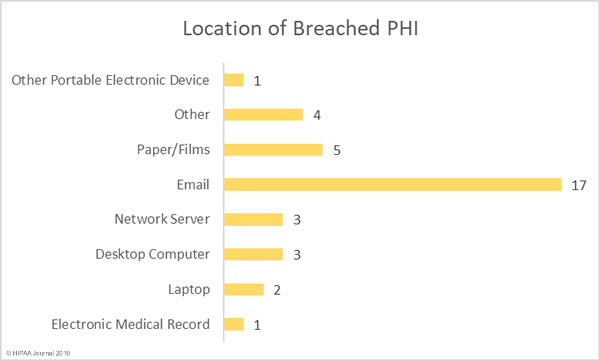
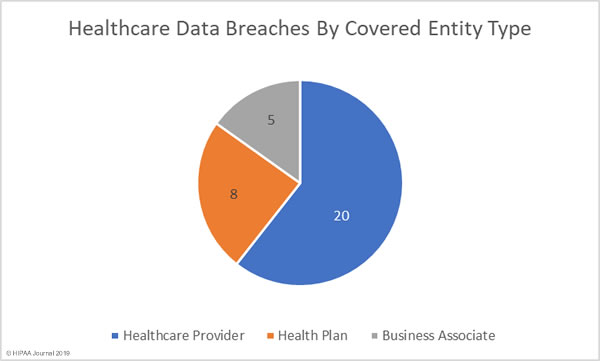
There are multiple new HIPAA regulations currently under consideration, and while some may be introduced as individual regulations, many could be combined into a HIPAA Omnibus Rule for 2024 similar to the HIPAA Omnibus Rule of 2013. The article below explains the proposed new HIPAA regulations in more detail and can be used in conjunction with our HIPAA compliance checklist to help better understand how the potential HIPAA updates for 2024 may impact HIPAA compliance.
Please use the form on this page to request your free copy of the checklist
Summary Of Article Contents
In recent years, new HIPAA regulations and changes attributable to related Acts have mostly had a minimal impact on HIPAA compliance. However, many of the anticipated HIPAA changes in 2024 could have a more significant impact.
The last major update to the HIPAA Rules was in 2013, when the HIPAA Omnibus Final Rule introduced new HIPAA regulations mandated by the Health Information Technology for Economic and Clinical Health (HITECH) Act. Since then, most HIPAA changes have consisted of amendments to existing standards to accommodate changes to other laws, Executive Orders, and new transaction code sets.
The next major update is now due, as OCR issued a Notice of Proposed Rulemaking (NPRM) on December 10, 2020, proposing a slew of changes to the HIPAA Privacy Rule. The Final Rule is expected to be published in the Federal Register at some point in 2024 now the comment period has closed. However, no date has been provided on when the Final Rule will be published, nor when the 2024 HIPAA changes will take effect (see the New HIPAA Regulations in 2024 section below).
For several years, new HIPAA regulations have been under consideration concerning how substance use disorder (SUD) and mental health information records are treated and protected. SUD records are covered by the Confidentiality of Substance Use Disorder Patient Records (42 CFR Part 2) regulations, which serve to protect the privacy of substance use disorder patients who seek treatment at federally assisted programs, whereas other healthcare data is covered under HIPAA.
There have been calls from many healthcare stakeholder groups to align the Part 2 regulations more closely with HIPAA so all healthcare data had equal protections. This would allow clinicians to view patients’ entire medical records, including SUD records, to get a complete view of a patient’s health history to inform treatment decisions. If details of treatment for SUD are withheld from doctors, there is a risk that a patient may be prescribed opioids when they are in recovery.
 While there are good reasons why these records need to be treated differently, as part of efforts to tackle the opioid crisis, the Substance Abuse and Mental Health Services Administration (SAMHSA) and the Office for Civil Rights (OCR) within the HHS have been considering changes to align the Part 2 regulations more closely with HIPAA.
While there are good reasons why these records need to be treated differently, as part of efforts to tackle the opioid crisis, the Substance Abuse and Mental Health Services Administration (SAMHSA) and the Office for Civil Rights (OCR) within the HHS have been considering changes to align the Part 2 regulations more closely with HIPAA.
There was progress on this front in 2020, through the Coronavirus Aid, Relief, and Economic Security (CARES) Act, which required the HHS to align the Part 2 regulations more closely with HIPAA, and in 2022, a Notice of Proposed Rulemaking was published in the Federal Register detailing Part 2 and HIPAA changes as mandated by the CARES Act to increase care coordination and better align these regulations.
New HIPAA Regulations and Part 2 Rulemaking
The CARES Act was passed by Congress on March 27, 2020, to ensure that every American has access to the care they need during the COVID-19 pandemic and to address the economic fallout from the SARS-CoV-2 and COVID-19. Individuals suffering from substance use disorder (SUD) must also be able to get the treatment they need during the COVID-19 pandemic, which has meant changes needed to be made to Part 2 regulations. The CARES Act improved Part 2 regulations by expanding the ability of healthcare providers to share the records of individuals with SUD but also tightening the requirements in the event of a breach of confidentiality.
The proposed changes to Part 2 regulations are based on the Legacy Act, which was introduced by Sens. Capito (R-WV) and Manchin (D-WV). Rather than having to obtain consent from a SUD patient for each use or disclosure, and for consent forms to state the specific parties with whom the information will be shared named in the consent form, patients can give broad consent for their SUD records to be shared for the purposes of treatment, payment, and healthcare operations.
The SUD records can then be shared by a covered entity or business associate for all treatment, payment, and healthcare operations (TPO) reasons, as is the case with HIPAA. Uses and disclosures must be limited to the minimum necessary information and consent can be withdrawn (in writing) by the patient at any time. The CARES Act also allows SUD information to be shared with a public health authority if it is de-identified in accordance with HIPAA Rules.
