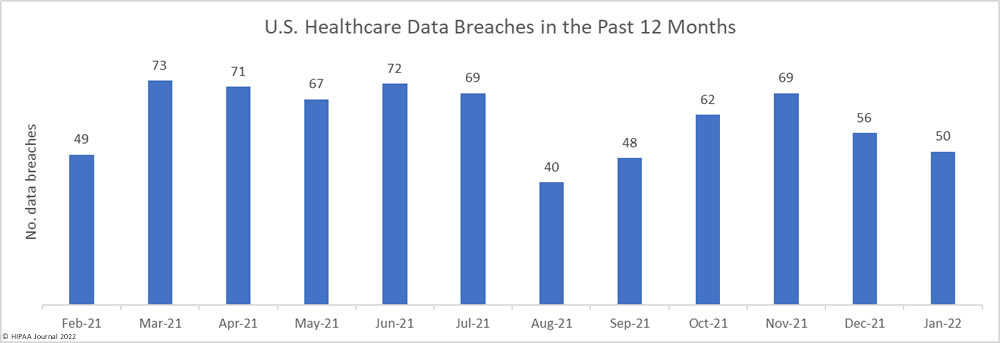
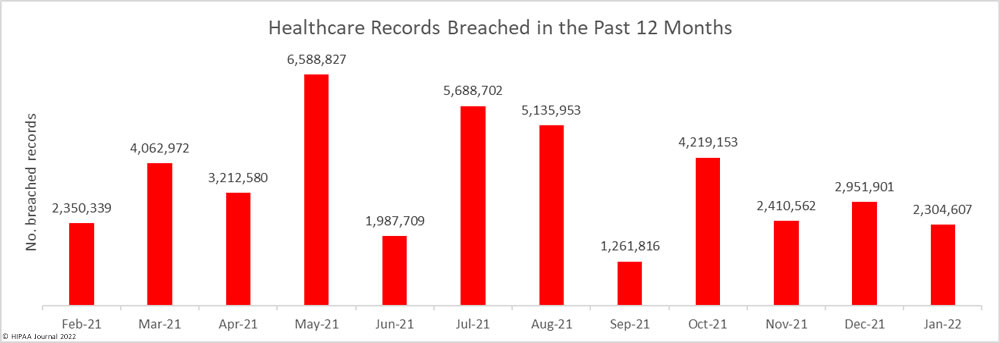
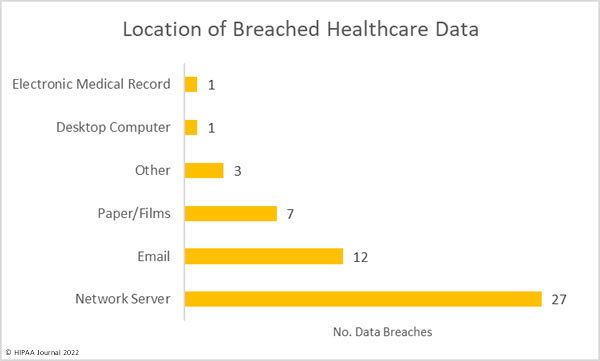
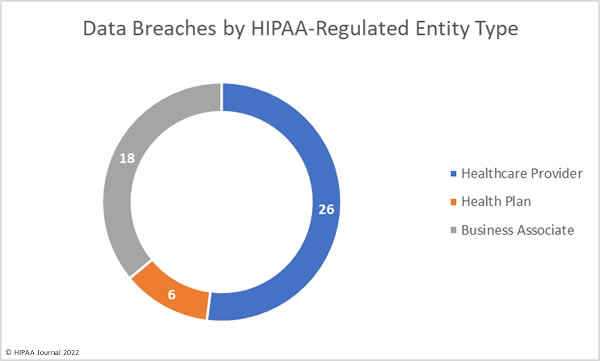
There have been calls for healthcare organizations to take steps to improve security due to a major rise in hacking incidents, ransomware attacks, and vulnerability disclosures in 2021. Record numbers of healthcare data breaches were reported last year, and tens of millions of healthcare records were compromised.
