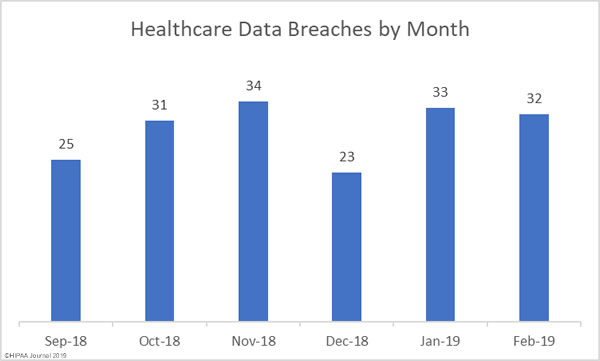
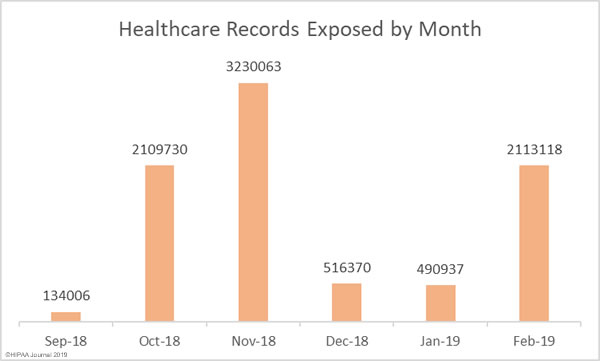
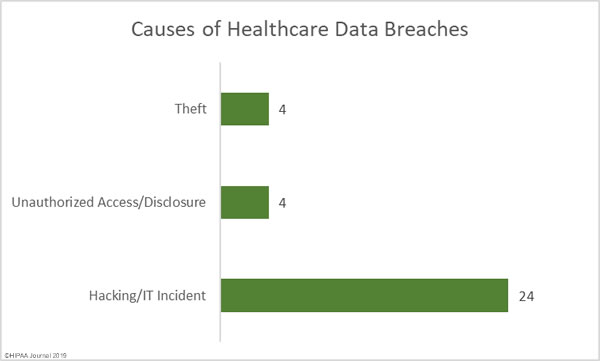
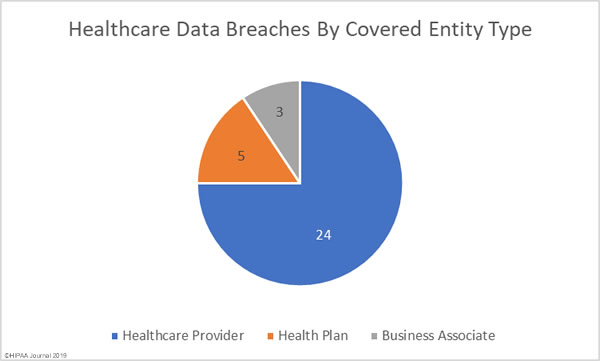
Health information is the least likely data type to be encrypted, even though health information is highly valuable to cybercriminals, according to the Global Encryption Trends Study conducted by the Ponemon Institute on behalf of cryptographic solution provider nCipher.
The study was conducted on 5,856 people across several industry sectors in 14 countries, including the United States. The aim of the study was to investigate data encryption trends, the types of data most likely to be encrypted, how extensively encryption has been adopted to improve security, and the challenges faced by companies when encrypting data.
The study shows the use of encryption has steadily increased over the past four years. 45% of surveyed organizations said they have an overall encryption plan or strategy that is applied across the whole organization. 42% said they have a limited encryption plan or strategy, with encryption only used on certain applications and data types. 13% of respondents said they do not use encryption at all on any type of data.
The use of encryption varies considerably from country to country. Germany leads the world with the highest prevalence of encryption, followed by the United States, Australia, and the United Kingdom. Out of the 14 countries represented in the survey, the Russian Federation and Brazil had the lowest prevalence of encryption. 65% of companies in the United States had an overall encryption plan that was consistently applied across the whole organization.
The industries that had the highest prevalence of encryption were tech & software (52%), financial services (50%), and the healthcare and pharmaceutical industries (49%).
Encryption technology varied considerably and there was no single technology that dominates in organizations. The most common uses of encryption were for Internet communications, databases and laptop hard drives.
The main reasons for implementing encryption, cited by 54% of respondents, were to protect sensitive intellectual property and customers’ personal information.
The types of data most commonly encrypted are payment-related data (55%), financial records (54%), HR/employee data (51%), and intellectual property (51%). Health information was the least likely type of data to be encrypted. This is surprising, given the value of healthcare data to cybercriminals and the harm that can be caused should information fall into the wrong hands. Only 24% of respondents said health data was routinely encrypted.
Organizations looking to encrypt data face several challenges. The biggest challenge which was faced by 69% of respondents was identifying all sensitive data on the network. The initial implementation of encryption was a major challenge for 49% of respondents and 32% of respondents said they faced problems classifying which data they should encrypt.
One of the biggest encryption headaches is key management. Respondents were asked to rate key management on a pain scale of 1-10. 61% of respondents said key management was very painful and managing keys was a major challenge.
The main reason why key management is difficult is a lack of clear ownership of the key management function, a lack of skilled personnel, and isolated or fragmented key management systems.
Various key management systems are used by organizations, the most common being formal key management policy (KMP), followed by formal key management infrastructure (KMI) and manual process.
The post Study Reveals Health Information the Least Likely Data Type to be Encrypted appeared first on HIPAA Journal.