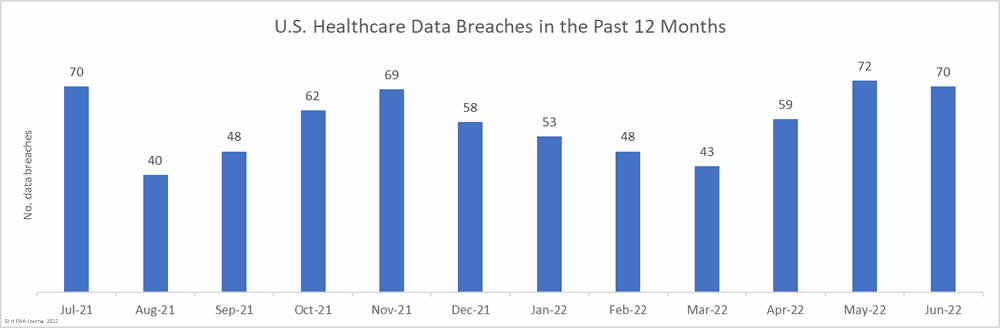
June 2022 saw 70 healthcare data breaches of 500 or more records reported to the Department of Health and Human Services’ Office for Civil Rights (OCR) – two fewer than May and one fewer than June 2021. Over the past 12 months, from July 2021 to June 2022, 692 large healthcare data breaches have been reported and the records of 42,431,699 individuals have been exposed or impermissibly disclosed. The past two months have seen data breaches reported at well over the 12-month average of 57.67 breaches a month.
The past 6 months have seen data breaches reported at similar levels to the second half of 2021 (345 in 1H 2022 v 347 in 2H 2021), but data breaches are down 6.25% from the first half of 2021 (368 in 1H 2021 v 345 in 2H 2022).
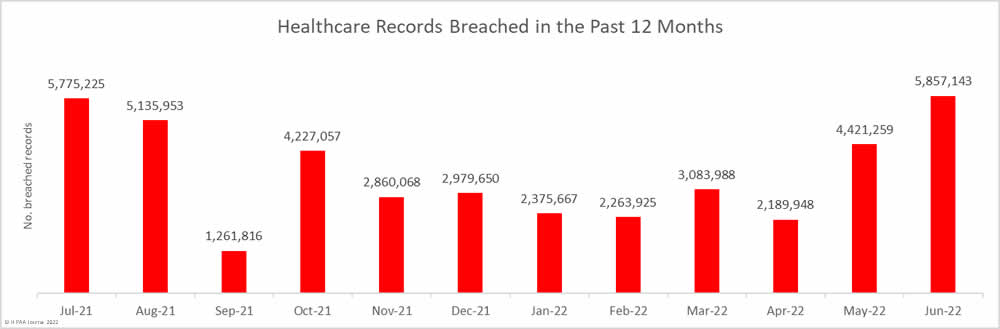
For the third successive month, the number of exposed or compromised records has increased. In June, 5,857,143 healthcare records were reported as breached. That is the highest monthly total so far in 2022. June saw 32.48% more records breached than the previous month and 65.64% more than the monthly average over the past 12 months.
While huge numbers of healthcare records are being breached, fewer records were breached in the first half of 2022 than were breached in either the first half or the second half of 2021. In 1H 2022, 20,191,930 records were breached – 26.84% fewer than the 27,600,651 records breached in 1H 2021 and 9.2% fewer than the 22,239,769 records breached in 2H 2021.
Largest Healthcare Data Breaches Reported in June 2022
There were 31 reported breaches of 10,000 or more healthcare records in June – the same number as May 2022 – two of which affected more than 1.2 million individuals. Several healthcare providers submitted breach reports in June 2022 due to the ransomware attack on the HIPAA business associate, Eye Care Leaders. At least 37 healthcare providers are now known to have been affected by that ransomware attack and more than 3 million records are known to have been exposed in the attack.
