May was the worst month of 2021 to date for healthcare data breaches. There were 63 breaches of 500 or more records reported to the Department of Health and Human Services’ Office for Civil Rights in May. For the past three months, breaches have been reported at a rate of more than 2 per day. The average number of healthcare data breaches per month has now risen to 54.67.
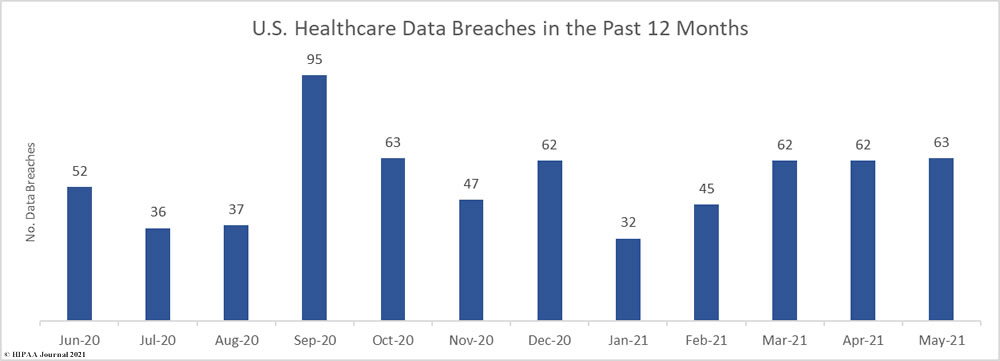
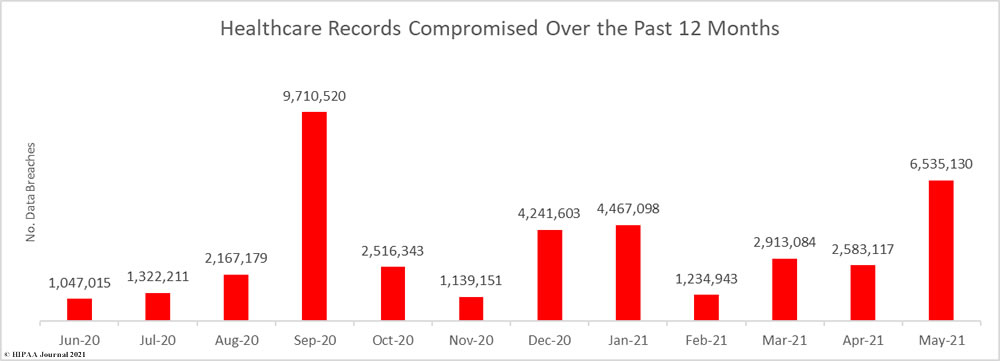
May was also the worst month of the year in terms of the severity of breaches. 6,535,130 healthcare records were breached across those 63 incidents. The average number of breached healthcare records each month has now risen to 3,323,116. 17,733,372 healthcare records have now been exposed or impermissibly disclosed so far in 2021 and almost 40 million records (39.87M) have been breached in the past 12 months.
Largest Healthcare Data Breaches Reported in April 2021
As was the case in April, there were 19 healthcare data breaches involving 10,000 or more records and 7 of those breaches involved 100,000 or more records. All but one of those breaches was a hacking incident or involved It systems being compromised by other means.
The largest healthcare data breach of the month by some distance affected 20/20 Eye Care Network, a vision and hearing benefits administrator. The records of more than 3.25 million individuals were stored in an AWS S3 bucket that was accessed by an unauthorized individual. Data was downloaded by the attacker before being deleted. Another benefits administrator, SEIU 775 Benefits Group, also suffered a breach in which sensitive data was deleted. That breach involved the PHI of 140,000 individuals.
Over the past two months, several healthcare providers have announced they were affected by a ransomware attack on the third-party administration service provider CaptureRx. At least 26 healthcare providers are known to have had PHI exposed in that breach. This month, CaptureRx issued its own notification to the HSS which confirms the breach affected 1,656,569 individuals. This month, several healthcare organizations have reported they have been affected by a ransomware attack on another business associate, Netgain Technologies. The table below shows the extent to which ransomware has been used in attacks on the healthcare industry.
