The topic of AI in healthcare often gets mixed reactions. While some people are firm believers in the benefits of AI in healthcare and the considerable benefits to patients, others have concerns about the ethics of AI in healthcare and there is considerable apprehension about the use of AI in healthcare attributable to a lack of knowledge about AI. In this article, we will explain what artificial intelligence is, the benefits of AI in healthcare, and how concerns about the ethics of AI in healthcare need to be overcome.
What is Artificial Intelligence (AI)?
One of the reasons why some people approach the topic of AI in healthcare with a degree of apprehension is that different sources offer different definitions of AI. It is also the case that some sources confuse AI with Machine Learning (ML), which strictly speaking is a subset of AI. To quote Microsoft’s definitions of the two terms:
Artificial intelligence is the capability of a computer system to mimic human cognitive functions such as learning and problem-solving. Through AI, a computer system uses math and logic to simulate the reasoning that people use to learn from new information and make decisions.
Machine learning is an application of AI. It is the process of using mathematical models of data to help a computer learn without direct instruction. This enables a computer system to continue learning and improving on its own, based on experience.
Therefore, while AI and ML are closely connected, they are not the same. Generally, a computer system uses AI to think like a human and perform tasks on its own, whereas ML is how a computer system develops its intelligence. Importantly, many of the concerns related to AI in healthcare revolve around how computer systems develop Artificial Intelligence and their capabilities to learn and make decisions without human instruction.
How Computer Systems Develop Artificial Intelligence
There are many different standard and hybrid techniques that determine how computer systems develop Artificial Intelligence. Generally, most follow the same two-stage process:
Supervised Learning
Most new AI systems start with a supervised learning process in which labeled datasets with known outcomes are fed into a system to train an algorithm on how to classify data. The outcomes produced by the system are then weighted to match the previously known outcomes. Often, this stage is followed by “semi-supervised learning” in which labeled datasets guide the algorithm as it classifies unlabeled datasets and predicts outcomes for the unlabeled data.
Unsupervised Learning
In unsupervised learning, the trained algorithm has to detect underlying patterns and relationships in never-before-seen unlabeled data in order to produce accurate outcomes. With unsupervised learning, it is important to remember that the aim is to make sense of data in the context of a specific question. How the answer is determined will depend on how the algorithm has been trained and weighted during the supervised and semi-supervised stages.
While this explanation might fail to reassure those who are concerned or apprehensive about AI – because “answers” are dependent on how the algorithm has been trained, the quality of data used to train the algorithm, how the output is weighted, and what the question is that the algorithm is trying to answer – artificial intelligence has in fact been present in many areas of everyday life for several years. For example:
- Most people have played a video game against an AI-driven computer
- AI is used by the finance industry to detect potential credit card fraud
- The security industry uses AI to monitor multiple clusters of CCTV systems
- Netflix “because you watched” recommendations are produced by AI
- AI produces the routes recommended by Google Maps and other travel apps
- Many email spam filters and antivirus software solutions are fine-tuned by AI
But, what about AI in healthcare? How is that being used, who is using it, and what are the benefits? Additionally, are concerns about the ethics of AI in healthcare justified; and, if so, what can be done to overcome the concerns? These questions are easier to answer with an understanding of what AI is and how computer systems develop artificial intelligence.
Examples of AI in Healthcare
AI in healthcare is an umbrella term for all the many different ML algorithms and other cognitive technologies that are used in the healthcare industry. Some algorithms are more advanced than others, most have been designed to answer specific questions, and – even when the specific question is the same – some have been trained or weighted differently from others.
Consequently, there are many examples of AI in healthcare from patient-orientated AI such as chatbots that can listen to a patient’s symptoms and health concerns, to pharma-orientated AI that can help bring life-saving treatments to market faster. Between either end of the healthcare spectrum, there are many more examples of AI in healthcare:
Medical Imaging
Using computer vision to identify health conditions in medical images is quickly becoming a primary use for AI-driven technology. More advanced algorithms can distinguish tumors from lesions and other diseases – resulting in more accurate diagnoses, faster administration of treatments, and better patient outcomes.
Precision Medicine
Similarly, computer systems that have been trained on precision medicine can develop medicinal or behavioral regimes specifically tailored to each patient depending on their condition, metabolic profile, microbiome composition, diet, lifestyle, sleep patterns, and many more data points collected and analyzed over years.
Physician Guidance
While robots performing major surgeries may still be a science fiction fantasy, some AI technologies have been developed that can guide physicians during minimally invasive surgical procedures via automated workflows and decision support. Most often, these technologies are used in treating strokes and heart conditions and for endovascular procedures.
Detecting Patient Deterioration
In post-acute environments, healthcare providers dedicate a lot of resources to checking vital signs to identify postoperative adverse events. AI-enabled tools can help care teams by calculating early warning scores that detect patient deterioration due to events such as respiratory failure or cardiac arrest – thus enabling more rapid responses.
