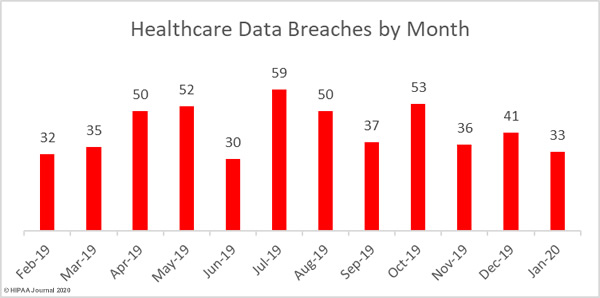
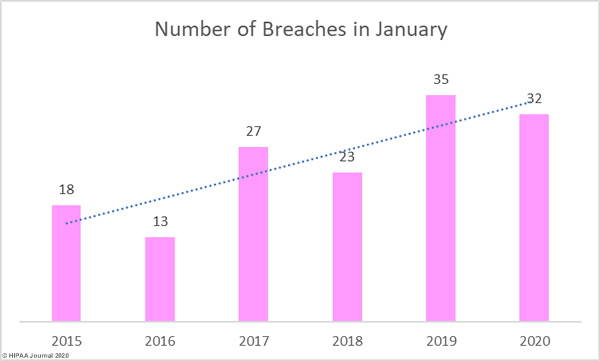
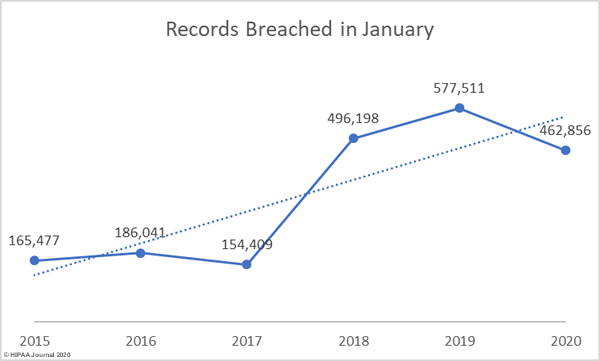
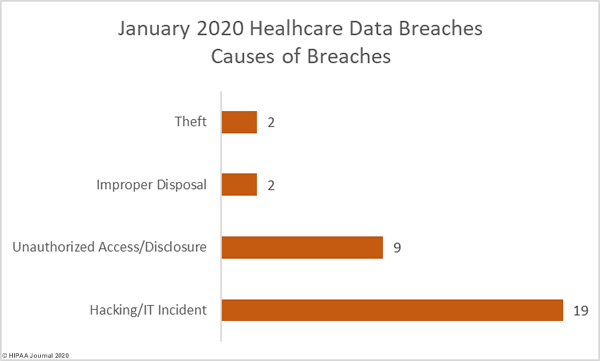
The 2019 Global State of Cybersecurity in Small and Medium-Sized Businesses Report from Keeper Security shows approximately two thirds of healthcare organizations have experienced a data breach in the past and 53% have experienced a breach of protected health information in the past 12 months.
The survey was conducted by the Ponemon Institute on 2,391 IT and IT security professionals in the United States, United Kingdom, DACH, Benelux, and Scandinavia, including 219 respondents from the healthcare industry.
Keeper Security reports indicates the average healthcare data breach results in the exposure of more than 7,200 confidential records and the average cost of a healthcare data breach is $1.8 million, including the cost of disruption to normal operations. The most common causes of healthcare data breaches are phishing attacks (68%), malware infections (41%), and web-based attacks (40%).
Healthcare data breaches have increased considerably in the past few years. Even though there is a high risk of an attack, healthcare organizations do not feel that they are well prepared. Only one third of IT and IT security professionals in the healthcare industry said they had enough budget to mount a strong defense to prevent cyberattacks. 90% of healthcare organizations devote less than 20% of their IT budget to cybersecurity, with an average allocation of just 13%. 87% said they did not have the personnel to achieve a more efficient cybersecurity posture. Even though emergency planning is a requirement of HIPAA, less than one third of respondents said they had a plan for responding to cyberattacks.
When asked about the importance of passwords for preventing data breaches, 66% of healthcare organizations agreed that good password security was an important part of their security defenses, but fewer than half of surveyed organizations have visibility into the password practices of their employees.
A second study conducted by the Ponemon Institute, on behalf of Censinet, shows healthcare vendors are also being targeted and are struggling to defend against cyberattacks. That survey revealed 54% of healthcare vendors have experienced at least one data breach in the past, and 41% of those respondents have experienced six or more data breaches in the past 2 years. For healthcare vendors, the average size of a data breach is over 10,000 records and the average cost of a breach is $2.75 million
When healthcare vendors experience a data breach it is common for customers to take their business elsewhere. 54% of healthcare vendors said a single data breach would result in a loss of business and 28% of healthcare vendors said they lost a customer when security gaps were discovered.
It is common for security gaps to go unnoticed, as 42% of respondents said healthcare providers do not require them to provide proof they are in compliance with privacy and data protection regulations. Even when security gaps are discovered, 41% of healthcare vendor respondents said they were not required to take any action.
Risk assessments are a requirement of HIPAA, but they are costly and time consuming to perform. Vendors spend an average of $2.5 million a year conducting risk assessments, but only 44% believe risk assessments improve their security posture which Censinet believes could be due to 64% of vendors finding risk assessments confusing and ambiguous.
59% of healthcare vendors said risk assessments become out of date within 3 months of being conducted, yet only 18% of respondents said their healthcare clients require them to complete risk assessments more than once a year.
“According to the research, 55 percent of vendors say that these certifications do not provide enough value for the cost, while 77 percent indicate challenges with the certification process, including respondents who believe it is too time-consuming, too costly and too confusing.” The solution could be automation. 61% of vendors believe workflow automation would streamline the risk assessment process and 60% believe workflow automation would reduce the cost of risk assessments by up to 50%.
The post 53% of Healthcare Organizations Have Experienced a PHI Breach in the Past 12 Months appeared first on HIPAA Journal.