Adhering to the minimum requirements of the HIPAA Security Rule and conducting risk analyses, having robust risk management practices, conducting vulnerability scans, and implementing technical safeguards such as intrusion prevention systems, next-generation firewalls, and spam filters are all important measures to improve cybersecurity and ensure HIPAA compliance, but it is also important to improve the human aspect of cybersecurity. Risky employee behaviors need to be eradicated and the workforce needs to be trained to be more security-aware and taught how to recognize common attacks that target individuals, such as phishing and social engineering.
The human aspect of cybersecurity is often one of the weakest links in the security chain, which has been highlighted by a recent study commissioned by New Zealand-based Mobile Mentor and conducted by the Austin, TX-based Center for Generational Kinetics. The aim of the study was to explore the Endpoint Ecosystem to understand how employees perceive privacy, productivity, and personal well-being in the modern workplace. The Endpoint Ecosystem is the combination of all devices, applications, and tools that are used by employees coupled with the experiences of employees using technologies.
The survey was conducted on 1,500 employees in highly regulated industries such as government, healthcare, education, and finance in the United States and Australia, and the findings are detailed in the Mobile Mentor report, The Endpoint Ecosystem – 2022 National Study.
Employees are Taking Security Risks
The survey confirmed what other studies have found – The pandemic has led to the workforce becoming much more distributed and employers have had difficulty adapting to this new way of working and ensuring security policies are implemented and enforced that are well suited to the change in how employees are working.
One of the major findings was a lack of awareness about security policies and a failure of employers to provide security awareness training to the workforce. 27% of employees said they saw security policies less than once a year and 39% said they receive security awareness training less than once a year. Healthcare and education employees were the least likely to see security policies and employees often felt they were not adequately trained to protect company data.
41% of respondents said security policies implemented by their employers restricted the way they work, and 36% of employees said they had found a way to work around security policies. The use of shadow IT – applications and services that have not been authorized by the IT department – was found to be out of control. Workers are routinely using unregulated apps and services for work activities, which can involve regulated data. Employees commonly used services such as Gmail and Dropbox because they believe it makes them more efficient, even though the use of those services has an impact on security.
Interestingly, while remote working is viewed as a security risk, remote workers appeared to be much more tech-savvy, were more aware of security and privacy policies, and were more careful with their passwords. That said, workers are allowing family members to use their work devices – 46% of younger workers said other family members use their work devices.
The lines are getting blurred between device use for personal and work purposes. Overall, 64% of respondents said they use personal devices for work, but only 31% had a secure BYOD program. 57% of younger workers said they use work devices for personal use and 71% said they used personal devices for work. Many employers are failing to address the security risks associated with the use of personal devices for work purposes and work devices for personal use.
Poor Password Hygiene is a Major Security Risk
One of the main security risks identified in the study related to passwords. Poor password hygiene is a major security risk. 80% of cyberattacks start with a compromised password. One of the findings, mirrored by a recent IDC survey, is employees have too many passwords to remember. While password policies may be in place – and enforced – they are often circumvented. 69% of respondents said they choose passwords that are easy to remember, 29% of employees said they write down their passwords in a personal journal, and 24% said they store work passwords on their phones. While many of the security problems associated with passwords can be solved by using a password manager, only 31% of respondents used one.
The survey revealed employees are much more concerned about personal privacy than security, with healthcare employees the most concerned about protecting personal privacy. Mobile Mentor suggests that healthcare employers looking to improve security need to teach employees that privacy and security are two sides of the same coin.
“When the endpoint ecosystem works well, you have a secure, productive, and happy workforce. It’s always been important, but it became urgent over the last two years when the pandemic forced more people to work remotely, cybersecurity attacks increased, and the Great Resignation forced employers to rethink how they support their employees,” said Denis O’Shea, founder of Mobile Mentor. “Until employers prioritize the importance of each component within the Endpoint Ecosystem, their company security and employee productivity are going to be exposed to serious risk.”
The post Poor Employee Cyber Hygiene is Putting Healthcare Cybersecurity at Risk appeared first on HIPAA Journal.