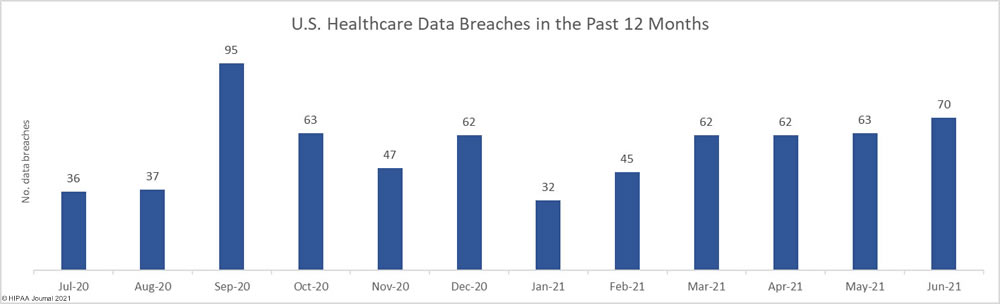
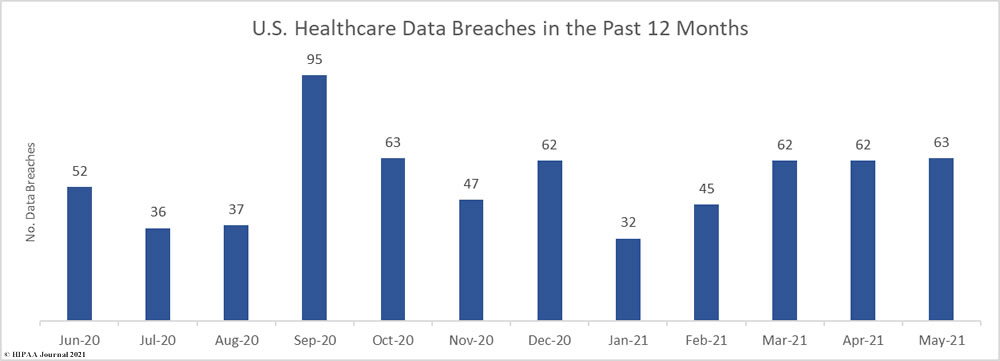
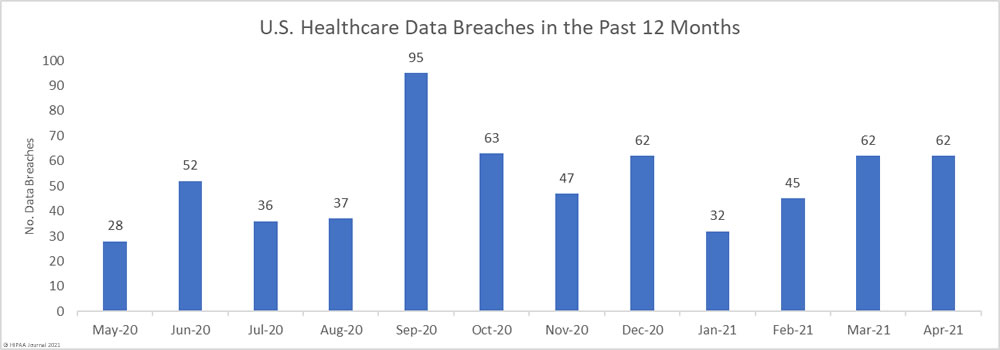
For the third consecutive month, the number of reported healthcare data breaches of 500 or more records increased. June saw an 11% increase in reported breaches from the previous month with 70 data breaches of 500 or more records reported to the HHS’ Office for Civil Rights – the highest monthly total since September 2020 and well above the average of 56 breaches per month over the past year.
