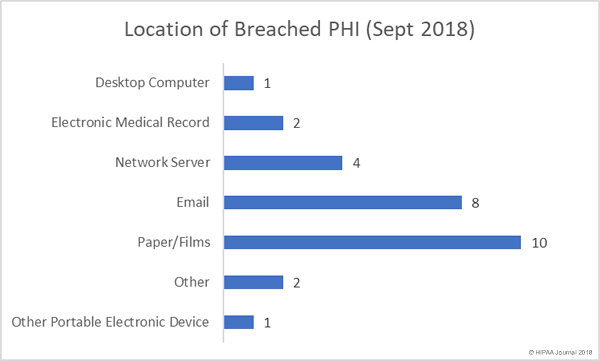
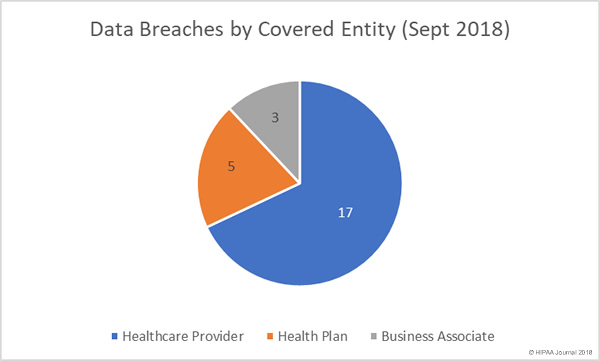
The threat actors behind SamSam ransomware have been highly active this year and most of the attacks have been conducted in the United States. Out of the 67 organizations that the group is known to have attacked, 56 were on organizations based in the United States, according to a recent analysis by cybersecurity firm Symantec.
The attacks have been conducted on a wide range of businesses and organizations, although the healthcare industry has been extensively targeted. Healthcare organizations account for 24% of the group’s ransomware attacks.
It is unclear why healthcare organizations are account for so many attacks. Symantec suggests that it could be due to healthcare organizations being easier to attack than other potential targets, or that there is a perception that healthcare providers are more likely to pay the ransom as they are reliant on access to patient data to operate.
In contrast to most ransomware attacks, the threat actors behind SamSam ransomware do not conduct random campaigns via email with the intention of infecting as many organizations as possible. SamSam ransomware attacks are highly targeted and conducted manually without any involvement from end users.
Access is gained to a healthcare network, the attackers move laterally, and the ransomware is manually deployed on as many devices as possible. When multiple devices have been compromised, the encryption routine is triggered on all infected devices simultaneously. This method ensures maximum disruption is caused, and with large numbers of devices taken out of action through file encryption, large ransoms can be demanded – typically of the order of around $50,000.
To gain access to networks the threat actors perform scans to identify organizations with open remote desktop protocol (RDP) connections. RDP backdoors can also be purchased on darknet forums, which may also be used to gain access to healthcare organizations’ networks.
Symantec points out that considerable work goes into each campaign. Once the perimeter has been breached, it can take several days for the threat actors to map the organization’s network and stealthily deploy their ransomware. The threat actors use off-the-shelf administration and pen testing tools – PsExec for instance – to allow them to move through the network without being identified. The Mimikatz hacking tool is also used to obtain passwords to infect further devices.
To reduce risk, healthcare organizations need to take steps to make it harder for the attackers to breach the perimeter, implement cybersecurity solutions to detect network intrusions and identify suspicious activity, and also ensure that backups are regularly made with copies of backed up files stored offline.
Good password policies are important to prevent brute force attacks. Strong unique passwords should be used and all default passwords must be changed. Rate limiting should also be applied to thwart brute force attacks and reports of suspicious login attempts should be automatically generated to alert security teams to a possible attack in progress. Access to public-facing ports should be restricted and multi-factor authentication should be applied on all applications. It is also strongly advisable to severely restrict the use of admin credentials.
The post Healthcare Organizations Account for a Quarter of SamSam Ransomware Attacks appeared first on HIPAA Journal.