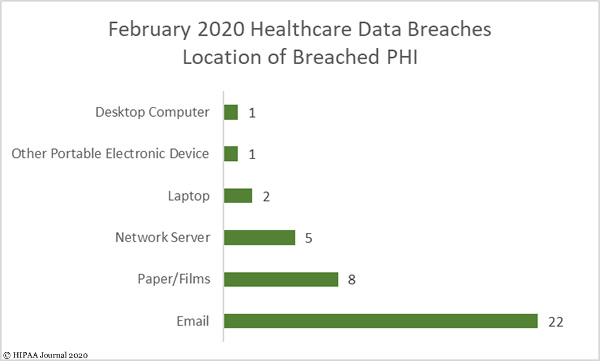
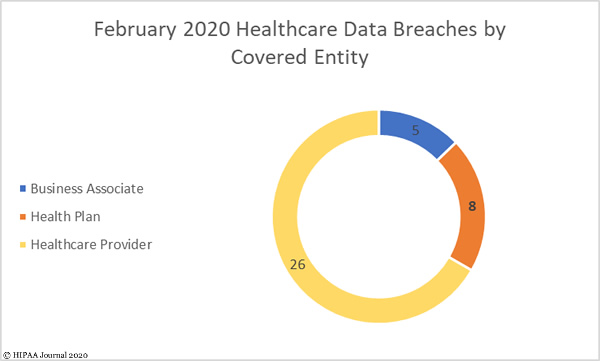
Human-operated ransomware attacks on healthcare organizations and critical infrastructure have increased during the COVID-19 pandemic. Dozens of attacks have occurred on healthcare organizations in recent weeks, including Parkview Medical Center, ExecuPharm, and Brandywine Counselling and Community Services.
Many ransomware attacks are automated and start with a phishing email. Once ransomware is downloaded, it typically runs its encryption routine within an hour. Human-operated ransomware attacks are different. Access is gained to systems several weeks or months before ransomware is deployed. During that time, the attackers obtain credentials, move laterally, and collect and exfiltrate data before encrypting files with ransomware.
The attackers can lay dormant in systems for several months before choosing their moment to deploy the ransomware to maximize the disruption caused. The COVID-19 pandemic is the ideal time for deployment of ransomware on healthcare organizations and others involved in the response to COVID-19, as there is a higher probability that the ransom will be paid to ensure a quick recovery.
In the first two weeks of April alone, dozens of attacks have been conducted by a range of advanced cybercriminal organizations on healthcare providers, medical billing companies, research and pharmaceutical firms, and suppliers to the healthcare industry, along with attacks on educational software providers, manufacturers, government institutions, and aid organizations, according to data from Microsoft.
During the first two weeks in April, Microsoft observed human-operated ransomware attacks using 10 different ransomware variants: RobbinHood, Maze, PonyFinal, REvil (Sodinokibi), Valet Loader, NetWalker, Paradise, RagnarLocker, MedusaLocker, and LockBit. While it may appear that ransomware activity has increased in recent weeks, Microsoft explains that in the April attacks, the attackers initially compromised the systems much earlier and they have been biding their time before deploying ransomware. In many cases, the initial compromise occurred several months before the ransomware was deployed.
Different threat groups use different ransomware variants to encrypt files, but the attacks usually occur in the same way. First, the attackers gain access to systems, then they steal credentials, move laterally, exfiltrate sensitive data, establish persistence, before delivering and executing the ransomware payload.
Microsoft has shared information on how the attackers gain access to systems to help network defenders harden their defenses and block attacks. While there are many possible ways of attacking an organization, these threat actors typically use the same methods to gain access.
One of the most common methods of attack is through Remote Desktop Protocol and Virtual Desktop endpoints that lack multi-factor authentication, either through the use of stolen credentials or through brute force tactics to guess weak passwords. Without multi-factor authentication, the stolen credentials can be used to access systems. Since valid credentials are used, network defenders fail to identify attackers accessing their systems.
Weaknesses in internet-facing systems are commonly exploited, such as misconfigured web servers, EHRs, backup servers, and systems management servers. Unpatched vulnerabilities are also often exploited to gain access, with several of the April 2020 attacks having exploited the Citrix Application Delivery Controller (ADC) flaw, CVE-2019-19781, and the Pulse Secure VPN flaw, CVE-2019-11510. Vulnerabilities in unsupported operating systems are also exploited. To block attacks, it is essential for operating systems to be updated to supported versions and for patches to be applied as soon as possible after release.
These are not smash-and-grab raids where ransomware is quickly deployed to obtain a quick payout. All of the threat actors using the above ransomware variants take their time to obtain administrative credentials and move laterally with the aim of infiltrating an organization’s entire environment, including EHRs, inboxes, endpoints, and applications. Almost all of the attacks involved the exfiltration of data, either to sell for profit, use for their own nefarious purposes, or to pressure organizations into paying the ransom.
“After gaining control over a domain admin account through credential theft, campaign operators used Cobalt Strike, PsExec, and a plethora of other tools to deploy various payloads and access data. They established fileless persistence using scheduled tasks and services that launched PowerShell-based remote shells,” explained Microsoft. “They also turned on Windows Remote Management for persistent control using stolen domain admin privileges. To weaken security controls in preparation for ransomware deployment, they manipulated various settings through Group Policy.” In virtually all cases, accounts had been set up and backdoors used to ensure networks could continue to be accessed after the attack, even after the ransom was paid.
The time between the initial compromise and the deployment of ransomware gives network defenders an opportunity to identify and block the attacks. While threat actors take steps to hide their activity, it is possible to identify their activities as they move laterally. Network defenders should be checking for activity that could indicate an attack in progress, such as the use of malicious PowerShell commands, Cobalt Strike, and other penetration-testing tools. Security logs should be checked to identify any signs of tampering and checks should be performed to identify registry modifications and suspicious access to Local Security Authority Subsystem Service (LSASS).
Microsoft also offers detailed advice on hardening security to prevent attacks and the steps that should be taken if an attack is discovered, including investigation, isolation of compromised endpoints, and recovery.
The post Advice for Healthcare Organizations on Preventing and Detecting Human-Operated Ransomware Attacks appeared first on HIPAA Journal.