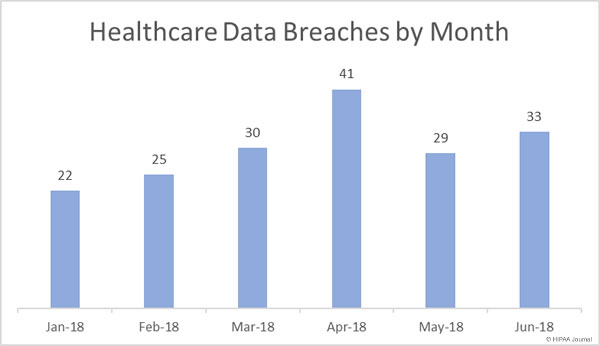
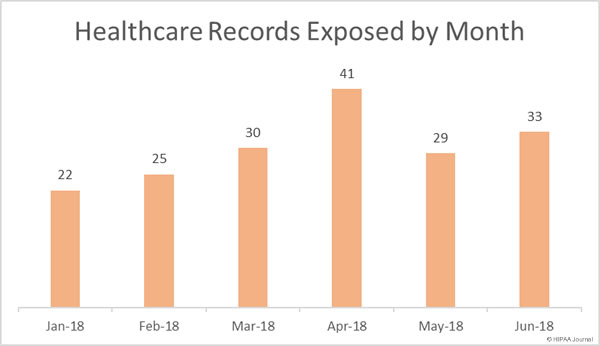
There was a 13.8% month-over-month increase in healthcare data breaches reported in June 2018, although the data breaches were far less severe in June with 42.48% fewer healthcare records exposed or stolen than the previous month.
In June there were 33 healthcare data breaches reported to the Department of Health and Human Services’ Office for Civil Rights and those breaches saw 356,232 healthcare records exposed or stolen – the lowest number of records exposed in healthcare data breaches since March 2018.
Healthcare Data Breaches (January-June 2018)
Healthcare Records Exposed (January-June 2018)
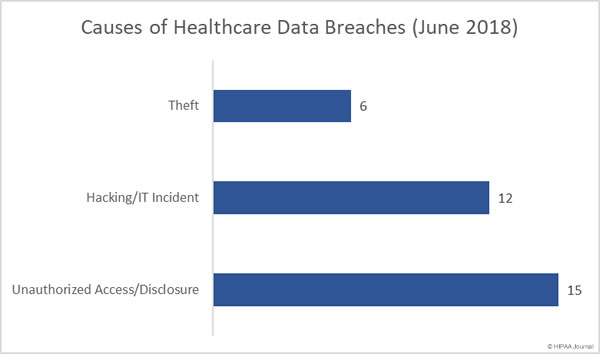
Causes of Healthcare Data Breaches (June 2018)
Unauthorized access/disclosure incidents were the biggest problem area in June, followed by hacking IT incidents. As was the case in May, there were 15 unauthorized access/disclosure breaches and 12 hacking/IT incidents. The remaining six breaches involved the theft of electronic devices (4 incidents) and paper records (2 incidents). There were no reported losses of devices or paperwork and no improper disposal incidents.
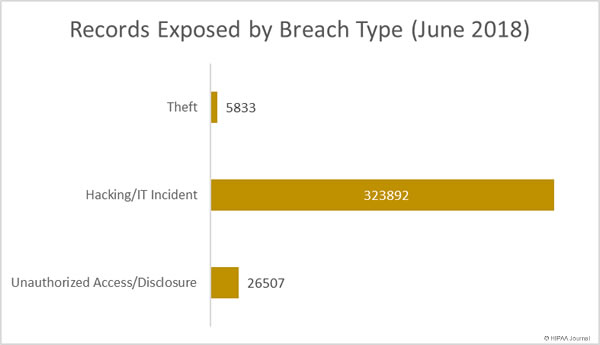
Healthcare Records Exposed by Breach Type
While unauthorized access/disclosure incidents were more numerous than hacking/IT incidents, they resulted in the theft/exposure of far fewer records. Compared to May, 157.5% more records were obtained by unauthorized individuals in theft incidents. There was a 56% fall in the number of healthcare records exposed/stolen in hacking/IT incidents and almost 74% fewer healthcare records exposed or stolen in unauthorized access/disclosure incidents.
Largest Healthcare Data Breaches (June 2018)
Hacking and phishing incidents were behind most (8) of the largest healthcare data breaches reported in June.
The largest breach was reported by the Med Associates, a provider of claims services to healthcare organizations. A computer used by one of the company’s employees was hacked and accessed remotely by an unauthorized individual. The device contained the PHI of 276,057 individuals.
HealthEquity Inc., Black River Medical Center, and InfuSystem Inc., all experienced phishing attacks that resulted in unauthorized individuals gaining access to email accounts containing ePHI. The New England Baptist Health breach involved a patient list that was accidentally emailed to an individual unauthorized to receive the information.
