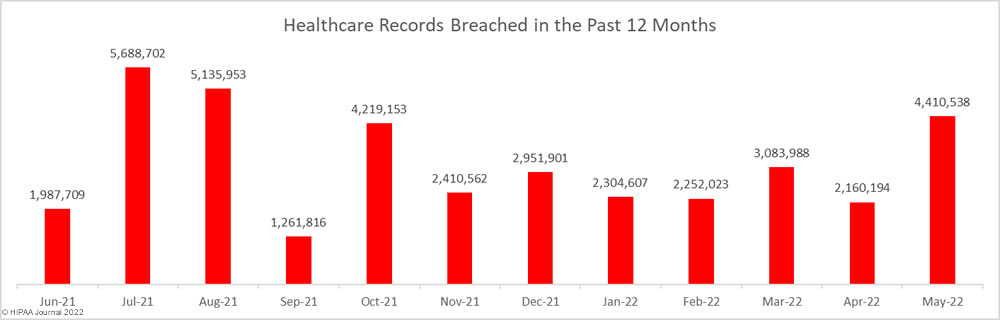
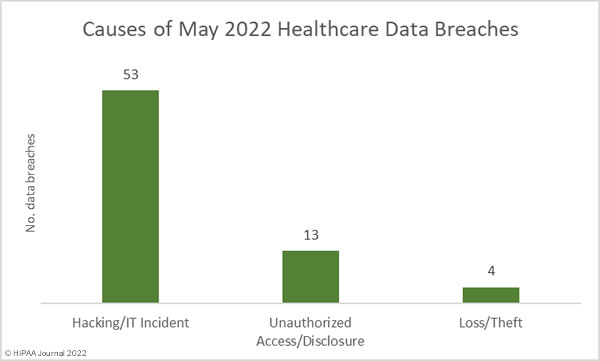
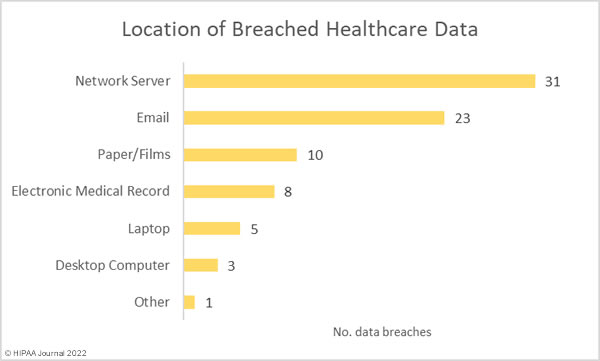
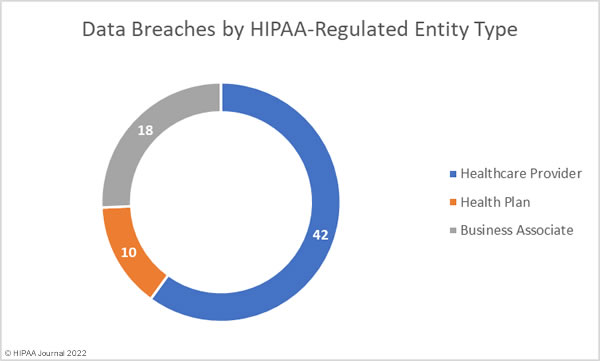
Earlier this month, a draft bipartisan bicameral bill was introduced that seeks federal data privacy and protection regulations, which would replace the current patchwork of data privacy laws in different U.S. states.
The American Data Privacy and Protection Act (ADPPA) was introduced by Energy and Commerce Committee Chair Frank Pallone, (D-NJ), Ranking Member Cathy McMorris Rodgers (R-WA), and Ranking Member of the Senate Committee on Commerce, Science, and Transportation, Senator Roger Wicker (R-MS), and advanced passed a subcommittee on June 23 with a unanimous vote.
In a statement, Pallone, Rodgers, Consumer Protection and Commerce Subcommittee Chair Jan Schakowsky (D-IL), and Subcommittee Ranking Member Gus Bilirakis (R-FL) said the markup of the bill is “another major step in putting people back in control of their data and strengthening our nation’s privacy and data security protections.”
