Our 2018 healthcare data breach report reveals healthcare data breach trends, details the main causes of 2018 healthcare data breaches, the largest healthcare data breaches of the year, and 2018 healthcare data breach fines. The report was compiled using data from the Department of Health and Human Services’ Office for Civil Rights (OCR).
2018 Was a Record-Breaking Year for Healthcare Data Breaches
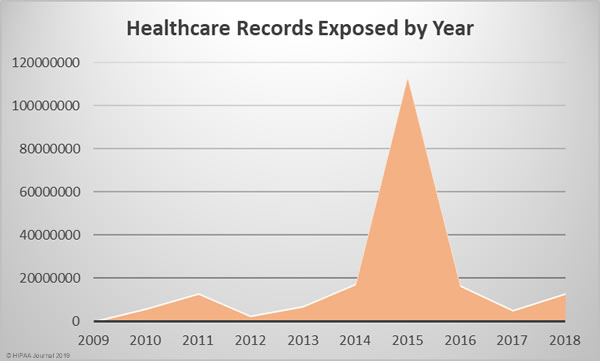
Since October 2009, the Department of Health and Human Services’ Office for Civil Rights has been publishing summaries of U.S. healthcare data breaches. In that time frame, 2,545 healthcare data breaches have been reported. Those breaches have resulted in the theft, exposure, or impermissible disclosure of 194,853,404 healthcare records. That equates to the records of 59.8% of the population of the United States.
The number of reported healthcare data breaches has been steadily increasing each year. Except for 2015, the number of reported healthcare data breaches has increased every year.
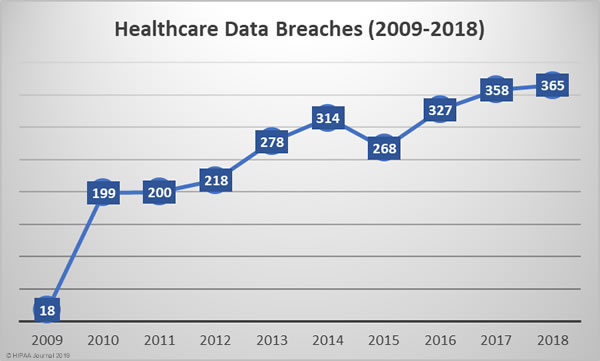
In 2018, 365 healthcare data breaches were reported, up almost 2% from the 358 data breaches reported in 2017 and 83% more breaches that 2010.
2018 was the worst year in terms of the number of breaches experienced, but the fourth worst in terms of the number of healthcare records exposed, behind 2015, 2014, and 2016. The last two years have certainly seen an improvement in that sense, although 2018 saw a 157.67% year-over-year increase in the number of compromised healthcare records.
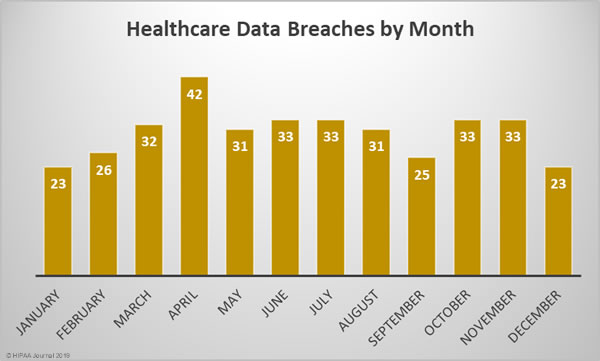
2018 Healthcare Data Breaches by Month
Healthcare Records Exposed Each Month in 2018

Largest 2018 Healthcare Data Breaches
| Rank |
Name of Covered Entity |
Covered Entity Type |
Individuals Affected |
Type of Breach |
| 1 |
AccuDoc Solutions, Inc. |
Business Associate |
2,652,537 |
Hacking/IT Incident |
| 2 |
Iowa Health System d/b/a UnityPoint Health |
Business Associate |
1,421,107 |
Hacking/IT Incident |
| 3 |
Employees Retirement System of Texas |
Health Plan |
1,248,263 |
Unauthorized Access/Disclosure |
| 4 |
CA Department of Developmental Services |
Health Plan |
582,174 |
Theft |
| 5 |
MSK Group |
Healthcare Provider |
566,236 |
Hacking/IT Incident |
| 6 |
CNO Financial Group, Inc. |
Health Plan |
566,217 |
Unauthorized Access/Disclosure |
| 7 |
LifeBridge Health, Inc |
Healthcare Provider |
538,127 |
Hacking/IT Incident |
| 8 |
Health Management Concepts, Inc. |
Business Associate |
502,416 |
Hacking/IT Incident |
| 9 |
AU Medical Center, INC |
Healthcare Provider |
417,000 |
Hacking/IT Incident |
| 10 |
SSM Health St. Mary’s Hospital – Jefferson City |
Healthcare Provider |
301,000 |
Improper Disposal |
Click for further information on the largest healthcare data breaches of 2018.
