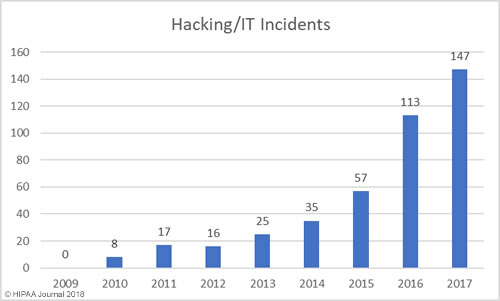
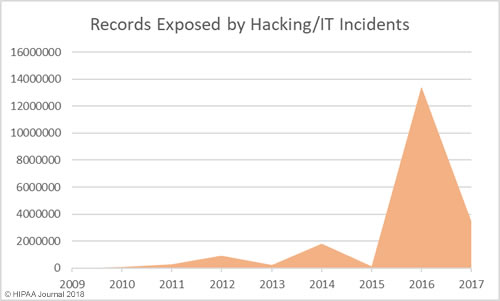
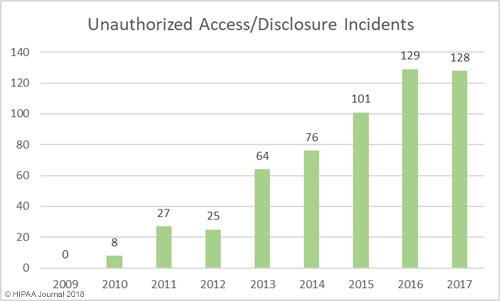
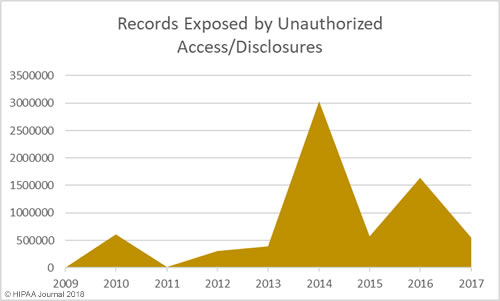
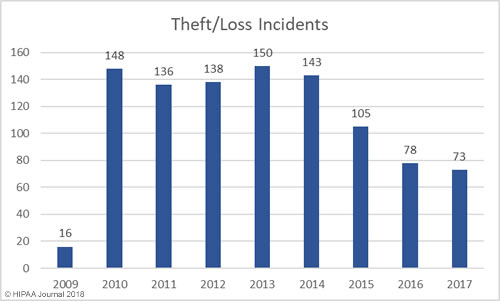
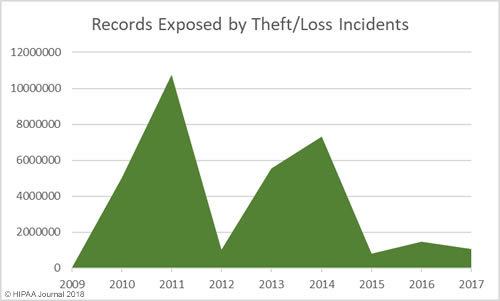
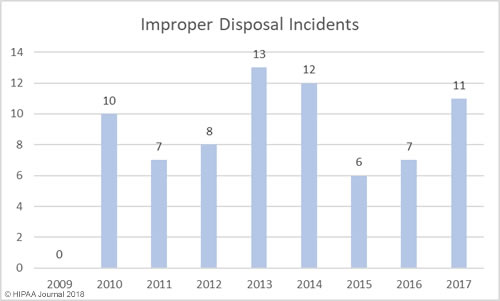
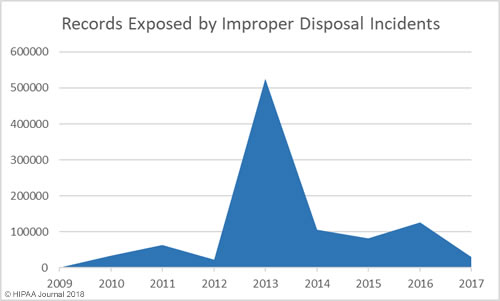
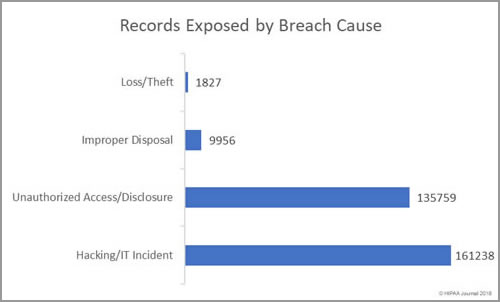
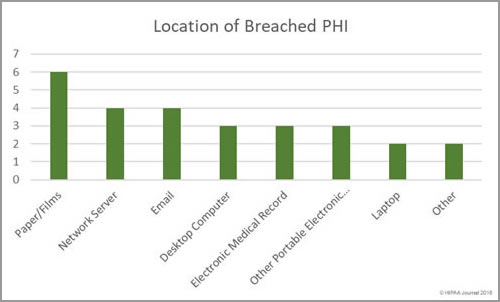
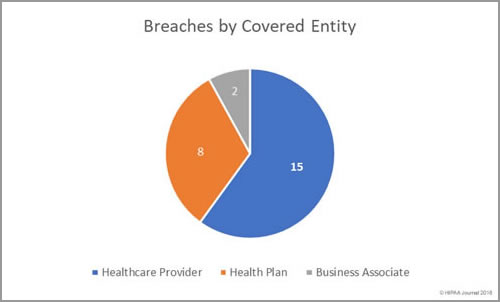
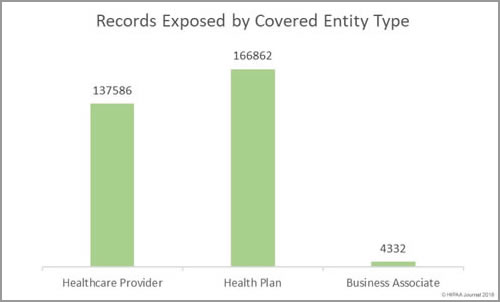
South Dakota has been slow to introduce legislation to improve protections for consumers affected by breaches of their personal information. Laws have already been introduced in 48 states that require individuals and companies that store personal information to issue notifications to breach victims when that information is compromised.