GDPR-Like Federal Data Privacy and Protection Regulations
“This bill will protect consumers’ data privacy, digital security, and our kids online. The bipartisan comprehensive privacy bill will provide regulatory certainty for the business community, end discriminatory use of Americans’ data, promote innovation and protect small businesses, and hold companies to high standards of data security,” said Representatives Schakowsky and Bilirakis. “Consumers across the nation have longed-for deserve strong privacy protections in the digital world that we all increasingly inhabit. This legislation provides those protections.”
The ADPPA shares many provisions with state-level data privacy and protection laws, including the California Consumer Privacy Act (CCPA), and would generally preempt state privacy laws such and, in many respects, is equivalent to the EU’s General Data Protection Regulation (GDPR).
ADPPA-covered entities are any individuals or entities that collect, process, or transfer covered data and are subject to the jurisdiction of the Federal Trade Commission (FTC), are common carriers subject to the Communications Act of 1934, or are not organized to carry on business for their own profit or that of their members. That means that in contrast to state laws such as the CCPA, the bill applies to nonprofits and many small businesses. Government entities are exempt.
The ADPPA applies to “covered data,” which is “information that identifies or is linked or reasonably linkable, alone or in combination with other information, to an individual or a device that identifies or is linked or reasonably linkable to an individual and may include derived data and unique identifiers.” The ADPPA will not apply to de-identified data, employee data, and publicly available information.
Requirements of the ADPPA
ADPPA-covered entities would be required to establish, implement, and maintain reasonable administrative, technical, and physical data security practices to protect covered data against unauthorized access and acquisition. Americans will be given rights over their personal data, such as the right to access their personal data that has been collected or processed by an ADPPA-covered entity, correct any errors in the data, have the data deleted, restrict certain uses of their data, have their personal data exported in human- and machine-readable format, and will have the right to an accounting of disclosures. A time frame of 30 or 60 days would be provided for meeting those requests, depending on the size of the covered entity
The ADPPA also has provisions for “sensitive covered data,” which is defined as “any information that describes or reveals the past, present, or future physical health, mental health, disability, diagnosis, or healthcare treatment of an individual.” Affirmative express consent would be required before an ADPPA-covered entity could collect and process sensitive covered data or transfer that information to a third party.
ADPPA-covered entities will be required to minimize the data collected, limits will be placed on the transfer of precise geolocation information, browsing history, and physical activity information collected from a smartphone or wearable device, and the collection, processing, or transferring of biometric information, known nonconsensual intimate images, or genetic information would be prohibited, apart from in limited circumstances.
The bill calls for privacy by design, and required policies and procedures to be implemented related to the collection, processing, and transfer of covered data, and ADPPA -covered entities would be required to make a privacy policy public that includes a detailed and accurate representation of the entity’s data collection, processing, and transfer activities. ADPPA-covered entities would be prevented from denying a service or product, conditioning a service or product, or setting the price of a service or a product based on an individual’s agreement to waive any privacy rights.
Implications for Healthcare Organizations
The ADPPA has implications for healthcare organizations and includes several provisions from the Health Insurance Portability and Accountability Act (HIPAA). Healthcare organizations that are compliant with HIPAA (or entities compliant with FERPA, the Gramm-Leach-Bliley Act, and other laws) would be seen to be compliant with the ADPPA, but only with respect to the data covered by those laws. In healthcare, the ADPPA would apply to all covered data that is not regulated by HIPAA including healthcare data collected, processed, or transferred by non-HIPAA-covered entities.
Any covered entity that fails to ensure personal data is kept private and confidential or does not allow Americans to exercise their rights under the ADPPA, will be held to account, with compliance enforced by the FDA and state attorneys general. The bill also includes a private cause of action that will allow Americans to sue over violations, although this is not due to be implemented until four years after the effective date.
This is not the first attempt at introducing a federal data privacy and protection bill and it is unclear if the bill has sufficient support in its current form.
The post American Data Privacy and Protection Act Establishes GDPR-like Federal Data Privacy and Protection Standards appeared first on HIPAA Journal.