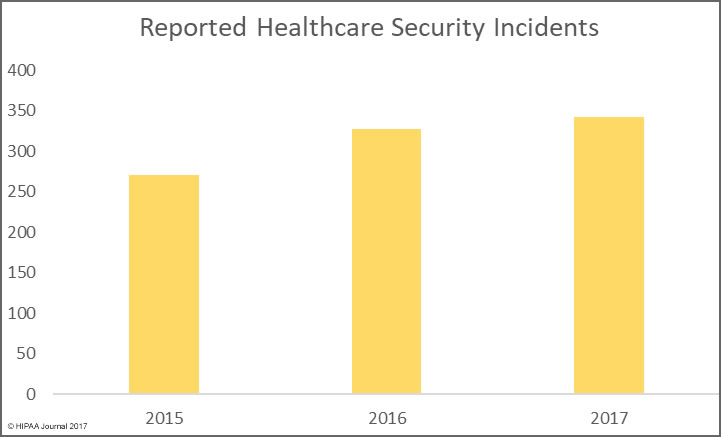
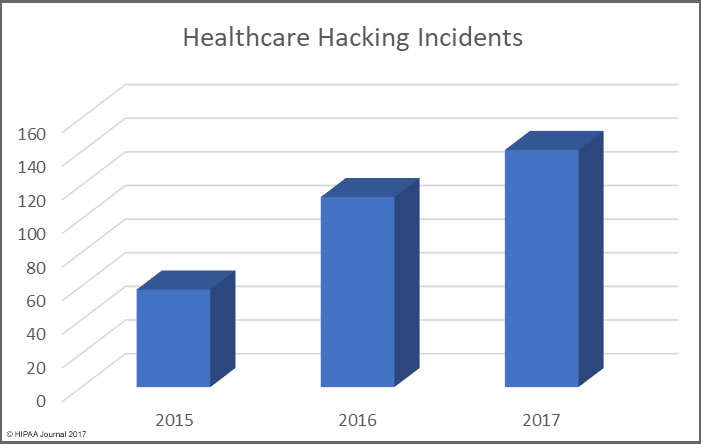
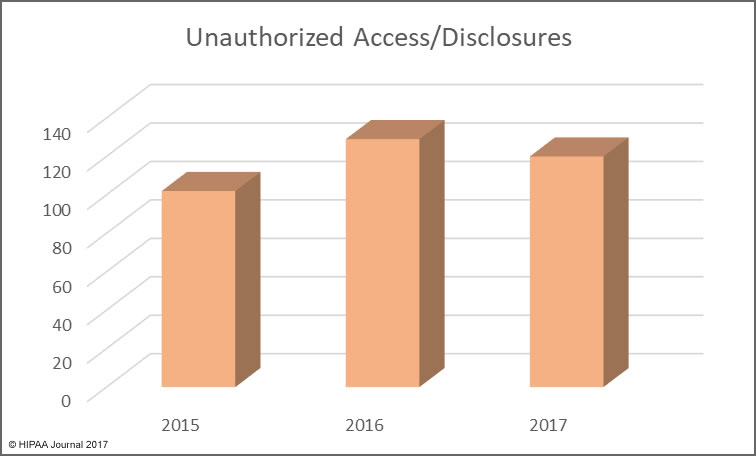
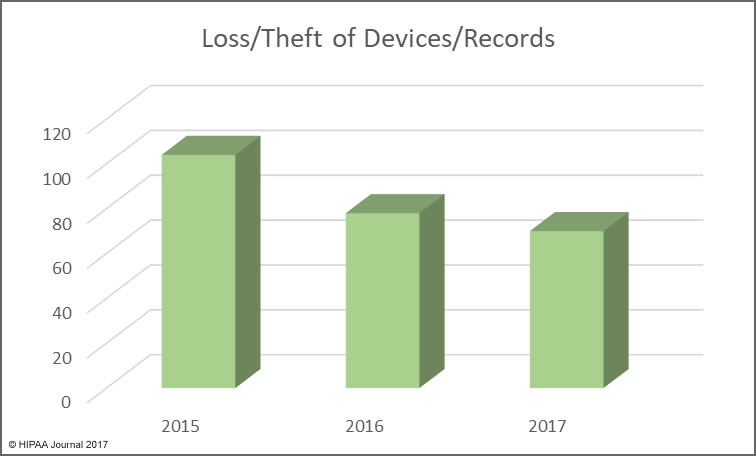
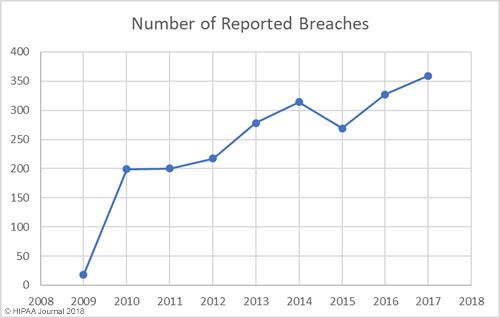
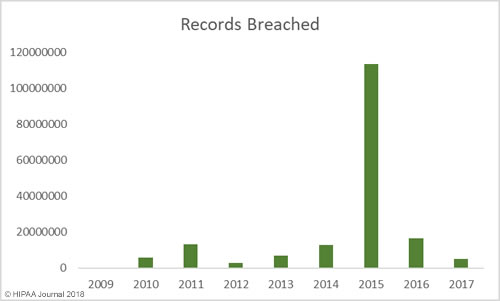
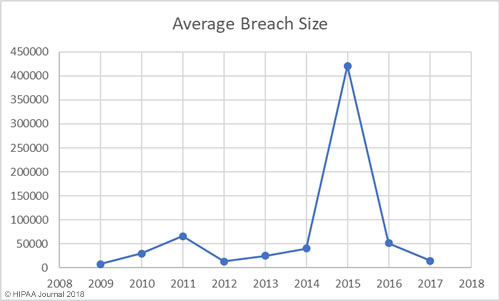
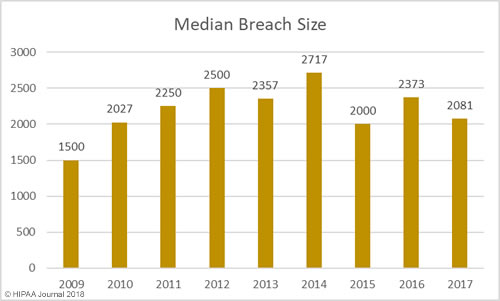
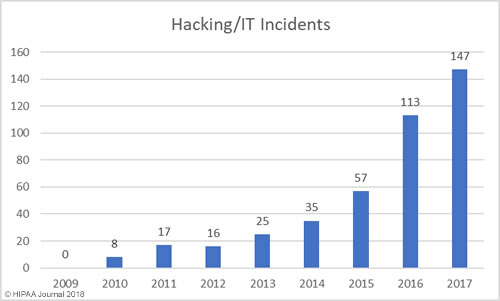