Predictive Equipment Maintenance
As well as detecting patient deterioration, AI can be deployed to predict when medical equipment is in need of maintenance. Through remote sensing, AI can monitor the performance of medical hardware to proactively identify when it may need maintenance or replacement – reducing downtime, preventing avoidable interruptions to clinical practice, and mitigating patient delays.
Automated Resource Allocation
A major administrative challenge for large healthcare providers is patient flow and resource allocation. The failure to have the right resources in the right place at the right time puts patients at risk and increases unnecessary bed occupancy. However, using AI to identify patterns from real-time and historical data enables providers to optimize flow management efficiency.
Healthcare AI Companies
Compiling a list of healthcare AI companies is difficult because companies face multiple challenges in developing AI solutions that demonstrate real-world performance, meet medical needs, and address regulatory requirements. Consequently, many start-ups fail to make an impact in the healthcare industry and redirect their talents elsewhere. Some of those currently making an impact include:
PathAI
PathAI was founded with the aim of developing AI technology that could reduce error rates in pathology. The company’s AISight pathology platform was developed, trained, and validated using more than fifteen million annotations, and PathAI is now in the process of developing diagnostic solutions for gastroenterologists, dermatologists, oncologists, urologists, and gynecologists.
Regard
Unlike patient-orientated AI which can help users identify the causes of symptoms, Regard is an end-to-end AI solution for physicians that analyzes and synthesizes patient data, recommends diagnoses, and automates note-taking. By mitigating the risk of misdiagnoses and tackling repetitive tasks, physicians have more time available to see more patients and maximize revenues.
Freenome
Freenome is one of a number of healthcare AI companies that combine computational biology and machine learning to support better cancer management through early detection and precision intervention. Freenome’s AI platform can be deployed at general screenings or used to detect signs of cancer in diagnostic and blood tests.
Beth Israel Lahey Health
The Beth Israel Deaconess Medical Center – also known as Harvard University’s teaching hospital – used 25,000 images of blood samples to develop an AI-enhanced microscope that can detect harmful bacteria such as staphylococcus and E. coli much faster than is possible using manual scanning. To date, the microscopes have achieved a 95% accuracy rate.
VirtuSense
VirtuSense uses AI sensors to track inpatients’ movements so that providers and caregivers can be notified of potential falls. The company’s product range includes VSTAlert, which can predict when a patient intends to stand up to alert care reams, and VST Balance, which employs AI and machine vision to analyze a person’s risk of falling within the next year.
Benefits of AI in Healthcare
The above examples of AI in healthcare and technologies developed by healthcare AI companies focus on the “in-house” benefits of AI in healthcare inasmuch as they help deliver accurate diagnoses and treatment plans, prevent adverse events and accidents, and improve patient flow management. Outside of hospital environments, there are many further benefits of AI in healthcare.
From a patient’s perspective, AI technologies not only improve outcomes and help prevent adverse events in hospitals but can also enhance the remote patient experience. Advocates of AI in healthcare see AI as a way of providing convenient access to medical advice in the home, increasing patient engagement, and empowering patients to take more responsibility for their health and well-being.
Further benefits of AI in healthcare relate to how quickly pharmaceutical companies can bring new drugs to markets. Drug development processes can be significantly accelerated with AI technologies that quickly extract meaningful information from large datasets to predict harmful interactions with existing drugs, improve the quality of clinical trials, and reduce time to approval.
One recent example of the benefits of AI in healthcare is how AI was used during the COVID-19 pandemic to detect outbreaks, facilitate diagnoses, and accelerate gene sequencing. It is hoped that, as a tool for public health, AI can be used in the future to predict and track the spread of other infectious diseases by analyzing data from government, healthcare, and other sources.
Ethics of AI in Healthcare
According to a survey conducted by Dataiku in 2020, concern about the ethics of AI in healthcare is the primary organizational challenge stalling the adoption of AI in healthcare environments. Although specific concerns differ by organization, the concerns can generally be categorized as informed consent to use data, safety and transparency, algorithmic fairness, and data privacy.
These concerns are not unique to the United States nor to the healthcare industry. Governments and regulatory agencies across the world have struggled to resolve this challenge – with many implementing rules and regulations to govern how AI is used. In the United States, a patchwork of state and federal laws partially addresses the challenge, but many concerns remain.
To help support governments and regulatory agencies pass fair and consistent legislation, in 2021 the World Health Organization published guidance on the “Ethics and Governance of Artificial Intelligence for Health”. This comprehensive publication endorses six key ethical principles for consideration by governments, developers, companies, and society as a whole:
- Protect human autonomy
- Promote human well-being, safety, and the public interest
- Ensure transparency, explainability, and intelligibility
- Foster responsibility and accountability
- Ensure inclusiveness and equity
- Promote AI that is responsive and sustainable
Although political influences have resulted in the United States AI strategy shifting towards a market-orientated approach, the National Defense Authorization Act 2021 instructed the National Institute of Standards and Technology (NIST) to develop a framework for trustworthy AI systems that establishes common definitions and characterizations for aspects of trustworthiness.
