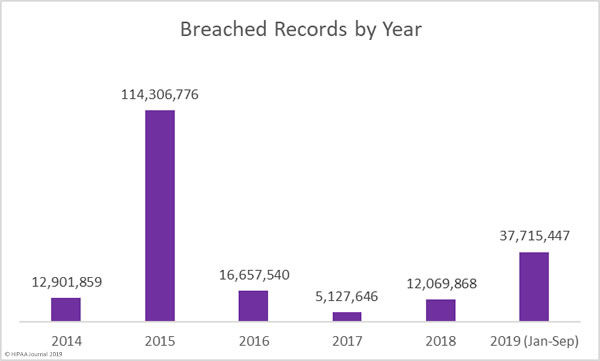
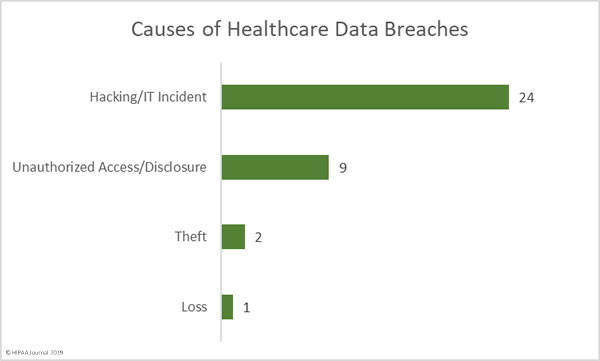
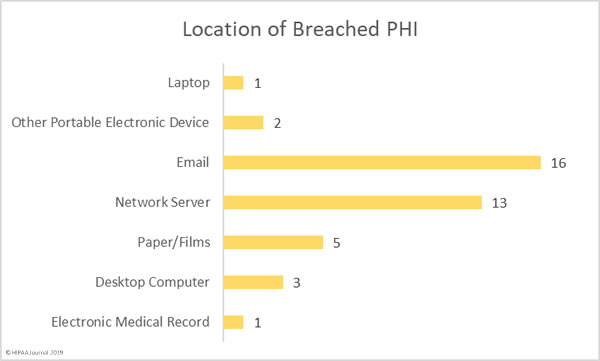
A recent survey has highlighted the cost of healthcare industry data breaches, the extent to which the healthcare industry is under attack, and how often those attacks succeed.
The survey was conducted by Black Book Market Research on 2,876 security professionals at 733 provider organizations between Q4, 2018 and Q3, 2019. Respondents were asked their views on cybersecurity to identify vulnerabilities and security gaps and determine why so many of these cyberattacks are succeeding.
96% of surveyed IT professionals believed that cybercriminals are outpacing medical enterprises, which is no surprise given that 93% of healthcare organizations reported having experienced a data breach since Q3, 2016. According to the report, 57% of organizations had experienced more than five data breaches during that time period. More than half of the data breaches reported by healthcare organizations were the result of hacks and other attacks by external threat actors.
The healthcare industry is being attacked because providers and insurers hold huge quantities of sensitive and valuable information and there are often security gaps that can be easily exploited. Even though the threat of attack is so high, the industry remains highly susceptible to data breaches.
The cost of these attacks to the healthcare industry is considerable. According to the report, the cost of data breaches at hospital organizations in 2019 was $423 per record. The report predicts that, based on the current level of data breaches, they will end up costing the healthcare industry $4 billion by the end of the year. Given the current trends and the annual increases in healthcare data breaches, that figure is likely to be considerably higher in 2020.
The survey confirmed that one of the main reasons why the healthcare industry is susceptible is due to budget constraints. Legacy systems and devices are still widely used in the healthcare industry, but the cost of replacing those systems is difficult to justify when that money does not increase revenue.
Overall, investment in cybersecurity for 2020 is planned to be increased to around 6% of total IT budgets at hospital systems, but smaller practices have seen a decrease in investment in cybersecurity, especially at physician organizations where only 1% of the 2020 IT budget will be spent on cybersecurity. 90% of hospital representatives surveyed said their cybersecurity budget had not changed since 2016.
When cybersecurity solutions are purchased, in many cases purchases are made blindly. A third of surveyed hospital executives said they chose cybersecurity solutions without much vision or discernment. 92% of data security product or service decisions since 2016 were made by C-level executives without including department managers and users in the purchasing decision. Only 4% of organizations said they had a steering committee to help evaluate the impact of investment in cybersecurity.
Many healthcare organizations are also operating without a dedicated security executive. Only 21% said they had a dedicated security executive and only 6% said that individual was the Chief Information Security Officer. At physician groups with more than 10 clinicians, only 1.5% said they had a dedicated CISO. Part of the reason is a shortage of qualified staff. 21% of healthcare organizations said they have had to outsource the role and are using cybersecurity-as-a-service as a stop gap measure.
The post Healthcare Data Breaches Predicted to Cost Industry $4 Billion in 2019 appeared first on HIPAA Journal.