The first HIPAA settlement of 2018 has been announced by the Department of Health and Human Services’ Office for Civil Rights (OCR). Fresenius Medical Care North America (FMCNA) has agreed to pay OCR $3.5 million to resolve multiple potential HIPAA violations that contributed to five separate data breaches in 2012.
The breaches were experienced at five separate covered entities, each of which was owned by FMCNA. Those breached entities were:
- Bio-Medical Applications of Florida, Inc. d/b/a Fresenius Medical Care Duval Facility in Jacksonville, Florida (FMC Duval)
- Bio-Medical Applications of Alabama, Inc. d/b/a Fresenius Medical Care Magnolia Grove in Semmes, Alabama (FMC Magnolia Grove)
- Renal Dimensions, LLC d/b/a Fresenius Medical Care Ak-Chin in Maricopa, Arizona (FMC Ak-Chin)
- Fresenius Vascular Care Augusta, LLC (FVC Augusta)
- WSKC Dialysis Services, Inc. d/b/a Fresenius Medical Care Blue Island Dialysis (FMC Blue Island)
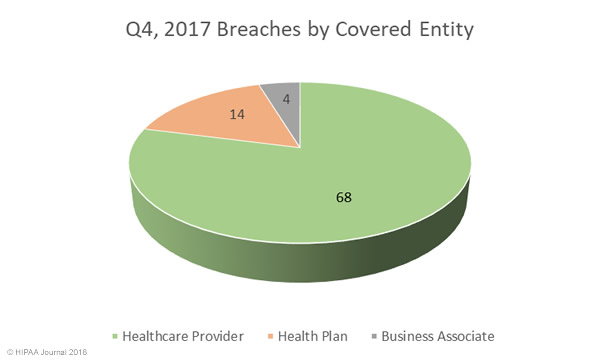
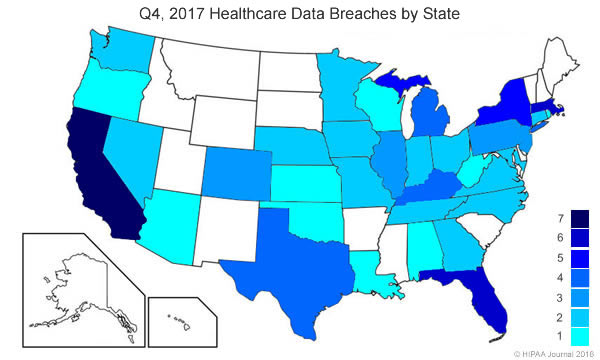
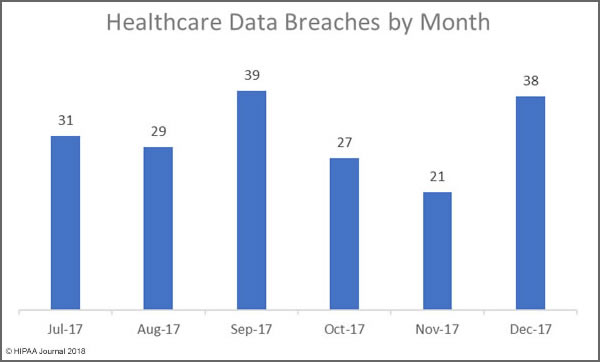
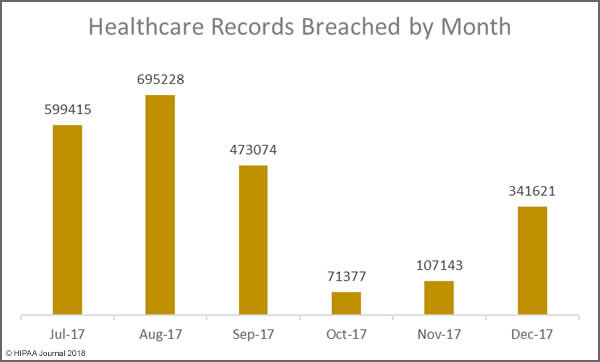
Breaches Experienced by FMCNA HIPAA Covered Entities
The five security breaches were experienced by the FMCNA covered entities over a period of four months between February 23, 2012 and July 18, 2012:
- The theft of two desktop computers from FMC Duval during a February 23, 2012 break-in. The computers contained the ePHI – including Social Security numbers – of 200 individuals
- The theft of an unencrypted USB drive from FMC Magnolia Grove on April 3, 2012. The device contained the PHI – including insurance account numbers – of 245 individuals
- On April 6, 2012 FMC Ak-Chin discovered a hard drive was missing. The hard drive had been removed from a computer that had been taken out of service and the drive could not be located. The hard drive contained the PHI – including Social Security numbers – of 35 individuals
- An unencrypted laptop computer containing the ePHI of 10 patients – including insurance details – was stolen from the vehicle of an employee on June 16, 2012. The laptop had been left in the vehicle overnight. The bag containing the laptop also contained the employee’s list of passwords
- Three desktop computers and one encrypted laptop were stolen from FMC Blue Island on or around June 17-18, 2012. One of the computers contained the PHI – including Social Security numbers – of 35 patients
Multiple HIPAA Failures Identified
OCR launched an investigation into the breaches to establish whether they were the result of failures to comply with HIPAA Rules. The investigation revealed a catalogue of HIPAA failures.
OCR established that the FMCNA covered entities had failed to conduct a comprehensive and accurate risk analysis to identify all potential risks to the confidentiality, integrity, and availability of ePHI: One of the most common areas of non-compliance with HIPAA Rules. If an accurate risk assessment is not performed, risks are likely to be missed and will therefore not be managed and reduced to an acceptable level.