The Arkansas Children’s Hospital breach was a case of snooping by a former employee, and the breach at RISE Wisconsin was a ransomware attack.
| Breached Entity | Entity Type | Records Exposed | Breach Type | Location of PHI |
| Med Associates, Inc. | Business Associate | 276,057 | Hacking/IT Incident | Desktop Computer |
| HealthEquity, Inc. | Business Associate | 16,000 | Hacking/IT Incident | |
| Black River Medical Center | Healthcare Provider | 13,443 | Hacking/IT Incident | |
| New England Baptist Health | Healthcare Provider | 7,582 | Unauthorized Access/Disclosure | |
| Arkansas Children’s Hospital | Healthcare Provider | 4,521 | Unauthorized Access/Disclosure | Electronic Medical Record |
| InfuSystem, Inc. | Healthcare Provider | 3,882 | Hacking/IT Incident | |
| RISE Wisconsin, Inc. | Healthcare Provider | 3,731 | Hacking/IT Incident | Network Server |
| Gwenn S Robinson MD | Healthcare Provider | 2,500 | Hacking/IT Incident | Desktop Computer |
| Capitol Anesthesiology Association | Healthcare Provider | 2,231 | Hacking/IT Incident | Network Server |
| Massac County Surgery Center dba Orthopaedic Institute Surgery Center | Healthcare Provider | 2,000 | Hacking/IT Incident |
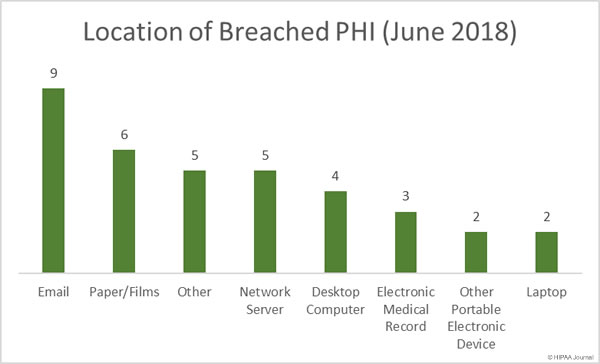
Location of Breached PHI (June 2018)
Email continues to be the most common location of breached PHI. In June, there were 9 email-related breaches reported to OCR. Seven of the nine email-related breaches involved unauthorized individuals accessing the email accounts of healthcare employees as a result of phishing attacks. One email-related breach involved PHI being sent to an individual unauthorized to receive the data and the cause of the other email-related breach has not been confirmed.
The high number of successful phishing attacks on healthcare organizations highlights the importance of ongoing security awareness training for all healthcare employees with email accounts. Once a year training sessions are no longer sufficient. Training programs should be ongoing, with phishing simulation exercises routinely conducted to reinforce training and condition employees to be more security aware. OCR reminded HIPAA-covered entities that security awareness training was a requirement of HIPAA and offered suggestions to increase resilience to phishing attacks in its July 2017 Cybersecurity Newsletter.
Unauthorized accessing and theft of paper records was behind 6 breaches, highlighting the need for physical controls to be implemented to keep physical records secure.
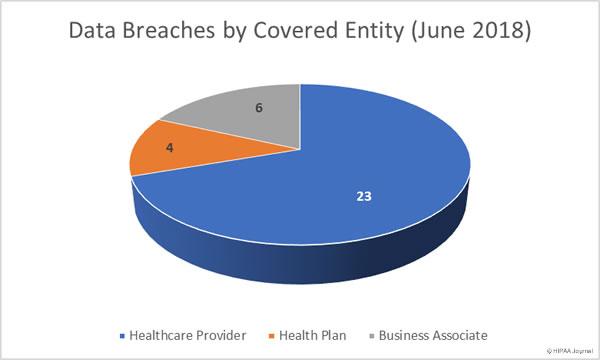
Data Breaches by Covered Entity Type
Healthcare providers experienced the most data breaches in June with 23 data security incidents reported. There was a marked month-over-month increase in health plan data breaches with six incidents reported compared to just two in May. Business associates reported six breaches in June, although in total, 10 incidents had some business associate involvement – on a par with May when 9 breaches involved business associates to some extent.
Data Breaches by State
California was the state worst affected by healthcare data breaches in June 2018, with 5 data breaches reported by healthcare organizations in the state. Texas saw four breaches reported, with three security breaches reported by Michigan-based healthcare organizations and two breaches reported by healthcare organizations in Florida, Missouri, Utah, Wisconsin.
Arkansas, Arizona, Iowa, Illinois, Massachusetts, Minnesota, Montana, North Carolina, New Jersey, New Mexico, New York, Pennsylvania, Washington each had one breach reported.
Penalties for HIPAA Violations Issued in June 2018
OCR penalized one HIPAA-covered entity in June for HIPAA violations – The fourth largest HIPAA violation penalty issued to date.
OCR investigated MD Anderson after three data breaches were reported in 2012 and 2013 – The theft of a laptop computer from the vehicle of a physician and the theft of two unencrypted thumb drives. 34,883 healthcare records were impermissibly disclosed as a result of the breaches.
OCR determined a financial penalty was appropriate for the failure to encrypt ePHI and the resultant impermissible disclosures of patient health information. University of Texas MD Anderson Cancer Center (MD Anderson) contested the penalty, with the case going before and administrative law judge. The ALJ ruled in favor of OCR.
University of Texas MD Anderson Cancer Center was ordered to pay $4,348,000 to resolve the HIPPA violations that led to the breaches.
The post June 2018 Healthcare Breach Report appeared first on HIPAA Journal.