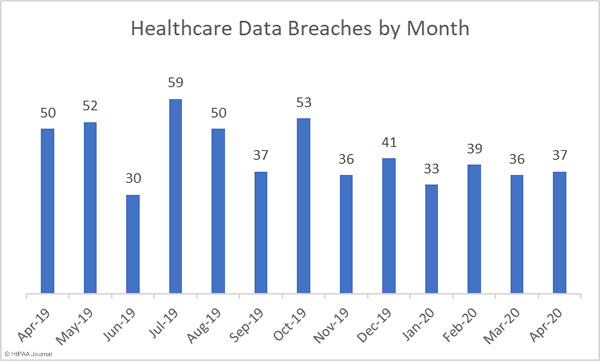
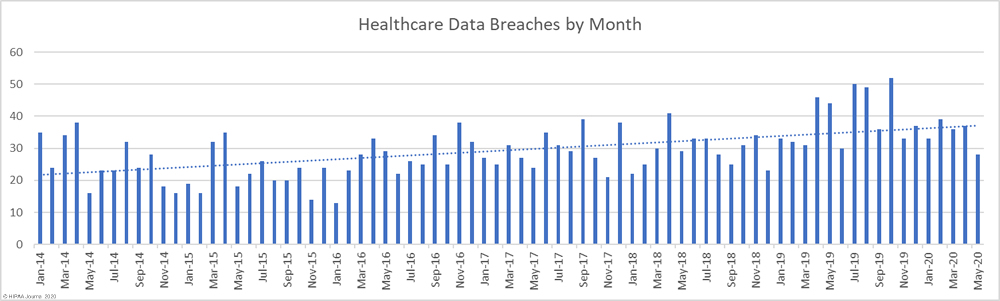
May 2020 saw a marked fall in the number of reported healthcare data breaches compared to April, with 28 data breaches of 500 or more records reported to the HHS’ Office for Civil Rights. That is the lowest number of monthly breaches since December 2018 and the first time in 17 months that healthcare data breaches have been reported at a rate of less than one per day. The monthly total would have been even lower had one breach been reported by the business associate responsible for an improper disposal incident, rather than the 7 healthcare providers impacted by the breach.
Several cybersecurity companies have reported an increase in COVID-19-related breaches, such as phishing attacks that use COVID-19-themed lures. While there is strong evidence to suggest that these types of attacks have increased since the start of the pandemic, the number of cyberattacks appears to have broadly remained the same or increased slightly. Microsoft has reported that its data shows a slight increase in attacks, but says it only represents a blip and the number of threats and cyberattacks has changed little during the pandemic.
Threat activity does not appear to have dropped, so the fall in reported cyberattacks and data breaches could indicate that threat actors have taken the decision not to attack healthcare providers on the front line in the fight against COVID-19. The Maze ransomware gang publicly stated that it would not target healthcare providers during the COVID-19 pandemic, but many other ransomware gangs appear to have stepped up their attacks and are making no such concessions.
It is also possible that rather than cyberattacks and data breaches falling, covered entities and business associates have not been detecting breaches or have delayed reporting. The reason for the fall in reported breaches is likely to become clearer over the coming weeks and months and we will see if this is part of a new trend or if the drop is simply a blip.
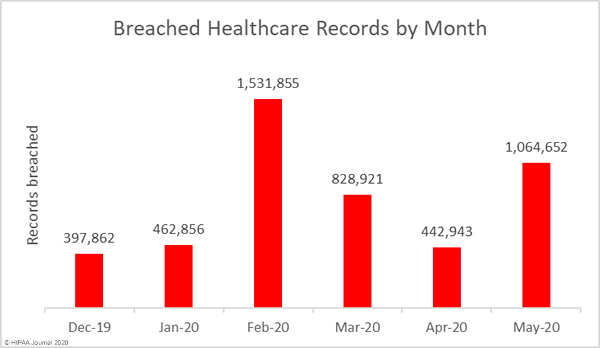
While it is certainly good news that the number of breaches has fallen, there was a significant increase in the number of exposed and compromised healthcare records. There were 10 fewer data breaches reported in May 2020 than April, but 1,064,652 healthcare records were breached in May. That is more than twice the number of records breached in April.
