attorney General imposed a $425,000 financial penalty on Regional Cancer Care Associates, which covered three separate Hackensack healthcare providers – Regional Cancer Care Associates LLC, RCCA MSO LLC, and RCCA MD LLC – that operate healthcare facilities in 30 locations in Connecticut, New Jersey, and Maryland.
The New Jersey Attorney General and the New Jersey Division of Consumer Affairs investigated a breach of the email accounts of several employees between April and June 2019 involving the protected health information of 105,000 individuals and a subsequent breach when the breach notification letters were sent to affected individuals’ next of kin in error.
The companies were alleged to have violated HIPAA and the Consumer Fraud Act by failing to ensure the confidentiality, integrity, and availability of patient data, failing to protect against reasonably anticipated threats to the security/integrity of patient data, a failure to implement security measures to reduce risks and vulnerabilities to an acceptable level, the failure to conduct an accurate and comprehensive risk assessment, and the lack of a security awareness and training program for all members of its workforce. The case was settled with no admission of liability. There were 4 HIPAA enforcement actions by state attorneys general in 2021. New Jersey was involved in 3 of those enforcement actions.
The post December 2021 Healthcare Data Breach Report appeared first on HIPAA Journal.