| Name of Covered Entity | State | Covered Entity Type | Individuals Affected | Location of Breached Information | Cause of Breach |
| Texas Tech University Health Sciences Center | TX | Healthcare Provider | 1,290,104 | Other | Eye Care Leaders ransomware attack |
| Baptist Medical Center | TX | Healthcare Provider | 1,243,031 | Network Server | Ransomware attack |
| MCG Health, LLC | WA | Business Associate | 793,283 | Network Server | Unspecified hacking and data theft incident |
| Yuma Regional Medical Center | AZ | Healthcare Provider | 737,448 | Network Server | Ransomware attack |
| Stokes Regional Eye Centers | SC | Healthcare Provider | 266,170 | Network Server | Eye Care Leaders ransomware attack |
| Spectrum Eye Physicians | CA | Healthcare Provider | 175,000 | Network Server | Eye Care Leaders ransomware attack |
| 90 Degree Benefits, Inc. | WI | Business Associate | 172,450 | Network Server | Unspecified hacking incident |
| Michigan Avenue Immediate Care | IL | Healthcare Provider | 144,104 | Network Server | Unspecified hacking and data theft incident |
| Mattax Neu Prater Eye Center, Inc. | MO | Healthcare Provider | 92,361 | Electronic Medical Record | Eye Care Leaders ransomware attack |
| Sight Partners Physicians, P.C. | WA | Healthcare Provider | 86,101 | Electronic Medical Record | Eye Care Leaders ransomware attack |
| Clinivate LLC | CA | Business Associate | 77,652 | Network Server | Unspecified hacking incident – No information publicly released |
| Kaiser Foundation Health Plan of Washington | WA | Healthcare Provider | 69,589 | Compromised email account | |
| Carolina Eyecare Physicians, LLC | SC | Healthcare Provider | 68,739 | Electronic Medical Record | Eye Care Leaders ransomware attack |
| Precision Eye Care, Ltd. | MO | Healthcare Provider | 58,462 | Electronic Medical Record | Eye Care Leaders ransomware attack |
| Resolute Health Hospital | TX | Healthcare Provider | 54,239 | Network Server | Ransomware attack |
| Aloha Laser Vision | HI | Healthcare Provider | 43,263 | Electronic Medical Record | Eye Care Leaders ransomware attack |
| Center for Sight, Inc. | MA | Healthcare Provider | 41,041 | Electronic Medical Record | Eye Care Leaders ransomware attack |
| McCoy Vision Center | AL | Healthcare Provider | 33,930 | Electronic Medical Record | Eye Care Leaders ransomware attack |
| Chesapeake Eye Center PA | MD | Healthcare Provider | 32,770 | Network Server | Eye Care Leaders ransomware attack |
| Kevin Wolf, DPM d/b/a Goldsboro Podiatry | NC | Healthcare Provider | 30,669 | Network Server | Unspecified hacking incident |
| Long Vision Center | TX | Healthcare Provider | 29,237 | Electronic Medical Record | Eye Care Leaders ransomware attack |
| Foxhall Ob Gyn Associates | DC | Healthcare Provider | 27,000 | Other | No information |
| Alabama Eye &Cataract, P.C. | AL | Healthcare Provider | 26,000 | Network Server | Eye Care Leaders ransomware attack |
| Lori A. Harkins MD, P.C. dba Harkins Eye Clinic | NE | Healthcare Provider | 23,993 | Electronic Medical Record | Eye Care Leaders ransomware attack |
| DialAmerica Marketing, Inc. | NJ | Business Associate | 19,796 | Network Server | Unspecified hacking incident |
| Central Florida Inpatient Medicine | FL | Healthcare Provider | 19,625 | Compromised email account | |
| Yale New Haven Hospital | CT | Healthcare Provider | 19,496 | Other | Data exposed on a public-facing website |
| Cherry Creek Eye Physicians and Surgeons, P.C. | CO | Healthcare Provider | 17,732 | Electronic Medical Record | Eye Care Leaders ransomware attack |
| Bayhealth Medical Center, Inc. | DE | Healthcare Provider | 17,481 | Network Server | Ransomware attack on business associate (Professional Finance Company) |
| Kernersville Eye Surgeons, P.C. | NC | Healthcare Provider | 13,412 | Electronic Medical Record | Eye Care Leaders ransomware attack |
| Phelps County Regional Medical Center d/b/a Phelps Health | MO | Healthcare Provider | 12,602 | Network Server | Data breach at business associate (MCG Health) |
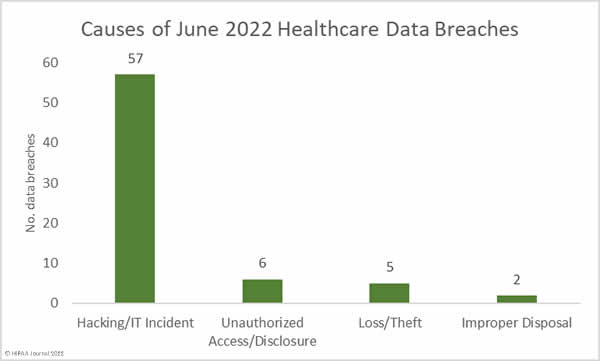
Causes of June 2022 Healthcare Data Breaches
As the above table shows, ransomware attacks on healthcare organizations continue to be reported in high numbers. 20 of the 31 affecting 10,000 or more individuals have been confirmed as involving ransomware. When these attacks occur at business associates they can affect many different HIPAA-covered entities. As mentioned, the Eye Care Leaders ransomware attack has affected at least 37 eye care providers, and a ransomware attack on Professional Finance Company affected 657 of its healthcare provider clients.
