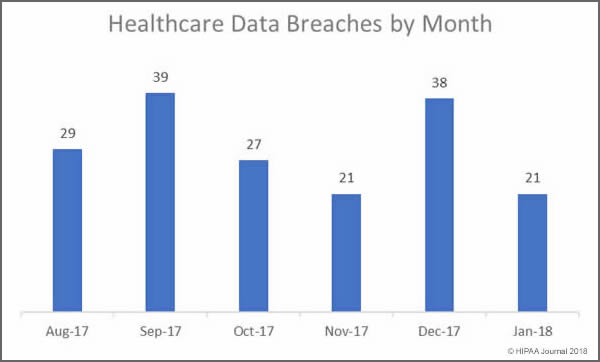
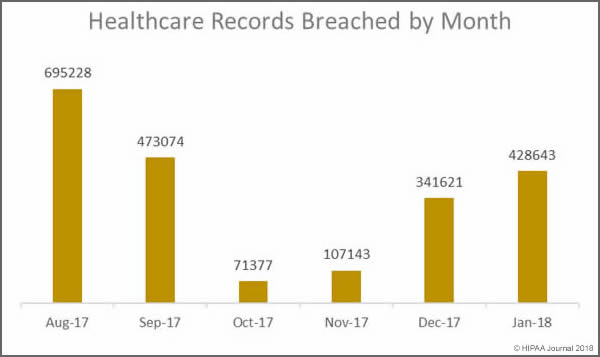
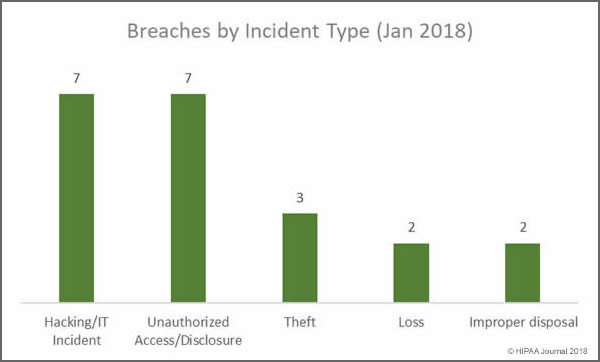
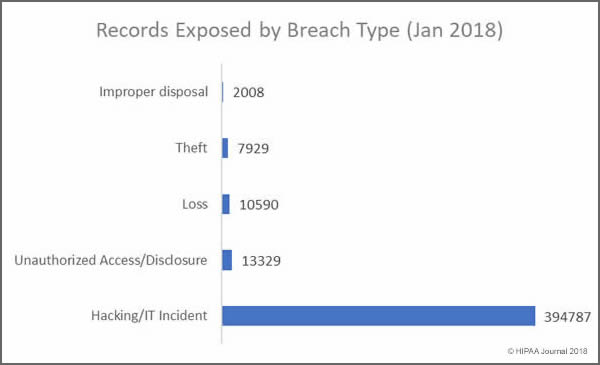
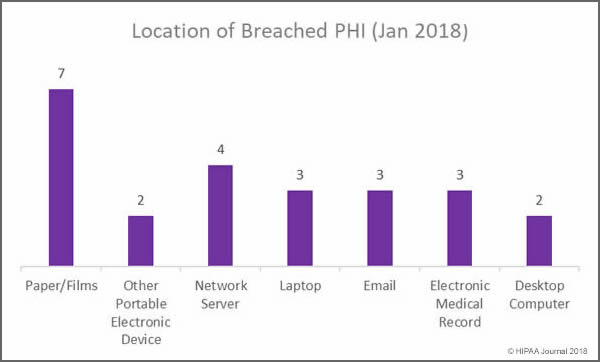
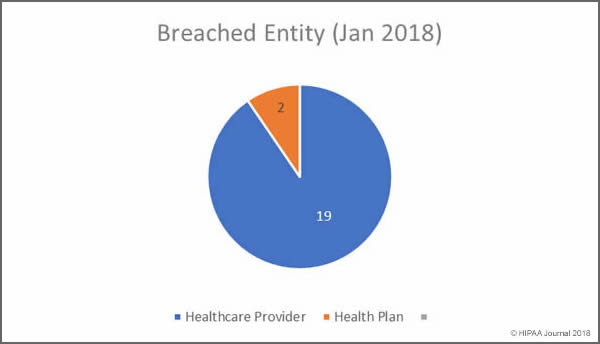
Healthcare organizations can benefit greatly from transitioning to the cloud, but it is essential to understand the requirements for cloud computing to ensure HIPAA compliance.
