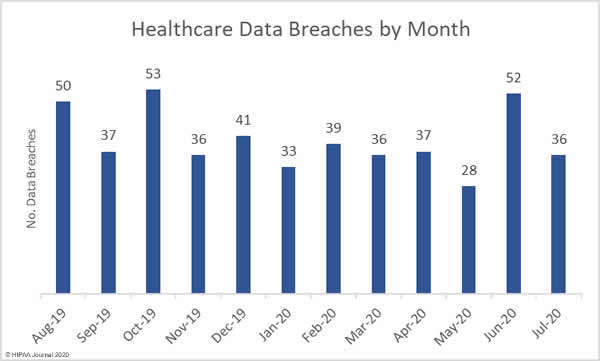
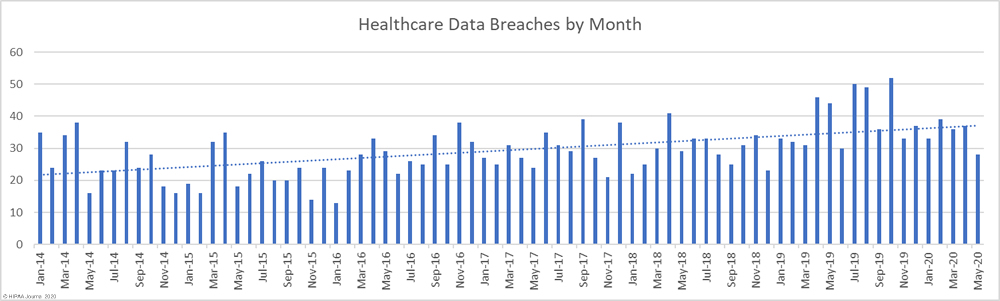
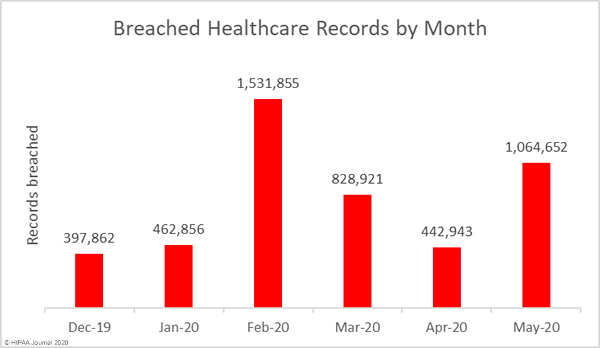
July saw a major fall in the number of reported data breaches of 500 or more healthcare records, dropping below the 12-month average of 39.83 breaches per month. There was a 30.8% month-over-month fall in reported data breaches, dropping from 52 incidents in June to 36 in July; however, the number of breached records increased 26.3%, indicating the severity of some of the month’s data breaches.
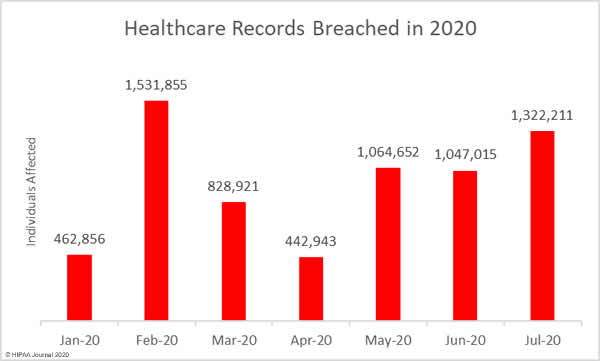
1,322,211 healthcare records were exposed, stolen, or impermissibly disclosed in July’s reported breaches. The average breach size was 36,728 records and the median breach size was 6,537 records.
Largest Healthcare Data Breaches Reported in July 2020
14 healthcare data breaches of 10,000 or more records were reported in July, with two of those breaches involving the records of more than 100,000 individuals, the largest of which was the ransomware attack on Florida Orthopaedic Institute which resulted in the exposure and potential theft of the records of 640,000 individuals. The other 100,000+ record breach was suffered by Behavioral Health Network in Maine. The breach was reported as a “malware” attack that prevented records from being accessed. 129,871 healthcare records were compromised in that attack.