There is no sign that ransomware attacks on healthcare providers will slow. This month, CISA has warned the health and public health sector that North Korean state-sponsored hackers are known to be targeting the sector and are using ransomware for extortion.
Hacking incidents continue to dominate the breach reports, with all but two of the top 31 breaches involving hacking. 81% of the month’s breaches were reported as hacking/IT incidents, and across those 57 incidents, the records of 5,784,009 were breached – 98.75% of all the breached records in June. The average breach size was 101,474 records and the median breach size was 12,602 records.
There were 6 unauthorized access/disclosure data breaches reported involving 59,224 records. The average breach size was 9,871 records and the median breach size was 5,672 records. 5 loss theft incidents were reported (4 x theft, 1 x loss) involving 12,184 records. The average breach size was 2,437 records and the median breach size was 1,126 records. Finally, there were two improper disposal incidents reported, both of which involving paper/films. In total 1,726 records were exposed as a result of those incidents.
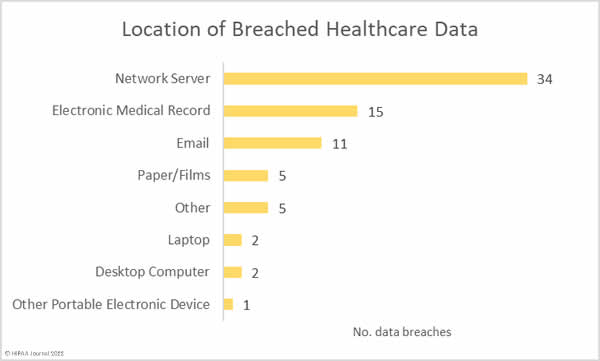
Location of Breached Protected Health Information
The bar graph below shows where the breached information was stored. The high number of network server breaches indicates the extent to which hackers are attacking healthcare organizations. Many of these attacks involved ransomware. Most data breaches reported by healthcare providers do not involve electronic health records, which are separate from other systems. The high number of breaches involving EHRs is due to the ransomware attack on Eye Care Leaders, which provides electronic medical record systems to eye care providers.
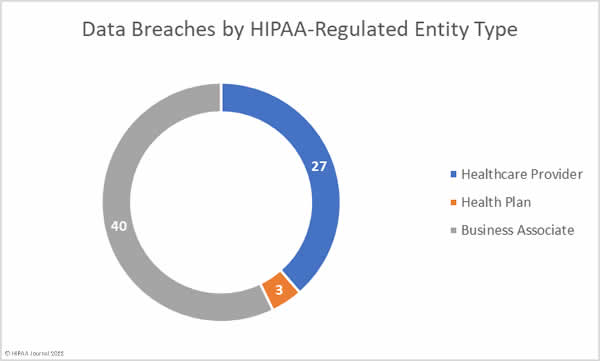
Data Breaches by HIPAA-Regulated Entity Type
Healthcare providers were the worst affected HIPAA-covered entity in June, accounting for 55 data breaches of 500 or more records, with 4 data breaches reported by health plans. Business associates of HIPAA-covered entities self-reported 11 data breaches; however, 29 data breaches occurred at business associates but were reported by the affected covered entity rather than the business associate.
Taking this into account, the breakdown of the month’s data breaches by HIPAA-regulated entity type is shown in the chart below.
Geographic Distribution of Breached Entities
Data breaches of 500 or more records were reported by HIPAA-regulated entities in 29 states and the District of Columbia.
| State | Number of Data Breaches |
| Washington | 5 |
| California, New Jersey, North Carolina, Ohio, South Carolina, Texas, & Virginia | 4 |
| Alabama, Missouri, Nebraska, & New York | 3 |
| Delaware, Illinois, Kansas, Maryland, Michigan, Pennsylvania, Tennessee, & the District of Columbia. | 2 |
| Arizona, Colorado, Connecticut, Delaware, Florida, Georgia, Hawaii, Massachusetts, Mississippi, & Wisconsin | 1 |
HIPAA Enforcement Activity in June 2022
There were no HIPAA enforcement actions announced by the OCR or state attorneys general in June; however, OCR announced this month (July) that a further 12 HIPAA penalties have been imposed, 11 of which were for violations of the HIPAA Right of Access.
The post June 2022 Healthcare Data Breach Report appeared first on HIPAA Journal.