The healthcare industry has had more than its fair share of hacking incidents, but the biggest threat comes from within. The actions of healthcare providers, health insurers, and their employees cause more breaches than hacks, malware, and ransomware attacks.
Researchers at Michigan State University and Johns Hopkins University analyzed data breaches reported to the Department of Health and Human Services’ Office for Civil Rights (OCR) over the past 7 years and found that more than half of breaches were the result on internal negligence.
The research study, which was recently published in the journal JAMA Internal Medicine, is a follow-on from a 2017 study that explored the risk of hospital data breaches and the types of hospitals that were most prone to data breaches. While the previous research cast light on which hospitals were most vulnerable, little information was available on the main causes of the breaches. The latest study addresses that gap in knowledge.
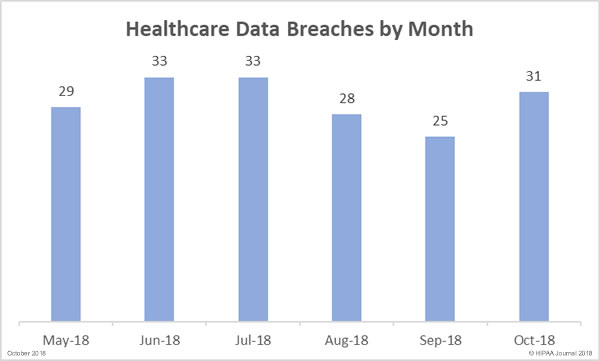
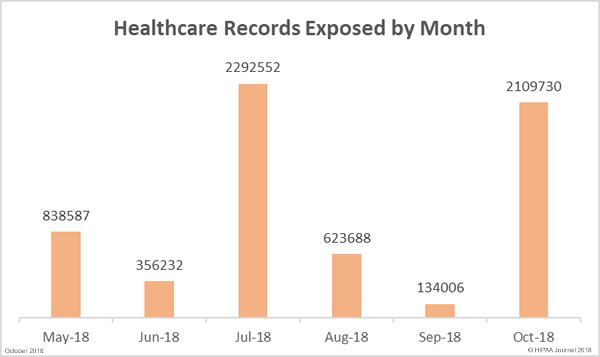
The researchers performed a retrospective analysis of the 1,183 healthcare data breaches reported to OCR between October 21, 2009 and December 31, 2017. Those breaches resulted in the exposure of 164 million healthcare records.
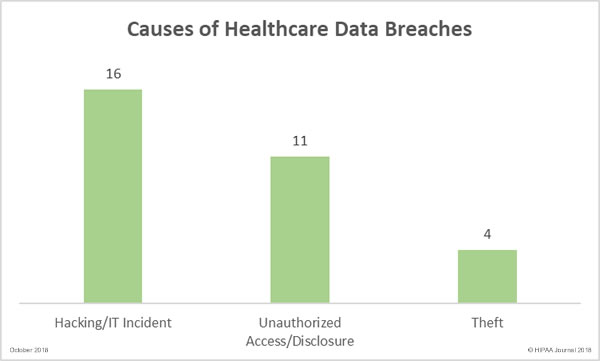
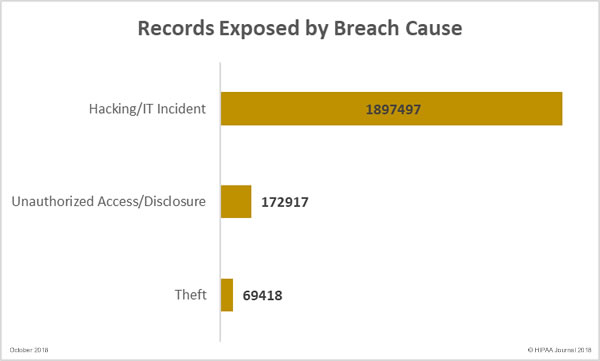
The analysis was limited to breaches of 500 or more records, as OCR does not publish summaries of smaller breaches. The breach reports split data breaches into six categories; hacking/IT incidents, unauthorized access/disclosure incidents, theft, loss, improper disposal, and unknown. 77.6% of breaches were correctly classified and 22.24% were misclassified or the cause was unknown.
The researchers discovered that theft of data by third-parties or unknown individuals was the single leading breach cause, accounting for 32.5% of incidents, with mailing errors in second place (10.5%), followed by theft by current or former employees (9%). Internal/external hacking incidents accounted for around 20% of breaches, although those incidents involved 133.8 million of the 164 million compromised records. 53% of all breaches were found to have originated from inside healthcare organizations.
“One quarter of all the cases were caused by unauthorized access or disclosure – more than twice the amount that were caused by external hackers,” said Xuefeng Liang, associate professor of accounting and information systems at MSU’s Eli Broad College of Business and lead author of the study. “This could be an employee taking PHI home or forwarding to a personal account or device, accessing data without authorization, or even through email mistakes, like sending to the wrong recipients, copying instead of blind copying or sharing unencrypted content.”
An analysis of the location of breached PHI showed 46.1% of breaches involved mobile devices, paper records were involved in 28.7% of breaches and 29.3% of breaches involved network servers.
Typically, the actions taken by healthcare organizations post-breach were the use of encryption software, restricting the use of mobile devices, switching to digital records, improving physical security, strengthening firewalls and other cybersecurity protections, and enhancing monitoring and auditing.
While many breaches involve little risk to patients – the accidental disclosure of a name and address to another patient – the consequences of some breaches can be severe: For patients as well as the breached entity. Anthem Inc’s 78.8 million record breach in 2015 was used as an example. Many breach victims had tax returns filed in their names, resulting in financial losses.
In addition to the considerable cost of mitigating the breach – improving cybersecurity protections; hiring forensic investigators, cybersecurity consultants, and legal advisors; printing and mailing notification letters; providing credit monitoring services for breach victims – Anthem had to cover the cost of defending multiple class action lawsuits, which were ultimately settled for $115 million. Anthem has also recently been fined $16 million by OCR to resolve the HIPAA violations uncovered during its breach investigation. Anthem’s reputation has also been tarnished by the breach, the cost of which is difficult to calculate.
The findings of the study are important. “Healthcare entities must understand the causes of PHI breaches if they aim to effectively manage the trade-off between wider access or higher efficiency and more security,” explained the researchers in the paper.
The post 53% Of Healthcare Data Breaches Due to Insiders and Negligence appeared first on HIPAA Journal.