For the second consecutive month there has been an increase in both the number of reported healthcare data breaches and the number of records exposed, stolen, or impermissibly disclosed.
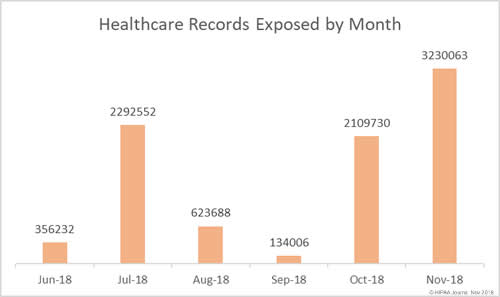
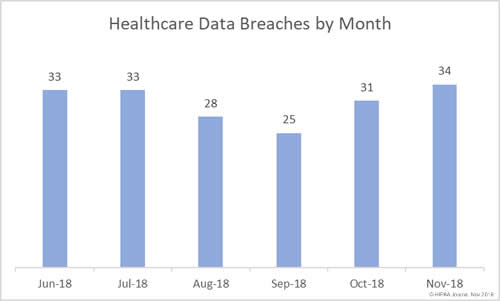
November was the worst month of the year to date for healthcare data breaches in terms of the number of exposed healthcare records. 3,230,063 records were exposed, stolen, or impermissibly disclosed in the breaches reported in November.
To put that figure into perspective, that’s more records than were exposed in all 180 data breaches reported to the HHS’ Office for Civil Rights (OCR) in the first half of 2018.
There were 34 healthcare data breaches reported to OCR in November, making it the second worst month of the year to date for breaches, behind June when 41 breaches were reported.
Largest Healthcare Data Breaches in November 2018
The largest healthcare data breach of 2018 was reported in November by Accudoc Solutions, a business associate of Atrium Health that provides healthcare billing services. That single breach resulted in the exposure of more than 2.65 million healthcare records.
AccuDoc Solutions discovered hackers had gained access to some of its databases for a week in September 2018. According to AccuDoc, the information in the databases could only be viewed, not downloaded.
| Rank | Name of Covered Entity | Covered Entity Type | Individuals Affected | Type of Breach |
| 1 | AccuDoc Solutions, Inc. | Business Associate | 2652537 | Hacking/IT Incident |
| 2 | HealthEquity, Inc. | Business Associate | 165800 | Hacking/IT Incident |
| 3 | New York Oncology Hematology, P.C. | Healthcare Provider | 128400 | Hacking/IT Incident |
| 4 | Baylor Scott & White Medical Center – Frisco | Healthcare Provider | 47984 | Hacking/IT Incident |
| 5 | Cancer Treatment Centers of America (CTCA) at Western Regional Medical Center | Healthcare Provider | 41948 | Hacking/IT Incident |
| 6 | Oprex Surgery (Baytown), L.P. d/b/a Altus Baytown Hospital | Healthcare Provider | 40000 | Hacking/IT Incident |
| 7 | Center for Vitreo-Retinal Diseases | Healthcare Provider | 20371 | Unauthorized Access/Disclosure |
| 8 | Veterans Health Administration | Healthcare Provider | 19254 | Unauthorized Access/Disclosure |
| 9 | Steward Medical Group | Healthcare Provider | 16276 | Hacking/IT Incident |
| 10 | Mind and Motion, LLC | Healthcare Provider | 16000 | Hacking/IT Incident |
Main Causes of November 2018 Healthcare Data Breaches
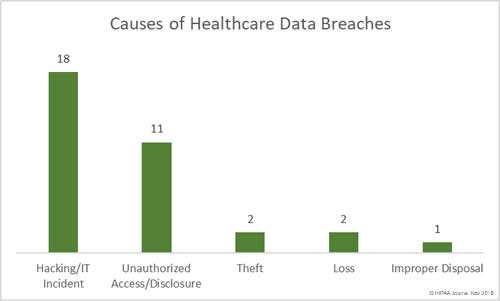
As was the case in October, hacking/IT incidents accounted for the highest number of data breaches and the most exposed/stolen healthcare records. There were 18 hacking/IT incidents reported in November. Those breaches impacted 3,138,657 individuals.