| Name of Covered Entity | State | Covered Entity Type | Individuals Affected | Type of Breach |
| Florida Orthopaedic Institute | FL | Healthcare Provider | 640,000 | Hacking/IT Incident |
| Behavioral Health Network, Inc. | MA | Healthcare Provider | 129,571 | Hacking/IT Incident |
| NCP Healthcare Management Company | MA | Business Associate | 78,070 | Hacking/IT Incident |
| Walgreen Co. | IL | Healthcare Provider | 72,143 | Theft |
| Allergy and Asthma Clinic of Fort Worth | TX | Healthcare Provider | 69,777 | Hacking/IT Incident |
| WellCare Health Plans | FL | Health Plan | 50,439 | Unauthorized Access/Disclosure |
| Maryland Health Enterprises DBA Lorien Health Services | MD | Healthcare Provider | 47,754 | Hacking/IT Incident |
| Central California Alliance for Health | CA | Health Plan | 35,883 | Hacking/IT Incident |
| University of Maryland Faculty Physicians, Inc. / University of Maryland Medical Center | MD | Healthcare Provider | 33,896 | Hacking/IT Incident |
| Highpoint Foot & Ankle Center | PA | Healthcare Provider | 25,554 | Hacking/IT Incident |
| Accu Copy of Greenville, Incorporated | NC | Business Associate | 21,800 | Hacking/IT Incident |
| CVS Pharmacy | RI | Healthcare Provider | 21,289 | Loss |
| Owens Ear Center | TX | Healthcare Provider | 19,908 | Unauthorized Access/Disclosure |
| University of Utah | UT | Healthcare Provider | 10,000 | Hacking/IT Incident |
| Rite Aid Corporation | PA | Healthcare Provider | 9,200 | Theft |
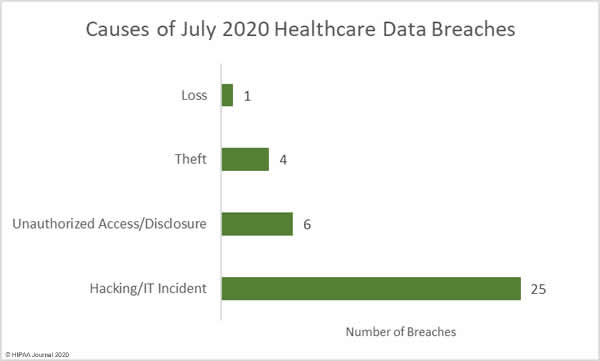
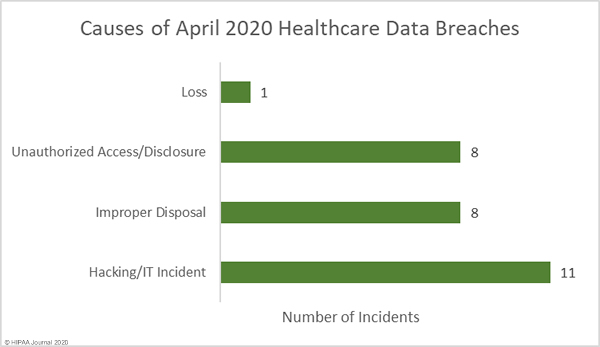
Causes of July 2020 Healthcare Data Breaches
Hacking and other IT incidents dominated the breach reports in July, accounting for 69.4% (25 incidents) of the month’s breaches and 86.3% of breached records (1,141,063 records). The mean breach size was 45,643 records with a median size of 7,000 records.
There were 6 unauthorized access/disclosure incidents reported. 76,553 records were breached in those incidents, with a mean breach size of 12,759 records and a median size of 2,123 records. There were 4 breaches categorized as theft involving the PHI/ePHI of 83,306 individuals. The mean breach size was 20,827 records and the median breach size was 5,332 records. One loss incident was reported that involved the PHI/ePHI of 20,827 individuals.
Many pharmacies across the United States were looted during the period of civil unrest in the wake of the death of George Floyd, with the Walgreens, CVS, and Rite Aid pharmacy chains hit particularly hard. In addition to the theft of prescription medications, devices containing ePHI and paperwork containing sensitive patient information were also stolen in the break-ins.
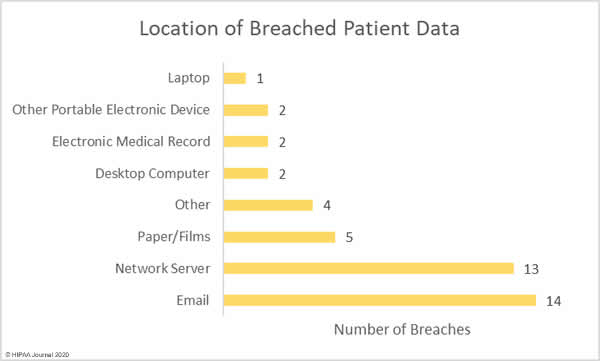
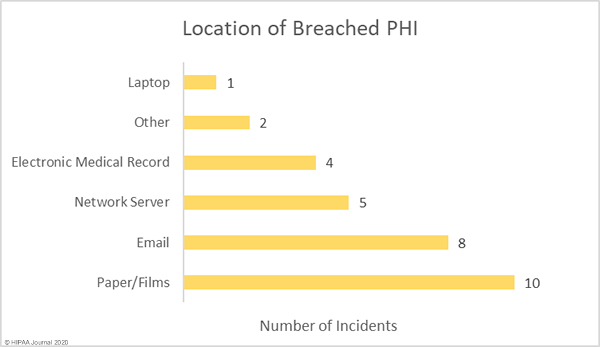
Phishing attacks usually dominate the healthcare breach reports and while email-related breaches were the most common type of breach in July, network server breaches were in close second, most commonly involving the use of malware or ransomware. The increase in the latter is certainly a cause of concern, especially considering the rise in human-operated ransomware attacks that involve the theft of patient data prior to file encryption. These attacks see patient data exposed or sold if the ransom is not paid, but there is no guarantee that stolen data will be deleted even if the ransom is paid. Phishing and ransomware attacks are likely to continue to be the leading causes of data breaches over the coming months.
