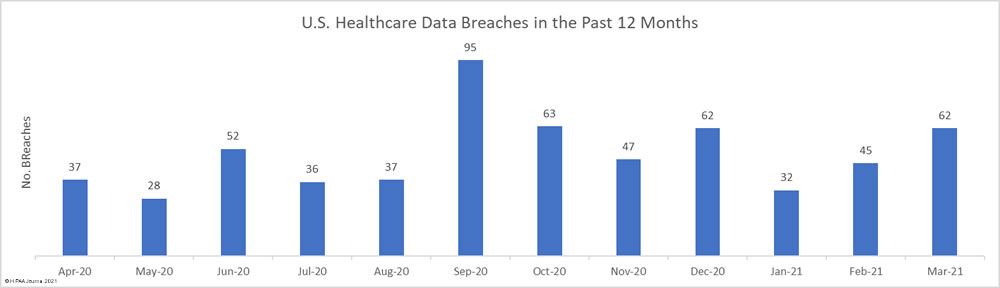
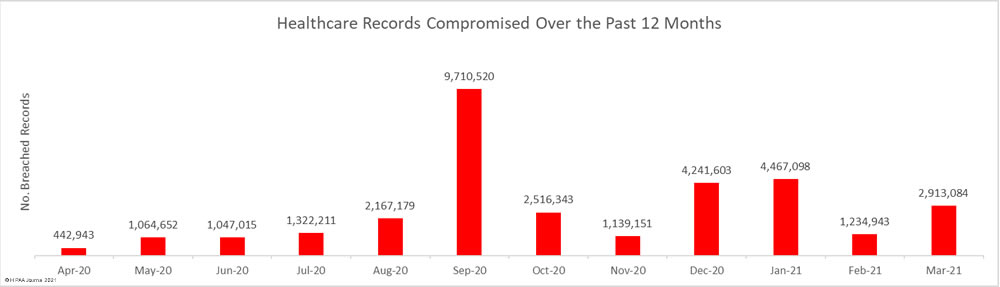
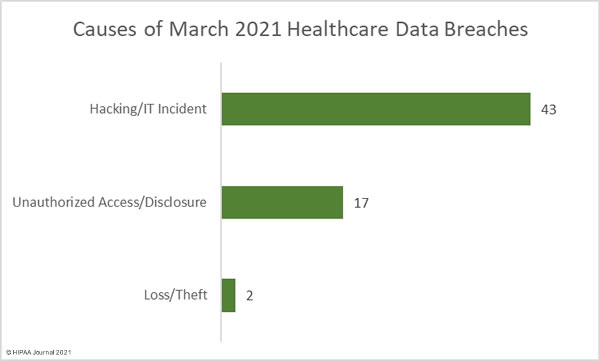
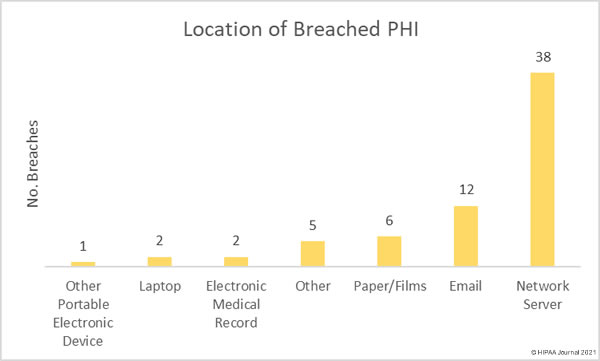
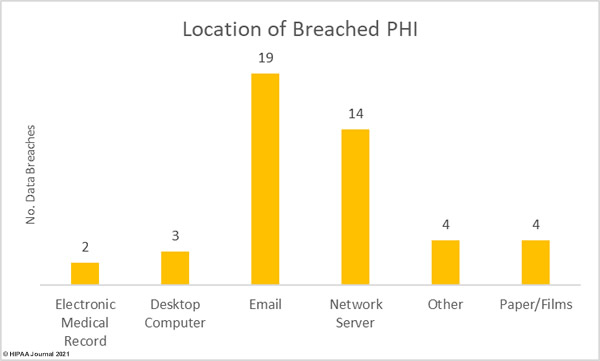
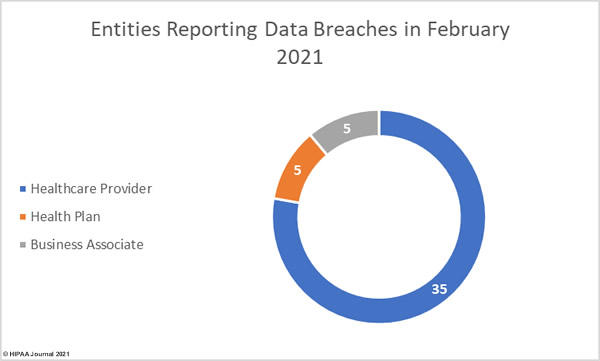
Several healthcare groups have expressed concern about the HIPAA Privacy Rule changes proposed by the Department of Health and Human Services (HHS) in December 2020 and published in the Federal Register in January. The HHS has received comments from more than 1,400 individuals and organizations and will now review all feedback before issuing a final rule or releasing a new proposed rule.
