October was the worst month of the year to date for healthcare data breaches, with 71 breaches reported and more than 6 million records breached. The first half of the year was looking like 2022 would see a reduction in healthcare data breaches; however, that is looking increasingly unlikely. In 2021, 714 data breaches of 500 or more records were reported to the HHS’ Office for Civil Rights. 594 data breaches were reported between January 1 and October 31, and with an average of 60 data breaches being reported each month, 2022 looks set to end with a similarly high number.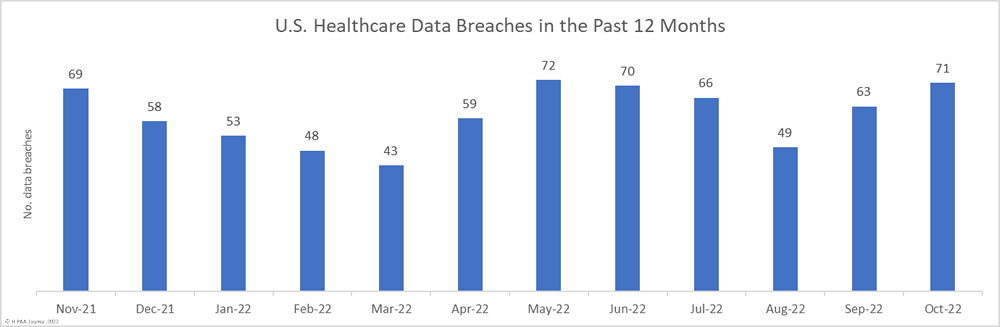
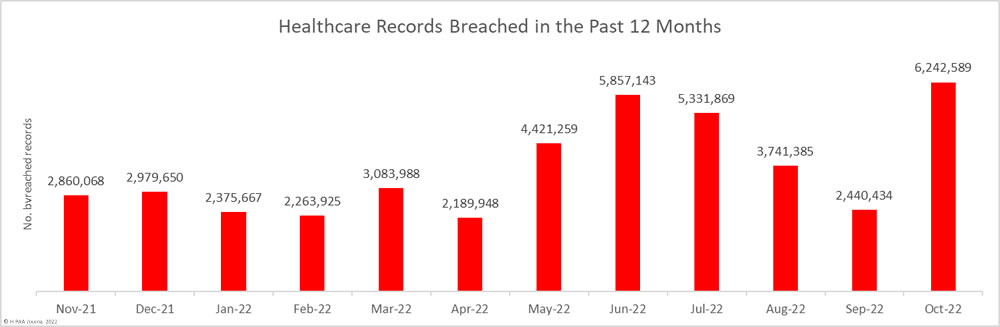
Across the 71 reported breaches, the protected health information of 6,242,589 individuals was exposed or impermissibly disclosed, with around half of that total coming from a single breach. So far this year, the records of 37,948,207 individuals have been exposed or impermissibly disclosed.
Largest Healthcare Data Breaches Reported in October
In October, 28 data breaches of 10,000 or more records were reported by HIPAA-regulated entities. The largest healthcare data breach reported in October – by some distance – was due to the use of Meta Pixel code on the website and patient portal of Advocate Aurora Health, which resulted in the impermissible disclosure of the PHI of up to 3 million patients to Meta/Facebook. Advocate Aurora Health was not alone. WakeMed Health and Hospitals reported a similar breach involving the PHI of 495,808 patients. Dozens of other healthcare providers have also used the code on their websites and lawsuits are mounting. Attorneys for Meta claim the company does not collect healthcare data without consent; however, U.S. District Judge William Orrick, who is presiding over a consolidated class action lawsuit against Meta over these impermissible disclosures, has expressed skepticism about those claims.
The data breach at SightCare Inc was due to a hacking incident at business associate USV Optical, a subsidiary of U.S. Vision, which also affected Nationwide Optometry. More than 700,000 records were compromised in the incident. The third largest breach of the month occurred at CorrectCare Integrated Health, Inc, which provides administrative services to healthcare providers that serve correctional facilities. A database was exposed over the Internet as a result of a misconfiguration that resulted in the exposure of the PHI of at least 612,490 inmates at correctional facilities across the country.
Two more eye care providers confirmed in October that they had been affected by the ransomware attack on their EHR vendor, Eye Care Leaders. The records of at least 3,649,470 patients are now known to have been compromised in that attack.
