This article details the largest healthcare data breaches of 2017 and compares this year’s breach tally to the past two years, which were both record-breaking years for healthcare data breaches.
2015 was a particularly bad year for the healthcare industry, with some of the largest healthcare data breaches ever discovered. There was the massive data breach at Anthem Inc., the likes of which had never been seen before. 78.8 million healthcare records were compromised in that single cyberattack, and there were also two other healthcare data breaches involving 10 million or more records. 2015 was the worst ever year in terms of the number of healthcare records exposed or stolen.
2016 was a better year for the healthcare industry in terms of the number of healthcare records exposed in data breaches. There was no repeat of the mega data breaches of the previous year. Yet, the number of incidents increased significantly. 2016 was the worst ever year in terms of the number of breaches reported by HIPAA-covered entities and their business associates. So how have healthcare organizations fared in 2017? Was 2017 another record-breaking year?
Healthcare Data Breaches Increased in 2017
The mega data breaches of 2015 were fortunately not repeated in 2017, and the decline in massive data breaches continued in 2017.
Last year, there were three breaches reported that impacted more than one million individuals and 14 breaches of more than 100,000 records.
In 2017, there was only one reported data breach that impacted more than 500,000 people and 8 breaches that impacted 100,000 or more individuals. The final total for individuals impacted by breaches last year was 14,679,461 – considerably less than the 112,107,579 total the previous year.
The final figures for 2017 cannot yet be calculated as there is still time for breaches to be reported to OCR. The HIPAA Breach Notification Rules allows covered entities up to 60 days to report data breaches of more than 500 records, so the final figures for 2017 will not be known until March 1, 2018. However, based on current data, 2017 has been a reasonably good year in terms of the number of exposed healthcare records. The current total stands at 3,286,498 records – A 347% reduction in breached records year on year.
While it is certainly good news that the severity of breaches has reduced, that only tells part of the story. Breaches of hundreds of thousands of records have reduced, but breaches of more than 10,000 records have remained fairly constant year over year. In 2015, there were 52 breaches of 10,000 or more records. That figure jumped to 82 in 2016. There were 78 healthcare data breaches in 2017 involving more than 10,000 records.
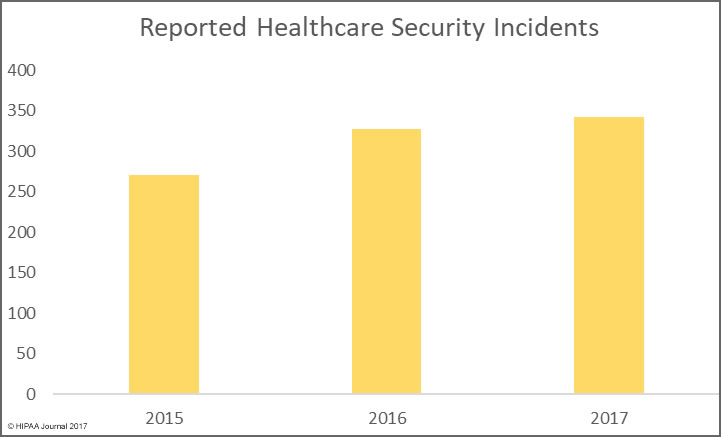
The bad news is there has been a significant rise in the number of healthcare data breaches in 2017. As of January 4, 2017, there have been 342 healthcare security breaches listed on the OCR breach portal for 2017. It is likely more incidents will be added in the next few days.
The final total for 2015 was 270 breaches, and there were 327 breaches reported in 2016. The severity of healthcare security incidents may have fallen, but the number of incidents continues to rise year on year.
Unfortunately, there is little evidence to suggest that the annual rise in healthcare data breaches will stop in 2018. Many cybersecurity firms have made predictions for the coming year, and they are united in the view that healthcare data breaches will continue to increase.