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Breach Cause |
Business Associate Involvement |
| 20/20 Eye Care Network, Inc |
Business Associate |
3,253,822 |
Hacking/IT Incident |
Unsecured AWS S3 Bucket |
Yes |
| NEC Networks, LLC d/b/a CaptureRx |
Business Associate |
1,656,569 |
Hacking/IT Incident |
Ransomware attack |
Yes |
| Orthopedic Associates of Dutchess County |
Healthcare Provider |
331,376 |
Hacking/IT Incident |
Ransomware attack |
No |
| Rehoboth McKinley Christian Health Care Services |
Healthcare Provider |
207,195 |
Hacking/IT Incident |
Ransomware attack |
No |
| Five Rivers Health Centers |
Healthcare Provider |
155,748 |
Hacking/IT Incident |
Phishing attack |
No |
| SEIU 775 Benefits Group |
Business Associate |
140,000 |
Hacking/IT Incident |
Unspecified hacking incident |
Yes |
| San Diego Family Care |
Healthcare Provider |
125,500 |
Hacking/IT Incident |
Ransomware attack (Netgain Technologies) |
Yes |
| Hoboken Radiology LLC |
Healthcare Provider |
80,000 |
Hacking/IT Incident |
Hacked medical imaging server |
No |
| CareSouth Carolina, Inc. |
Healthcare Provider |
76,035 |
Hacking/IT Incident |
Ransomware attack (Netgain Technologies) |
Yes |
| Arizona Asthma and Allergy Institute |
Healthcare Provider |
70,372 |
Hacking/IT Incident |
Ransomware attack |
No |
| New England Dermatology, P.C. |
Healthcare Provider |
58,106 |
Improper Disposal |
Improper disposal of specimen bottles |
No |
| Sturdy Memorial Hospital |
Healthcare Provider |
57,379 |
Hacking/IT Incident |
Ransomware attack |
No |
| LogicGate |
Business Associate |
47,035 |
Hacking/IT Incident |
Unsecured AWS S3 Bucket |
Yes |
| Lafourche Medical Group |
Healthcare Provider |
34,862 |
Hacking/IT Incident |
Phishing attack |
No |
| Internal Medicine Associates of Jasper, PC, dba Prestige Medical Group |
Healthcare Provider |
34,203 |
Hacking/IT Incident |
Ransomware attack |
No |
| SAC Health Systems |
Healthcare Provider |
28,128 |
Hacking/IT Incident |
Ransomware attack (Netgain Technologies) |
Yes |
| Monadnock Community Hospital |
Healthcare Provider |
14,340 |
Hacking/IT Incident |
Unspecified hacking incident |
Yes |
| Community Access Unlimited |
Business Associate |
13,813 |
Hacking/IT Incident |
Ransomware attack (Netgain Technologies) |
Yes |
| Westwood Obstetrics and Gynecology |
Healthcare Provider |
12,931 |
Hacking/IT Incident |
Unspecified hacking incident |
Yes |
Causes of May 2021 Healthcare Data Breaches
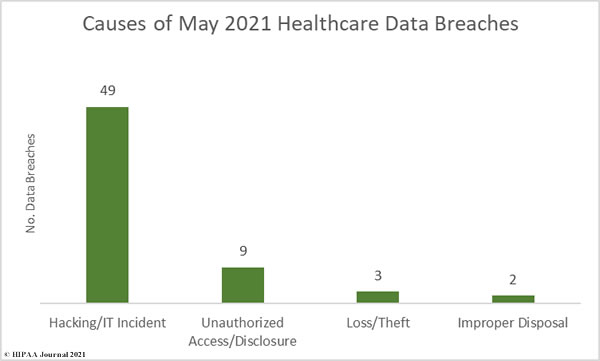
Hacking/IT incidents dominated the breach reports in May. Out of the 63 reported breaches, 47 (74.60%) were hacking/IT incidents. These incidents resulted in the exposure or theft of 6,432,367 healthcare records – 98.43% of all records breached in the month. The average breach size was 131,273 records and the median breach size was 4,250 records.
