Our February 2018 healthcare data breach report details the major data breaches reported by healthcare providers, health plans, and business associates in February 2018.
Summary of February 2018 Healthcare Data Breaches
February may have been a shorter month, but there was an increase in the number of healthcare data breaches reported to the Department of Health and Human Services’ Office for Civil Rights. In February, HIPAA covered entities and business associates reported 25 breaches – a 19% month on month increase in breaches.
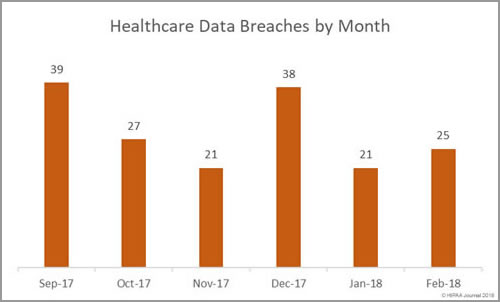
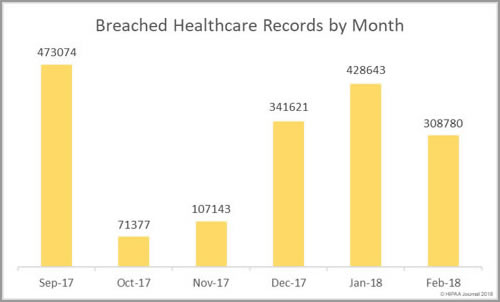
While there was a higher breach tally this month, the number of healthcare records exposed as a result of healthcare data breaches fell by more than 100,000. In January 428,643 healthcare records were exposed. February 2018 healthcare data breaches saw 308,780 healthcare records exposed.
Largest Healthcare Data Breaches of February 2018
The largest healthcare data breaches reported to the Office for Civil Rights in February are listed below.
| Covered Entity | Covered Entity Type | Individuals Affected | Type of Breach | Location of PHI |
| St. Peter’s Surgery & Endoscopy Center | Healthcare Provider | 134,512 | Hacking/IT Incident | Network Server |
| Tufts Associated Health Maintenance Organization, Inc. | Health Plan | 70,320 | Unauthorized Access/Disclosure | Paper/Films |
| Triple-S Advantage, Inc. | Health Plan | 36,305 | Unauthorized Access/Disclosure | Paper/Films |
| CarePlus Health Plan | Health Plan | 11,248 | Unauthorized Access/Disclosure | Paper/Films |
| Union Lake Supermarket, LLC | Healthcare Provider | 9,956 | Improper Disposal | Other Portable Electronic Device |
The top five data breaches were responsible for 85% of all exposed healthcare records in February. The largest data breach – a malware-related incident at St. Peter’s Surgery & Endoscopy Center – accounted for 43.6% of the exposed healthcare records in February.
Main Causes of February 2018 Healthcare Data Breaches
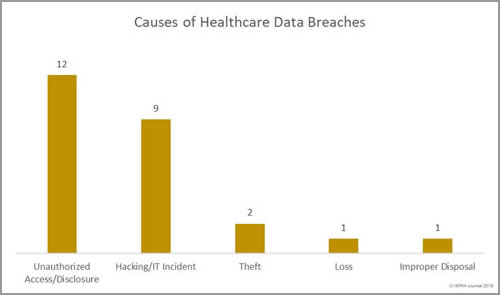
Unauthorized access/disclosures topped the list of the main causes of healthcare data breaches in February 2018 with 12 incidents and included three of the most serious breaches. Hacking incidents were in close second with 9 breaches, followed by three loss/theft incidents and one case of improper disposal of ePHI.
