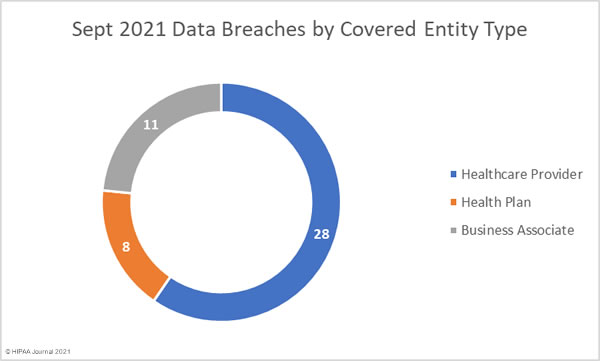
The advanced persistent threat (APT) actor Nobelium (aka APT29; Cozy Bear) that was behind the 2020 SolarWinds supply chain attack is targeting cloud service providers (CSPs), managed service providers (MSPs), and other IT service providers, according to a recent alert from Microsoft.
Rather than conducting attacks on many companies and organizations, Nobelium is favoring a compromise-one-to-compromise-many approach. This is possible because service providers are often given administrative access to customers’ networks to allow them to provide IT services. Nobelium is attempting to leverage that privileged access to conduct attacks on downstream businesses and has been conducting attacks since at least May 2021.
Nobelium uses several techniques to compromise the networks of service providers, including phishing and spear phishing attacks, token theft, malware, supply chain attacks, API abuse, and password spraying attacks on accounts using commonly used passwords and passwords that have previously been stolen in data breaches.
Once access to service providers’ networks has been gained, Nobelium moves laterally in cloud environments then leverages the trusted access to conduct attacks on downstream businesses using trusted channels such as externally facing VPNs or the unique software solutions used by service providers to access customers’ networks.
Some of the attacks conducted by Nobelium have been highly sophisticated and involved chaining together artifacts and access from multiple service providers in order to reach their end target, as indicated in the diagram below.
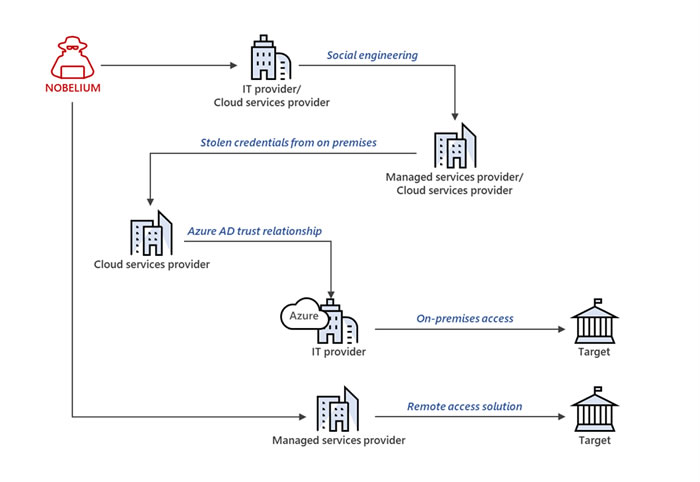
Example of a Nobelium attack leveraging multiple service providers. Source: Microsoft Threat Intelligence Center
Microsoft Threat Intelligence Center (MSTIC) has made several recommendations for service providers and downstream businesses to help with mitigation and remediation.
CPSs and MSPs that rely on elevated privileges to provide services to their customers have been advised to verify and monitor compliance with Microsoft Partner Center security requirements, which include enabling multifactor authentication and enforcing conditional access policies, adopting the Secure Application Model Framework, checking activity logs and monitoring user activities, and removing delegated administrative privileges that are no longer in use.
All downstream businesses that rely on service providers that have administrative access have been advised to review, audit, and minimize access privileges and delegated permissions, including hardening and monitoring all tenant administrator accounts and reviewing service provider permissions access from B2B and local accounts. They should also verify MFA is enabled and conditional access policies are being enforced and regularly review audit logs and configurations.
Microsoft has published detailed information on the tactics, techniques, and procedures (TTP) of Nobelium in its alerts to help IT security teams to block, detect, investigate, and mitigate attacks.
The post Microsoft Warns of Ongoing Attacks by SolarWinds Hackers on Service Providers and Downstream Businesses appeared first on HIPAA Journal.