There have been calls for changes to the HIPAA Privacy Rule to be made to align it more closely with other regulations, such as the 21st Century Cures Act, the 42 CFR Part 2 regulations covering federally assisted substance use disorder (SUD) treatment programs, and for there to be greater alignment with state health data privacy laws. Some of the proposed HIPAA Privacy Rule changes are intended to remove barriers to data sharing for care coordination, but the changes may still conflict with state laws, especially in relation to SUD treatment. There is concern that poor alignment with other regulations could be a major cause of confusion and could create new privacy and security risks.
Another area of concern relates to personal health applications (PHA). The HHS has defined PHAs, but many groups and organizations have voiced concern about the privacy and security risks associated with sending protected health information (PHI) to these unregulated apps. PHAs fall outside the scope of HIPAA, so any PHI that a covered entity sends to a PHA at the request of a patient could result in a patient’s PHI being used in ways not intended by the patient. A patient’s PHI could also easily be accessed and used by third parties.
PHAs may not have robust privacy and security controls since compliance with the HIPAA Security Rule would not be required. There is no requirement for covered entities to enter into business associate agreements with PHA vendors, and secondary disclosures of PHI would not be restricted by the HIPAA Privacy Rule.
“Personal health applications should be limited to applications that do not permit third-party access to the information, include appropriate privacy protections and adequate security and are developed to correctly present health information that is received from electronic health records,” suggested the American Hospital Association in its feedback to the HHS.
The College of Healthcare Information Management Executives (CHIME) has voiced concerns about the proposal for covered entities to require PHAs to register before providing patient data, and how covered entities would be required to respond when a patient requested their health information to be sent to a PHA that does not have appropriate privacy and security protections. For instance, if a patient requested their PHI be sent to a PHA developed by nation state actor, whether providers would still be required to send PHI at the request of a patient. Concern has also been raised about the growing number of platforms that exchange PHI that fall outside the scope of HIPAA.
One of the proposed changes relates to improving patients’ access to their health data and shortening the time to provide that information from 30 to 15 days. The Association for Behavioral Health and Wellness (ABHW) and CHIME have both voiced concerns about the shortening of the timeframe for honoring patient requests for their healthcare data, as this will place a further administrative burden on healthcare providers, especially during the pandemic. CHIME said it may not be possible to provide PHI within this shortened time frame and doing so may well add costs to the healthcare system. CHIME has requested the HHS document when exceptions are allowed, such as in cases of legal disputes and custody cases. ABHW believes the time frame should not be changed and should remain as 30 days.
It is likely that if the final rule is issued this year, it will be necessary for organizations to ensure compliance during the pandemic, which could prove to be extremely challenging. ABHW has recommended delaying the proposed rule for an additional year to ease the burden on covered entities. CHIME has suggested the HHS should not issue a final rule based on the feedback received, but instead reissue the questions raised in the proposed rule as a request for information and to host a listening session to obtain more granular feedback and then enter into a dialogue about the proposed changes.
The post Healthcare Groups Raise Concern About the Proposed HIPAA Privacy Rule Changes appeared first on HIPAA Journal.