There were 9 reported unauthorized access/disclosure incidents involving the records of 17,834 individuals. The average breach size was 1,982 records and the median breach size was 1,562 records. There were 3 loss/theft incidents reported involving the 20,325 records and two incidents involving the improper disposal of protected health information affecting 64,604 individuals.
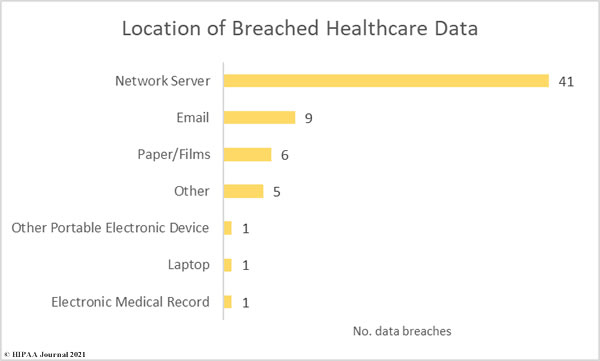
While phishing incidents have plagued the healthcare industry over the past few years, it is now network server incidents that dominate the breach reports. 41 of the month’s breaches involved compromised network servers, compared to just 9 incidents involving email.
May 2021 Healthcare Data Breaches by Covered Entity Type
47 healthcare providers reported data breaches in May 2021, although only 20 of those incidents were breaches directly involving the healthcare provider. 27 of those breaches were reported by the healthcare provider but occurred at a business associate.
7 data breaches were reported to the HHS’ Office for Civil Rights by business associates of HIPAA-covered entities, although in total, the business associate was present in 31 of the month’s breaches.
8 breaches affected health plans, 4 of which had some business associate involvement, and one breach was reported by a healthcare clearinghouse.

States Affected by Healthcare Data Breaches
Healthcare data breaches were reported by HIPAA-covered entities and business associates based in 32 U.S. states.
| State |
No. Reported Data Breaches |
| Texas |
6 |
| New York & Ohio |
5 |
| California, Illinois, West Virginia |
4 |
| Mississippi & Missouri |
3 |
| Florida, Maryland, Massachusetts, New Jersey, & Oklahoma |
2 |
| Arizona, Arkansas, Connecticut, Delaware, Georgia, Indiana, Louisiana, Maine, Minnesota, North Carolina, Nevada, New Hampshire, New Mexico, Pennsylvania, Rhode Island, South Carolina, Tennessee, Washington, and Wisconsin |
1 |
HIPAA Enforcement in May 2021
There was one HIPAA enforcement action announced by the HHS’ Office for Civil Rights in May, bringing the total up to 8 for 2021. Most of the settlements announced so far in 2021 have resolved violations of the HIPAA Right of access; however, May’s settlement was for multiple violations of the HIPAA Security Rule.
Most financial penalties stem from an OCR investigation into a data breach or complaint from a patient. May’s financial penalty was atypical, as it was the result of a compliance investigation. OCR had investigated a data breach reported by the Department of Veteran Affairs involving its business associate Authentidate Holding Corporation (AHC).
That investigation was resolved without financial penalty; however, during the investigation OCR learned that AHC had entered into a reverse merger with Peachstate Health Management, LLC, a CLIA-certified laboratory that provides clinical and genetic testing services through its publicly traded parent company, AEON Global Health Corporation (AGHC).
OCR decided to conduct a compliance review of Peachstate’s clinical laboratories to assess Privacy and Security Rule compliance and discovered multiple violations of the HIPAA Security Rule. OCR discovered potential violations related to risk assessments, risk management, audit controls, and a lack of documentation of HIPAA Security Rule policies and procedures. The case was settled for $25,000.
The post May 2021 Healthcare Data Breach Report appeared first on HIPAA Journal.