Protections have been put in place for SUD patients, which place limitations on the use of SUD records in criminal, civil, or administrative investigations or proceedings, and there are prohibitions on discrimination against patients suffering from SUD. Two new patient rights have been proposed, better aligning Part 2 with the HIPAA Privacy Rule. These are the right to an accounting of disclosures of SUD records and the right to request restrictions on disclosures for treatment, payment, and health care operations. Part 2 programs will also be required to establish a process to receive complaints about Part 2 violations, and will be prohibited from taking adverse action against patients who file complaints. Requiring patients to waive the right to file a complaint as a condition of providing treatment, enrollment, payment, or eligibility for services will also be prohibited.
Disclosures will be required to be made to the Secretary of the HHS for enforcement, and the HIPAA and HITECH Act civil and criminal penalties will apply to Part 2 violations. The same breach notification requirements as HIPAA will apply to breaches of Part 2 records by Part 2 programs, so any data breach will require the patient to be notified without unnecessary delay, and no later than 60 days from the discovery of the breach. The Part 2 confidentiality notice requirements will also align with the HIPAA Notice of Privacy Practices.
An update to HIPAA is also included in the Notice of Proposed Rulemaking, requiring the HIPAA Notice of Privacy Practices requirements to be updated for covered entities who receive or maintain Part 2 records to include a provision limiting re-disclosure of Part 2 records for legal proceedings per the Part 2 standards.
How are New HIPAA Regulations Introduced?
The process of implementing HIPAA updates is slow. Before any regulations are introduced, changed, or rescinded, the Department of Health and Human Services seeks feedback through a Request for Information (RFI) on aspects of HIPAA regulations that are proving problematic or, due to changes in technologies or practices are no longer as important as when they were originally published.
 After considering the comments and feedback received from the RFI, the HHS releases a Notice of Proposed Rulemaking (NPRM) which is followed by a comment period. Comments received from healthcare industry stakeholders are considered before a Final Rule is issued. HIPAA-regulated entities are then given a grace period to make the necessary changes before compliance with the new HIPAA regulations becomes mandatory and the HIPAA changes become enforceable.
After considering the comments and feedback received from the RFI, the HHS releases a Notice of Proposed Rulemaking (NPRM) which is followed by a comment period. Comments received from healthcare industry stakeholders are considered before a Final Rule is issued. HIPAA-regulated entities are then given a grace period to make the necessary changes before compliance with the new HIPAA regulations becomes mandatory and the HIPAA changes become enforceable.
The NPRM for the proposed HIPAA Privacy Rule changes was published in the Federal Register on January 21, 2021, and healthcare industry stakeholders were invited to submit comments on the 357-page proposal, with the deadline for submitting comments set as March 22, 2021. The proposed HIPAA Privacy Rule changes are far-reaching and affect almost everyone that interacts with the healthcare system. Due to the extent of the proposed HIPAA changes and their potential impact, the deadline for submitting comments was extended to May 6, 2021. OCR has yet to provide a date for when the Final Rule will be issued, but it is likely to result in HIPAA changes in 2024, although they may not become enforceable until the following year.
In April 2022, the HHS also released an RFI on how best to take into consideration the recognized security practices of the 2021 HIPAA Safe Harbor Law, and how to introduce a method of “settlement sharing” in which victims of data breaches could claim a percentage of civil monetary penalties as originally required (but never enacted) by §13410(c)(3) of the HITECH Act. OCR has yet to issue an NPRM on the settlement sharing, but this is one of the new HIPAA regulations in 2024 that is likely to be confirmed. A video presentation was published in response to the RFI on how HIPAA-regulated entities can demonstrate they have implemented recognized security practices, details of which are available here.
New HIPAA Regulations in 2024
There are expected to be new HIPAA regulations in 2024 when OCR publishes the final rule on the proposed changes to the HIPAA Privacy Rule. While there have been calls from industry stakeholders to make several other HIPAA updates, there are unlikely to be any other new HIPAA laws in 2023. Given the extent of the proposed HIPAA changes in 2022 through the Privacy Rule update and their impact on HIPAA-regulated entities, further notices of proposed rulemaking on HIPAA updates are unlikely in 2023.
Final Rule Expected on Proposed Changes to the HIPAA Privacy Rule
OCR issued a request for information in December 2018 asking HIPAA-covered entities for feedback on aspects of HIPAA Rules that were overly burdensome or obstructed the provision of healthcare, and areas where HIPAA updates could be made to improve care coordination and data sharing.
OCR was specifically looking at making changes to aspects of the HIPAA Privacy Rule that impede the transformation to value-based healthcare and areas where current Privacy Rule requirements limit or discourage coordinated care. The proposed changes to HIPAA include the easing of restrictions on disclosures of PHI that require authorizations from patients and several HIPAA changes to strengthen patient rights to access their own PHI. One proposed change that has attracted some criticism is the requirement to make the sharing of ePHI with other providers mandatory. Both the American Hospital Association (AHA) and the American Medical Association (AMA) have voiced their concern about the mandatory sharing of healthcare data, and also against another proposed change that shortens the timescale for responding to patient requests for copies of their medical records.
HHS Deputy Secretary Eric Hargan had previously explained that complaints had been received that some provisions of the HIPAA Privacy Rule are stopping patients and their families from getting the help they need and that changes are necessary to help with the fight against the current opioid crisis in the United States. HIPAA changes have also been proposed to reduce the administrative burden on HIPAA-covered entities.
The proposed new HIPAA regulations announced by OCR in December 2020 are as follows:
- Allowing patients to inspect their PHI in person and take notes or photographs of their PHI.
- Changing the maximum time to provide access to PHI from 30 days to 15 days.
- Requests by individuals to transfer ePHI to a third party will be limited to the ePHI maintained in an EHR.
- Individuals will be permitted to request their PHI be transferred to a personal health application.