There were 11 breaches classified as unauthorized access/disclosure incidents which impacted 65,143 individuals, and 4 loss/theft incidents that resulted in the exposure of 22,333 healthcare records. One improper disposal incident exposed 3,930 healthcare records.
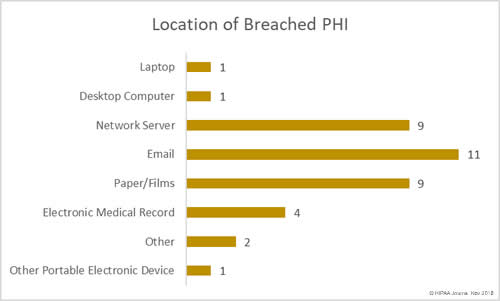
Location of Breached Protected Health Information
Email breaches continue to be a major problem in healthcare. These breaches include phishing attacks, unauthorized accessing of email accounts, and misdirected emails. There were 11 email-related breaches of PHI in November. Up until December 19, 2018, 111 email-related healthcare data breaches have been reported to OCR. Those breaches involved more than 3.4 million healthcare records.
Technical solutions can be implemented to reduce the number of email related breaches. Spam filters will prevent the majority of phishing emails from reaching inboxes, but no technical solution will be 100% effective so employees need to be trained how to recognize phishing attacks and other email threats.
All individuals in an organization from the CEO down should receive regular security awareness training with a particular emphasis on phishing. In addition to regular training sessions, phishing simulation exercises should be conducted. Through phishing simulations, healthcare organizations can assess their security awareness training programs and find out which employees require further training.
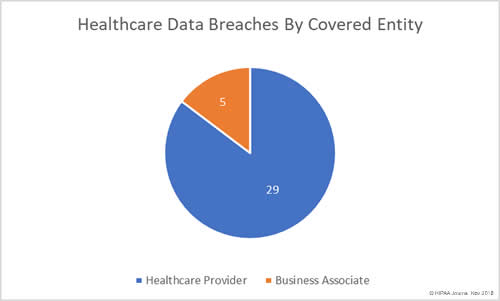
Data Breaches by Covered-Entity Type
Healthcare providers were the covered entities worst affected by healthcare data breaches in November 2018 with 29 reported incidents.
Business associates of HIPAA-covered entities reported 5 breaches and there were a further five breaches reported by healthcare providers that had some business associate involvement – Twice the number of breaches involving business associates (to some degree) as October.
There were no health plan data breaches reported in November.
Healthcare Data Breaches by State
Texas was the state worst affected by healthcare data breaches in November with 8 reported breaches. New York experienced three healthcare data breaches and there were two breaches reported in each of Georgia, Iowa, Illinois, Missouri, North Carolina, Utah, and Virginia.
One healthcare data breach was reported in Arizona, California, District of Columbia, Massachusetts, Maryland, Nebraska, New Jersey, Pennsylvania, and Washington.
Penalties for HIPAA Violations in November 2018
The Department of Health and Human Services’ Office for Civil Rights settled one HIPAA violation case with a healthcare provider in November.
Allergy Associates of Hartford was fined $125,000 over a physician’s impermissible disclosure of PHI to a TV reporter. The disclosure occurred after the physicians was instructed by the Allergy Associates of Hartford Privacy Officer not to respond to the reporter’s request for information about a patient, or to reply with ‘no comment’. Allergy Associates of Hartford failed to take any action against the physician over the HIPAA violation.
New Jersey also issued a financial penalty to a HIPAA-covered entity in November to resolve a HIPAA violation case. Best Transcription Medical was fined $200,000 for exposing the electronic protected health information of patients over the Internet. The breach affected 1,650 New Jersey residents.
The post November 2018 Healthcare Data Breach Report appeared first on HIPAA Journal.