This post summarizes the 2018 HIPAA fines and settlements that have resulted from the enforcement activities of the Department of Health and Human Services’ Office for Civil Rights (OCR) and state attorneys general.
Another Year of Heavy OCR HIPAA Enforcement
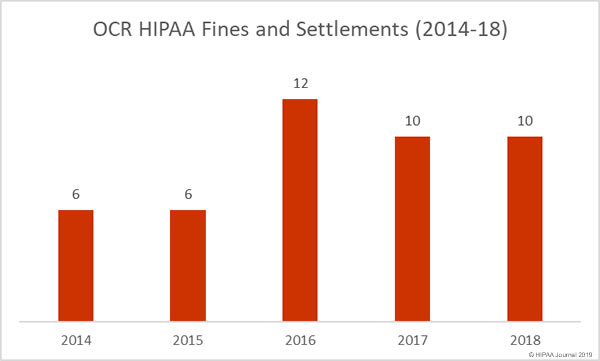
In 2016, there was a significant increase in HIPAA files and settlements compared to the previous year. In 2016, one civil monetary penalty was issued by OCR and 12 settlements were agreed with HIPAA covered entities and their business associates. In 2015, OCR only issued 6 financial penalties.
The high level of HIPAA enforcement continued in 2017 with 9 settlements agreed and one civil monetary penalty issued.
While there were two settlements agreed in February 2018 to resolve HIPAA violations, there were no further settlements or penalties until June. By the end of the summer it was looking like OCR had eased up on healthcare organizations that failed to comply with HIPAA Rules.
However, in September, a trio of settlements were agreed with hospitals that had allowed a film crew to record footage of patients without first gaining consent. Further settlements were agreed in October, November, and December and OCR finished the year on one civil monetary penalty and 9 settlements to resolve HIPAA violations.
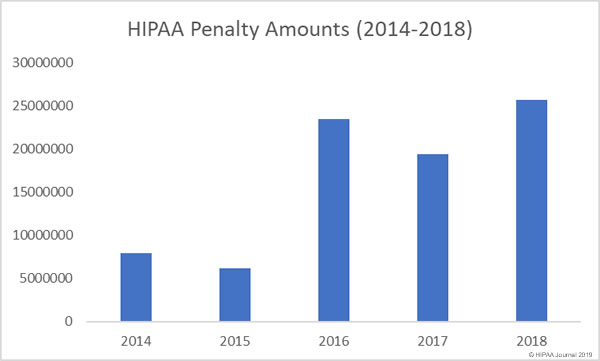
While 2018 was not a record-breaking year in terms of the number of financial penalties for HIPAA violations, it was a record-breaker in terms of the total penalty amounts paid. OCR received $25,683,400 in financial penalties in 2018. The mean financial penalty was $2,568,340.
The median HIPAA fine in 2018 was $442,000: Much lower than 2017 median of $2,250,000. It was also the lowest median fine amount of the last 5 years, although 2018 did see the largest ever HIPAA violation penalty.
In October 2018, Anthem Inc., settled its HIPAA violation case with OCR for $16,000,000. The massive fine was due to the extent of the HIPAA violations discovered by OCR and the scale of its 2015 data breach, which saw the protected health information of around 78,800,000 plan members stolen by hackers.
2018 HIPAA Fines and Settlements
| Year | Covered Entity | Amount | Settlement/CMP | Reason |
| February 2018 | Fresenius Medical Care North America | $3,500,000 | Settlement | Risk analysis failures, impermissible disclosure of ePHI; Lack of policies covering electronic devices; Lack of encryption; Insufficient security policies; Insufficient physical safeguards |
| February 2018 | Filefax, Inc. | $100,000 | Settlement | Impermissible disclosure of PHI |
| June 2018 | University of Texas MD Anderson Cancer Center | $4,348,000 | Civil Monetary Penalty | Impermissible disclosure of ePHI; No Encryption |
| September 18 | Massachusetts General Hospital | $515,000 | Settlement | Filming patients without consent |
| September 18 | Brigham and Women’s Hospital | $384,000 | Settlement | Filming patients without consent |
| September 18 | Boston Medical Center | $100,000 | Settlement | Filming patients without consent |
| October 2018 | Anthem Inc | $16,000,000 | Settlement | Risk Analysis failures; Insufficient reviews of system activity; Failure related to response to a detected breach; Insufficient technical controls to prevent unauthorized ePHI access |
| November 2018 | Allergy Associates of Hartford | $125,000 | Settlement | PHI disclosure to reporter; No sanctions against employee |
| December 2018 | Advanced Care Hospitalists | $500,000 | Settlement | Impermissible PHI Disclosure; No BAA; Insufficient security measures; No HIPAA compliance efforts prior to April 1, 2014 |
| December 2018 | Pagosa Springs Medical Center | $111,400 | Settlement | Failure to terminate employee access; No BAA |
State Attorneys General HIPAA Enforcement Activities
It is difficult to obtain meaningful statistics on HIPAA fines and settlements by state attorneys general. While state attorneys general can issue fines for violations of HIPAA Rules, in many cases, financial penalties instead issued for violations of state laws. That said, 2018 did see a major increase in HIPAA enforcement activity by state attorneys general.
There were 12 HIPAA-related financial penalties issued in 2018 by state attorneys general. The New Jersey attorney general was the most active HIPAA enforcer behind OCR with 4 HIPAA fines, followed by New York with 3, Massachusetts with 2, and 1 financial penalty issued by each of Connecticut, District of Columbia, and Washington.
The largest attorney general HIPAA fine of 2018 – Aetna’s $1,150,000 penalty – was issued by New York. Aetna was also fined a total of $640,171 in a multi-state action by Connecticut, New Jersey, Washington, and the District of Columbia. Washington has yet to agree to a settlement amount with Aetna.
EmblemHealth was fined a total of $675,000 for a 2016 data breach: $575,000 by New York and $100,000 by New Jersey.
| State | Covered Entity | Amount | State Residents Affected |
| Massachusetts | McLean Hospital | $75,000 | 1,500 |
| New Jersey | EmblemHealth | $100,000 | 6,443 |
| New Jersey | Best Transcription Medical | $200,000 | 1,650 |
| Washington | Aetna | TBA* | 13,160 (multi-state total) |
| Connecticut | Aetna | $99,959 | 13,160 (multi-state total) |
| New Jersey | Aetna | $365,211.59 | 13,160 (multi-state total) |
| District of Columbia | Aetna | $175,000 | 13,160 (multi-state total) |
| Massachusetts | UMass Memorial Medical Group / UMass Memorial Medical Center | $230,000 | 15,000 |
| New York | Arc of Erie County | $200,000 | 3,751 |
| New Jersey | Virtua Medical Group | $417,816 | 1,654 |
| New York | EmblemHealth | $575,000 | 81,122 |
| New York | Aetna | $1,150,000 | 13,160 (multi-state total) |
*Washington yet to determine settlement amount
The post Summary of 2018 HIPAA Fines and Settlements appeared first on HIPAA Journal.