- States when individuals should be provided with ePHI at no cost.
- Covered entities will be required to inform individuals that they have the right to obtain or direct copies of their PHI to a third party when a summary of PHI is offered instead of a copy.
- HIPAA-covered entities will be required to post estimated fee schedules on their websites for PHI access and disclosures.
- HIPAA-covered entities will be required to provide individualized estimates of the fees for providing an individual with a copy of their own PHI.
- Pathway created for individuals to direct the sharing of PHI maintained in an EHR among covered entities.
- Healthcare providers and health plans will be required to respond to certain records requests from other covered healthcare providers and health plans, in cases when an individual directs those entities to do so under the HIPAA Right of Access.
- The requirement for HIPAA-covered entities to obtain written confirmation that a Notice of Privacy Practices has been provided has been dropped.
- Covered entities will be allowed to disclose PHI to avert a threat to health or safety when harm is “seriously and reasonably foreseeable.” The current definition is when harm is “serious and imminent.”
- Covered entities will be permitted to make certain uses and disclosures of PHI based on their good faith belief that it is in the best interest of the individual.
- The addition of a minimum necessary standard exception for individual-level care coordination and case management uses and disclosures, regardless of whether the activities constitute treatment or health care operations.
- The definition of healthcare operations has been broadened to cover care coordination and case management.
- The Armed Forces’ permission to use or disclose PHI to all uniformed services has been expanded.
- A definition has been added for electronic health records.
Challenges Complying with the New HIPAA Regulations in 2024
The proposed changes to the HIPAA Privacy Rule are a cause of concern for many covered entities, business associates, and patient privacy advocates due to the potential impact they will have on the privacy and security of healthcare data, and the administrative and economic burden the changes may place on healthcare providers. While changes have been made to align the Part 2 regulations more closely with HIPAA, there has been criticism that the proposed changes have not gone far enough.
While some of the proposed changes to the HIPAA Privacy Rule are intended to ease the administrative burden on healthcare organizations, when the Final Rule is published, considerable time and effort will need to be put into implementing the changes. There will be a need to update HIPAA policies and procedures and communicate those changes to patients and health plan members. Employees will need to be given further HIPAA training, as the HIPAA Privacy Rule requires training to be provided whenever there is a material change to HIPAA policies. Training courses will need to be updated, and providing training to the workforce has the potential to cause workflow disruption. The Privacy Rule is largely concerned with restricting the uses and disclosures of PHI. The latest HIPAA changes introduce new requirements to make healthcare information flow more freely and improve access rights for patients. Implementing those HIPAA changes could well create challenges for healthcare organizations.
The Office for Civil Rights has been cracking down on violations of the HIPAA Right of Access when timely access to medical records is not provided, and the proposed HIPAA changes shorten the timeframe for providing those records. Based on the number of financial penalties for HIPAA Right of Access violations – 46 as of December 2023 – it is clear some healthcare providers have struggled to provide records within 30 days. Providing the records within 15 days will be particularly challenging, especially considering the maximum extension has also been shortened to 15 days.
Another area of concern is the definition of electronic health records, which includes billing records. Billing records will need to be provided when an individual requests a copy of their records. Billing records are often kept in a different system – not in the EHR – which can slow down the processing of requests for copies of medical records. The Privacy Rule change also prohibits unreasonable barriers to individuals exercising their right of access, such as unreasonable identity checks, which may be a cause of confusion as to what qualifies as ‘unreasonable’.
A definition has been added for Personal Health Application – an application used by an individual to access their health records. Healthcare organizations will be required to inform individuals about the privacy and security risks of sending their PHI to a third-party application, which is not required to have safeguards mandated by HIPAA. Healthcare providers are likely to have to develop their own patient warnings to ensure patients are made aware of the risks. A change has also been made that allows patients to orally request a copy of their PHI be sent to a third party. Healthcare organizations may struggle to implement the necessary changes to allow those requests to be processed correctly.
There has also been a change to the language of the HIPAA Privacy Rule regarding the need to provide copies of ePHI in the format requested by the individual. “Readily producible” copies of PHI now include copies requested through standards-based APIs using individuals’ personal health applications. It may not be easy for some healthcare providers to provide records in those formats, as they may be restricted by the EHR system they have implemented.
The new HIPAA regulations will allow patients to inspect their PHI in person and take notes and photographs. That too will create challenges, as patients will need to be allowed to inspect their PHI privately, and care will need to be taken to ensure they are not photographing PHI they are not authorized to – such as the PHI of others or any of their own PHI that is excluded from the HIPAA Right of Access. HIPAA-covered entities will need to determine how best to provide that information. It may be necessary to create an area where records can be viewed electronically, and even to supervise individuals who are inspecting their PHI in person. In-person requests to inspect PHI will also need to be provided free of charge, even though providing in-person access has the potential to have a cost impact on a HIPAA-covered entity.
As these issues show, while the changes in many cases are minor, the implications for HIPAA-covered entities are considerable. It will likely take considerable planning and resources to implement all of the changes, update policies and procedures, and provide training to the workforce. Efforts to implement the new HIPAA changes will need to be initiated promptly after the Final Rule is published to ensure it is possible to be compliant with any new HIPAA regulations in 2024, and certainly by the effective date.
Latest HIPAA Updates Relating to Transaction Code Sets
 In the introduction to this article, it was mentioned that most HIPAA changes have consisted of amendments to existing standards to accommodate changes to other laws, Executive Orders, and new transaction code sets. While it is understandable that most covered entities’ attention may be focused on the proposed modifications to the Privacy Rule, it is important to keep up to date with the latest HIPAA updates relating to transaction code sets.
In the introduction to this article, it was mentioned that most HIPAA changes have consisted of amendments to existing standards to accommodate changes to other laws, Executive Orders, and new transaction code sets. While it is understandable that most covered entities’ attention may be focused on the proposed modifications to the Privacy Rule, it is important to keep up to date with the latest HIPAA updates relating to transaction code sets.
