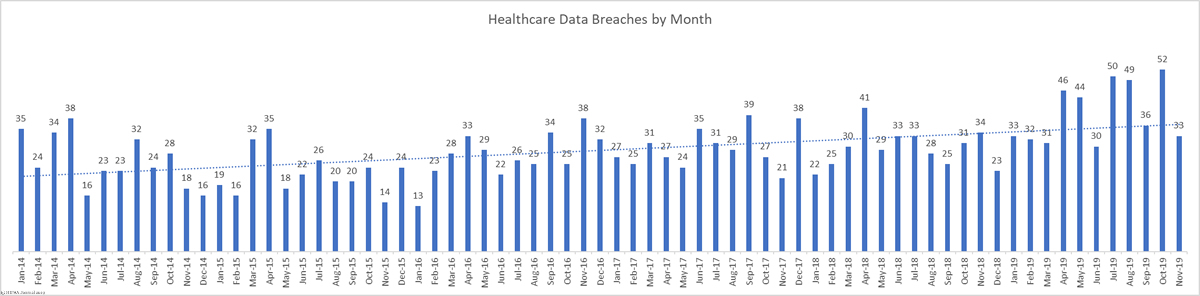
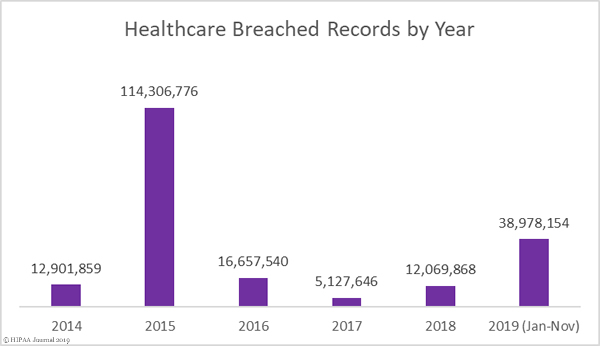
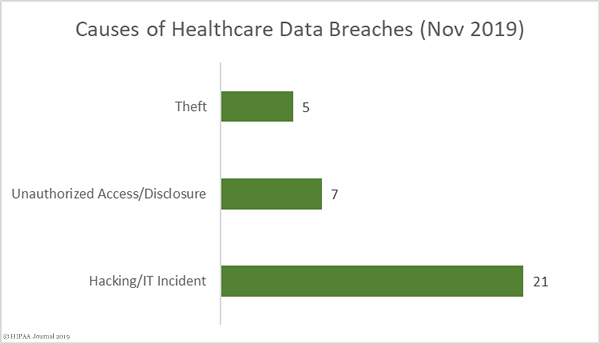
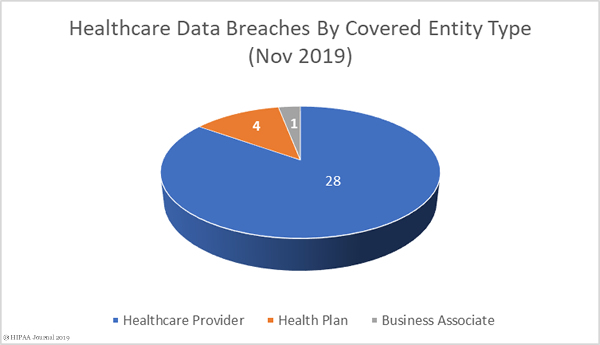
It has been another year of heavy enforcement of HIPAA compliance. HIPAA enforcement in 2019 by the Department of Health and Human Services’ Office for Civil Right (OCR) has resulted in 10 financial penalties. $12,274,000 has been paid to OCR in 2019 to resolve HIPAA violation cases.
2019 saw one civil monetary penalty issued and settlements were reached with 9 entities, one fewer than 2018. In 2019, the average financial penalty was $1,022,833.

Particularly egregious violations will attract financial penalties, but some of the HIPAA settlements in 2019 provide insights into OCRs preferred method of dealing with noncompliance. Even when HIPAA violations are discovered, OCR prefers to settle cases through voluntary compliance and by providing technical assistance. When technical assistance is provided and covered entities fail to act on OCR’s advice, financial penalties are likely to be issued.
