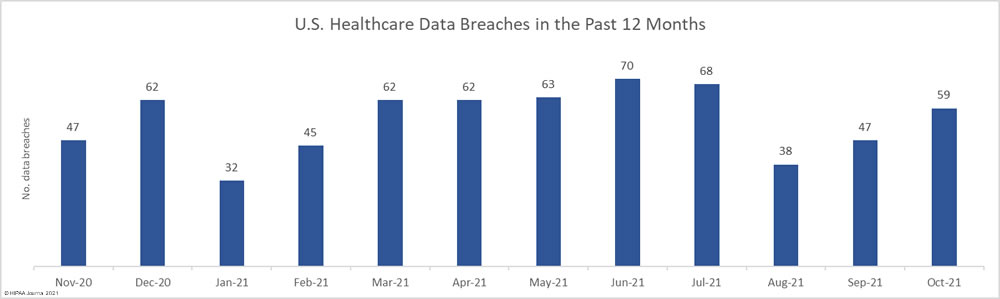
October saw 59 healthcare data breaches of 500 or more records reported to the Department of Health and Human Services’ Office for Civil Rights, which represents a 25.5% increase from September. Over the past 12 months, from November 2020 to October 2021, there have been 655 reported breaches of 500 or more records, 546 of which have been reported in 2021.
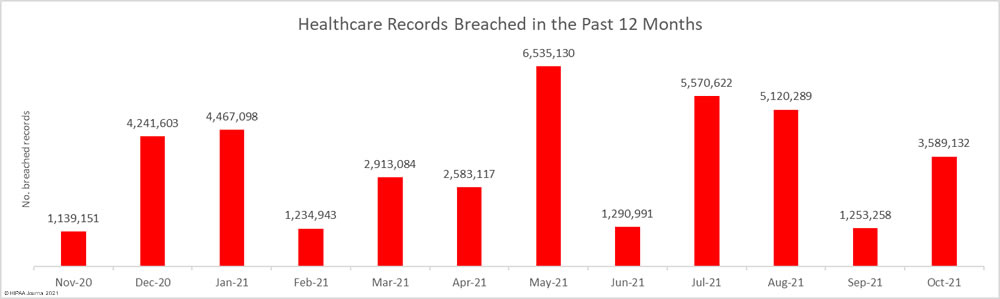
The protected health information (PHI) of 3,589,132 individuals was exposed, stolen, or impermissibly disclosed across the 59 reported data breaches, which is 186% more records than September. Over the past 12 months, from November 2020 to October 2021, the PHI of 39,938,418 individuals has been exposed or stolen, with 34,557,664 individuals known to have been affected by healthcare data breaches so far in 2021.
Largest Healthcare Data Breaches in October 2021
There were 18 data breaches reported to the HHS’ Office for Civil Rights in October that impacted 10,000 or more individuals, as detailed in the table below.