This is because, in December 2022, HHS’ Centers for Medicare and Medicaid Services (CMS) published a proposed rule that would add three new transaction codes to the existing transaction code sets. The new transaction codes are to enable the electronic transmission of healthcare attachment transactions – transactions in which further information is provided to support an authorization request or a bill, or to preempt a query relating to a bill.
Currently, healthcare attachment transactions are sent by fax or mail and, by facilitating the electronic transmission of these transactions, the new transaction codes will accelerate authorizations, treatments, and payments. However, to validate their authenticity, electronically transmitted healthcare attachment transactions will have to be digitally signed by software capable of supporting the HL7 IF for CDA R2 protocol.
These latest HIPAA updates relating to transaction code sets could be significant for all covered entities that already use e-signatures in day-to-day healthcare operations (i.e., Business Associate Agreements, remote authorizations for uses and disclosures not permitted by the Privacy Rule, e-prescribing, etc.) if the e-signature requirements are extended to other HIPAA-covered transactions, and then to day-to-day healthcare operations.
HIPAA Privacy Rule Changes Proposed after Dobbs
In June 2022, the Supreme Court delivered a decision in the case of Dobbs v. Jackson Women’s Health Organization which overruled previous rulings that the Constitution of the United States protects a pregnant individual’s liberty to have an abortion. The decision led to many anti-abortion states passing laws that prohibited or restricted terminations, and resulted in tens of thousands of women crossing state lines to terminate pregnancies.
Anti-abortion states are unable to prevent women from crossing state lines for terminations, but some have introduced legislation that criminalizes assisting or facilitating an abortion procedure. In response, neighboring states are introducing “shield” laws to prevent the extraterritorial application of anti-abortion legislation and protect their citizens from being charged for assisting or facilitating an event that is safe and legal in their home state.
The patchwork of state legislation is a concern to OCR due to possible uses or disclosures of PHI in extraterritorial civil, criminal, or administrative investigations or proceedings. Currently, covered entities are permitted to disclose PHI for judicial and administrative proceedings under §164.512(e) of the Privacy Rule, and OCR believes this may result in patients withholding information from healthcare providers. To mitigate the risk of patients withholding information, the agency is proposing:
- A definition of “reproductive health care” is added to HIPAA. This definition will not only cover terminations, but also contraception, fertility, and miscarriage health care.
- New limitations will be imposed on the uses and disclosures of PHI relating to reproductive health care that cannot be bypassed by obtaining consent or an authorization.
- The limited uses and disclosures will be subject to an attestation that PHI will not be further used or disclosed for an out-of-state judicial or administrative proceeding.
- The proposed HIPAA Privacy Rule changes will also clarify that providing or facilitating reproductive health care is not abuse, neglect, or domestic violence.
- To reassure patients that PHI relating to reproductive health care will not be used or disclosed, a new section must be added to existing Notices of Privacy Practices.
In the Notice of Proposed Rulemaking (88 FR 23506), OCR notes that a false attestation that PHI relating to reproductive health care will not be further used or disclosed constitutes a violation of §1177 of the Social Security Act (wrongful disclosures of individually identifiable health information). OCR also notes that if reproductive health care data is disclosed in violation of the proposed HIPAA Privacy Rule changes, the disclosure will qualify as a notifiable data breach.
Recent Changes to HIPAA Enforcement
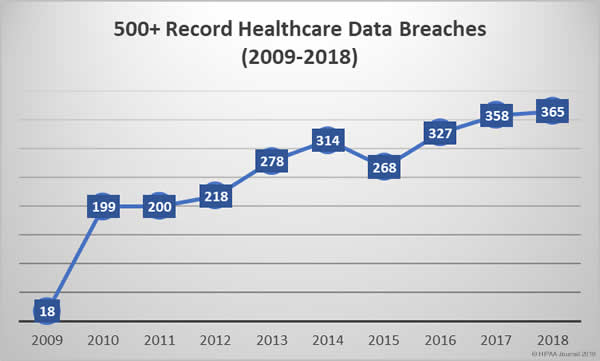
Halfway through 2018, OCR had only agreed to three settlements with HIPAA-covered entities to resolve HIPAA violations and its enforcement actions were at a fraction of the level in the previous two years. It was starting to look like OCR was easing up on its enforcement of compliance with the HIPAA Rules. However, OCR announced many more settlements in the second half of the year and closed 2018 on 10 settlements and one civil monetary penalty – One more penalty than in 2018. 2018 ended up being a record year for HIPAA enforcement. The final total for fines and settlements was $28,683,400, which beat the previous record set in 2016 by 22%.
OCR’s enforcement activities continued at a high level in 2019 and OCR closed the year with 10 settlements and civil monetary penalties, totaling $12,274,000. In late 2019, OCR announced it was embarking on a new enforcement drive focused on compliance with the HIPAA Right of Access, which requires individuals to be provided with timely access to their medical records for only a reasonable, cost-based fee.
OCR settled two cases in 2019 under this initiative – both for $85,000 – and a further 11 settlements were announced in 2020 to resolve potential violations of the HIPAA Right of Access. In addition to noncompliance with the HIPAA Right of Access, OCR imposed financial penalties for particularly egregious cases of noncompliance. The failure to conduct comprehensive risk analyses, poor risk management practices, lack of HIPAA policies and procedures, no business associate agreements, impermissible PHI disclosures, and a lack of safeguards all attracted HIPAA fines in 2020. 2020 saw more financial penalties imposed for violations of the HIPAA Rules than any other year, with the year closing with 19 settlements totaling $13,554,900.