With the exception of protecting human autonomy, the five remaining key ethical principles endorsed by the World Health Organization likely will be incorporated into the framework according to NIST’s latest report to Congress. If approved by Congress, the NIST AI standards could resolve many of the concerns about the ethics of AI in healthcare.
How NIST Standards Could Accelerate AI Adoption in Healthcare
In January 2021, a HITECH Act update came into effect – an amendment that gave the HHS’ Office for Civil Rights enforcement discretion when investigating data breaches if the breached organization could demonstrate twelve month’s continuous compliance with “standards, guidelines, best practices, methodologies, procedures, and processes developed under section 2(c)(15) of the NIST Act” or a similar Act.
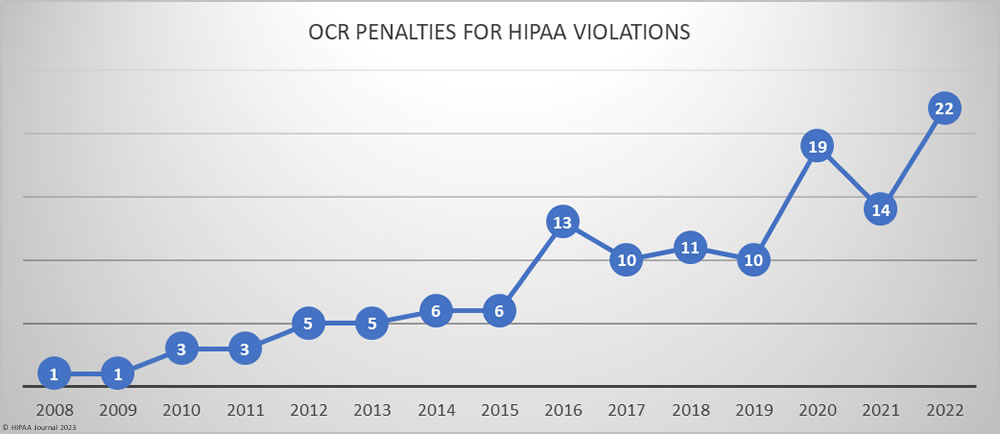
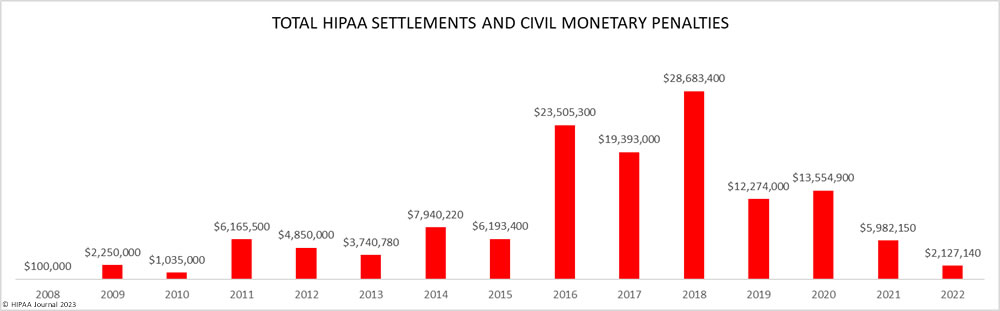
There is no evidence that HIPAA Covered Entities and Business Associates took their compliance obligations any more seriously after the enactment of the HITECH Act update, but it is noticeable that – despite a significant increase in the number of financial penalties issued by HHS’ Office for Civil Rights in the past two years – only four have been for violations of the Security Rule.
If there are amendments to the NIST Act to incorporate AI standards, and if a law is passed giving HHS’ Office for Civil Rights enforcement discretion when the standards are applied in healthcare organizations, this could accelerate AI adoption in healthcare as not only would it resolve many of the concerns about the ethics of AI in healthcare, it would also resolve the second highest challenge to the adoption of AI in healthcare (according to Dataiku) – the lack of regulatory guidance.
The Future of AI in Healthcare
The future of AI in healthcare is unclear if concerns about the ethics of AI in healthcare and the lack of regulatory guidance are allowed to continue. If the situation remains as it is, AI will continue to be incorporated into healthcare processes in piecemeal stages – which will continue to add value to healthcare operations and improve the patient experience but may result in inequalities that could make the wider adoption of AI in healthcare much more difficult in the future.
Alternatively, and notwithstanding that AI technologies are improving and becoming more sophisticated all the time, federal agencies – including the HHS – could introduce temporary guidance on the use of AI until such time as effective standards are developed. This would give healthcare organizations more confidence to adopt AI technologies with benefits for patients, organizations, and public health in general.
The post AI in Healthcare appeared first on HIPAA Journal.