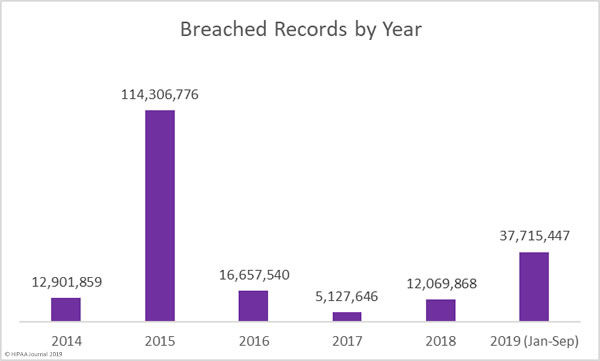
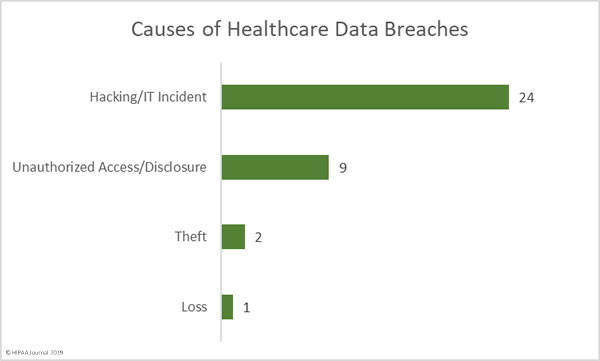
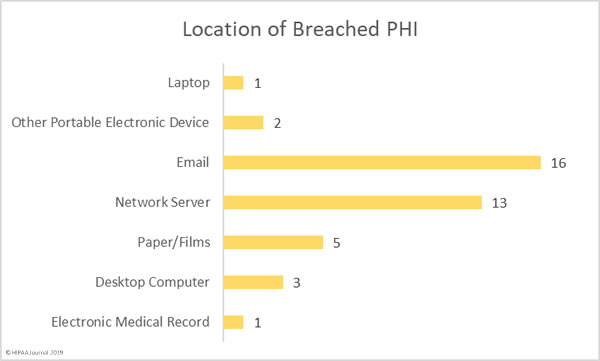
A recent study conducted by the password manager provider LastPass has revealed only 57% of businesses use multi-factor authentication, even though it is one of the best ways of ensuring stolen credentials cannot be used to gain access to email accounts and corporate networks.
Multi-factor authentication requires a second factor to authenticate users in addition to a password. In the event of credentials being stolen, via a phishing attack for example, they could not be used to access an account unless the attacker also has an additional authentication factor – A one-time code sent to a mobile phone or a token, for example.
The study, which was conducted on 47,000 businesses, showed use of multi-factor authentication has increased by 12% since last year. According to the report, 95% of companies that have implemented multi-factor authentication use a software-based system such as a mobile app. 4% use a hardware-based multi-factor authentication solution, and 1% use biometrics such as a fingerprint scan. Software-based solutions are usually the most cost-effective to implement which accounts for the high percentage of businesses that use this MFA method.
The threat from phishing can be reduced through anti-phishing solutions such as spam filters and susceptibility to phishing attacks can be reduced by providing user security awareness training and conducting phishing simulation exercises. Multi-factor authentication should also be implemented as an additional security layer to protect against phishing attacks.
According to Microsoft’s Director of Identity Security, Alex Weinert, companies that implement multi-factor authentication are 99.9% less likely to be compromised than companies that do not use MFA. Considering how effective MFA can be at preventing data breaches, it is surprising that Microsoft’s figures show fewer than 10% of enterprise users per month use MFA on their accounts.
While MFA can certainly reduce the risk of a data breach, it can give companies a false sense of security. Multi-factor authentication is not infallible and should not be seen as a substitute for end user training on social engineering and phishing attacks.
Knowledge-based MFA authentication can be bypassed by obtaining information via social engineering scams and since MFA tokens are stored somewhere, they could be stolen and be used by attackers to access resources. MFA tokens can also be manipulated through techniques such as SIM swapping. The FTC has recently issued guidance on SIM swapping following an increase in attacks.
As the number of organizations using multi-factor authentication has increased, so too have attacks that bypass MFA. The rise in attacks prompted the FBI to warn businesses that they should not rely on MFA to secure their accounts. In a Private Industry Notification issued in September, the FBI explained that cybercriminals are managing to bypass multi-factor authentication using a variety of different methods.
The advice of the FBI is to use biometric methods of authenticating users rather than software-based MFA solutions, tokens, or one-time codes. Biometric means of authenticating users is the most secure MFA method, provided that all biometric information used for authentication is stored securely.
The post 57% Rely on Multi-Factor Authentication to Improve Security but MFA is Not Infallible appeared first on HIPAA Journal.