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Breach Cause |
| Eskenazi Health |
IN |
Healthcare Provider |
1,515,918 |
Hacking/IT Incident |
Ransomware attack |
| Sea Mar Community Health Centers |
WA |
Healthcare Provider |
688,000 |
Hacking/IT Incident |
Ransomware attack |
| ReproSource Fertility Diagnostics, Inc. |
MA |
Healthcare Provider |
350,000 |
Hacking/IT Incident |
Ransomware attack |
| QRS, Inc. |
TN |
Business Associate |
319,778 |
Hacking/IT Incident |
Unauthorized network server access |
| UMass Memorial Health Care, Inc. |
MA |
Business Associate |
209,048 |
Hacking/IT Incident |
Phishing attack |
| OSF HealthCare System |
IL |
Healthcare Provider |
53,907 |
Hacking/IT Incident |
Ransomware attack |
| Educators Mutual Insurance Association |
UT |
Health Plan |
51,446 |
Hacking/IT Incident |
Unauthorized network access and malware infection |
| Lavaca Medical Center |
TX |
Healthcare Provider |
48,705 |
Hacking/IT Incident |
Unauthorized network access |
| Professional Dental Alliance, LLC |
PA |
Healthcare Provider |
47,173 |
Unauthorized Access/Disclosure |
Phishing attack on a vendor |
| Nationwide Laboratory Services |
FL |
Healthcare Provider |
33,437 |
Hacking/IT Incident |
Ransomware attack |
| Professional Dental Alliance of Michigan, PLLC |
PA |
Healthcare Provider |
26,054 |
Unauthorized Access/Disclosure |
Phishing attack on a vendor |
| Syracuse ASC, LLC |
NY |
Healthcare Provider |
24,891 |
Hacking/IT Incident |
Unauthorized network access |
| Professional Dental Alliance of Georgia, PLLC |
PA |
Healthcare Provider |
23,974 |
Unauthorized Access/Disclosure |
Phishing attack on a vendor |
| Professional Dental Alliance of Florida, LLC |
PA |
Healthcare Provider |
18,626 |
Unauthorized Access/Disclosure |
Phishing attack on a vendor |
| Professional Dental Alliance of Illinois, PLLC |
PA |
Healthcare Provider |
16,673 |
Unauthorized Access/Disclosure |
Phishing attack on a vendor |
| Professional Healthcare Management, Inc. |
TN |
Healthcare Provider |
12,306 |
Hacking/IT Incident |
Ransomware attack |
| Professional Dental Alliance of Tennessee, LLC |
PA |
Healthcare Provider |
11,217 |
Unauthorized Access/Disclosure |
Phishing attack on a vendor |
| Professional Dental Alliance of New York, PLLC |
PA |
Healthcare Provider |
10,778 |
Unauthorized Access/Disclosure |
Phishing attack on a vendor |
Ransomware attacks continue to plague healthcare organizations and threaten patient safety. Half of the top 10 data breaches involved ransomware, including the top three data breaches reported in October.
The worst breach of the month was reported by Eskenazi Health. The PHI of more than 1.5 million patients was exposed and patient data is known to have been stolen in the attack. A major ransomware attack was also reported by Sea Mar Community Health Centers. Its systems were first compromised in December 2020, the ransomware attack was identified in March 2021, and Sea Mar was notified about the posting of patient data on a darknet marketplace in June. It took until late October to issue notifications to affected individuals.
Hackers often gain access to healthcare networks through phishing attacks, and phishing remains the leading attack vector in ransomware attacks. Large quantities of sensitive data are often stored in email accounts and can easily be stolen if employees respond to phishing emails. A phishing attack on UMass Memorial Health Care resulted in the exposure of the PHI of 209,048 individuals, and a phishing attack on a vendor used by the Professional Dental Alliance exposed the PHI of more than 174,000 individuals.
Causes of October 2021 Healthcare Data Breaches
Data breaches classified as hacking/IT incidents, which include ransomware attacks, were the main cause of data breaches in October. 57.63% of all breaches reported in the month were classified as hacking/IT incidents and they accounted for 94.14% of all breached records (3,378,842 records). The average size of the data breaches was 99,378 records and the median breach size was 5,212 records.
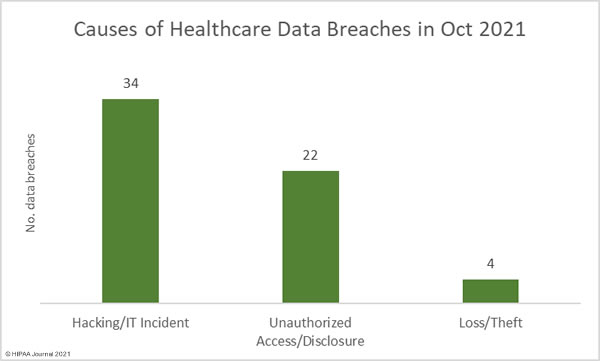
22 breaches were classified as unauthorized access/disclosure incidents and involved the PHI of 200,887 individuals. Those breaches include the phishing attack that affected the Professional Dental Alliance. The average breach size was 9,131 records and the median breach size was 4,484 records.