OCR also discovered the FMCNA covered entities had impermissibly disclosed the ePHI of many of its patients by providing access to PHI that is prohibited under the HIPAA Privacy Rule.
Several other potential HIPAA violations were discovered at some of the FMCNA covered entities.
FMC Magnolia Grove did not implement policies and procedures governing the receipt and removal of computer hardware and electronic storage devices containing ePHI from its facility, and neither the movement of those devices within its facility.
FMC Magnolia Grove and FVC Augusta had not implemented encryption, or an equivalent, alternative control in its place, when such a measure was reasonable and appropriate given the risk of exposure of ePHI.
FMC Duval and FMC Blue were discovered not to have sufficiently safeguarded their facilities and computers, which could potentially lead to unauthorized access, tampering, or theft of equipment.
FMC Ak-Chin had no policies and procedures in place to address security breaches.
Financial Penalty Reflects the Seriousness and Extent of HIPAA Violations
The $3.5 million settlement is one of the largest issued to date by OCR to resolve violations of HIPAA Rules. In addition to paying the sizeable financial penalty, FMCNA has agreed to adopt a robust corrective actin plan to address all HIPAA failures and bring its policies and procedures up to the standard demanded by HIPAA.
The FMCNA covered entities must conduct comprehensive, organization wide risk analyses to identify all risks to the confidentiality, integrity, and availability of PHI and develop a risk management plan to address all identified risks and reduce them to a reasonable and acceptable level.
Policies and procedures must also be developed and implemented covering device, media, and access controls and all staff must receive training on current and new HIPAA policies and procedures.
“The number of breaches, involving a variety of locations and vulnerabilities, highlights why there is no substitute for an enterprise-wide risk analysis for a covered entity,” said OCR Director Roger Severino. “Covered entities must take a thorough look at their internal policies and procedures to ensure they are protecting their patients’ health information in accordance with the law.”
Settlement Shows it is Not the Size of the Breach that Matters
All of the five breaches resulted in the exposure of relatively few patients’ PHI. No breach involved more than 235 records, and three of the breaches exposed fewer than 50 records.
The settlement shows that while the scale of the breach is considered when deciding on an appropriate financial penalty, it is the severity and the extent of non-compliance that is likely to see financial penalties pursued.
The settlement also clearly shows that OCR does investigate smaller breaches and will do so when breaches suggest HIPAA Rules have been violated.
The post $3.5 Million Settlement to Resolve HIPAA Violations That Contributed to Five Data Breaches appeared first on HIPAA Journal.