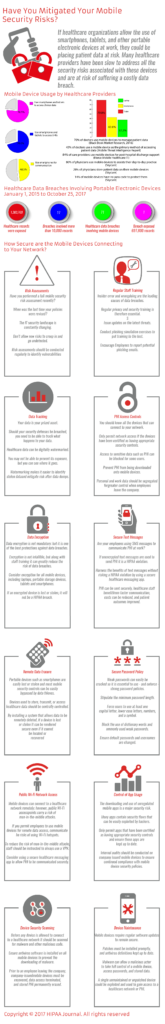
An essential part of HIPAA compliance is reducing mobile device security risks to a reasonable and acceptable level.
As healthcare organizations turn to mobiles devices such as laptop computers, mobile phones, and tablets to improve efficiency and productivity, many are introducing risks that could all too easily result in a data breach and the exposure of protected health information (PHI).
As the breach reports submitted to the HHS’ Office for Civil Rights show, mobile devices are commonly involved in data breaches. Between January 2015 and the end of October 2017, 71 breaches have been reported to OCR that have involved mobile devices such as laptops, smartphones, tablets, and portable storage devices. Those breaches have resulted in the exposure of 1,303,760 patients and plan member records.
17 of those breaches have resulted in the exposure of more than 10,000 records, with the largest breach exposing 697,800 records. The majority of those breaches could have easily been avoided.
The Health Insurance Portability and Accountability Act (HIPAA) Security Rule does not demand encryption for mobile devices, yet such a security measure could have prevented a high percentage of the 71 data breaches reported to OCR.
When a mobile device containing ePHI is lost or stolen, the HIPAA Breach Notification Rule requires the breach to be reported and notifications to be sent to affected individuals. If PHI has been encrypted and a device containing ePHI is lost or stolen, notifications need not be sent as it would not be a HIPAA data breach. A breach report and patient notifications are only required for breaches of unencrypted PHI, unless the key to decrypt data is also obtained.
Even though HIPAA does not demand the use of encryption, it must be considered. If the decision is taken not to encrypt data, the decision must be documented and an alternative safeguard – or safeguards – must be employed to ensure the confidentiality, integrity, and availability of ePHI. That alternative safeguard(s) must provide a level of protection equivalent to encryption.
Before the decision about whether or not to encrypt data can be made, HIPAA covered entities must conduct an organization-wide risk analysis, which must include all mobile devices. All risks associated with the use of mobile devices must be assessed and mitigated – see 45 C.F.R. § 164.308(a)(1)(ii)(A)–(B).
OCR Reminds Covered Entities of Need to Address Risks Associated with Mobile Devices
In its October 2017 Cybersecurity Newsletter, OCR reminded covered entities of the risks associated with mobile devices that are used to create, receive, maintain, or transmit ePHI. HIPAA covered entities were reminded of the need to conduct an organization-wide risk assessment and develop a risk management plan to address all mobile device security risks identified during the risk analysis and reduce them to an appropriate and acceptable level.
While many covered entities allow the use of mobile devices, some prohibit the use of those devices to create, receive, maintain, or transmit ePHI. OCR reminds covered entities that if such a policy exists, it must be communicated to all staff and the policy must be enforced.
When mobile devices can be used to create, receive, maintain, or transmit ePHI, appropriate safeguards must be implemented to reduce risks to an appropriate and acceptable level. While loss or theft of mobile devices is an obvious risk, OCR draws attention to other risks associated with the devices, such as using them to access or send ePHI over unsecured Wi-Fi networks, viewing ePHI stored in the cloud, or accessing or sharing ePHI via file sharing services.
OCR also remined covered entities to ensure default settings on the devices are changed and how healthcare employees must be informed of mobile device security risks, taught best practices, and the correct way to uses the device to access, store, and transmit ePHI.
OCR offers the following advice to covered entities address mobile security risks and keep ePHI secure at all times.
To access OCR’s guidance – Click here.
OCR’s Tips for Reducing Mobile Device Security Risks
- Implement policies and procedures regarding the use of mobile devices in the work place – especially when used to create, receive, maintain, or transmit ePHI.
- Consider using Mobile Device Management (MDM) software to manage and secure mobile devices.
- Install or enable automatic lock/logoff functionality.
- Require authentication to use or unlock mobile devices.
- Regularly install security patches and updates.
- Install or enable encryption, anti-virus/anti-malware software, and remote wipe capabilities.
- Use a privacy screen to prevent people close by from reading information on your screen.
- Use only secure Wi-Fi connections.
- Use a secure Virtual Private Network (VPN).
- Reduce risks posed by third-party apps by prohibiting the downloading of third-party apps, using whitelisting to allow installation of only approved apps, securely separating ePHI from apps, and verifying that apps only have the minimum necessary permissions required.
- Securely delete all PHI stored on a mobile device before discarding or reusing the mobile device.
- Include training on how to securely use mobile devices in workforce training programs.
Penalties for Failing to Address Mobile Security Risks
The failure to address mobile device security risks could result in a data breach and a penalty for noncompliance with HIPAA Rules. Over the past few years there have been several settlements reached between OCR and HIPAA covered entities for the failure to address mobile device security risks.
These include:
| Covered Entity | HIPAA Violation | Individuals Impacted | Penalty |
| Children’s Medical Center of Dallas | Theft of unencrypted devices | 6,262 | $3.2 million |
| Oregon Health & Science University | Loss of unencrypted laptop / Storage on cloud server without BAA | 4,361 | $2,700,000 |
| Cardionet | Theft of an unencrypted laptop computer | 1,391 | $2.5 million |
| Catholic Health Care Services of the Archdiocese of Philadelphia | Theft of mobile device | 412 | $650,000 |
Addressing Mobile Device Security Risks
Mobile device security risks must be reduced to a reasonable and appropriate level. Some of the mobile device security risks, together with mitigations, have been summarized in the infographic below. (Click image to enlarge)
The post Tips for Reducing Mobile Device Security Risks appeared first on HIPAA Journal.