Causes of 2018 Healthcare Data Breaches
The biggest causes of healthcare data breaches in 2018 were hacking/IT incidents (43.29%) and unauthorized access/disclosures (39.18%), which together accounted for 82.47% of all data breaches reported in 2018. There were 42 theft incidents (11.5%) reported in 2018, 13 cases (3.56%) of lost PHI/ePHI, and 9 cases (2.47%) of improper disposal of PHI/ePHI.
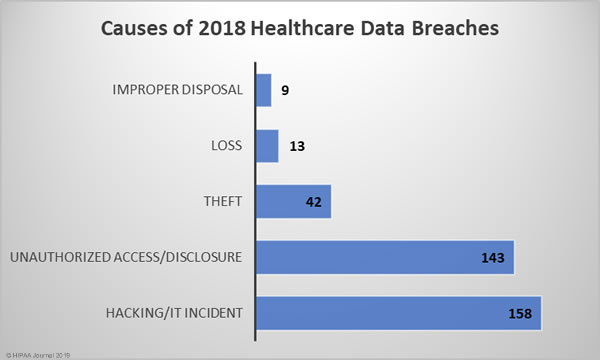
There was a 5.33% annual increase in hacking/IT incidents – 158 breaches compared to 150 in 2017. While the number of hacking/IT-related breaches rose only slightly, the breaches were far more damaging in 2018 and resulted in the theft/exposure of 161.89% more healthcare records. The mean breach size of hacking/IT incidents in 2017 was 23,218 records and in 2018 it rose to 57,727 records in 2018 – A year-over-year increase of 148.63%.
2018 saw an even larger increase in unauthorized access/disclosure incidents. 14.4% more incidents were reported in 2018 than 2017 and 146.49% more healthcare records were exposed in unauthorized access/disclosure incidents than the previous year. The mean breach size of unauthorized access/disclosure incidents in 2017 was 9,893 records and 21,316 records in 2018 – An increase of 115.47%.
Loss, theft, and improper disposal incidents all declined in 2018. Loss incidents fell from 16 to 13 year-over-year (-18.75%), improper disposal incidents fell from 11 to 9 (-18.18%), and theft incidents fell from 56 in 2017 to 42 in 2018 (-25%).
While there was a reduction in the number of cases of theft and improper disposal year-over-year, the severity of those two types of breaches increased in 2018. The mean breach size of theft incidents rose from 6,908 records in 2017 to 16,605 records in 2018 – A rise of 140.37%. Improper disposal incidents increased from a mean of 2,802 records in 2017 to 37,794 records in 2018 – A rise of 1,248.82%.
There was a slight reduction in the severity of loss incidents, which fell from an average of 2,461 records in 2017 to 2,305 – A fall of 6.33%.

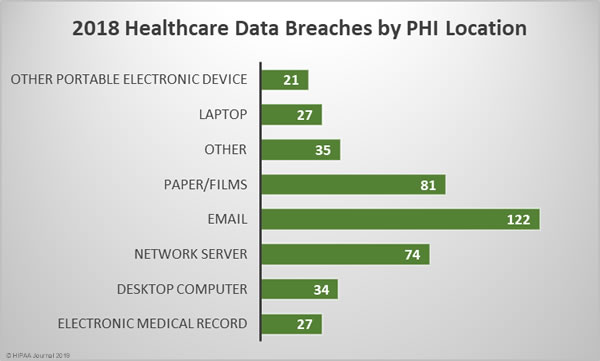
Location of Breached Protected Health Information
The breakdown of 2018 healthcare data breaches by the location of breached PHI highlights the importance of increasing email security and providing further training to healthcare employees. 33.42% of all healthcare data breaches in 2018 involved email. Those breaches include phishing attacks, other unauthorized email access incidents and misdirected emails.
While healthcare organizations may be focused on preventing cyberattacks and improving technical defenses, care must still be taken with physical records. There were 81 breaches of physical PHI such as charts, documents, and films in 2018. Paper/films were involved in 22.19% of breaches.
The next most common location of breached PHI was network servers, which were involved in 20.27% of breaches in 2018. These incidents include hacks, ransomware attacks, and malware-related breaches.
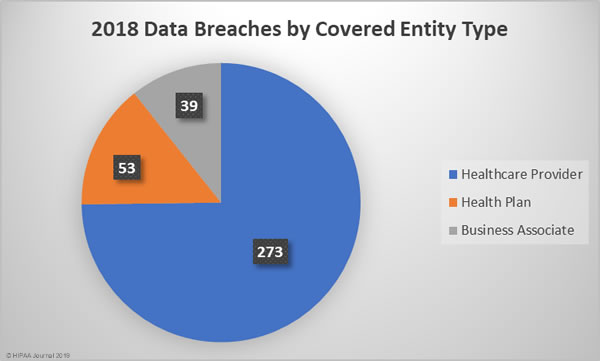
2018 Healthcare Data Breaches by Covered Entity Type
Given the relative percentages of healthcare providers to health plans, it is no surprise that more healthcare provider data breaches occurred. 74.79% of the year’s breaches affected healthcare providers, 14.52% occurred at health plans, and 10.68% affected business associates of HIPAA-covered entities.
