For the past 15 years, Verizon has been publishing annual Data Breach Investigation Reports (DBIR), with this year’s report confirming just how bad the past 12 months have been. Verizon described the past 12 months as representing an unprecedented year in cybersecurity history. “From very well-publicized critical infrastructure attacks to massive supply chain breaches, the financially motivated criminals and nefarious nation-state actors have rarely, if ever, come out swinging the way they did over the last 12 months,” explained Verizon.
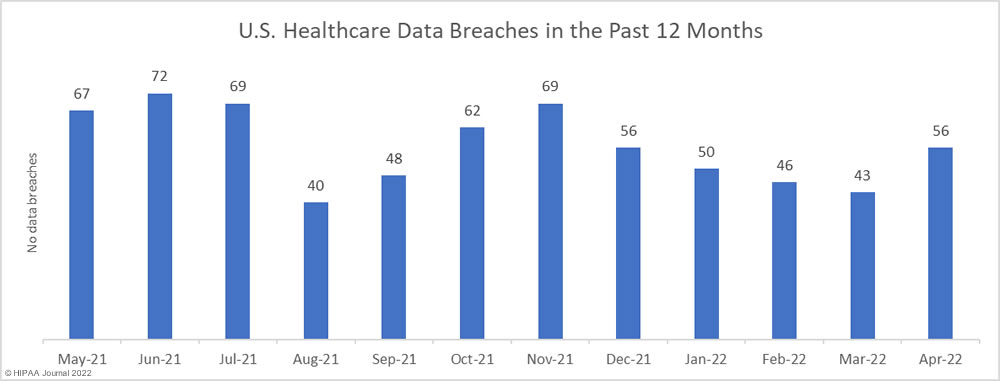
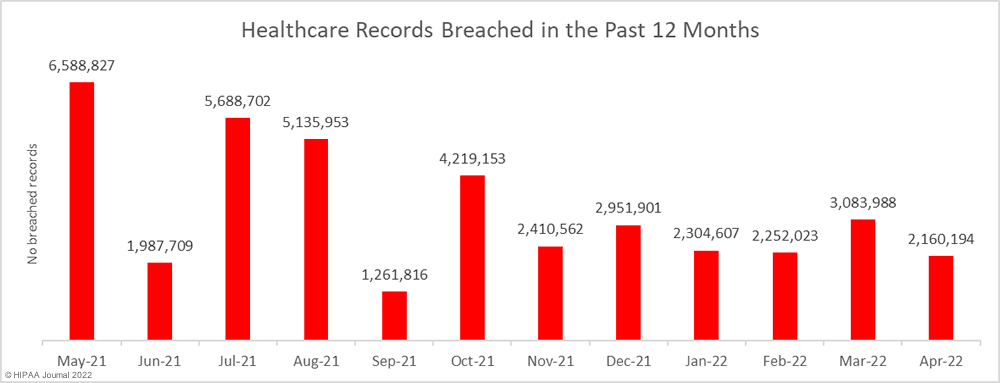
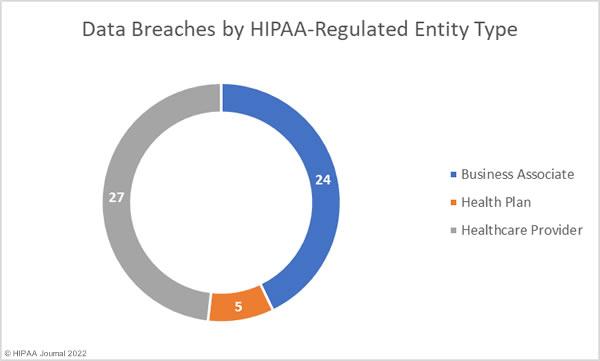
The 2022 DBIR was compiled in conjunction with 87 partner organizations using data from 23,896 security incidents, of which 5,212 were confirmed data breaches, 849 of the security incidents analyzed in the report occurred in the healthcare sector, with 571 of those incidents resulting in confirmed data breaches.
The report confirms there was a major increase in ransomware attacks in 2021, increasing 13% from the previous year. To add some perspective, the increase is greater than the combined increases over the previous five years. As Verizon points out in the report, ransomware is just a way of taking advantage of access to victims’ networks, but it has proven to be particularly successful at monetizing illegal access to networks and private information. Ransomware was involved in 25% of data breaches in 2021.