There was a slight reduction in HIPAA enforcement actions in 2021, with 14 financial penalties announced to resolve HIPAA violations, the majority of which (12) were for violations of the HIPAA Right of Access. Aside from one financial penalty of $5,100,000 for Excellus Health Plan, the financial penalties were far lower in 2021 than in recent years, with penalties totaling $5,982,150 for the year. 2021 also saw an increase in the number of penalties for small healthcare providers.
The trend for smaller penalties continued in 2022, in part due to the nature of the HIPAA violations being enforced and also the new penalty structure OCR adopted (see the Penalty Structure for Violations of HIPAA Regulations section below). OCR continued with its heavy focus on the enforcement of compliance with the HIPAA Right of Access, which typically involves a failure to provide one individual with a copy of their medical records, rather than widespread non-compliance with the HIPAA Rules. The average penalty amount in 2022 was $98,688, with a median penalty of $50,000.
2022 saw more settlements and civil monetary penalties imposed (22) than in any other year to date, yet 2022 saw the lowest fine total since 2010, with $2,127,140 in financial penalties imposed. The second lowest of any full year since OCR was given the authority to enforce HIPAA compliance. Another trend that became clear in 2022 was OCR pursuing financial penalties against smaller healthcare organizations. 55% of all fines imposed in 2022 were on small medical practices.
HIPAA Civil Monetary Penalty Overturned
In 2018, OCR imposed a civil monetary penalty of $4,348,000 on the University of Texas MD Anderson Cancer Center. OCR launched an investigation into three data breaches that collectively resulted in an impermissible disclosure of PHI of almost 35,000 individuals. The incidents occurred in 2012 and 2013 and involved the theft of an unencrypted laptop computer and two flash drives.
OCR determined MD Anderson had violated the HIPAA Rules by failing to encrypt the devices. In April 2019, MD Anderson appealed the fine alleging the HHS did not have the authority to impose the penalty and that it was excessive. In January 2021, the penalty was overturned and OCR admitted it could not defend a fine of more than $450,000. The case was remanded for further proceedings and the civil monetary penalties were vacated by the Fifth Circuit Court of Appeals. The judge stated the civil monetary penalties were “arbitrary, capricious and otherwise unlawful.”
The overturning of the HIPAA fine is thought to have forced OCR to change its approach to HIPAA enforcement as the successful appeal may encourage other covered entities to appeal any proposed financial penalties for HIPAA violations. In 2022, financial penalties were imposed for a variety of reasons, but the majority were for HIPAA Right of Access violations, which appears to be safe ground.
HIPAA enforcement in 2024 is expected to encompass a much wider range of HIPAA violations. In an effort to improve efficiency, OCR restructured and created three new divisions to better utilize the skillsets of its staff. OCR has had a flat budget for years, but its workload has increased significantly with a 69% increase in complaints between 2017 and 2022 and a 58% increase in data breaches between 2017 and 2021.
The restructuring will make better use of OCR’s resources to improve efficiency, which will help the department address the current backlog of investigations and conduct more timely investigations, especially investigations of hacking incidents which could lead to an increase in enforcement actions. OCR has also stated its intention to make the enforcement of reproductive health care privacy violations a priority in 2024.
OCR Gets a New Director
In September 2021, 8 months into the Biden administration, Lisa J. Pino was appointed as the new OCR Director, taking over from acting OCR director Robinsue Frohboese who headed the agency since the resignation of Roger Severino in January 2021. In contrast to past directors, Pino had cybersecurity and data breach experience, having served as a senior executive service official and senior counsel in the U.S. Department of Homeland Security (DHS). Pino’s cybersecurity experience was expected to see a change in how OCR conducts investigations of data breaches, especially in light of the HIPAA Safe Harbor Law. However, Piso left the role in July 2022, less than a year into her tenure, and Melanie Fontes Rainer was appointed OCR Director. It is unclear what direction she will take OCR in.
Penalty Structure for Violations of HIPAA Regulations in 2024
In 2019, there was a notable HIPAA change related to enforcement action. OCR issued a Notice of Enforcement Discretion after reinterpreting the requirements of the HITECH Act regarding penalties for non-compliance with the HIPAA Rules. The HITECH Act called for an increase in penalties for non-compliance with the HIPAA Rules and at the time, the HHS interpreted the language of the HITECH Act as requiring a cap of $1.5 million for HIPAA violations across all four penalty tiers. In 2019, the requirements of the HITECH Act were reassessed and interpreted differently. Rather than capping the penalties across all four tiers at the same amount, different maximum fines (adjusted for inflation) were set for each of the four tiers, as detailed in the table below.
| Annual Penalty Limit | Annual Penalty Limit | Minimum Penalty per Violation | Maximum Penalty per Violation | Annual Penalty Cap |
| Tier 1 | Lack of Knowledge | $137 | $34,464 | $34,464 |
| Tier 2 | Reasonable Cause | $1,379 | $68,928 | $137,886 |
| Tier 3 | Willful Neglect | $13,785 | $68,928 | $344,638 |
| Tier 4 | Willful neglect (not corrected within 30 days | $68,928 | $68,928 | $2,067,813 |
This table reflects the penalty values published in the Federal Register on October 6, 2023, and the Enforcement Discretion Caps announced in April 2019. Since the change was addressed through a Notice of Enforcement Discretion, it is not legally binding but will remain in effect indefinitely.
New HIPAA Regulations in 2021
While there were no changes to HIPAA regulations in 2021, new legislation was introduced related to the HIPAA Privacy and Security Rules in terms of cybersecurity, patient access to healthcare data, and HIPAA enforcement.
2021 HIPAA Safe Harbor Law Updating the HITECH Act
On January 5, 2021, the HIPAA Safe Harbor Bill (HR 7898) was signed into law by President Trump and amended the HITECH Act. The purpose of the HIPAA Safe Harbor Bill was to encourage healthcare organizations to adopt “recognized security practices” to improve their defenses against cyberattacks.
