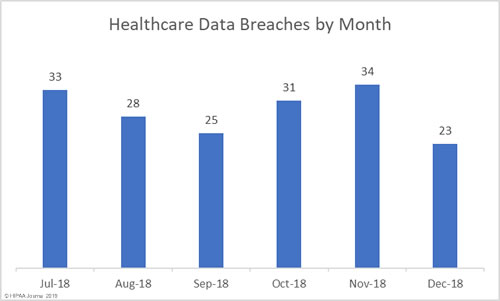
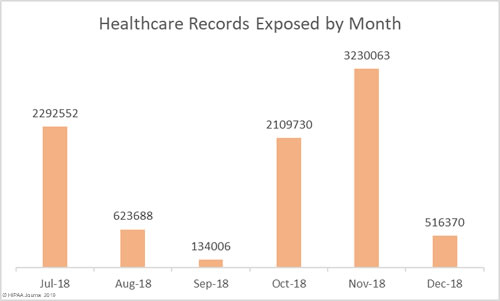
November was a particularly bad month for healthcare data breaches, so it is no surprise that there was an improvement in December. November was the worst month of the year in terms of the number of healthcare records exposed (3,230,063) and the second worst for breaches (34). December was the second-best month for healthcare data breaches with 23 incidents reported, only one more than January.
In total, 516,370 records were exposed, impermissibly disclosed, or stolen in breaches reported in December: A considerable improvement on November. Were it not for the late reporting of the Adams County breach, December would have been the best month of the year to date in terms of the records exposed. The Adams County breach was experienced in March 2018, confirmed on June 29, yet reporting to OCR was delayed until December 11.
Largest Healthcare Data Breaches in December 2018
| Rank | Name of Covered Entity | Covered Entity Type | Individuals Affected | Type of Breach |
| 1 | Adams County | Healthcare Provider | 258,120 | Unauthorized Access/Disclosure |
| 2 | JAND Inc. d/b/a Warby Parker | Healthcare Provider | 177,890 | Hacking/IT Incident |
| 3 | University of Vermont Health Network – Elizabethtown Community Hospital | Healthcare Provider | 32,470 | Hacking/IT Incident |
| 4 | The Podiatric Offices of Bobby Yee | Healthcare Provider | 24,000 | Hacking/IT Incident |
| 5 | Choice Rehabilitation | Business Associate | 4,309 | Hacking/IT Incident |
| 6 | Virtual Radiologic Professionals, LLC | Healthcare Provider | 2,568 | Hacking/IT Incident |
| 7 | Kent County Community Mental Health Authority | Healthcare Provider | 2,284 | Hacking/IT Incident |
| 8 | Butler County Board of County Commissioners | Health Plan | 1,912 | Unauthorized Access/Disclosure |
| 9 | Barnes-Jewish Hospital | Healthcare Provider | 1,643 | Hacking/IT Incident |
| 10 | Tift Regional Medical Center | Healthcare Provider | 1,045 | Hacking/IT Incident |
Causes of December 2018 Healthcare Data Breaches
The healthcare industry experiences more insider breaches than other industry sectors, although in December, hacking/IT Incidents outnumbered unauthorized/access disclosure incidents by almost two to one. Eight of the top ten data breaches for the month were hacks, ransomware attacks, and other IT incidents.
While unauthorized access/disclosure incidents usually impact fewer individuals that hacking breaches, that was not the case in December. The largest breach of the month was the unauthorized accessing of a network server by a former employee of Adams County, WI.
In total, 264,049 healthcare records were exposed in the 7 unauthorized access/disclosure incidents reported in December. The mean breach size was 37,721 records and the median breach size was 911 records.
250,404 healthcare records were exposed in the 13 hacking/IT incidents. The mean breach size was 19,261 records and the median breach size was 1,643 records.
There were two theft incidents reported in December and one case of improper disposal of paper records. No lost devices were reported.
Location of Breached Protected Health Information
Phishing attacks continue to plague healthcare organizations and December was no exception. The largest phishing incident reported in December affected 32,470 patients of Elizabethtown Community Hospital. The PHI was contained in a single email account.
Three email accounts were compromised at Kent County Community Mental Health Authority, although they only contained the PHI of 2,200 individuals.
The most common location of breached PHI in December was email, although network server breaches were more severe. The two largest December 2018 healthcare data breaches were network server incidents which impacted 436,010 individuals – 84.43% of the total number of breached records in December.