Last week, South Dakota residents were given similar protections to those in place in neighboring states. On March 21, 2018, South Dakota attorney general Marty Jackley issued a statement confirming SB 62 had been signed by Governor Daugaard and will take effect on July 1, 2018.
The bipartisan bill requires entities that experience a breach of personal information to issue notifications to affected state residents within 60 days of discovery of the breach – The same time frame as HIPAA.
Personal information is classed as the full name or first initial and last name of a state resident in combination with either a government ID number, Social Security number, driver’s license number, credit/debit card number (with an associated code that allows the card to be used), employment ID number (with authentication information), and health information (the same definition as HIPAA 45 CFR 160.103). A notification must also be issued to the state attorney general if the breach impacts more than 250 state residents, also within 60 days of discovery of the breach.
In contrast to many states, there is a risk of harm exception in the South Dakota data breach notification law. If a breached entity “reasonably determines that the breach will not likely result in harm to the affected person,” notifications do not need to be issued.
Delaying breach notifications could attract a fine up to $10,000 per day plus state attorneys’ fees, with a fine of $10,000 possible for each violation.
Now that the South Dakota data breach notification law has been enacted, Alabama is the only state that has not yet introduced state-level data breach notification regulations. That is likely to change soon as data breach legislation is currently under consideration by the House of Representatives following the unanimous passing of the Alabama Data Breach Notification Act of 2018 by the Alabama Senate earlier this month.
State Attorneys General Oppose Federal Data Breach Notification Regulations
Just as the patchwork of data breach notification regulations approaches completion, federal regulations are being considered that could see those state level laws rendered obsolete. A discussion draft of the Data Acquisition and Technology Accountability and Security Act was issued in February, which if signed into law, would apply to “any person, partnership, corporation, trust, estate, cooperative, association, or other entity that accesses, maintains, or stores personal, or handles personal information.”
The Data Acquisition and Technology Accountability and Security Act would require security safeguards to be implemented to protect personal information stored by any entity included in the above definition. Data breach notifications would need to be issued if, following a risk assessment, the breached entity determines there is a “reasonable risk that the breach of data security has resulted in or will result in identity theft, fraud, or economic loss to the consumers to whom the personal information involved in the incident relates.” The notifications would need to be issued without unreasonable delay.
The discussion draft of the bill has attracted criticism from state attorneys general who have already enacted their own laws to protect residents in their respective states. A bipartisan group of 32 (20 Democrats / 12 Republicans) state attorneys general, led by Illinois attorney general Lisa Madigan, sent a joint letter to the House Financial Services Committee on March 19 opposing the Data Acquisition and Technology Accountability and Security Act.
The proposed Data Acquisition and Technology Accountability and Security Act preempts state regulations and appears to place credit reporting agencies such as Equifax outside the scope of state regulation. While the above definition of entities appears to be comprehensive, a notable exception is any entity covered by the Gramm-Leach-Bliley Act – Namely financial institutions and credit reporting agencies.
Further, the proposed bill would see protections for consumers lessened in most states, since the breach reporting requirements in the Data Acquisition and Technology Accountability and Security Act are far less stringent. Not only does the DATAS Act allow a breached entity to determine the level of risk to consumers – and whether data breach notifications are required – breached entities would have much longer to issue notifications. Those notifications could even be issued after consumers have experienced identity theft and fraud due to a breach of their personal information.
The post South Dakota Enacts Data Breach Notification Law as Congress Considers Federal Breach Notice Bill appeared first on HIPAA Journal.