Our October 2018 healthcare data breach report shows there has been a month-over-month increase in healthcare data breaches with October seeing more than one healthcare data breach reported per day.
31 healthcare data breaches were reported by HIPAA-covered entities and their business associates in October – 6 incidents more than the previous month. It should be noted that one breach at a business associate was reported to OCR as three separate breaches.
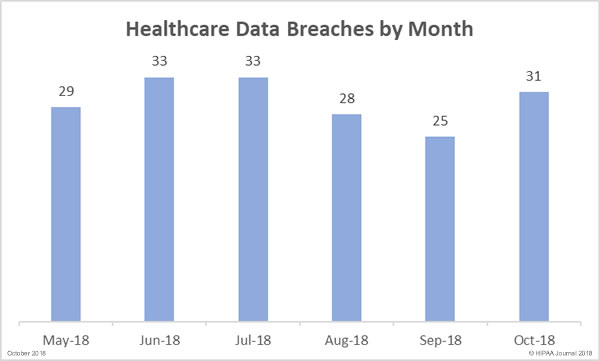
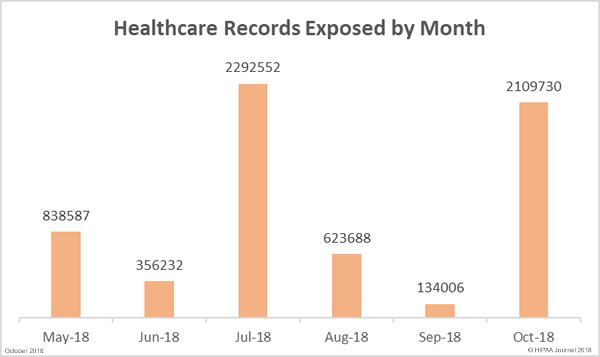
The number of breached records in September (134,006) was the lowest total for 6 months, but the downward trend did not continue in October. There was a massive increase in exposed protected health information (PHI) in October. 2,109,730 records were exposed, stolen or impermissibly disclosed – 1,474% more than the previous month. In October, the average breach size was 68,055 records and the median was 4,058 records.
Largest Healthcare Data Breaches in October 2018
There were 11 healthcare data breaches of more than 10,000 records reported in October – A 120% increases from the five 10,000+ record breaches in September. The largest healthcare data breach in October resulted in the exposure of 1.24 million records: An unauthorized access/disclosure incident at Employees Retirement System of Texas. A flaw in its ERS Online portal allowed members to view the PHI of other members.
566,217 records were exposed in a breach at Banker’s Life, a division of CNO Financial Group Inc., also an unauthorized access/disclosure incident. Employee credentials were stolen and used to gain access to company websites, resulting in the exposure and potential theft of policyholder and applicant information.
| Rank |
Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
| 1 |
Employees Retirement System of Texas |
Health Plan |
1248263 |
Unauthorized Access/Disclosure |
| 2 |
CNO Financial Group, Inc. |
Health Plan |
566217 |
Unauthorized Access/Disclosure |
| 3 |
Health First, Inc |
Healthcare Provider |
42000 |
Hacking/IT Incident |
| 4 |
Jones Eye Center, P.C. |
Healthcare Provider |
39605 |
Hacking/IT Incident |
| 5 |
Gold Coast Health Plan |
Business Associate |
37005 |
Hacking/IT Incident |
| 6 |
The May Eye Care Center |
Healthcare Provider |
30000 |
Hacking/IT Incident |
| 7 |
CJ Elmwood Partners, L.P. |
Healthcare Provider |
22416 |
Hacking/IT Incident |
| 8 |
Minnesota Department of Human Services |
Health Plan |
20800 |
Hacking/IT Incident |
| 9 |
Catawba Valley Medical Center |
Healthcare Provider |
20000 |
Hacking/IT Incident |
| 10 |
National Ambulatory Hernia Institute |
Healthcare Provider |
15974 |
Hacking/IT Incident |
Causes of October 2018 Healthcare Data Breaches
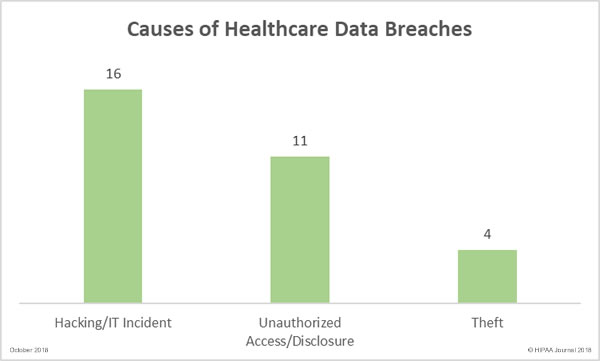
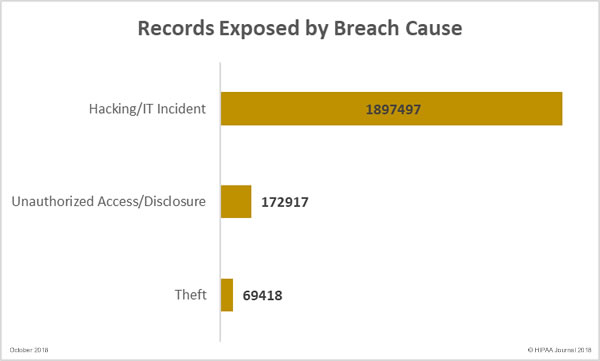
Unauthorized access/disclosure breaches resulted in the highest number of compromised records, but hacking/IT incidents were more common in October. October saw 16 hacking/IT incidents reported, 11 unauthorized access/disclosure incidents, and four theft incidents. There were no reports of lost PHI/ePHI and no improper disposal incidents.