Spam filters, web filters, and end user training are essential for reducing susceptibility to phishing attacks, along with multi-factor authentication on email accounts. Ransomware and other forms of malware are commonly delivered by email and these measures are also effective at blocking attacks. It is also essential for vulnerabilities to be patched promptly. Many of the recent ransomware attacks have involved the exploitation of vulnerabilities, even though patches to address the flaws were released several weeks or months prior to the attacks. Brute force tactics continue to be used on RDP, so it is essential for storing passwords to be set. Human operated ransomware attacks often see attackers gain access to healthcare networks weeks before ransomware is deployed. By monitoring networks and event logs for anomalous user behavior, it may be possible to detect and block an attack before ransomware is deployed.
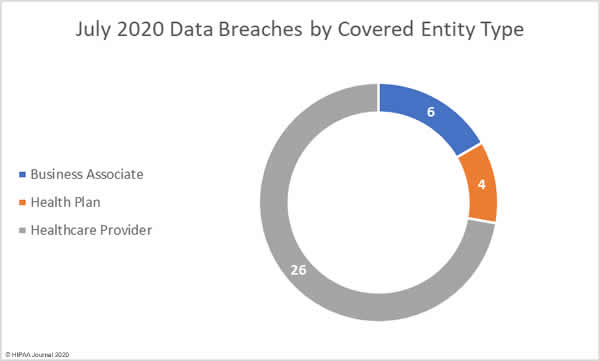
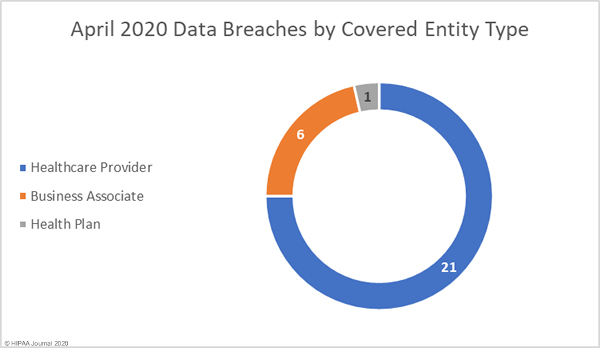
Healthcare Data Breaches by Covered Entity Type
There were 26 data breaches reported by healthcare providers in July 2020, 4 by health plans, and 6 breaches were reported by business associates of HIPAA-covered entities. A further three breaches were reported by a covered entity but had some business associate involvement.
July 2020 Healthcare Data Breaches by State
The 36 data breaches were reported by HIPAA-covered entities and business associates in 21 states. California and Texas were worst affected with 4 breaches apiece, followed by Florida and Pennsylvania with three breaches, and two breaches in each of Illinois, Massachusetts, Maryland, North Carolina, and Wisconsin. One breach was reported in each of Alaska, Arizona, Colorado, Connecticut, Michigan, Nebraska, New Mexico, New York, Ohio, Rhode Island, Utah, and West Virginia.
HIPAA Enforcement in July 2020
The HHS’ Office for Civil Rights has issued multiple notices of enforcement discretion this year spanning the duration of the nationwide COVID-19 public health emergency; however, that does not mean that OCR has scaled back enforcement of HIPAA Rules. OCR accepts that it may be difficult to ensure continued compliance with all aspects of HIPAA Rules during such difficult times, but entities that are discovered to have violated the HIPAA Rules can and will still face financial penalties for noncompliance.
In July, OCR announced two settlements had been reached with HIPAA covered entities to resolve HIPAA violation cases. A settlement of $1,040,000 was agreed with Lifespan Health System Affiliated Covered Entity to resolve HIPAA violations discovered during the investigation of a 2017 breach report submitted following the theft of an unencrypted laptop computer.
OCR discovered multiple compliance failures. Lifespan had not implemented encryption on portable devices that stored ePHI, even though Lifespan was aware of the risk of ePHI exposure. There were also device and media control failures, the failure to enter into business associate agreements with vendors, and an impermissible disclosure of 20,431 patients’ ePHI.
Metropolitan Community Health Services dba Agape Health Services was investigated over a 2011 data breach of 1,263 patient records and OCR discovered longstanding, systemic noncompliance with the HIPAA Security Rule. A settlement of $25,000 was agreed with OCR to resolve the violations, with the small size of the healthcare provider taken into consideration when determining an appropriate penalty amount.
The post July 2020 Healthcare Data Breach Report appeared first on HIPAA Journal.