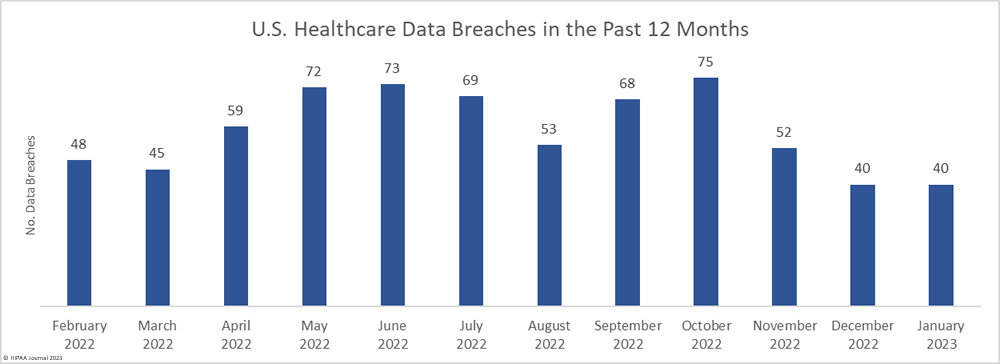
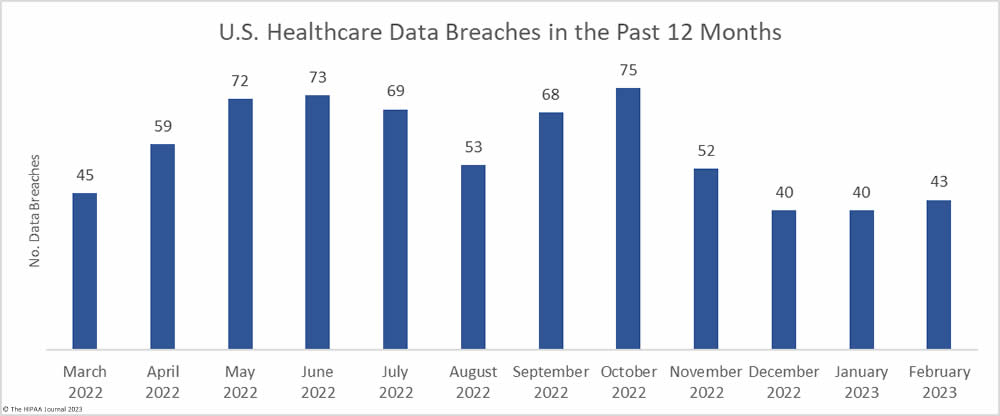
The number of healthcare data breaches reported over the past three months has remained fairly flat, with only a small uptick in breaches in February, which saw 43 data breaches of 500 or more records reported to the HHS’ Office for Civil Rights (OCR), well below the 12-month average of 57.4 reported breaches a month. An average of 41 data breaches have been reported each month over the past 3 months, compared to an average of 50.6 breaches per month for the corresponding period last year.
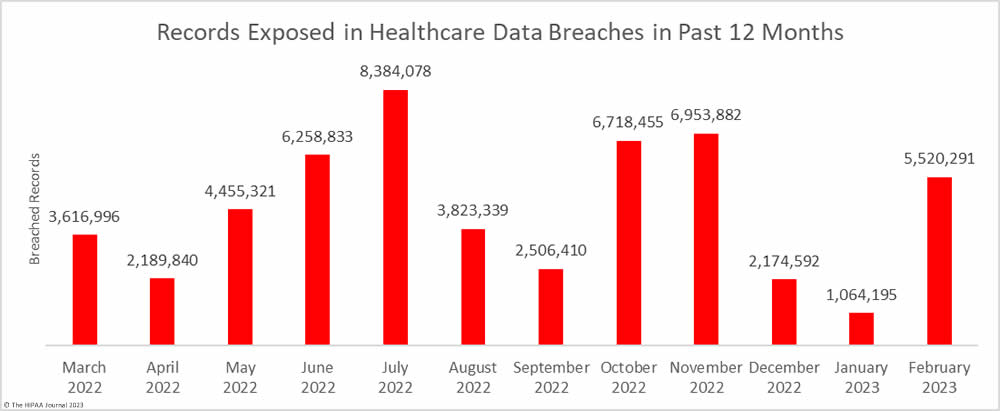
The downward trend in breached records did not last long. There was a sizeable month-over-month increase in breached records, jumping by 418.7% to 5,520,291 records. February was well above the monthly average of 4,472,186 breached records a month, with the high total largely due to a single breach that affected more than 3.3 million individuals.