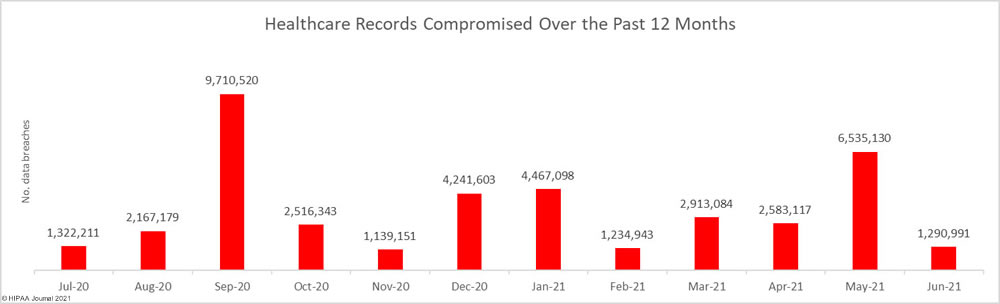
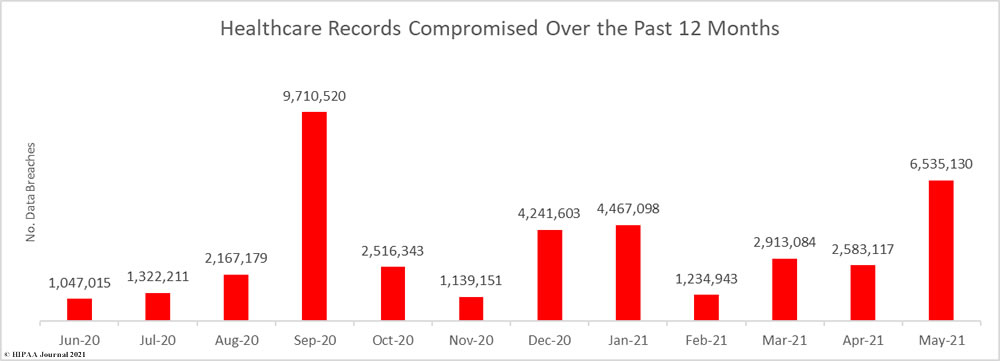
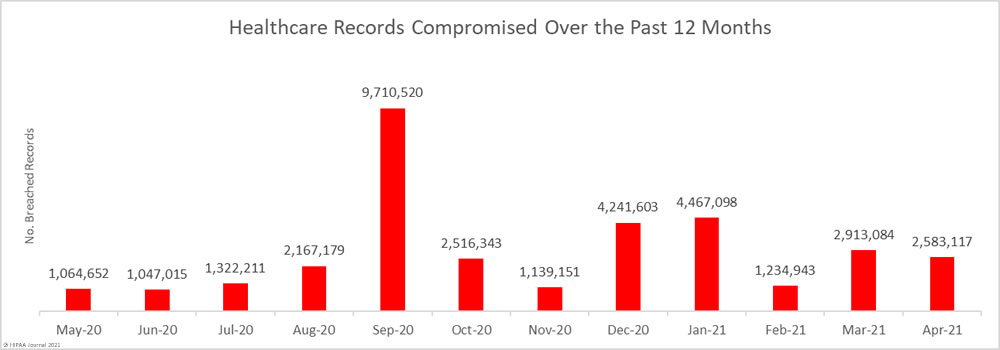
While the number of reported breaches increased, there was a substantial fall in the number of breached healthcare records, which decreased 80.24% from the previous month to 1,290,991 breached records. That equates to more than 43,000 breached records a day in June.
More than 40 million healthcare records have been exposed or impermissibly disclosed over the past 12 months across 674 reported breaches. On average, between July 2020 and June 2021, an average of 3,343,448 healthcare records were breached each month.
Largest Healthcare Data Breaches in June 2021
There were 19 healthcare data breaches of 10,000 or more records reported in June. Ransomware continues to pose problems for healthcare organizations, with 6 of the top 10 breaches confirmed as ransomware attacks. Several healthcare organizations reported ransomware attacks in June that occurred at third-party vendors, with the number of healthcare providers confirmed as being affected by the ransomware attacks on vendors Elekta, Netgain Technologies, and CaptureRx continuing to grow.
The largest healthcare data breach to be reported in June was a phishing attack on the medical payment billing service provider MultiPlan. A threat actor gained access to an email account containing the protected health information of 214,956 individuals.
Northwestern Memorial HealthCare and Renown Health were affected by the ransomware attack on the Swedish radiation therapy and radiosurgery solution provider Elekta Inc., That attack is known to have affected a total of 42 healthcare providers in the United States.