This was made clear in two of the most recent HIPAA enforcement actions. OCR launched compliance investigations into two covered entities after being notified about data breaches. OCR discovered in both cases that HIPAA Rules had been violated. OCR chose to provide technical assistance to both entities rather than issue financial penalties, but the covered entities failed to act on the guidance and a financial penalty was imposed.
Sentara Hospitals disagreed with the guidance provided by OCR and refused to update its breach report to reflect the actual number of patients affected. West Georgia Ambulance was issued with technical guidance and failed to take sufficient steps to address the areas of noncompliance identified by OCR.
If you are told by OCR that your interpretation of HIPAA is incorrect, or are otherwise issued with technical guidance, it pays to act on that guidance quickly. Refusing to take corrective action is a sure-fire way to guarantee a financial penalty, attract negative publicity, and still be required to change policies and procedures in line with the guidance.
There were two important HIPAA enforcement updates in 2019. OCR adopted a new interpretation of the Health Information Technology for Economic and Clinical Health (HITECH) Act’s requirements for HIPAA penalties and a new enforcement initiative was launched.
The HITECH Act of 2009 called for an increase in the penalties for HIPAA violations. On January 25, 2013, the HHS implemented an interim final rule and adopted a new penalty structure. At the time it was thought that there were inconsistencies in the language of the HITECH Act with respect to the penalty amounts. OCR determined that the most logical reading of the HITECH Act requirements was to apply the same maximum penalty of $1,500,000 per violation category, per calendar year to all four penalty tiers.
In April 2019, OCR issued a notice of enforcement discretion regarding the penalties. A review of the language of the HITECH Act led to a reduction in the maximum penalties in three of the four tiers. The maximum penalties for HIPAA violations were changed to $25,000, $100,000, and $250,000 for penalty tiers, 1, 2, and 3. (subject to inflationary increases).
2019 saw the launch of a new HIPAA Right of Access enforcement initiative targeting organizations who were overcharging patients for copies of their medical records and were not providing copies of medical records in a timely manner in the format requested by the patient.
The extent of noncompliance was highlighted by a study conducted by Citizen Health, which found that 51% of healthcare organizations were not fully compliant with the HIPAA Right of Access. Delays providing copies of medical records, refusals to send patients’ PHI to their nominated representatives or their chosen health apps, not providing a copy of medical records in an electronic format, and overcharging for copies of health records are all common HIPAA Right of Access failures.
The two HIPAA Right of Action settlements reached so far under OCR’s enforcement initiative have both resulted in $85,000 fines. With these enforcement actions OCR is sending a clear message to healthcare providers that noncompliance with the HIPAA Right of Access will not be tolerated.
Right of Access violations aside, the same areas of noncompliance continue to attract financial penalties, especially the failure to conduct a comprehensive, organization-wide risk analysis. 2019 also saw an increase in the number of cited violations of the HIPAA Breach Notification Rule.
HIPAA Compliance Issues Cited in 2019 Enforcement Actions
| Noncompliance Issue |
Number of Cases |
| Risk Analysis |
5 |
| Breach Notifications |
3 |
| Access Controls |
2 |
| Business Associate Agreements |
2 |
| HIPAA Right of Access |
2 |
| Security Rule Policies and Procedures |
2 |
| Device and Media Controls |
1 |
| Failure to Respond to a Security Incident |
1 |
| Information System Activity Monitoring |
1 |
| No Encryption |
1 |
| Notices of Privacy Practices |
1 |
| Privacy Rule Policies and Procedures |
1 |
| Risk Management |
1 |
| Security Awareness Training for Employees |
1 |
| Social Media Disclosures |
1 |
OCR’s HIPAA enforcement in 2019 also clearly demonstrated that a data breach does not have occurred for a compliance investigation to be launched. OCR investigates all breaches of 500 or more records to determine whether noncompliance contributed to the cause of a breach, but complaints can also result in an investigation and compliance review. That was the case with both enforcement actions under the HIPAA Right of Access initiative.
The post HIPAA Enforcement in 2019 appeared first on HIPAA Journal.