The 20 Largest Healthcare Breaches of 2017
The list of the 20 largest healthcare data breaches of 2017 is listed below.
| Position |
Breached Entity |
Entity Type |
Records Exposed |
Cause of Breach |
| 1 |
Commonwealth Health Corporation |
Healthcare Provider |
697,800 |
Theft |
| 2 |
Airway Oxygen, Inc. |
Healthcare Provider |
500,000 |
Hacking/IT Incident |
| 3 |
Women’s Health Care Group of PA, LLC |
Healthcare Provider |
300,000 |
Hacking/IT Incident |
| 4 |
Urology Austin, PLLC |
Healthcare Provider |
279,663 |
Hacking/IT Incident |
| 5 |
Pacific Alliance Medical Center |
Healthcare Provider |
266,123 |
Hacking/IT Incident |
| 6 |
Peachtree Neurological Clinic, P.C. |
Healthcare Provider |
176,295 |
Hacking/IT Incident |
| 7 |
Arkansas Oral & Facial Surgery Center |
Healthcare Provider |
128,000 |
Hacking/IT Incident |
| 8 |
McLaren Medical Group, Mid-Michigan Physicians Imaging Center |
Healthcare Provider |
106,008 |
Hacking/IT Incident |
| 9 |
Harrisburg Gastroenterology Ltd |
Healthcare Provider |
93,323 |
Hacking/IT Incident |
| 10 |
VisionQuest Eyecare |
Healthcare Provider |
85,995 |
Hacking/IT Incident |
| 11 |
Washington University School of Medicine |
Healthcare Provider |
80,270 |
Hacking/IT Incident |
| 12 |
Emory Healthcare |
Healthcare Provider |
79,930 |
Hacking/IT Incident |
| 13 |
Salina Family Healthcare Center |
Healthcare Provider |
77,337 |
Hacking/IT Incident |
| 14 |
Stephenville Medical & Surgical Clinic |
Healthcare Provider |
75,000 |
Unauthorized Access/Disclosure |
| 15 |
Morehead Memorial Hospital |
Healthcare Provider |
66,000 |
Hacking/IT Incident |
| 16 |
Primary Care Specialists, Inc. |
Healthcare Provider |
65,000 |
Hacking/IT Incident |
| 17 |
Enterprise Services LLC |
Business Associate |
56,075 |
Unauthorized Access/Disclosure |
| 18 |
ABCD Pediatrics, P.A. |
Healthcare Provider |
55,447 |
Hacking/IT Incident |
| 19 |
Network Health |
Health Plan |
51,232 |
Hacking/IT Incident |
| 20 |
Oklahoma Department of Human Services |
Health Plan |
47,000 |
Hacking/IT Incident |
The Largest Healthcare Data Breaches of 2017 Were Due to Hacking
One thing is abundantly clear from the list of the largest healthcare data breaches of 2017 is hacking/IT incidents affect more individuals than any other breach type. Hacking/IT incidents accounted for all but three of the largest healthcare data breaches of 2017.
In 2016, hacking incidents only accounted for 11 out of the top 20 data breaches and 12 of the top 20 in 2015. Hacking incidents therefore appear to be rising.
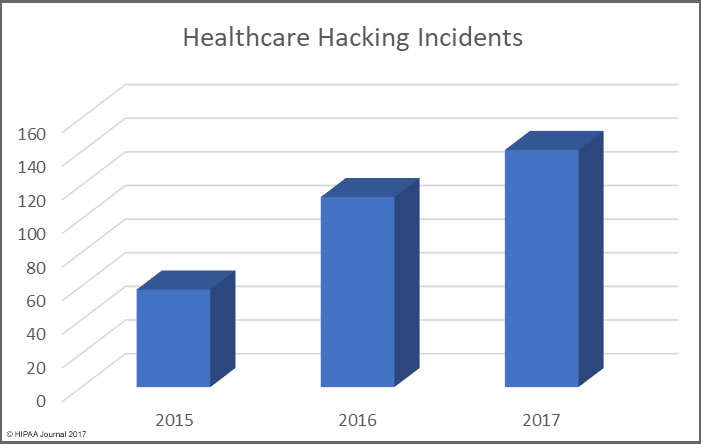
The rise in hacking incidents can partly be explained by the increase in ransomware attacks on healthcare providers in 2017. Healthcare organizations are also getting better at discovering breaches.