| Name of Covered Entity | Covered Entity Type | Individuals Affected | Breach Cause | Business Associate Involvement |
| MultiPlan | Business Associate | 214,956 | Phishing attack | Yes |
| Northwestern Memorial HealthCare | Healthcare Provider | 201,197 | Elekta ransomware attack | Yes |
| Scripps Health | Healthcare Provider | 147,267 | Ransomware attack | No |
| San Juan Regional Medical Center | Healthcare Provider | 68,792 | Unspecified hacking and data exfiltration incident | No |
| Renown Health | Healthcare Provider | 65,181 | Elekta ransomware attack | Yes |
| Minnesota Community Care | Healthcare Provider | 64,855 | Netgain ransomware attack | Yes |
| Francisco J. Pabalan MD, INC | Healthcare Provider | 50,000 | Hacking/IT Incident (Unknown) | No |
| Prominence Health Plan | Health Plan | 45,000 | Ransomware attack | No |
| NYC Health + Hospitals | Healthcare Provider | 43,727 | CaptureRx ransomware attack | Yes |
| UofL Health, Inc. | Healthcare Provider | 42,465 | Misdirected email | No |
| Peoples Community Health Clinic | Healthcare Provider | 40,084 | Phishing attack | No |
| Reproductive Biology Associates, LLC and its affiliate My Egg Bank, LLC | Healthcare Provider | 38,000 | Ransomware attack | No |
| Hawaii Independent Physicians Association | Business Associate | 18,770 | Phishing attack | Yes |
| UW Medicine | Healthcare Provider | 18,389 | Hacking/IT Incident (Unknown) | Yes |
| Cancer Care Center | Healthcare Provider | 18,000 | Hacking/IT Incident (Unknown) | Yes |
| Temple University Hospital, Inc. | Healthcare Provider | 16,356 | Hacking/IT Incident (Unknown) | Yes |
| Walmart Inc. | Healthcare Provider | 14,532 | Loss of paper/films | No |
| Discovery Practice Management, Inc. | Business Associate | 13,611 | Phishing attack | Yes |
| Jawonio | Healthcare Provider | 13,313 | Phishing attack | No |
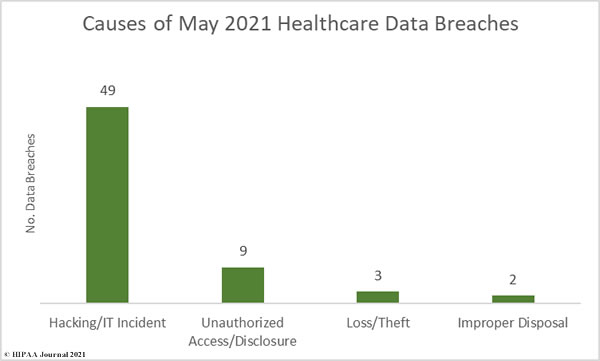
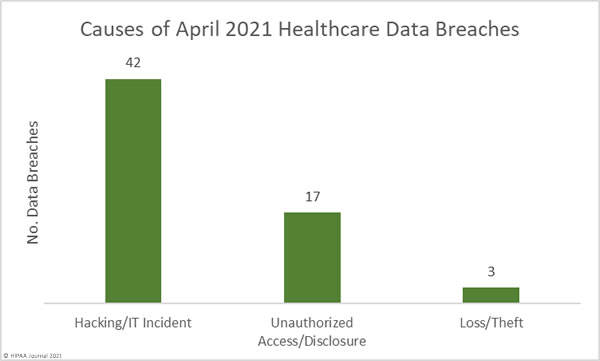
Causes of June 2021 Healthcare Data Breaches
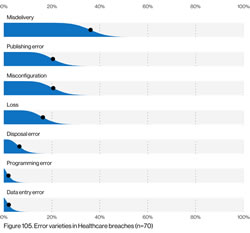
Hacking/IT incidents dominated the breach reports in June 2021, with ransomware attacks accounting for a large percentage of those breaches. There were 58 reported hacking/IT incidents, in which the protected health information of 1,190,867 individuals was exposed or compromised – 92.24% of all breached records in June. The mean breach size was 20,532 records and the median breach size was 2,938 records.
There were 9 unauthorized access/disclosure incidents reported that involved the impermissible disclosure of the PHI of 81,764 individuals. The mean breach size was 9,085 records and the median breach size was 5,509 records.
There was one incident reported involving the loss of paperwork containing the PHI of 14,532 individuals, one portable electronic device theft affecting 1,166 patients, and 1 incident involving the improper disposal of 2,662 physical records.