The most common vectors in ransomware attacks were the use of stolen credentials, mostly for desktop sharing software, which provided initial access in 40% of attacks. Phishing was the second most common vector in attacks, providing initial access in 35% of ransomware attacks followed by the exploitation of vulnerabilities in web applications and direct installs. The high percentage of attacks involving remote desktop software and email highlights the importance of locking down RDP and securing email.
The increase in ransomware attacks is alarming, as is the number of supply chain attacks, which account for 62% of system intrusions. Supply chain attacks may be conducted by financially motivated cyber actors, but oftentimes they are used by nation-state actors to gain persistent access to systems for espionage purposes.
Protecting against cyberattacks requires action to be taken to address the four main avenues that lead to initial access to networks being gained, which are credentials, phishing, exploitation of vulnerabilities, and botnets. While insiders can and do cause data breaches, by far the main cause is external actors. Breaches due to external actors outnumber insider breaches by four to 4. While external attacks are much more likely, the median number of records involved in insider breaches is far higher.
Human error continues to play a large part in data breaches. 13% of breaches involved misconfigurations, mostly of cloud storage facilities, and 82% of all data breaches analyzed in the past 12 months involved a human element. 25% of all breaches in 2021 were the result of social engineering attacks, highlighting not only the importance of implementing advanced email defenses but also providing regular security awareness training to the workforce.
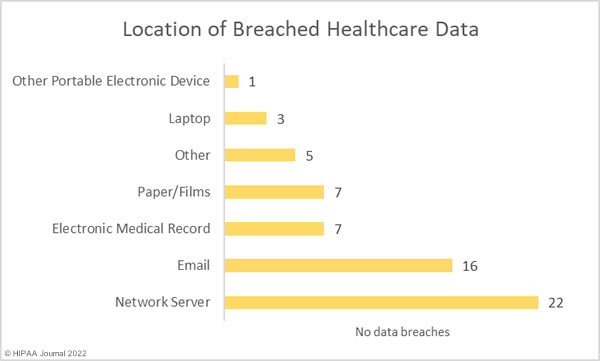
The top three attack methods were the same as last year, albeit changing position. System intrusions took the top spot, followed by web application attacks, and social engineering. In healthcare, the leading causes of data breaches were web application attacks, miscellaneous errors, and system intrusions, which accounted for 76% of all data breaches.
Verizon reports that while insiders have long been a leading cause of data breaches in healthcare, the increase in web application attacks has meant external threats have overtaken insiders. Healthcare employees caused 39% of breaches in 2021, which is considerably higher than the 18% across all other industry sectors. While there will always be malicious insiders in healthcare, employees are 2.5 times more likely to make an error than to maliciously abuse their access to data, with misdelivery and loss the most common errors made in healthcare.
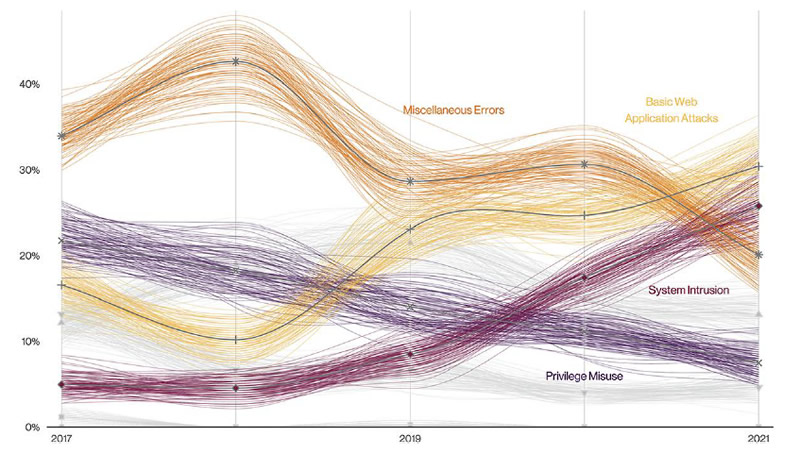
Patterns in Healthcare data breaches. Source: Verizon DBIR 2022
The post Verizon Data Breach Investigations Report Reveals 2021 Data Breach Trends appeared first on HIPAA Journal.