The HIPAA Safe Harbor Bill instructs the HHS to take into account the cybersecurity best practices that a HIPAA-regulated entity has adopted, which have been consistently in place for the 12 months preceding any data breach when considering HIPAA enforcement actions and calculating financial penalties related to security breaches and HIPAA Security Rule violations.
The name of the bill is a little misleading, as the HITECH Act amendment does not create a safe harbor where HIPAA-regulated entities avoid any audits or financial penalties for data breaches and/or Security Rule violations. The bill requires the HHS to decrease the length and extent of any audits in response to those breaches if recognized security practices have been implemented, and financial penalties will be reduced, but not avoided entirely.
If a HIPAA-regulated entity can adequately demonstrate that Recognized security practices have been implemented for 12 months, it will be considered by OCR as a mitigating factor. Organizations that have adopted recognized security practices and have completed a HIPAA Security Risk Analysis, identified risks to the confidentiality, integrity, and availability of electronic protected health information (ePHI) and have reduced them to a low and acceptable level, and have implemented technical safeguards to protect ePHI, will be treated more leniently by OCR. Financial penalties will not be increased for HIPAA-regulated entities that do not implement recognized security practices.
In addition to facing lower penalties and sanctions, HIPAA-regulated entities that adopt recognized security practices and are compliant with the requirements of the HIPAA Security Rule will be better protected against security incidents and data breaches.
21st Century Cures Act
The 21st Century Cures Act (Cures Act) of 2016 was introduced to encourage innovation in medical research, and one of the ways that this was achieved was to make it easier for patients to obtain their healthcare data and share that information with research institutions. The Cures Act called for the HHS to create a new Rule that would improve the flow of healthcare data between providers, patients, and developers of Health IT such as electronic health record (EHR) vendors.
The HHS’ Office of the National Coordinator for Health Information Technology (ONC) published its Interoperability and Information Blocking Final Rule in March 2020, and healthcare providers, developers of Certified Health IT, and health information networks or exchanges were given until November 2, 2020, comply with the information blocking provisions of the Final Rule, although the compliance date was then extended to April 5, 2021, due to the COVID-19 pandemic.
The Centers for Medicare and Medicaid Services (CMS) also published an interoperability rule in March 2020 that applies to Medicare- and Medicaid-participating short-term acute care hospitals, long-term care hospitals, rehabilitation hospitals, psychiatric hospitals, children’s hospitals, cancer hospitals, and critical access hospitals (CAHs). The compliance date for the CMS Rule was July 1, 2021, and the CMS is now enforcing compliance.
Under the CMS Final Rule, CMS-regulated payers including Medicare Advantage (MA) organizations, Medicaid Fee-for-Service (FFS) programs, Medicaid managed care plans, CHIP FFS programs, CHIP managed care entities, and QHP issuers, must implement and maintain a secure, standards-based Application Programming Interface (API) to allow patients to access their claims and receive information through a third-party app of their choice, make provider directory information publicly available through a standards-based API, and send electronic patient event notifications of a patient’s admission, discharge, or transfer to another healthcare facility or another community provider or practitioner.
The final interoperability and information-blocking rules do not amend HIPAA or the HITECH Act, although they are related. The final rules promote patient access to ePHI and are intended to make access easier. It is possible that HIPAA policies and procedures could violate the ONC Final Rule if they include practices considered to constitute information blocking. Any entity that engages in information blocking can face financial penalties, which are capped at $1 million (adjusted annually for inflation).
Proposed HIPAA Security Rule Changes in 2024
Since the publication of the Omnibus Final Rule in 2013, there have been minor HIPAA updates to the Privacy Rule, amendments to the HIPAA Enforcement Rule to account for inflation, and new HIPAA Part 162 requirements, but no changes – other than a technical correction – to the Security Rule. This will likely change in 2024 due to the publication of a Healthcare Sector Cybersecurity “concept paper” that outlines four concurrent steps HHS will be taking to improve cyber resiliency and protect patient safety:
- Establish voluntary cybersecurity goals for the healthcare sector
- Provide resources to incentivize and implement cybersecurity practices
- Implement an HHS-wide strategy to support greater enforcement and accountability
- Expand and mature the one-stop shop within HHS for healthcare sector cybersecurity.
In the context of proposed HIPAA Security Rule changes in 2024, the third of the steps aims to have all hospitals meeting sector-specific Cybersecurity Performance Goals (CPGs). To achieve this aim, CMS will propose new cybersecurity requirements for hospitals in the Medicare and Medicaid programs, while OCR will introduce new standards in the Security Rule and petition Congress for increased resources to investigate HIPAA violations and increased penalties for HIPAA violations.
HIPAA Changes in 2020/2021 Due to the COVID-19 Pandemic Ended on May 11, 2023
The COVID-19 pandemic has not resulted in any permanent changes to HIPAA, but it has seen unprecedented flexibilities introduced on a temporary basis to make it easier for healthcare providers and business associates on the front line in the fight against COVID-19.
During emergency situations such as disease outbreaks, the HIPAA Rules remain in effect and the requirements of the HIPAA Privacy Rule, Security Rule, and Breach Notification Rule remain unchanged. However, enforcement of compliance may be eased.
OCR announced three Notices of Enforcement Discretion in 2020 and one in 2021 in response to the COVID-19 pandemic, which will see penalties and sanctions for certain HIPAA violations waived for the duration of the COVID-19 nationwide public health emergency.
The Notices of Enforcement Discretion are as follows, and remain in place until the COVID-19 Public Health Emergency (PHE) ends. On April 11, 2023, OCR confirmed that the Secretary of the Department of Health and Human Services will not be renewing the COVID-19 Public Health Emergency, which is due to expire on May 11, 2023. The flexibilities introduced through the following Notifications of Enforcement Discretion will end at 11:59 pm on May 11, 2023. There will, however, be a 90-day transition period with regard to telehealth. OCR will continue to exercise enforcement discretion with regard to the good faith provision of telehealth services until 11:59 pm on August 11, 2023.
