September has been a bad month for data breaches. 95 data breaches of 500 or more records were reported by HIPAA-covered entities and business associates in September – A 156.75% increase compared to August 2020.
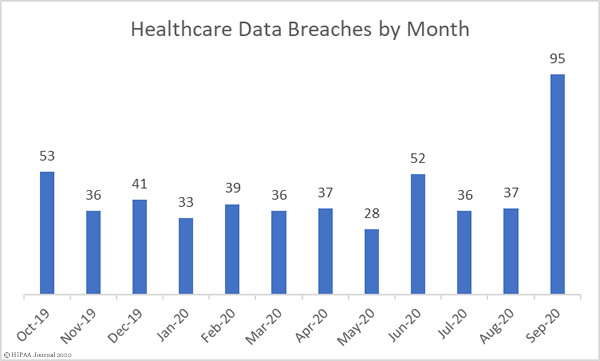
Not only did September see a massive increase in reported data breaches, the number of records exposed also increased significantly. 9,710,520 healthcare records were exposed in those breaches – 348.07% more than August – with 18 entities suffering breaches of more than 100,000 records. The mean breach size was 102,216 records and the median breach size was 16,038 records.
Causes of September 2020 Healthcare Data Breaches
The massive increase in reported data breaches is due to the ransomware attack on the cloud software company Blackbaud. In May 2020, Blackbaud suffered a ransomware attack in which hackers gained access to servers housing some of its customers’ fundraising databases. Those customers included many higher education and third sector organizations, and a significant number of healthcare providers.
Blackbaud was able to contain the breach; however, prior to the deployment of the ransomware, the attackers exfiltrated some customer data. The breach was initially thought to only include limited data about donors and prospective donors, but further investigations revealed Social Security numbers and financial information were also exfiltrated by the hackers.
Blackbaud negotiated a ransom payment and paid to prevent the publication or sale of the stolen data. Blackbaud has reported it has received assurances that all stolen data were deleted. Blackbaud has engaged a company to monitor dark web sites but no data appears to have been offered for sale.
Blackbaud announced the ransomware attack in July 2020 and notified all affected customers. HIPAA-covered entities affected by the breach started to report the data breach in August, with most reporting in September.
It is currently unclear exactly how many U.S. healthcare organizations were affected by the breach and the final total may never be known. Databreaches.net has been tracking the Blackbaud breach reports and, at last count, at least 80 healthcare organizations are known to have been affected. The records of more than 10 million patients are thought to have been compromised as a result of the ransomware attack.
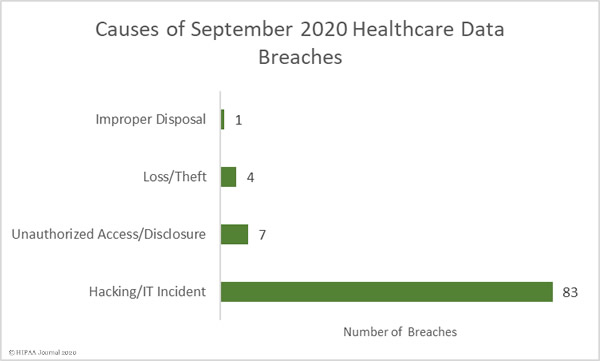
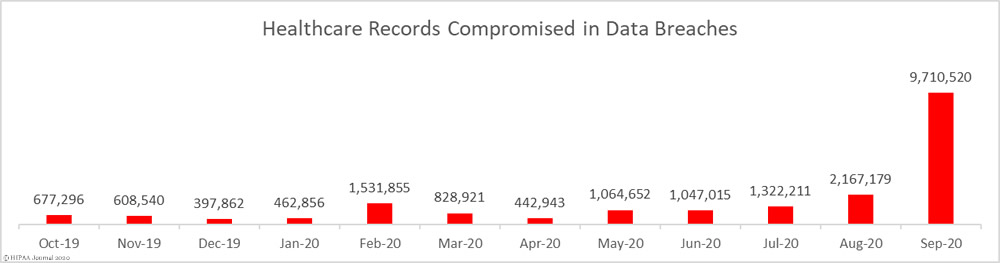
Unsurprisingly, given the numbers of healthcare providers affected by the Blackbaud breach, hacking/IT incidents dominated the breach reports. 83 breaches were attributed to hacking/IT incidents and 9,662,820 records were exposed in those breaches – 99.50% of all records reported as breached in September. The mean breach size was 116,420 records and the median breach size was 27,410 records.
There were 7 unauthorized access/disclosure incidents reported in September involving a total of 34,995 records. The mean breach size was 4,942 records and the median breach size was 1,818 records. There were 4 loss/theft incidents reported involving 12,029 records, with a mean breach size of 3,007 records and a median size of 2,978 records. There was 1 improper disposal incident reported involving 1,076 records.
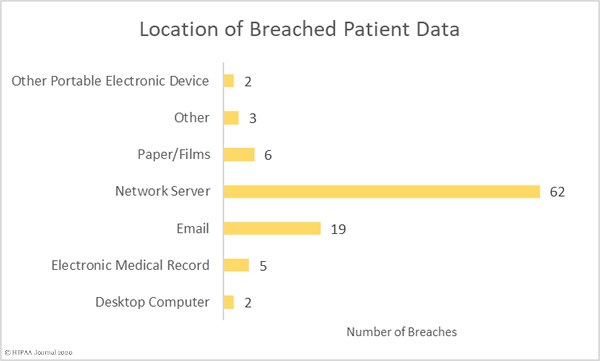
Most of the compromised records were stored on network servers, although there were a sizable number of breaches involving PHI stored in email accounts.