In this post we explain some important considerations for healthcare organizations looking to take advantage of the cloud, HIPAA compliance considerations when using cloud services for storing, processing, and sharing ePHI, and we will dispel some of the myths about cloud computing and HIPAA compliance.
Myths About Cloud Computing and HIPAA Compliance
There are many common misconceptions about the cloud and HIPAA compliance, which in some cases prevent healthcare organizations from taking full advantage of the cloud, and in others could result in violations of HIPAA Rules.
Some of the common myths about cloud computing and HIPAA compliance are detailed below:
Use of a ‘HIPAA compliant’ cloud service provider will ensure HIPAA Rules are not violated
False: A cloud service provider can incorporate all the necessary safeguards to ensure the service or platform can be used in a HIPAA compliant manner, but it is the responsibility of the covered entity or business associate using the service to ensure that HIPAA Rules are followed. CSPs will not accept liability for misuse of their service/platform or misconfigurations by healthcare employees.
Cloud service providers are classed as conduits and a BAA is not required
False: Cloud services providers are considered business associates (see below) even if they do not – or cannot access stored data. The failure to enter into a business associate agreement prior to using the platform or service in connection with ePHI is a serious violation of HIPAA Rules.
A business associate agreement is required before de-identified PHI can be stored in the cloud
False: There are no HIPAA Privacy Rule restrictions covering the use or storage of de-identified PHI. De-identified PHI is not considered to be protected health information.
Physicians cannot use mobile devices to access ePHI stored in the cloud
False. There is nothing in HIPAA Rules that prevents the use of mobile devices for accessing data stored in the cloud, provided administrative, technical, and physical safeguards are in place to ensure the confidentiality, integrity, and availability of PHI for any data stored in the cloud or downloaded to a mobile device. However, some healthcare organizations may have internal policies prohibiting the use of mobile devices with cloud services.
Cloud service providers must retain PHI for 6 years
False: HIPAA-covered entities must retain PHI for 6 years, but that rule does not apply to cloud service providers. If a HIPAA covered entity stops using a cloud service, all stored data must be returned to the covered entity or should be permanently deleted. If the CPS is required to retain stored data to meet the requirements of other laws, the information must be returned or deleted when that time period has elapsed.
A cloud service provider cannot be used if data is stored outside of the United States
False: A cloud service provider can store data on servers located in any country. There are no geographical restrictions. However, HIPAA covered entities should assess the risks – by means of a risk analysis – before using such a cloud service, as data stored on servers overseas may not be subject to the same level of protection as data stored on U.S-based servers.
Cloud Service Providers and Business Associate Agreements
While cloud service providers have long been known to be HIPAA business associates, the introduction of the HIPAA Omnibus Rule in 2013 made this clearer. “A data storage company that has access to protected health information (whether digital or hard copy) qualifies as a business associate, even if the entity does not view the information or only does so on a random or infrequent basis.”
The HIPAA conduit exception rule does not apply to cloud service providers. Companies are only considered ‘conduits’ if they offer a transmission only communication services when access to communications is only transient in nature. Cloud service providers are not considered to be conduits, even if the service provider encrypts all data and does not hold the keys to unlock the encryption.
Consequently, a business associate agreement must be entered into with the cloud platform or service provider before the platform or service is used for storing, processing, or transmitting ePHI.
If the cloud service is only ever used for sharing or storing de-identified PHI, a BAA is not required. De-identified PHI is no longer PHI, provided all identifiers have been stripped from the data. (See deidentification of PHI for further information.)