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Description |
| Advocate Aurora Health |
WI |
Healthcare Provider |
3,000,000 |
Unauthorized Access/Disclosure |
Website Code Passed Patient Information to Meta/Facebook |
| SightCare, Inc. |
AZ |
Health Plan |
637,999 |
Hacking/IT Incident |
Hacking incident at business associate (USV Optical) |
| OakBend Medical Center / OakBend Medical Group |
TX |
Healthcare Provider |
500,000 |
Hacking/IT Incident |
Ransomware attack |
| WakeMed Health and Hospitals |
NC |
Healthcare Provider |
495,808 |
Unauthorized Access/Disclosure |
Website Code Passed Patient Information to Meta/Facebook |
| CorrectCare Integrated Health, Inc. |
KY |
Business Associate |
438,713 |
Unauthorized Access/Disclosure |
Exposure of PHI over the Internet |
| Keystone Health |
PA |
Healthcare Provider |
235,237 |
Hacking/IT Incident |
Hacked network server |
| Louisiana Department of Public Safety and Corrections |
LA |
Healthcare Provider |
85,466 |
Unauthorized Access/Disclosure |
Exposure of PHI over the Internet (CorrectCare Integrated Health) |
| Urology of Greater Atlanta, LLC |
GA |
Healthcare Provider |
79,795 |
Hacking/IT Incident |
Hacking Incident (No information) |
| Nationwide Optometry, PC |
AZ |
Healthcare Provider |
73,073 |
Hacking/IT Incident |
Hacking incident at business associate (USV Optical) |
| Ascension St. Vincent’s Coastal Cardiology |
GA |
Healthcare Provider |
71,227 |
Hacking/IT Incident |
Ransomware attack |
| Valle del Sol, Inc. |
AZ |
Healthcare Provider |
70,268 |
Hacking/IT Incident |
Hacked network server |
| CorrectCare Integrated Health, Inc. |
KY |
Business Associate |
53,496 |
Unauthorized Access/Disclosure |
Exposure of PHI over the Internet |
| FOREFRONT DERMATOLOGY, SC |
WI |
Healthcare Provider |
45,580 |
Theft |
Theft of an unencrypted portable electronic device at a business associate |
| VisionWeb Holdings, LLC |
TX |
Business Associate |
35,900 |
Hacking/IT Incident |
Compromised email accounts |
| University of Michigan/Michigan Medicine |
MI |
Healthcare Provider |
33,857 |
Hacking/IT Incident |
Compromised email accounts (phishing) |
| Aesthetic Dermatology Associates, PC |
PA |
Healthcare Provider |
33,793 |
Hacking/IT Incident |
Hacked network server |
| Choice Health Insurance LLC |
SC |
Business Associate |
32,064 |
Hacking/IT Incident |
Database exposed over the Internet (data theft confirmed) |
| PrimeCare Medical, Inc. |
PA |
Healthcare Provider |
22,254 |
Unauthorized Access/Disclosure |
Exposure of PHI over the Internet (CorrectCare Integrated Health) |
| Administrative Fund of the Detectives’ Endowment Association, Inc., Police Department City of New York |
NY |
Health Plan |
21,544 |
Hacking/IT Incident |
Compromised email accounts (Phishing) |
| Wenco Management, LLC Health and Welfare Benefit Plan |
OH |
Health Plan |
20,526 |
Hacking/IT Incident |
Compromised email accounts |
| Gateway Ambulatory Surgery Center |
NC |
Healthcare Provider |
18,479 |
Hacking/IT Incident |
Compromised email accounts (Phishing) |
| Alain A. Montiel, DDS |
CA |
Healthcare Provider |
17,157 |
Theft |
Theft of an unencrypted laptop |
| St Luke’s Health – Texas |
TX |
Healthcare Provider |
16,906 |
Hacking/IT Incident |
Compromised email accounts at business associate (Adelanto Healthcare Ventures) |
| Lifespire Services, Inc. |
NY |
Healthcare Provider |
15,375 |
Hacking/IT Incident |
Hacked network server |
| HH/Killeen Health System, LLC doing business as Seton Medical Center Harker Heights |
TX |
Healthcare Provider |
15,056 |
Hacking/IT Incident |
Compromised email accounts at an unspecified business associate |
| Massengale Eye Care |
OK |
Healthcare Provider |
15,000 |
Hacking/IT Incident |
Ransomware attack on a business associate (Eye Care Leaders) |
| Wisconsin Department of Health Services |
WI |
Health Plan |
12,358 |
Unauthorized Access/Disclosure |
Compromised email accounts |
| Somnia Pain Mgt of Kentucky |
NY |
Healthcare Provider |
10,848 |
Hacking/IT Incident |
Hacked network server |
Causes of October 2022 Data Breaches
Across all industry sectors, ransomware attacks have decreased slightly this year; however, the healthcare industry continues to be a target for ransomware gangs, with Hive, LockBit 2.0, Lorenz, and the Venus ransomware gangs among those that are attacking healthcare organizations. According to Check Point Research, healthcare was the most targeted industry sector in Q3, 2022, and saw the second-highest percentage increase in attacks out of all industry sectors, with 60% more attacks than in Q3, 2021. The largest confirmed ransomware attack was on OakBend Medical Center, which saw half a million records compromised.