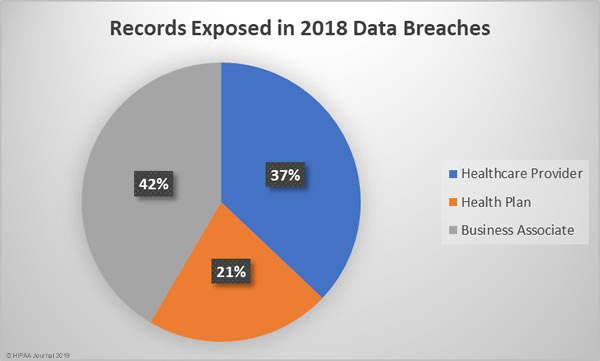
Business associate data breaches were the most severe, accounting for 42% of all exposed/stolen records in 2018, followed by healthcare provider breaches and breaches at health plans. The mean breach size for business associate data breaches was 140,915 records, 53,471 records for health plan data breaches, and 17,974 records for healthcare provider data breaches.
States Worst Affected By 2018 Healthcare Data Breaches
Being the two most populated states, it is no surprise that California and Texas were the worst affected by healthcare data breaches in 2018. Only four states avoided healthcare data breaches in 2018 – New Hampshire, South Carolina, South Dakota, Vermont.
| Number of Breaches |
State |
| 38 |
California |
| 32 |
Texas |
| 19 |
Illinois |
| 18 |
Florida |
| 18 |
Massachusetts |
| 16 |
New York |
| 14 |
Missouri |
| 11 |
Pennsylvania |
| 10 |
Iowa, Michigan, Minnesota, Wisconsin |
| 9 |
Maryland, Ohio, Oregon |
| 8 |
Arizona, North Carolina, Virginia |
| 7 |
Georgia, New Jersey, Tennessee, Washington |
| 6 |
Colorado, Kansas, Nevada |
| 5 |
Arkansas, Indiana, Nebraska, New Mexico, Utah |
| 4 |
Connecticut, Kentucky |
| 3 |
Alaska, Louisiana, Mississippi, Montana, Rhone Island |
| 2 |
Alabama, District of Columbia, Oklahoma, Wyoming |
| 1 |
Hawaii, Idaho, Maine, North Dakota, West Virginia |
| 0 |
New Hampshire, South Carolina, South Dakota, Vermont |
HIPAA Fines and Settlements in 2018
The HHS’ Office for Civil Rights is the main enforcer of HIPAA Rules and has the authority to issue financial penalties for violations of Health Insurance Portability and Accountability Act (HIPAA) Rules. State attorneys general also play a role in the enforcement of HIPAA compliance and can also issue fines for HIPAA violations.
In 2018, OCR issued 10 financial penalties to resolve HIPAA violations that were discovered during the investigation of healthcare data breaches and complaints.
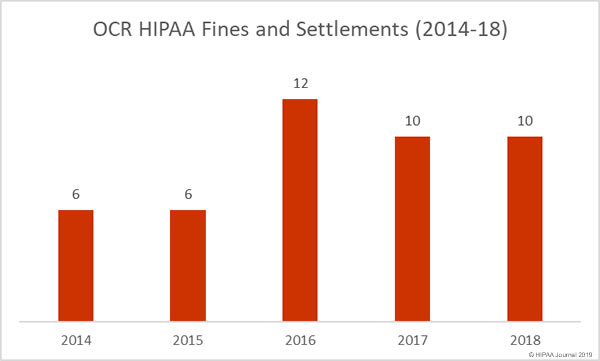
The financial penalties issued by OCR in 2018 totaled $25,683,400, making 2018 a record-breaking year for HIPAA penalties.
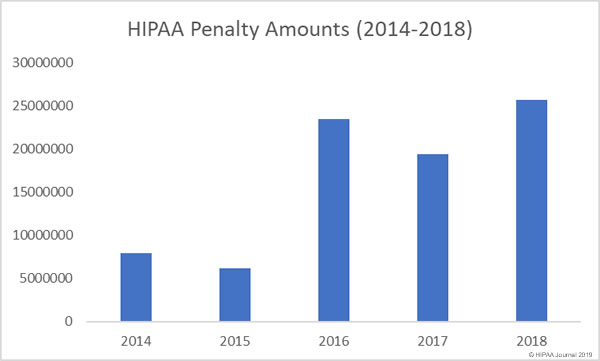
12 financial penalties were issued by state attorneys general over violations of HIPAA Rules.
You can read more about the – HIPAA fines and settlements in 2018 here.
The post Analysis of 2018 Healthcare Data Breaches appeared first on HIPAA Journal.