There were 4 breaches reported that involved the loss or theft of physical PHI or electronic devices containing PHI, 3 of which were theft incidents and 1 was a lost laptop computer. The PHI of 9,403 individuals was exposed as a result of those incidents. The average breach size was 2,351 records and the mean breach size was 1,535 records.
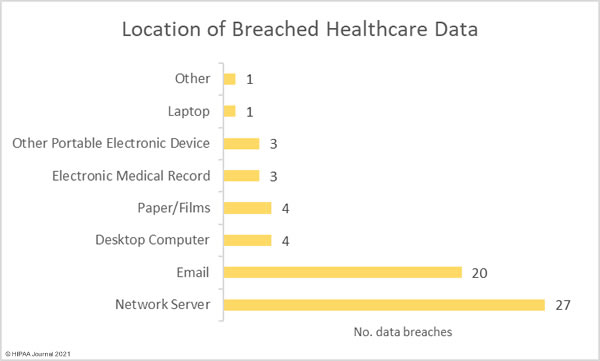
Healthcare Data Breaches by HIPAA-Regulated Entity Type
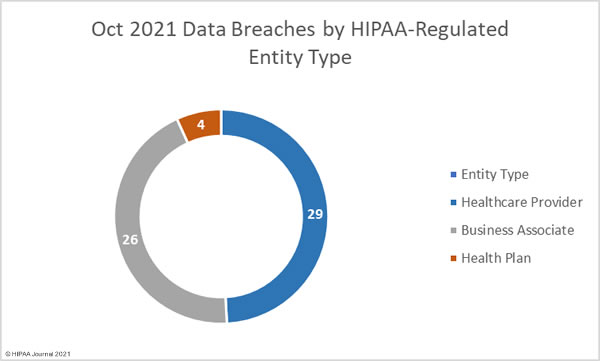
Healthcare providers were the worst affected covered entity type with 43 reported breaches. 8 data breaches were reported by business associates of HIPAA-covered entities and 8 were reported by health plans. Many data breaches occur at business associates of HIPAA-covered entities but are reported by the affected covered entity. The pie chart below shows the breakdown of breaches based on where they occurred.
Healthcare Data Breaches by State
Healthcare data breaches were reported by HIPAA-regulated entities in 26 states. Pennsylvania was the worst affected state with 12 reported breaches, although 11 of those breaches were the same incident – the phishing attack on the Professional Dental Alliance vendor that was reported separately by each affected HIPAA-covered entity.
| State |
No. Breaches |
| Pennsylvania |
12 |
| California |
5 |
| Illinois, Indiana, & Texas |
4 |
| New York & Washington |
3 |
| Connecticut, Florida, Massachusetts, New Jersey, North Carolina & Tennessee |
2 |
| Alabama, Arkansas, Kansas, Kentucky, Minnesota, Mississippi, Nebraska, Ohio, South Carolina, Utah, Virginia, & West Virginia |
1 |
HIPAA Enforcement Activity in October 2021
There was only one HIPAA enforcement action announced in October. The New Jersey Attorney General agreed to settle an investigation into a data breach reported by Diamond Institute for Infertility and Menopause that resulted in the exposure of the PHI of 14,663 New Jersey residents.
The New Jersey Department of Law and Public Safety Division of Consumer Affairs uncovered violations of 29 provisions of the HIPAA Privacy and Security Rules, and violations of the New Jersey Consumer Fraud Act. In addition to paying $495,000 in civil monetary penalties and investigation costs, Diamond agreed to implement additional measures to improve data security.
The post October 2021 Healthcare Data Breach Report appeared first on HIPAA Journal.