Largest Healthcare Data Breaches in May 2020
| Name of Covered Entity |
State |
Covered Entity Type |
Individuals Affected |
Type of Breach |
| Elkhart Emergency Physicians, Inc. |
IN |
Healthcare Provider |
550,000 |
Improper Disposal |
| BJC Health System |
MO |
Business Associate |
287,876 |
Hacking/IT Incident |
| Saint Francis Healthcare Partners |
CT |
Business Associate |
38,529 |
Hacking/IT Incident |
| Everett & Hurite Ophthalmic Association |
PA |
Healthcare Provider |
34,113 |
Hacking/IT Incident |
| Management and Network Services, LLC |
OH |
Business Associate |
30,132 |
Hacking/IT Incident |
| Sanitas Dental Management |
FL |
Healthcare Provider |
19,000 |
Loss |
| Mediclaim, LLC |
MI |
Business Associate |
14,931 |
Hacking/IT Incident |
| Woodlawn Dental Center |
OH |
Healthcare Provider |
14,419 |
Hacking/IT Incident |
| Mat-Su Surgical Associates, APC |
AK |
Healthcare Provider |
13,146 |
Hacking/IT Incident |
| Mille Lacs Health System |
MN |
Healthcare Provider |
10,630 |
Hacking/IT Incident |
Causes of May 2020 Healthcare Data Breaches
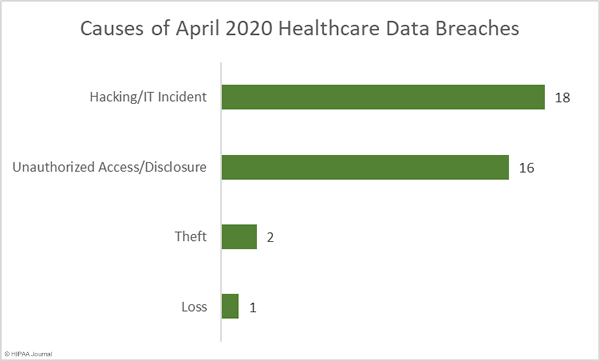
The largest healthcare data breach of the month affected Elkhart Emergency Physicians, Inc. and involved the improper disposal of paper records by business associate Central Files Inc. Elkhart Emergency Physicians was one of seven Indiana healthcare providers to be affected by the breach. In total, the records of 554,876 patients were exposed as a result of that improper disposal incident. There was one other improper disposal incident reported in May, making this the joint second biggest cause of data breaches in the month. Those improper disposal incidents accounted for 52.17% of breached records in May. The mean breach size was 69,434 records and the median breach size was 938 records.
There were 8 reported unauthorized access/disclosure incidents reported, although those breaches only accounted for 2.35% of breached records in May. The mean breach size was 3,124 records and the median breach size was 3,220 records.
Hacking/IT incidents once again topped the list as the main cause of healthcare data breaches, accounting for 39.28% of the month’s breaches and 43.69% of breached records in May. The mean breach size was 42,290 records and the median breach size was 14,419 records.
There was one loss incident involving a network server that contained the records of 19,000 patients. There were no reports of theft of physical records or devices containing electronic protected health information.
