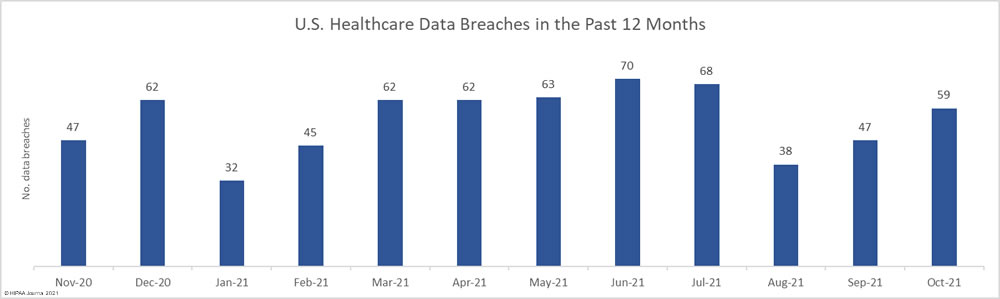
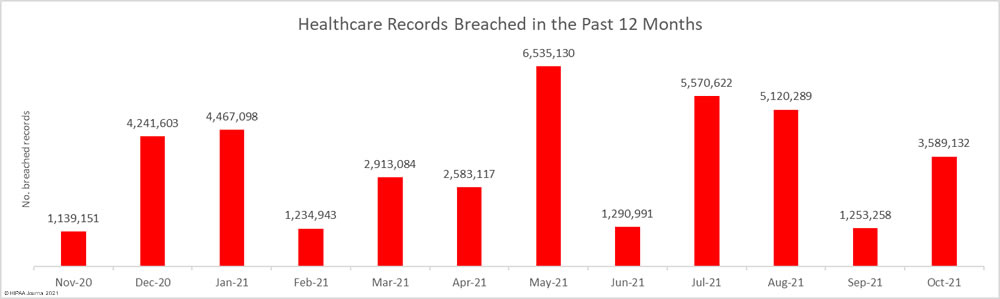
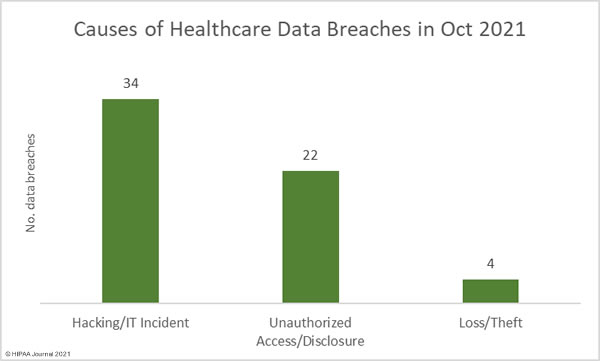
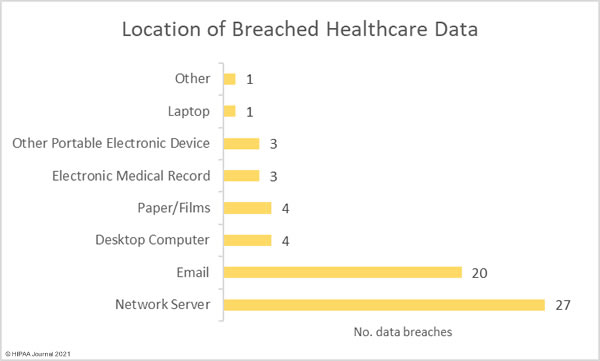
The HHS’ Health Sector Cybersecurity Coordination Center (HC3) has issued a threat brief warning the healthcare and public health sector about an increase in financially motivated zero-day attacks, outlining mitigation tactics that should be adopted to reduce risk to a low and acceptable level.
A zero-day attack leverages a vulnerability for which a patch has yet to be released. The vulnerabilities are referred to as zero-day, as the developer has had no time to release a patch to correct the flaw.
Zero-day attacks are those where a threat actor has exploited a zero-day vulnerability using a weaponized exploit for the flaw. Zero-day vulnerabilities are exploited in attacks on all industry sectors and are not only a problem for the healthcare industry. For instance, in 2010, exploits were developed for four zero-day vulnerabilities in the “Stuxnet” attack on the Iranian nuclear program, which caused Iranian centrifuges to self-destruct to disrupt Iran’s nuclear program.
More recently in 2017, a zero-day vulnerability was exploited to deliver the Dridex banking Trojan. While it would normally be necessary for an individual to take additional actions after opening a malicious email attachment for malware to be downloaded, by including an exploit for a zero-day vulnerability the threat actors were able to install the Dridex banking Trojan if an individual simply opened an infected email attachment. A zero-day vulnerability was also exploited this year in the 2021 SonicWall ransomware attacks. The vulnerability was identified by the UNC2447 threat group and was exploited to deliver FiveHands ransomware.
The very nature of zero-day vulnerabilities means it is not possible to eliminate risk entirely, as software developers need to develop patches to fix the vulnerabilities, but strategies can be adopted to reduce the potential for zero-day vulnerabilities to be exploited.
The number of detected exploits for zero-day vulnerabilities more than doubled between 2019 and 2021. This is, in part, due to the high value of exploits for zero-day flaws. The price paid for working exploits rose by more than 1,150% between 2018 and 2021. While the market for zero-day exploits was limited to a handful of groups with deep pockets, there are now many threat actors with considerable resources that are willing to pay as they know they can make their money back many times over by using the exploits in their attacks. Now, an exploit for a zero-day vulnerability could be worth more than $1 million.
Zero-day attacks specifically conducted against the healthcare sector are a very real possibility. In August this year, a zero-day vulnerability dubbed PwnedPiper was identified in the pneumatic tube systems used in hospitals to transport biological samples and medications. The vulnerability was identified in the control panel, which would allow unsigned firmware updates to be applied. An attacker could exploit the flaw and take control of the system and deploy ransomware.
In August 2020, four zero-day vulnerabilities were identified that exposed OpenClinic patients’ test results. Unauthenticated attackers could successfully request files containing sensitive documents from the medical test directory, including medical test results.
The best defense against zero-day vulnerabilities is to patch promptly, but patching is often slow, especially in healthcare. In 2019, a survey conducted by the Ponemon Institute revealed the average time to apply, test, and deploy a patch for a zero-day vulnerability was 97 days after the patch was released.
The advice of HC3 is to “patch early, patch often, patch completely.” HC3 provides up-to-date information on actively exploited zero-days and the available patches to fix zero-day flaws. HC3 also suggests implementing a web-application firewall to review incoming traffic and filter out malicious input, as this can prevent threat actors from gaining access to vulnerable systems. It is also recommended to use runtime application self-protection (RASP) agents, which sit inside applications’ runtime and can detect anomalous behavior. Segmenting networks is also strongly recommended.
The TLP: WHITE Zero-Day Threat Brief is available for download on this link.
The post HHS Warns Healthcare Sector About Risk of Zero-day Attacks appeared first on HIPAA Journal.