Data Breaches by Covered-Entity Type
Health plans made it through November without reporting any data breaches, although they didn’t fare so well in December. 6 health plan data breaches were announced in December; however, all were relatively small, with only the breach at Butler County Board of County Commissioners impacting more than 1,000 plan members (1,912).
One data breach was reported by a business associate of a HIPAA-covered entity, although a further three breaches had some business associate involvement. The remaining 16 breaches were reported by healthcare providers.
Healthcare Data Breaches by State
In December 2018, healthcare organizations in 13 states reported PHI breaches. Minnesota was the worst affected state with a total of four breaches followed by Arizona with three. There were two breaches reported by healthcare organizations based in each of California, Missouri, New York, Ohio, and Wisconsin, and a single breach was experienced in each of Georgia, Illinois, Kentucky, Massachusetts, Michigan, and Pennsylvania.
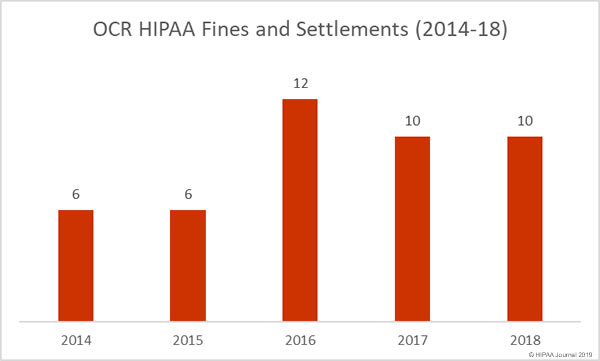
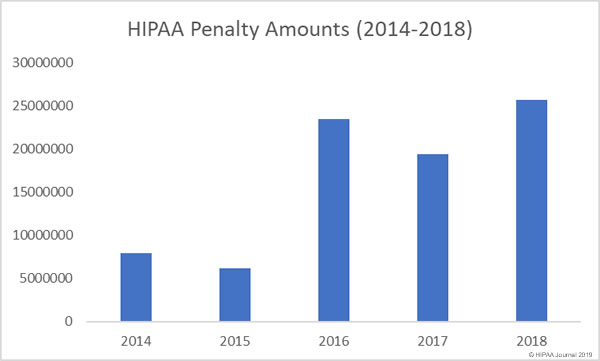
HIPAA Fines and Settlements in December 2018
The Department of Health and Human Services’ Office for Civil Rights (OCR) agreed two settlements with HIPAA-covered entities in December to resolve violations of HIPAA Rules. OCR finished the year on ten fines and settlements, the same number as 2017. (You can view all 2018 HIPAA fines and settlements here).
Advanced Care Hospitalists, a Florida Contractor Physicians’ Group, was investigated by OCR following the submission of a breach report in April 2014. The report stated the PHI of 400 patients had been subject to unauthorized access, although the number of individuals affected was subsequently increased to 8,855 patients.
OCR confirmed there had been a preventable impermissible disclosure of PHI, and found that a business associate had been engaged without first entering into a business associate agreement. Additionally, insufficient security measures had been implemented and there had been no effort to comply with HIPAA Rules prior to April 1, 2014. Advanced Care Hospitalists and OCR settled the HIPAA violation case for $500,000.
On June 7, 2013, OCR received a complaint about Pagosa Springs Medical Center, a critical access hospital in Colorado, which had failed to terminate access to a web-based scheduling calendar after an employee’s contract had been terminated. The OCR investigation confirmed the former employee accessed the calendar on two occasions after leaving employment.
For the failure to terminate employee access and the lack of a business associate agreement with Google covering Google Calendar resulted in a financial penalty of $111,400 for Pagosa Springs Medical Center.
There were two financial penalties issued by state Attorneys General in December to resolve violations of HIPAA Rules.
The Massachusetts Attorney General fined McLean Hospital $75,000 over a breach of 1,500 patients PHI. The information was stored on backup tapes that had been taken offsite by an employee. When the employee was terminated, McLean Hospital was unable to recover two of the backup tapes.
The New Jersey Attorney General issued a financial penalty of $100,000 to EmblemHealth over an impermissible disclosure of PHI. In 2016, an EmblemHealth mailing had Social Security numbers printed on the outside of envelopes. This was the second fine for EmblemHealth in relation to the breach. The New York Attorney General had previously settled its case with EmblemHealth for $575,000 earlier in the year.
The post December 2018 Healthcare Data Breach Report appeared first on HIPAA Journal.