Good Faith Telehealth Remote Communications During the COVID-19 Nationwide Public Health Emergency
The first Notice of Enforcement Discretion in relation to COVID-19 was announced by OCR on March 17, 2020, and concerns the good faith provision of telehealth services. OCR is waiving potential penalties for HIPAA violations by healthcare providers that provide virtual care to patients through everyday communications technologies during the COVID-19 nationwide public health emergency.
This means healthcare providers are permitted to use everyday communications tools to provide telehealth services to patients, even if those tools would not normally be considered fully HIPAA compliant.
Platforms such as FaceTime, Skype, Zoom, and Google Hangouts video can be used in the good faith provision of telehealth services to patients without penalty for the duration of the public health emergency. However, public-facing platforms such as TikTok and Facebook Live must not be used.
Good Faith Uses and Disclosures of Protected Health Information by Business Associates for Public Health and Health Oversight Activities
On April 2, 2020, OCR announced it would be exercising enforcement discretion and would not impose sanctions and penalties on business associates of HIPAA-covered entities for uses and disclosures of PHI for public health and health oversight activities. HIPAA prohibits these uses and disclosures unless it is stated in a business associate agreement (BAA) that the disclosures are permitted. For the duration of the public health emergency, business associates will not face penalties for these uses and disclosure, provided they notify the covered entity after the event, within 10 days of the use or disclosure occurring.
Participation in the Operation of Community-Based Testing Sites During the COVID-19 Nationwide Public Health Emergency
On April 9, 2020, OCR announced it will be exercising enforcement discretion for noncompliance with HIPAA Rules in relation to the good faith participation in the operation of COVID-19 testing sites and will refrain from imposing sanctions and penalties on covered entities and business associates at drive-through, walk-up, and mobile sites.
The Notice of Enforcement Discretion covers the operation of these sites and all activities that support the collection of specimens from individuals for COVID-19 testing only. While penalties will not be applied, “OCR encourages covered health care providers participating in the good faith operation of a CBTS to implement reasonable safeguards to protect the privacy and security of individuals’ PHI.”
The Notice of Enforcement Discretion is retroactive to March 13, 2020.
Notice of Enforcement Discretion Regarding Online or Web-Based Scheduling Applications for Scheduling of COVID-19 Vaccination Appointments
OCR announced a further Notice of Enforcement Discretion on January 19, 2021, to help HIPAA-covered entities with the rollout of COVID-19 vaccines.
OCR said HIPAA sanctions and penalties will not be imposed on HIPAA-covered entities or their business associates in relation to the good faith use of online or web-based scheduling applications (WBSAs) for scheduling COVID-19 vaccination appointments.
WBSAs can be used for scheduling COVID-19 vaccination appointments, even if their use would not normally be considered fully compliant with the HIPAA Rules (e.g., no business associate agreement).
The Notice of Enforcement Discretion does not cover the use of WBSAs for scheduling vaccination appointments if the WBSA provider has prohibited the use of its WBSA for making healthcare appointments. Enforcement discretion will not apply if the WBSA is used for anything other than booking COVID-19 appointments, such as arranging appointments for other medical services or for conducting screening for COVID-19 prior to arranging an in-person healthcare visit.
Any WBSA must have privacy and security safeguards that can be activated to ensure the privacy and confidentiality of healthcare data, and OCR encourages HIPAA-covered entities and their business associates to ensure that safeguards are implemented, such as the use of encryption, if possible, adhering to the minimum necessary standard, and activating all privacy controls.
The Notice of Enforcement Discretion took effect on January 19, 2021, and is retroactive to December 11, 2020.
New HIPAA Regulations FAQs
Once a Notice of Proposed Rulemaking has been issued, is it guaranteed there will be a change to the HIPAA Rules?
Once a Notice of Proposed Rulemaking has been issued, it is not guaranteed there will be a change to the HIPAA Rules. For example, in 2014, the Department of Health & Human Services issued a Notice of Proposed Rulemaking that would have required health plans to prove compliance with certain areas of the Administration Simplification standards via certification. The proposed Rule was withdrawn in 2017 due to concerns it would place a significant burden on employers’ self-funded health plans.
How likely is it that all the new HIPAA regulations being proposed in the current NPRM will be adopted?
There is a low likelihood that all the new HIPAA regulations being proposed in the current NPRM will be adopted. The American Hospital Association (AHA) is one of a number of stakeholders that have raised concerns about the proposed changes – particularly changes relating to a reduction in the maximum time allowed to respond to patient requests, allowing patients to photograph PHI, and transferring PHI to personal health applications.
Will there definitely be some new HIPAA regulations in 2024?
It is impossible to know if there will definitely be some new HIPAA regulations in 2024. It can take years for relatively simple Rules (such as the NICS Rule) to be finalized; and, due to potential conflicts between the proposed new HIPAA regulations, 42 CFR Part 2 regulations (relating to the confidentiality of substance use disorder patient records), and Cures Act regulations, it could be some time until any new HIPAA regulations are finalized.
How much disruption might the new HIPAA regulations create?
The disruption the new HIPAA regulations might create depends on how many of the proposals are adopted in the Final Rule. If patients are allowed to photograph PHI or the maximum time allowed to respond to patient requests is reduced, this will create significant disruption in terms of developing new policies and procedures, training employees on the new policies and procedures, and monitoring compliance.
When a Final Rule is published, will covered entities have to comply with it immediately?
When a Final Rule is published, it is unlikely covered entities will have to comply with it immediately. In most cases, covered entities have 90 or 180 days to comply with a rule change depending on its complexity. When the original Privacy Rule Final Rule was published in 2002, covered entities were given a year to make systems, policies, and procedures HIPAA compliant. Small health plans were given two years. If a Final Rule is published in 2024, OCR will most likely allow an appropriate period of time for covered entities to make the necessary adjustments.
