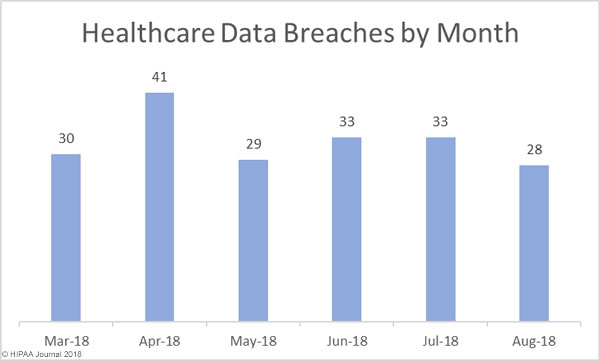
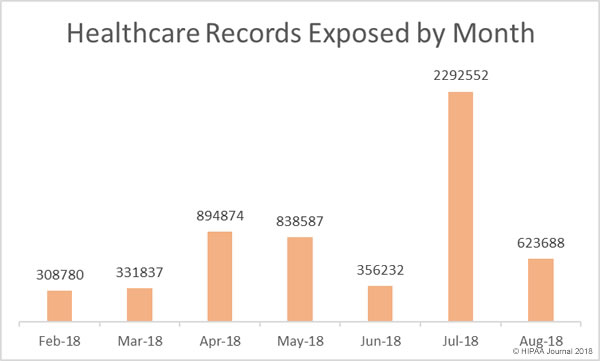
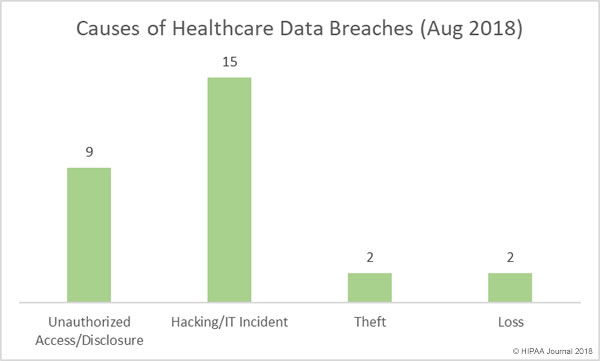
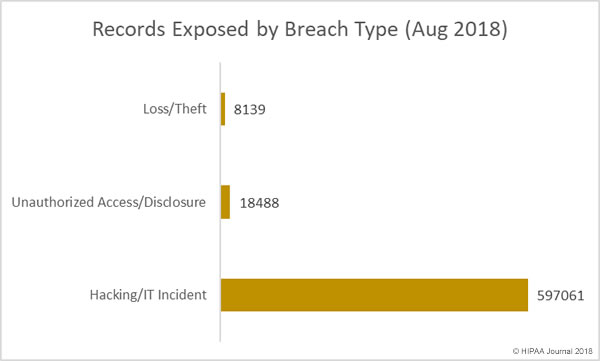
On October 1, 2018, the U.S. Food and Drug Administration released a Medical Device Cybersecurity Regional Incident Preparedness and Response Playbook for healthcare delivery organizations to help them prepare for and respond to medical device cybersecurity incidents.
The playbook is intended to help healthcare delivery organizations develop a preparedness and response framework to ensure they are prepared for medical device security incidents, can detect and analyze security breaches quickly, contain incidents, and rapidly recover from attacks.
The playbook was developed by MITRE Corp., which worked closely with the FDA, healthcare delivery organizations, researchers, state health departments, medical device manufacturers and regional healthcare groups when developing the document.
The past 12 months have seen many vulnerabilities identified in medical devices which could potentially be exploited by hackers to gain access to healthcare networks, patient health information, or to cause harm to patients. While the FDA has not received any reports to suggest an attack has been conducted on medical devices to cause patients harm, the number of cyberattacks on healthcare organizations has increased significantly in recent years and concerns have been raised with the FDA about the potential for cybercriminals to attack patient medical devices.
“The playbook supplements existing HDO emergency management and/or incident response capabilities with regional preparedness and response recommendations for medical device cybersecurity incidents,” said MITRE. “The playbook outlines how hospitals and other HDOs can develop a cybersecurity preparedness and response framework, which starts with conducting device inventory and developing a baseline of medical device cybersecurity information.”
In addition to releasing the guidance for HDOs, the FDA has developed its own internal playbook to ensure that it can respond rapidly to any medical device cybersecurity incident. “Our internal playbook establishes an effective and appropriate incident plan that’s flexible and clear. It aims to help the agency respond in a timely manner to medical device cybersecurity attacks – mitigating impacts to devices, healthcare systems and ultimately, patients,” said Scott Gottlieb, MD, Commissioner of the FDA.
The Playbook includes several recommendations for healthcare delivery organizations, although it may not be possible for all recommendations to be executed by healthcare delivery organizations due to operational constraints. However, the document does serve as a starting point for developing a response plan for medical device security incidents and will include recommendations that could be incorporated into existing disaster recovery plans.
The FDA has also announced it has signed two memoranda of understanding which will establish information sharing analysis organizations (ISAOs) that will be tasked with gathering, analyzing, and distributing important information about new cyber threats to medical device security. Through the sharing of timely information it is hoped that device manufacturers will be able to address security issues more rapidly before they can be exploited.
The FDA is also working closely with the Department of Homeland Security and is holding joint cybersecurity exercises to simulate attacks on medical devices with a view to improving medical device security. The FDA has also made significant updates to its premarket guidance for medical device manufacturers which is expected to be released in the next few weeks.
The Medical Device Cybersecurity Regional Incident Preparedness and Response Playbook can be downloaded from MITRE on this link (PDF – 543.73 KB)
The post FDA Issues Medical Device Cybersecurity Regional Incident Preparedness and Response Playbook appeared first on HIPAA Journal.