Largest Healthcare Data Breaches Reported in February 2023
17 healthcare data breaches of 10,000 or more records were reported in February, all of which were hacking incidents. The largest data breach affected 3,300,638 patients of 4 medical groups in California that are part of the Heritage Provider Network – Regal Medical Group, Inc.; Lakeside Medical Organization, A Medical Group, Inc.; ADOC Acquisition Co., A Medical Group Inc.; & Greater Covina Medical Group, Inc. This was a ransomware attack with confirmed data theft and was, at the time of reporting, the largest data healthcare data breach of the year. That record did not stand for long, as a 4.4 million-record breach was reported this month (Independent Living Systems).
Hacking incidents were reported by CentraState Healthcare System in New York (617,901 records), Cardiovascular Associates in Alabama (441,640 records), and the Florida-based revenue cycle management company, Revenetics (250,918 records), all of which saw sensitive data exfiltrated. It is unclear whether these incidents were ransomware or extortion attacks. An email account breach at Highmark Inc. rounds out the top five. That incident was reported to the HHS’ Office for Civil Rights as two separate breaches, affecting 239,039 and 36,600 individuals -275,639 in total. The breach occurred as a result of an employee clicking a link in a phishing email.
The full list of 10,000+ record data breaches and their causes are detailed in the table below.
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Business Associate Present |
| Regal Medical Group, Inc., Lakeside Medical Organization, A Medical Group, Inc., ADOC Acquisition Co., A Medical Group Inc. & Greater Covina Medical Group, Inc. |
CA |
Healthcare Provider |
3,300,638 |
Ransomware attack (data theft confirmed) |
| CentraState Healthcare System, Inc. |
NJ |
Healthcare Provider |
617,901 |
Hacking incident (data theft confirmed) |
| Cardiovascular Associates |
AL |
Healthcare Provider |
441,640 |
Hacking incident (data theft confirmed) |
| Reventics, LLC |
FL |
Business Associate |
250,918 |
Hacking incident (data theft confirmed) |
| Highmark Inc |
PA |
Health Plan |
239,039 |
Phishing attack |
| 90 Degree Benefits, Inc. |
WI |
Business Associate |
175,000 |
Hacking incident |
| Hutchinson Clinic, P.A. |
KS |
Healthcare Provider |
100,000 |
Hacking incident |
| Lawrence General Hospital |
MA |
Healthcare Provider |
76,571 |
Hacking incident |
| Sharp Healthcare |
CA |
Healthcare Provider |
62,777 |
Hacked web server (data theft confirmed) |
| Rise Interactive Media & Analytics, LLC |
IL |
Business Associate |
54,509 |
Hacking incident |
| Highmark Inc |
PA |
Business Associate |
36,600 |
Phishing attack |
| Teijin Automotive Technologies Welfare Plan |
MI |
Health Plan |
25,464 |
Ransomware attack – Access gained through phishing |
| Evergreen Treatment Services |
WA |
Healthcare Provider |
21,325 |
Hacking incident |
| Aloha Nursing Rehab Centre |
HI |
Healthcare Provider |
20,216 |
Hacking incident (data theft confirmed) |
| NR Pennsylvania Associates, LLC |
PA |
Healthcare Provider |
14,335 |
Hacking incident (data theft confirmed) |
| Intelligent Business Solutions |
NC |
Business Associate |
11,595 |
Ransomware attack |
| Arizona Health Advantage, Inc. dba Arizona Priority Care; AZPC Clinics, LLC; and health plans for which APC has executed a BAA |
AZ |
Healthcare Provider |
10,978 |
Ransomware attack |
Causes of Healthcare Data Breaches in February 2023
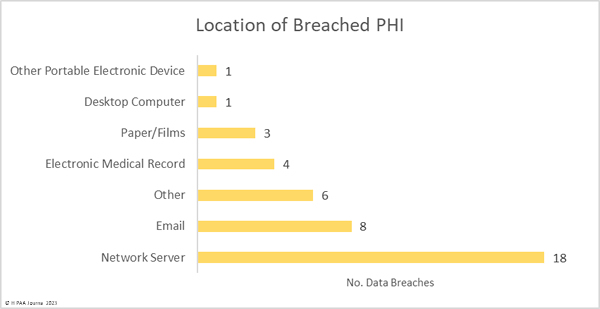
Hacking and other IT incidents dominated the breach reports in February with 33 such incidents reported, accounting for 76.7% of all breaches reported in February. Across those incidents, the records of 5,497,797 individuals were exposed or stolen – 99.59% of the breached records in February. The average breach size was 166,600 records and the median breach size was 10,978 records.