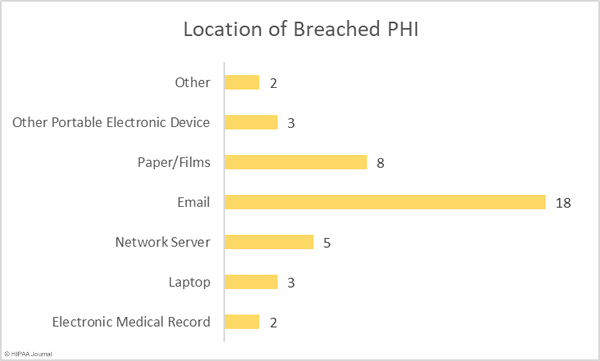
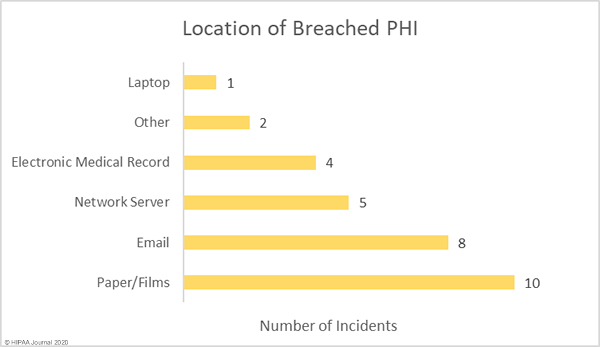
The graph below shows the location of breached protected health information. For the past several months, email has been the most common location of breached PHI due to the high number of healthcare phishing attacks. The number of reported phishing attacks dropped in May, hence the lower than average number of email-related breaches. While the number of incidents fell, there was one major phishing attack reported. An attack on BJC Health System saw 3 email accounts compromised. Those accounts included emails and attachments containing the PHI of 287,876 patients.
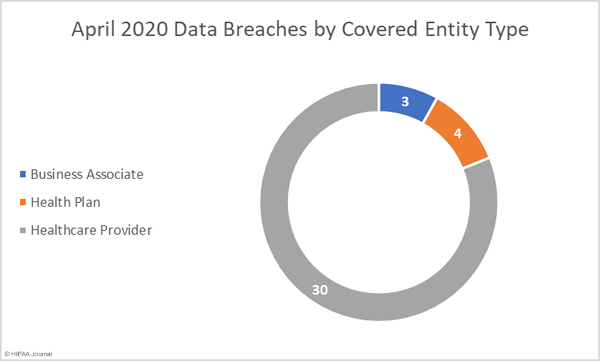
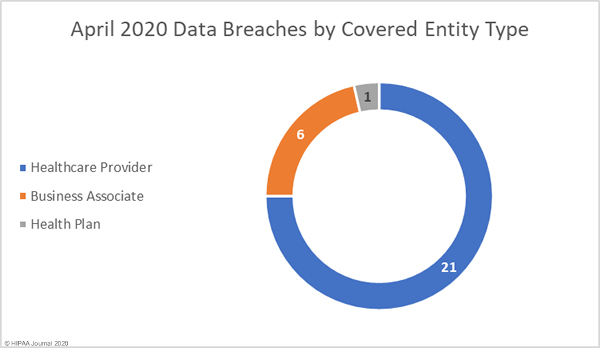
May 2020 Healthcare Data Breaches by Covered Entity Type
In line with virtually every other month since the HITECH Act mandated the HHS’ Office for Civil Rights to start publishing summaries of data breaches on its’ Wall of Shame’, healthcare providers were hardest hit, with 21 reported data breaches. It was a good month for health plans, with only one reported breach, but a particularly bad month for business associates. 6 business associates reported data breaches in May, and a further 8 breaches involved business associates but were reported by the covered entity.
Healthcare Data Breaches by State
Data breaches were reported by covered entities and business associates in 17 states in May. Indiana was the worst affected state with 7 reported breaches of 500 or more records, all of which were due to the improper disposal of records by business associate, Central Files, Inc.
There were 3 data breaches reported in each of Michigan and Ohio, two breaches reported by healthcare providers in Pennsylvania, and one breach was reported in each of Alaska, Arizona, California, Connecticut, Florida, Georgia, Illinois, Maryland, Minnesota, Missouri, Nebraska, New York, and Texas.
HIPAA Enforcement Activity in May 2020
There were no announcements about HIPAA penalties from the HHS’ Office for Civil Rights or state attorneys general in May 2020.
The post May 2020 Healthcare Data Breach Report appeared first on HIPAA Journal.