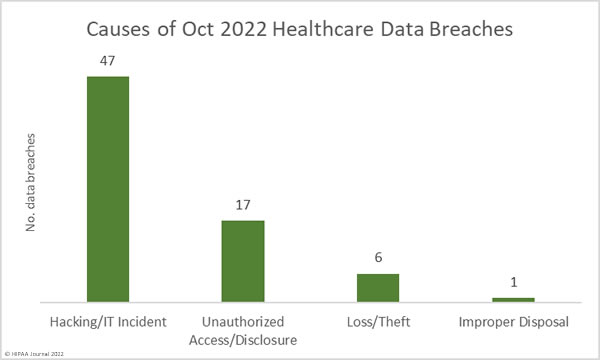
As has been the case for several months, hacking incidents outnumber all other types of data breaches. In October, 47 hacking incidents were reported – 66% of the month’s data breaches – and 2,025,704 records were exposed in those incidents. The average breach size was 43,100 records and the median breach size was 6,594 records. October saw an increase in unauthorized access/disclosure incidents, due in part to the data breach that occurred at CorrectCare Integrated Health that exposed the PHI of inmates of correctional facilities. 7 of the 17 reported unauthorized access/disclosure incidents were due to this incident. Unsurprisingly, given the 3 million-record data breach reported by Advocate Aurora Health, 66% of the breached records were due to unauthorized access/disclosure incidents. 4,145,396 records were compromised in these incidents. The average breach size was 243,847 records and the median breach size was 7,000 records.
There were 6 loss/theft incidents reported in October (4 theft, 2 loss), all but one of which involved portable electronic devices that had not been encrypted. 67,244 records were exposed or stolen across these incidents. The average breach size was 11,207 records and the median breach size was 1,396 records. There was also one incident involving the improper disposal of paperwork that contained the PHI of 4,245 patients.
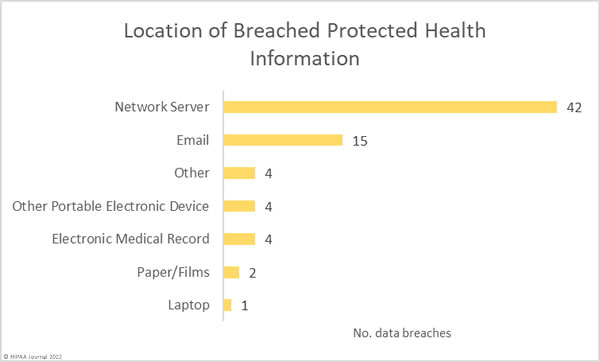
The most common location of breached PHI was network servers due to the high number of hacking incidents. Email accounts are also commonly targeted, with 15 incidents reported in October that involved compromised email accounts. Good password management and multifactor authentication can significantly improve defenses against these attacks, although phishing attacks that bypass MFA are increasing. The increase in these attacks prompted CISA to issue guidance on implementing phishing-resistant MFA this month.
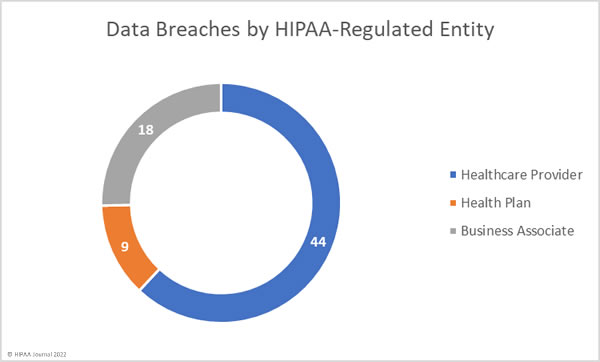
Healthcare Data Breaches by HIPAA-Regulated Entity Type
55 breaches were reported by healthcare providers in October; however, 11 of those data breaches occurred at business associates. 10 data breaches were reported by health plans, with one of those breaches occurring at a business associate. Business associates self-reported 6 breaches. The chart below shows the breaches broken down by where they occurred rather than the entity that reported the data breach.
Healthcare Data Breaches by State
Data breaches of 500 or more records were reported by HIPAA-regulated entities in 30 states, with New York the worst affected state with 11 reported breaches. This was due to a data breach at a New York-based management company that affected multiple anesthesiology service providers.
| State |
Number of Reported Data Breaches |
| New York |
11 |
| Texas & Wisconsin |
5 |
| Florida & New Jersey |
4 |
| Arizona, California, Georgia, Kentucky, North Carolina, Pennsylvania & Virginia |
3 |
| Delaware, Maryland & Oregon |
2 |
| Colorado, Connecticut, Illinois, Indiana, Kansas, Louisiana, Maine, Michigan, Minnesota, Nebraska, New Mexico, Ohio, Oklahoma, South Carolina & Washington |
1 |
HIPAA Enforcement Activity in October
No HIPAA enforcement actions were reported in October by the HHS Office for Civil Rights or State Attorneys general.
The post October 2022 Healthcare Data Breach Report appeared first on HIPAA Journal.