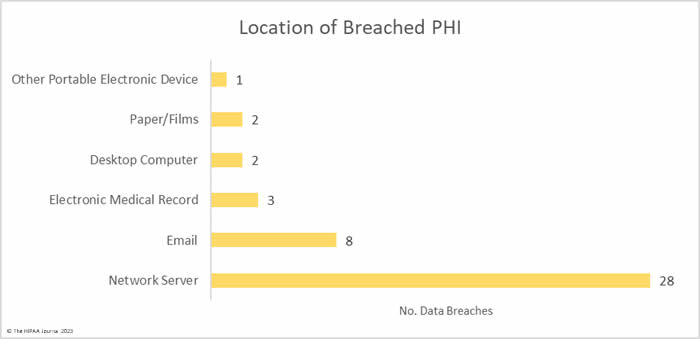
There were 8 unauthorized access/disclosure incidents reported involving a total of 13,950 records. The average breach size was 1,744 records and the median breach size was 689 records. One of the incidents – reported by Asante – involved a physician accessing the records of patients when there was no treatment relationship. The unauthorized access occurred for 9 years before it was detected, during which time the records of 8,834 patients were impermissibly viewed. Incidents such as this show why it is important to maintain logs of medical record access and to review those logs regularly, ideally automating the process using a monitoring and alerting system.

One theft incident was reported involving a portable electronic device containing the PHI of 986 patients and one incident involved the improper disposal of paper records that contained the PHI of 7,558 patients.
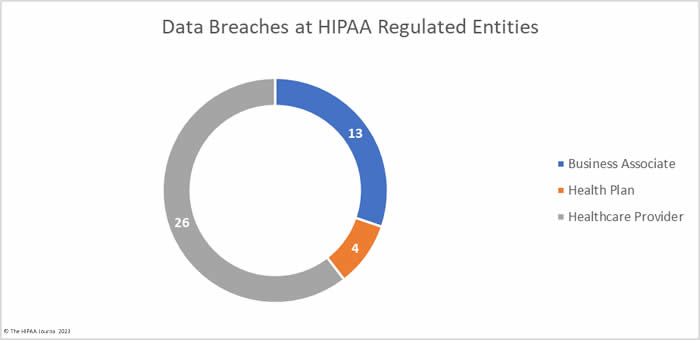
What HIPAA-Regulated Entities were Affected?