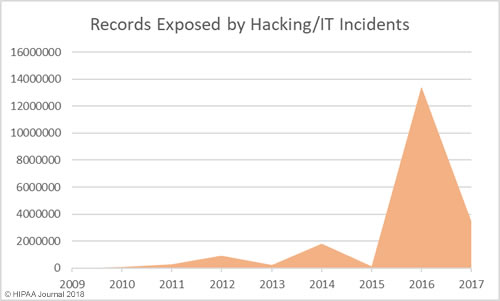
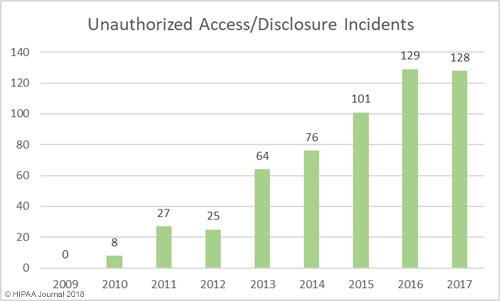
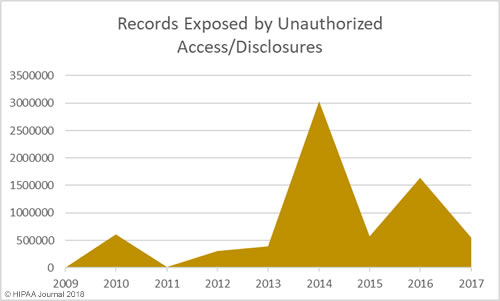
Alabama has become the 50th state to require companies to issue breach notifications to individuals whose personal information has been exposed or compromised as a result of a data breach. Governor Kay Ivey signed the act into law on March 28. The effective date is May 1, 2018.