Largest Healthcare Data Breaches Reported in September 2020
| Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
Breach Cause |
| Trinity Health |
Business Associate |
3,320,726 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| Inova Health System |
Healthcare Provider |
1,045,270 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| NorthShore University HealthSystem |
Healthcare Provider |
348,746 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| SCL Health – Colorado (affiliated covered entity) |
Healthcare Provider |
343,493 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| Nuvance Health (on behalf of its covered entities) |
Healthcare Provider |
314,829 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| The Baton Rouge Clinic, A Medical Corporation |
Healthcare Provider |
308,169 |
Hacking/IT Incident |
Ransomware Attack |
| Virginia Mason Medical Center |
Healthcare Provider |
244,761 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| University of Tennessee Medical Center |
Healthcare Provider |
234,954 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| Legacy Community Health Services, Inc. |
Healthcare Provider |
228,009 |
Hacking/IT Incident |
Phishing Attack |
| Allina Health |
Healthcare Provider |
199,389 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| University of Missouri Health Care |
Healthcare Provider |
189,736 |
Hacking/IT Incident |
Phishing Attack |
| The Christ Hospital Health Network |
Healthcare Provider |
183,265 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| Stony Brook University Hospital |
Healthcare Provider |
175,803 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| Atrium Health |
Healthcare Provider |
165,000 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| University of Kentucky HealthCare |
Healthcare Provider |
163,774 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| Children’s Minnesota |
Healthcare Provider |
160,268 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| Roswell Park Comprehensive Cancer Center |
Healthcare Provider |
141,669 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| Piedmont Healthcare, Inc. |
Healthcare Provider |
111,588 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| SCL Health – Montana (affiliated covered entity) |
Healthcare Provider |
93,642 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
| Roper St. Francis Healthcare |
Healthcare Provider |
92,963 |
Hacking/IT Incident |
Blackbaud Ransomware Attack |
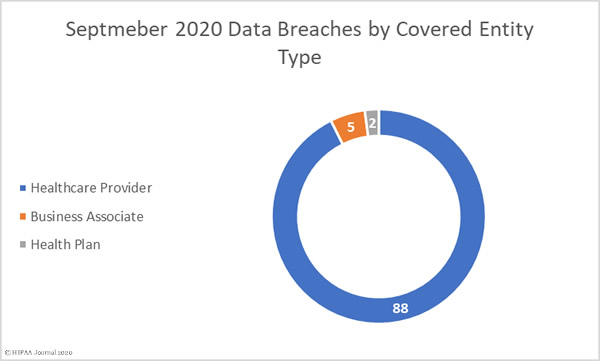
September 2020 Data Breaches by Covered Entity Type
88 healthcare providers reported data breaches of 500 or more records in September and 2 breaches were reported by health plans. 5 breaches were reported by business associates of HIPAA-covered entities, but a further 53 breaches involved a business associate, with the breach reported by the covered entity. Virtually all of those 53 breaches were due to the ransomware attack on Blackbaud.
September 2020 Data Breaches by State
Covered entities and business associates in 30 states and the district of Columbia reported data breaches of 500 or more records in September.
New York was the worst affected state with 10 breaches, 6 breaches were reported in each of California, Minnesota, and Pennsylvania, 5 in each of Colorado, South Carolina, and Texas, 4 in Florida, Georgia, Massachusetts, Ohio, and Virginia, 3 in each of Iowa, Kentucky, Louisiana, and Michigan, and 2 in each of Connecticut, Maryland, North Carolina, Tennessee, and Wisconsin.
One breach was reported in each of Alabama, Delaware, Illinois, Indiana, Missouri, New Hampshire, New Jersey, Oklahoma, Washington, and the District of Columbia.
HIPAA Enforcement Activity in September 2020
Prior to September, the HHS’ Office for Civil Rights had only imposed three financial penalties on covered entities and business associates to resolve HIPAA violations, but there was a flurry of announcements about HIPAA settlements in September with 8 financial penalties announced.
The largest settlement was agreed with Premera Blue Cross to resolve HIPAA violations discovered during the investigation of its 2014 data breach that affected 10.4 million of its members. OCR found compliance issues related to risk analyses, risk management, and hardware and software controls. Premera agreed to pay a financial penalty of $6,850,000 to resolve the case. This was the second largest HIPAA fine ever imposed on a covered entity.
CHSPSC LLC, a business associate of Community Health Systems, agreed to pay OCR $2,300,000 to resolve its HIPAA violation case which stemmed from a breach of the PHI of 6 million individuals in 2014. OCR found compliance issues related to risk analyses, information system activity reviews, security incident procedures, and access controls.
Athens Orthopedic Clinic PA agreed to pay a $1,500,000 penalty to resolve its case with OCR which stemmed from the hacking of its systems by TheDarkOverlord hacking group. The PHI of 208,557 patients was compromised in the attack. OCR’s investigation uncovered compliance issues related to risk analyses, risk management, audit controls, HIPAA policies and procedures, business associate agreements, and HIPAA Privacy Rule training for the workforce.
Five of the September settlements resulted from OCR’s HIPAA Right of Access enforcement initiative and were due to the failure to provide patients with timely access to their medical records.
| Entity |
Settlement |
| Beth Israel Lahey Health Behavioral Services |
$70,000 |
| Housing Works, Inc. |
$38,000 |
| All Inclusive Medical Services, Inc. |
$15,000 |
| Wise Psychiatry, PC |
$10,000 |
| King MD |
$3,500 |
There was one settlement to resolve a multistate investigation by state attorneys general, with Anthem Inc. agreeing to pay a financial penalty of $48.2 million to resolve multiple violations of HIPAA and state laws in relation to its 78.8 million record data breach in 2015, which is on top of the $16 million financial penalty imposed by OCR in October 2018.
The post September 2020 Healthcare Data Breach Report: 9.7 Million Records Compromised appeared first on HIPAA Journal.




