2021 was a challenging year for healthcare organizations. Not only was the industry on the frontline in the fight against COVID-19, hackers who took advantage of overrun hospitals to steal data and conduct ransomware attacks.
The 2021 Breach Barometer Report from Protenus shows the extent to which the healthcare industry suffered from cyberattacks and other breaches in 2020. The report is based on 758 healthcare data breaches that were reported to the HHS’ Office for Civil Rights or announced via the media and other sources in 2020, with the data for the report provided by databreaches.net.
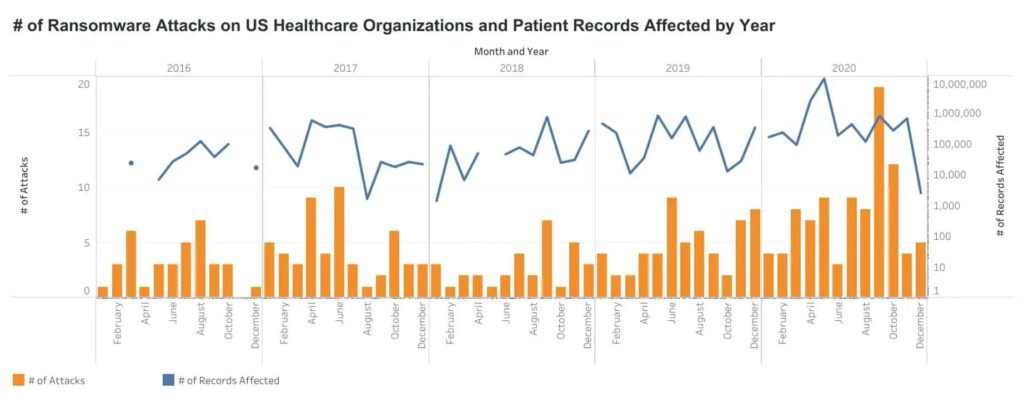
The number of data breaches has continued to rise every year since 2016 when Protenus started publishing its annual healthcare breach report. 2020 saw the largest annual increase in breaches with 30% more breaches occurring than 2019. Data was obtained on 609 of those incidents, across which 40,735,428 patient and health plan members were affected. 2020 was the second consecutive year that saw more than 40 million healthcare records exposed or compromised.
Healthcare Hacking Incidents Increased by 42% in 2020
Healthcare hacking incidents increased by 42% in 2020, continuing a 5-year trend that has seen hacking incidents increase each year. 470 incidents were classed as hacking-related breaches, which accounted for 62% of all breaches in the year. 31,080,823 healthcare records were compromised in the 277 incidents where the number of affected individuals is known. Many of the 2020 hacking incidents involved the use of ransomware. Ransomware attacks increased considerably in 2020, with more than double the number of ransomware attacks on healthcare organizations than in 2019.
Surge in Insider Data Breaches in 2020
There has been a four-year decline in insider breaches, but the Protenus report shows insider data breaches increased in 2020. More than 8.5 million records were exposed or compromised in those incidents – more than double the number of breached records by insiders as 2019. In fact, more records were breached by insiders in 2020 than in 2017, 2018, and 2019 combined. In 2020, 1 in 5 data breaches was an insider incident.
Insider breaches include insider errors and insider wrongdoing. 96 breaches involved insider error in 2020, of which data was obtained for 74 of the incidents. There were 45 cases of insider wrongdoing, with data obtained for 30 of the incidents. Errors by employees resulted in the exposure of the protected health information of at least 7,673,363 individuals and insider wrongdoing incidents resulted in the exposure/theft of at least 241,128 records.
Business Associates Often Involved
The number of data breaches involving business associates increased in 2020, with 12% of all breaches having at least some business associate involvement. Business associate breaches resulted in the exposure or theft of more than 24 million patient records, with 55% of all hacking incidents having some business associate involvement along with 25% of insider error incidents. The number of breaches involving business associates could be considerably higher as the researchers were unable to accurately determine if business associates were involved in many of the breaches.
Data Breaches Discovered Faster but Breach Reporting Slower
In 2020 it took an average of 187 days from the breach occurring to discovery by the breached entity, which is a considerable improvement on the 224-day average discovery time in 2019. In 2020, the median discovery time was just 15 days. However, there was considerable variation in discovery times, from almost immediately in some cases to several years after the breach in others.
Reporting on data breaches was slower than in 2019, with the average time for reporting a breach increasing from 80 days in 2019 to 85 days in 2020, with a median time of 60 days – the maximum time allowed for reporting a breach by the HIPAA Breach Notification Rule. The figures were based on just 339 out of the 758 breaches due to a lack of data.
“The current climate has increased risk for health systems as a new trend emerged of at least two data breaches per day, a troubling sign of the continuing vulnerability of patient information, heightened by the pandemic,” explained Protenus in the report. “Healthcare organizations need to leverage technology that allows organizations to maintain compliance priorities in a resource-constrained environment. Hospitals can’t afford the costs often associated with these incidents, as more than three dozen hospitals have filed bankruptcy over the last several months. Non-compliance is not an option.”
The post 2020 Saw Major Increase in Healthcare Hacking Incidents and Insider Breaches appeared first on HIPAA Journal.