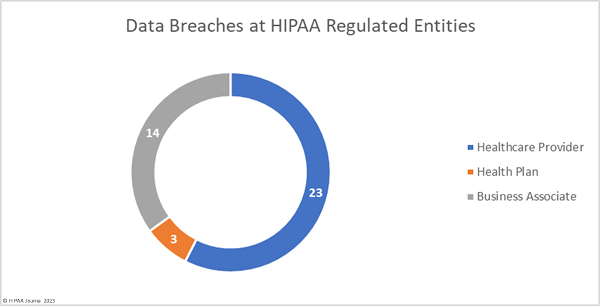
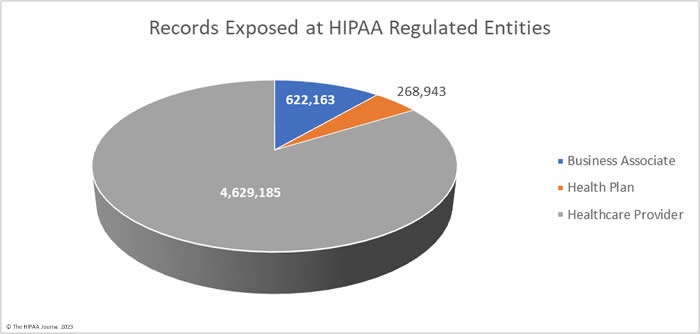
Healthcare providers were the worst affected HIPAA-regulated entity in February, with 31 data breaches of 500 or more records. Seven data breaches were reported by business associates and five were reported by health plans. When data breaches involve business associates, they are often reported by the covered entity. In February, 6 data breaches involved business associates but were reported by the affected healthcare providers and health plans. The two charts are based on where the breach occurred rather than who reported it.
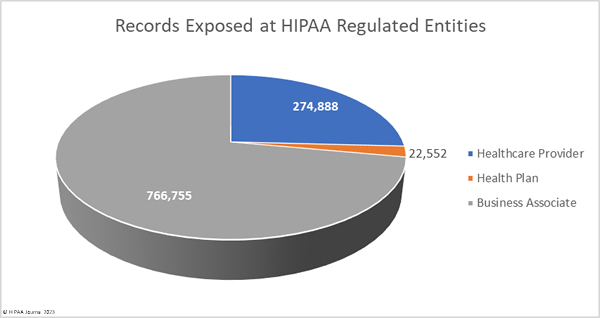
The average healthcare provider breach exposed 178,046 records (median: 3,061 records), the average health plan data breach exposed 67,236 records (median: 3,909 records), and the average business associate data breach involved 47,859 records (median: 8,500 records).
Where Did the Breaches Occur?
Data breaches were reported by HIPAA-covered entities and business associates in 28 states, with California being the worst affected state with 4 breaches reported in February.
| State |
Breaches |
| California |
4 |
| Pennsylvania & Texas |
3 |
| Arizona, Illinois, Kansas, Massachusetts, New Jersey, Oregon, Virginia & Washington |
2 |
| Alabama, Colorado, Connecticut, Florida, Georgia, Hawaii, Iowa, Maryland, Michigan, New Hampshire, New Mexico, North Carolina, Rhode Island, Tennessee, Utah, Wisconsin & Wyoming |
1 |
HIPAA Enforcement Activity in February 2023
The HHS’ Office for Civil Rights announced one enforcement action in February to resolve alleged violations of the HIPAA Rules. OCR investigated Banner Health over a 2016 breach of the protected health information of 2.81 million individuals and identified multiple potential HIPAA violations related to risk analyses, system activity reviews, verification of identity for access to PHI, and technical safeguards. Banner Health agreed to settle the case and paid a $1,125,000 financial penalty.
DNA Diagnostics Center was investigated by the Attorneys General in Pennsylvania and Ohio after a reported breach of the personal and health information of 45,600 state residents. The investigation determined there was a lack of safeguards, a failure to update its asset inventory, and a failure to disable or remove assets that were not used for business purposes. While these failures would have been HIPAA violations, the settlement resolved violations of state laws. DNA Diagnostics Center paid a financial penalty of $400,000, which was split equally between the two states.
In February, the Federal Trade Commission (FTC) announced its first-ever settlement to resolve a violation of the FTC Health Breach Notification Rule. While the Rule has been in effect for a decade, the FTC has never enforced it. That has now changed. The FTC stated last year that it would be holding non-HIPAA-covered entities accountable for impermissible disclosures of health information and breach notification failures. GoodRx Holdings Inc. was found to have used tracking technologies on its website that resulted in unauthorized disclosures of personal and health information to Facebook, Google, and other third parties and failed to issue notifications to affected individuals. The allegations were settled and GoodRx paid a $1,500,000 financial penalty.
The post February 2023 Healthcare Data Breach Report appeared first on HIPAA Journal.