The data breach notification law has taken a long time to be enacted although Alabama residents will now have some of the best protections in the country, with the law one of the strictest introduced in any state.
While every state now has a data breach notification law that requires notifications to be issued to all individuals impacted by a data breach, only 28% of U.S. states – including Alabama – also require ‘covered entities’ to maintain reasonable security measures to protect the confidentiality of sensitive personally identifying information of state residents. Service providers must also be contractually required to maintain appropriate safeguards.
Sensitive personally identifying information is classed as a state resident’s first name or first initial and last name in combination with any of the following data elements:
- A non-truncated Social Security or tax-identification number
- A non-truncated driver’s license, passport, or other government identification number
- A financial account number combined with security/access code, password, PIN or expiration date necessary to access or enter into a transaction that will “credit or debit the account”
- An individual’s medical history, mental/physical condition, medical treatment/diagnosis by a health care professional, health insurance policy/subscriber number, or other insurance identifier
- user name or email address combined with a password or security question/answer permitting access to an online account affiliated with the covered entity that is reasonably likely to contain or is used to obtain Sensitive personally identifying information.
The Data Breach Notification Act requires at least one employee to be designated to coordinate data security measures. Covered entities must determine ‘reasonable security measures’ by means of a risk assessment covering internal and external threats. Appropriate safeguards must then be implemented to address identified risks and reduce them to a reasonable level. The measures introduced must be reevaluated and adjusted when circumstances change.
When personal information is no longer required, covered entities must take reasonable steps to ensure the information is permanently destroyed.
In the event of a breach of personal information, the covered entity must conduct a “good faith and prompt investigation” to determine the nature and scope of the breach, the types of sensitive personally identifying information involved, the likelihood of the information being acquired by an unauthorized individual, and whether the acquisition of sensitive personally identifying information is likely to cause substantial harm. The covered entity must also ensure measures are introduced to restore the security of its systems after a breach has occurred.
Data breach notifications must be issued to all individuals impacted by the breach “without unreasonable delay” and no later than 45 days after the discovery of a breach of sensitive personally identifying information.
The breach notice must include the date – or estimated date – of the breach, the type of information exposed or stolen, a general description of remedial measures taken by the covered entity in response to the breach, and a list of actions that individuals can take to protect themselves against identity theft and fraud. Contact information must also be suppled to allow individuals to find out more about the breach should they wish to do so.
In addition to personal notifications, the Alabama state attorney general must also be notified of a breach within 45 days if it impacts more than 1,000 individuals.
HIPAA covered entities should note that they are not deemed to be in compliance with the Alabama Data Breach Notification Act by complying with HIPAA Rules.
Any entity that violates the Alabama Data Breach Notification Act will be subject to penalties for an unlawful trade practice under the Alabama Deceptive Trade Practices Act, although a violation would not be classed as a criminal offense. The maximum civil monetary penalty is $5,000 for each day past the 45-day deadline for issuing data breach notifications. The maximum civil monetary penalty for violations of the Act is $500,000.
The post Alabama Governor Enacts Data Breach Notification Act appeared first on HIPAA Journal.