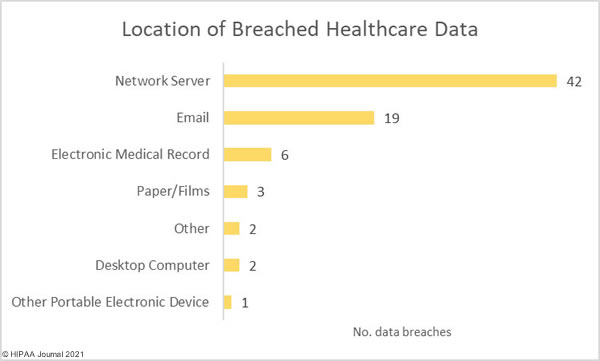
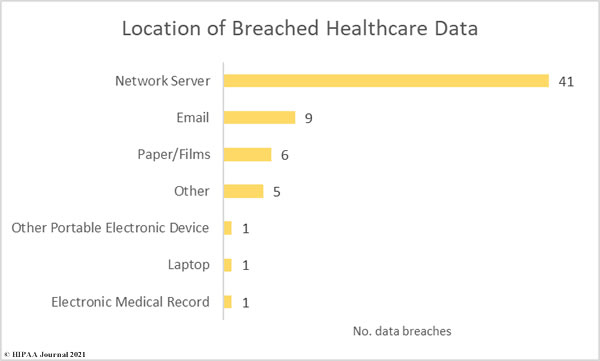
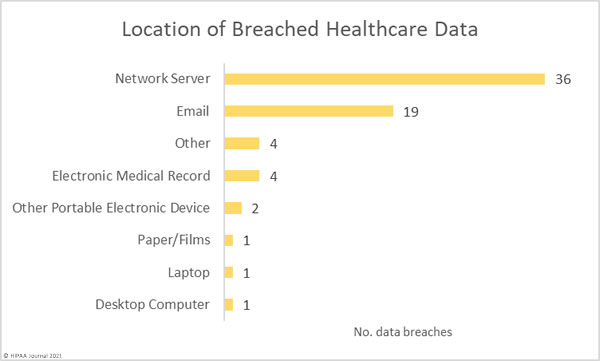
42 hacking incidents involved PHI stored on network servers, most of which were data access and exfiltration incidents involving ransomware. There were 19 email security breaches involving PHI stored in email accounts, most of which were phishing incidents.
Covered Entities Reporting Data Breaches in June
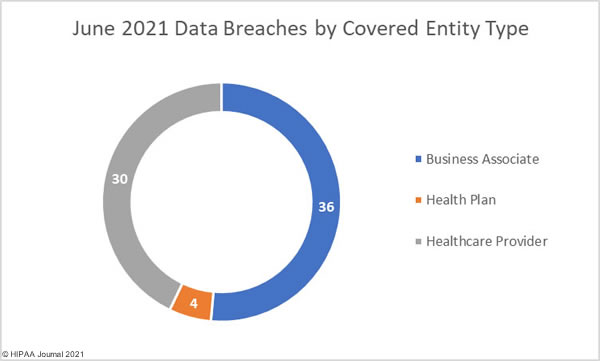
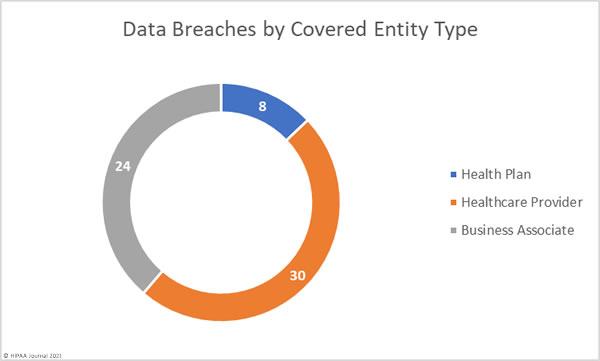
The breach reports show healthcare providers were the worst affected covered entity type with 53 data breaches. 9 breaches were reported by health plans, and 8 by business associates of HIPAA covered entities. HIPAA-covered entities often report breaches at third party vendors, which can mask the extent to which business associates are being targeted by hackers. Adjusted figures taking this into account show the extent to which business associates are suffering data breaches. There were 36 data breaches reported that involved business associates, as shown in the pie chart below.
June 2021 Healthcare Data Breaches by State
There were large healthcare data breaches reported by HIPAA covered entities and business associates based in 32 states. California was the worst affected state with 8 reported breaches, followed by New York with 6.
| State | No. Data Breaches |
| California | 8 |
| New York | 6 |
| Illinois, Pennsylvania, Washington | 4 |
| Georgia, New Jersey, Ohio, Oregon, Texas | 3 |
| Arkansas, Kentucky, Michigan, Mississippi, Nevada, Tennessee, Wisconsin | 2 |
| Alaska, Arizona, Colorado, Connecticut, Florida, Hawaii, Iowa, Maryland, Massachusetts, Minnesota, Montana, New Mexico, Oklahoma, Rhode Island, South Carolina | 1 |
HIPAA Enforcement Activity in June 2021
The HHS’ Office for Civil Rights announced one HIPAA enforcement action in June under its HIPAA Right of Access enforcement initiative. The Diabetes, Endocrinology & Lipidology Center, Inc. in Martinsburg, West Virginia was ordered to pay a financial penalty of $5,000 to resolve its HIPAA Right of Access case and agreed to adopt a robust corrective action plan to ensure that patients will be provided with timely access to their medical records. There were no confirmed HIPAA enforcement actions by state Attorneys General in June.
The post June 2021 Healthcare Data Breach Report appeared first on HIPAA Journal.