Are HIPAA laws still in effect?
The HIPAA laws are still in effect unless a state has adopted regulations with more stringent privacy and security protections or greater individual rights. In some states, laws exist that have more stringent elements than HIPAA (for example, with regards to the privacy of AIDS patients), and in these states, the more stringent elements pre-empt the equivalent standards of HIPAA, but the remaining HIPAA laws are still in effect.
Can HIPAA be overturned?
HIPAA can be overturned by Congress; and, while there have been attempts in the past to repeal certain parts of the Act (for example, the requirement to develop a system of National Patient Identifiers), no part of HIPAA has been overturned to date. However, there have been numerous additions to HIPAA through the Rules added to the Administrative Simplification provisions and via the passage of the HITECH Act in 2009.
Will there be new HIPAA rules for text messaging and email in 2024?
New HIPAA rules for text messaging and email are not currently on the agenda for 2024, and it is likely that – because of the risks associated with these two methods of unsecure communication – there will not be any changes to the existing rules. Organizations using these communication channels are advised to warn individuals of the risks of communicating PHI by text messaging and email, and document the warning. Thereafter, if the individual still requests to be contacted by either of these methods, document the request.
When was HIPAA last updated?
HIPAA was last updated in 2020 when the Department of Health and Human Services published a Final Rule relating to the codes used in Part 162 of the HIPAA Administrative Simplification provisions. Because the changes to the code only affected retail pharmacy transactions for Schedule II drugs, the update did not receive a lot of attention. However, the next planned round of HIPAA updates to Part 162 affects more organizations and will likely see the update covered more widely.
Does HIPAA have to be signed yearly?
HIPAA does not have to be signed yearly, but Congress has to be kept informed of its effectiveness via several annual and semi-annual reports. Congress could – if it wished – repeal some or all of the Act, but so much of HIPAA is entwined with other state and federal privacy and security laws, that this is an unlikely option.
Would the changes to HIPAA in 2024 require policy revisions?
Many proposed changes to HIPAA in 2024 will require policy revisions. For example, the changes to HIPAA relating to patients inspecting PHI in person and being able to take notes or photographs will require policy revisions for covered entities in the healthcare sector. Because these policy changes will affect large groups of the workforce, there will also have to be “material change” training.
When were the most recent HIPAA changes to the Privacy Rule?
The most recent HIPAA changes to the Privacy Rule were in 2016 when a new sub-section was added to 45 CFR 164.512 to include reporting to the National Instant Criminal Background Check System among the permitted uses and disclosures of PHI for which an authorization or opportunity to agree or object is not required.
How will the proposed HIPAA changes 2024 affect the Security Rule safeguards?
The proposed HIPAA changes 2024 to support the Healthcare Sector Cybersecurity concept paper will affect the Security Rule safeguards as the concept paper states there will be “new cybersecurity standards”. While these may affect some Administrative Safeguards (i.e., security management, contingency planning, and security awareness training), most of the new cybersecurity standards should appear as Technical Safeguards.
In the absence of new HIPAA regulations in 2024 to support Healthcare Sector Cybersecurity, the other proposed HIPAA changes 2024 are unlikely to affect the Security Rule safeguards unless new implementation specifications are adopted to facilitate the transfer of PHI to personal health applications. Any other HIPAA changes to the Security Rule will more likely be in the Security Rule’s General Rules (45 CFR §164.306) rather than the Administrative, Physical, or Technical Safeguards.
What was the name of the last update to HIPAA?
The name of the last update to HIPAA in 2016 was “Administrative Simplification: Modification of the Requirements for the Use of Health Insurance Portability and Accountability Act of 1996 (HIPAA) National Council for Prescription Drug Programs (NCPDP) D.0 Standard”. The name of the last major update to HIPAA was the “Omnibus HIPAA Final Rule” in 2013.
Where can I find the current HIPAA regulations?
To find the current HIPAA regulations, you can visit www.ecfr.gov and navigate to Title 45, Subtitle A, Subchapter C – “Administrative Data Standards and Related Requirements”. This Subchapter contains the current General Rule, Privacy Rule, Security Rule, and Breach Notification Rule among other HIPAA regulations relating to data standards, enforcement procedures, and the imposition of fines.
It is important to be aware of other federal laws closely related to HIPAA (i.e., 42 CFR Part 2 and §1177 of the Social Security Act) and that some state laws pre-empt HIPAA or exempt HIPAA covered entities. It is also important to be aware that the Combined Regulation Text published by the Dept. for Health and Human Services is not an up-to-date version of the current HIPAA regulations.
How often does HIPAA need to be updated?
There are no regulations that stipulate how often HIPAA needs to be updated. However, Parts of the Act are updated every few years to accommodate other acts of legislation (i.e., the NICS changes in 2016 were attributable to an amendment to the Brady Gun Law), to introduce new transaction codes for recently developed drugs and medical products, or to close loopholes in claims procedures.
Will there be changes to the HIPAA laws regarding minors in 2024?
There will not be any changes to the HIPAA laws regarding minors in 2024 – even if the proposed HIPAA Privacy Rule changes in 2024 for reproductive health are finalized – because under HIPAA minors are either “unemancipated” (i.e., subject to the control, authority, and supervision of their patents) or “emancipated” (i.e., living independently as an adult regardless of their age).
As an unemancipated minor can be as old as 21 years in some jurisdictions and an emancipated minor as young as 14 years in others (subject to court approval), it would be impossible for HHS to change the HIPAA laws regarding minors in 2024 without creating further challenges with regards to minors’ personal representatives (i.e., parents, guardians, etc.) and providers’ good faith beliefs about what PHI should be disclosed to – or withheld from – minors’ personal representatives.
The post New HIPAA Regulations in 2023-2024 appeared first on HIPAA Journal.