Healthcare Records Exposed by Breach Cause
Location of Breached Protected Health Information
Phishing is arguably the biggest cyber threat faced by healthcare organizations and October saw many phishing attacks reported by healthcare providers. In October, there were 9 incidents involving PHI exposure via email. There were also 9 network server-related breaches, which included hacks, malware, and ransomware attacks.

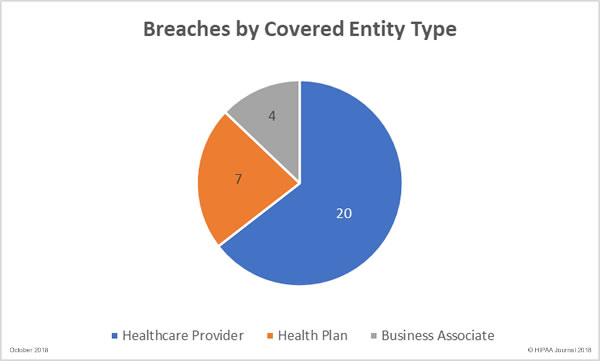
Data Breaches by Covered-Entity Type
In terms of the number of incidents, healthcare providers were the worst hit by data breaches in October with 20 reported breaches, followed by health plans/health insurers with 7. Four HIPAA business associate breaches were reported, three of which were by the same business associate – HealthFitness. One further breach had some business associate involvement.
In terms of the number of exposed records, health plans/insurers fared worse than other HIPAA-covered entities. 1,848,235 healthcare records were exposed at health plans/insurers, 221,994 healthcare records were exposed in healthcare provider breaches, and 39,501 records exposed by business associates.
Healthcare Data Breaches by State
Texas was worst affected by healthcare data breaches in October. 5 breaches were reported by covered entities/business associates based in Texas. California, Connecticut, Illinois, and Washington each had 3 breaches reported. There were two breaches reported in each of Florida, Iowa, Indiana, and Pennsylvania. Minnesota, Missouri, North Carolina, New Mexico, Oklahoma, and Oregon had one breach apiece.
Penalties for HIPAA Violations in October
After a period of quiet on the HIPAA penalty front, the Department of Health and Human Services’ Office for Civil Rights announced three settlements in September related to filming patients without consent. There were followed up in October with a massive fine for Anthem Inc.
The Anthem Inc., HIPAA violation penalty was expected, and given the scale of the breach (78.8 million records), the penalty was likely to be large. After assessing the extent of HIPAA violations, the scale of the breach, and its impact, OCR fined Anthem $16,000,000. The previous largest ever HIPAA penalty was $5,550,000 (Advocate Health Care Network, 2016)
In October, a multi-state action against the health insurer Aetna was concluded and settlements were reached to resolve the HIPAA violations. The penalties related to the impermissible disclosure of 13,160 plan members’ HIV/AIDS diagnoses via a mailing. Settlements were reached with Connecticut, New Jersey, and the District of Columbia totaling $640,170. Washington was also part of the multi-state action, but the settlement amount has not yet been decided.
The post October 2018 Healthcare Data Breach Report appeared first on HIPAA Journal.