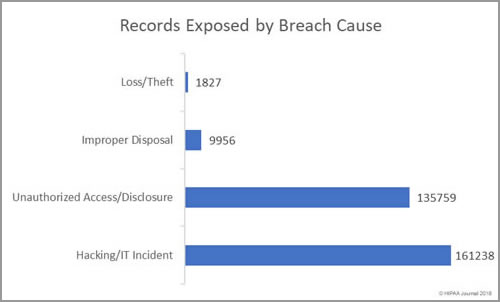
Records Exposed by Breach Type
Hacking/IT incidents were the second biggest cause of healthcare data breaches in February, but the incidents resulted in the exposure/theft of the largest amount of healthcare data.
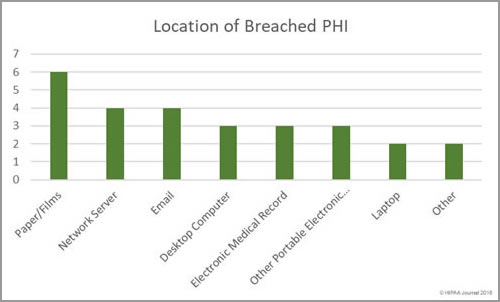
Location of Breached Records
Overall, there were more breaches involving electronic health data than physical records, although breaches involving paper/films were the most numerous with 6 incidents. The breach reports show that while technological controls are essential to prevent hacks and unauthorized access/disclosures of electronic records, physical security is important for paper records and administrative safeguards are necessary to prevent unauthorized access. All six of the breaches involving paper/films were unauthorized access/disclosures.
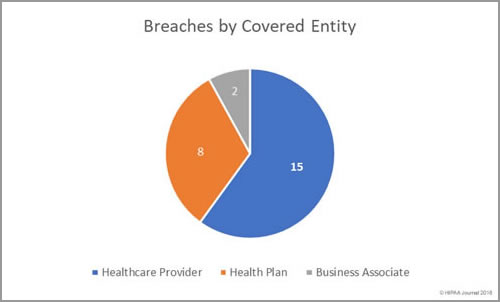
Data Breaches by Covered Entity
Healthcare providers were the worst affected by data breaches in February with 15 incidents (reported by 14 healthcare providers). There were three breaches reported by pharmacies in February. 8 data breaches were reported by 7 health plans and two security incidents were reported by business associates.
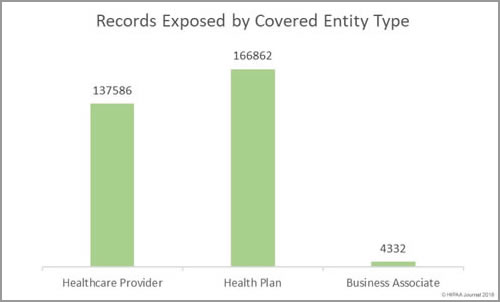
Healthcare provider breaches exposed the most health records in February. 168,732 records were exposed by healthcare providers. The mean breach size was 11,248 records and the median breach size was 1,670 records.
Health plans experienced fewer breaches, but the incidents were more severe. 133,580 records were exposed by health plans. The mean breach size was 16,698 records and the median breach size was 6,075 records. The mean and median breach size for business associate data breaches was 3,234 records.
February 2018 Healthcare Data Breaches by State
Healthcare organizations based in 18 states reported data breaches in February 2018. There were six states that experienced 2 data breaches– Alabama, California, Massachusetts, Mississippi, Rhode Island, and Wisconsin.
Arkansas, Connecticut, Illinois, Kentucky, Maine, Michigan, Missouri, North Carolina, New Jersey, New York, Tennessee, and Virginia each had one data breach reported.
Financial Penalties for HIPAA Covered Entities in February 2018
The Office for Civil Rights settled one HIPAA violation case in February. Filefax Inc, agreed to settle potential HIPAA violations with OCR for $100,000. The financial penalty sent a message to HIPAA-covered entities and their business associates that HIPAA responsibilities do not end when a business ceases trading. The fine relates to HIPAA violations that occurred after the business closed – the improper disposal of paperwork containing protected health information.
The post Analysis of February 2018 Healthcare Data Breaches appeared first on HIPAA Journal.