Cloud Computing and HIPAA Compliance
Cloud computing and HIPAA compliance are not at odds. It is possible to take advantage of the cloud and even improve security, but there are important considerations for any healthcare organizations considering using cloud services for storing, sharing, processing, or backing up ePHI
Risk Analysis and Risk Management
Prior to the use of any cloud service it should be subjected to a risk assessment. HIPAA-covered entities and their business associates must conduct their own risk analysis and establish risk management policies.
Business Associate Agreements
Before any cloud platform or service is used in connection with ePHI, the service provider and covered entity must enter into a HIPAA-compliant business associate agreement. The use of a cloud service without a BAA in place is a violation of HIPAA Rules.
Service Level Agreements (SLA)
In addition to a BAA, covered entities should consider a service level agreement (SLA) covering more technical aspects of the service, which may or may not address HIPAA concerns. The service level agreement can cover system uptime, reliability, data backups, disaster recovery times, customer service response times, and data return or deletion when the BAA is terminated. The SLA should also include the penalties should performance fall short of what has been agreed.
Encryption
Any data shared via the cloud should be protected by end-to-end encryption, and any data stored in the cloud should be encrypted at rest. Full considerations should be given to the level of encryption used by the CSP, which should meet NIST standards. While encryption is important, it will not satisfy all Security Rule requirements and will not maintain the integrity of ePHI nor ensure its availability.
Access Controls
Covered entities must ensure that access controls are carefully configured to ensure that only authorized individuals are able to access ePHI stored in the cloud. Prior to the use of any cloud platform or service, the administrative and physical controls implemented by the cloud service provider should be carefully evaluated.
Data Storage Locations
Covered entities should determine the locations where data is stored and risks associated with those locations should be evaluated during the risk analysis. Cloud service providers often store data in multiple locations to ensure fast access and rapid data recovery in the event of disaster. Data protection laws in foreign countries may differ considerable from those in the U.S.
Maintaining an Audit Trail
Healthcare organizations must have visibility into how cloud services are used, who is accessing cloud data, failed attempts to view cloud resources, and files that have been shared, uploaded, or downloaded. An audit trail must be maintained and logs should be reviewed regularly.
Cloud Benefits for Healthcare Organizations
Some of the key benefits for healthcare organizations from transitioning to the cloud are detailed below:
- Linking a public cloud with data centers allows healthcare organizations to increase capacity without having to invest in additional hardware
- The cloud is highly scalable – Capacity can be easily increased to meet business demands
- Healthcare organizations can improve security by avoiding transporting ePHI on portable devices such as zip drives, portable hard drives, and laptop computers. The loss and theft of portable devices is a major cause of HIPAA data breaches
- The cloud makes sharing ePHI with partners, patients, and researchers easier and faster
- An unlimited number of data backups can be stored in the cloud. Data can be recovered quickly in the event of disaster
- The cloud can help healthcare organizations decommission legacy infrastructure and improve security
- The cloud allows healthcare organizations to reduce their data center footprints
- Healthcare data can be securely accessed by authorized individuals in any location
- The cloud allows healthcare organizations to offer and improve their telehealth services
- The cloud supports the creation of an edge computing system to reduce latency and speed up data access
Choosing a Cloud Partner
While there are many cloud service providers that are willing to work with healthcare organizations, not all are prepared to accept liability for data breaches or violations of HIPAA Rules. Any CSP that will not sign a BAA should be avoided; however, not all cloud companies offer the same level of protection for stored and transmitted data. Willingness to sign a BAA is no guarantee of the quality of the service.
It is essential for a HIPAA covered entity to carefully assess any cloud service, even if the company claims it supports HIPAA compliance.
HIPAA-Compliant Cloud Platforms and Cloud Services
Over the coming weeks we will be assessing the services of a wide variety of cloud service providers to determine whether their platforms support HIPAA compliance.
For further information on specific vendors and to find out if they offer platforms that support HIPAA compliance, visit the links below:
Cloud Platforms
Cloud-Based Services
- Amazon CloudFront
- Box
- Citrix FileShare
- Dropbox
- E-FileCabinet
- G Suite
- HelloFax
- iCloud
- Microsoft OneDrive
- WebEx
- Zoom
The post What Covered Entities Should Know About Cloud Computing and HIPAA Compliance appeared first on HIPAA Journal.