Other Major Causes of Healthcare Data Breaches in 2017
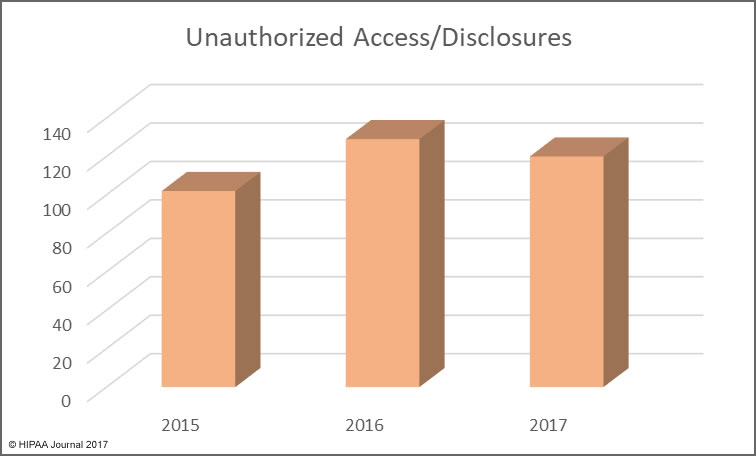
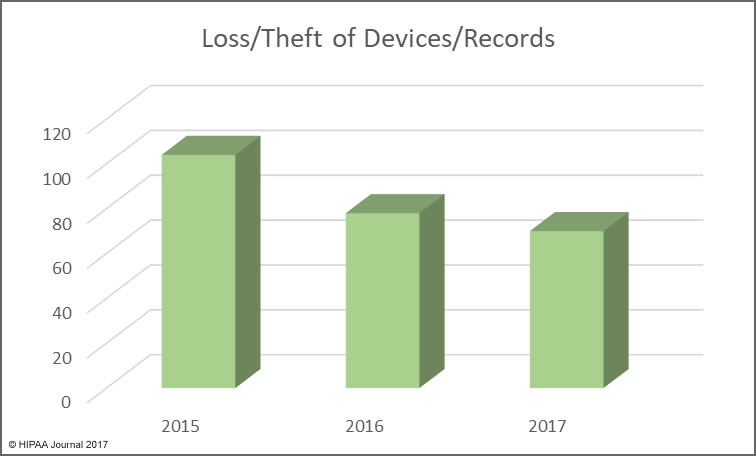
Unauthorized access/disclosures continue to be a leading cause of healthcare data breaches, although there was a slight fall in numbers of these incidents in 2017. That decrease is offset by an increase in incidents involving the improper disposal of physical records and electronic devices used to store ePHI.
The use of encryption for stored data is more widespread, with many healthcare organizations having implemented encryption on all portable storage devices and laptops, which has helped to reduce the exposure of ePHI when electronic devices are stolen.
Minimizing the Risk of Healthcare Data Breaches
This year saw OCR publish the preliminary findings of its HIPAA compliance audits on HIPAA-covered entities. The audits revealed there is still widespread non-compliance with HIPAA Rules.
One of the biggest problems was not a lack of cybersecurity defenses, but the failure to conduct an enterprise-wide risk analysis.
Even with several layers of security, vulnerabilities are still likely to exist. Unless a comprehensive risk analysis is performed to identify security gaps, and those gaps are addressed, it will only be a matter of time before they are exploited.
Complying with HIPAA Rules will not prevent all data breaches, but it will ensure healthcare organizations achieve at least the minimum standard for data security, which will prevent the majority of healthcare data breaches.
There is a tendency to invest cybersecurity budgets in new technology, but it is important not to forget the basics. Many healthcare data breaches in 2017 could have been prevented had patches been applied promptly, if secure passwords had been chosen, and if cloud storage services and databases had been configured correctly. Many data breaches were caused as a result of employees leaving unencrypted laptops in risky locations – in unattended vehicles for instance.
Phishing remains one of the main ways that malicious actors gain access to protected health information, yet security awareness training is still not being provided frequently. As a result, employees are continuing to fall for phishing and social engineering scams. Technological solutions to block phishing emails are important, but healthcare organizations must also educate employees about the risks, teach them how to recognize scams, and reinforce training regularly. Only then will organizations be able to reduce the risk from phishing to an acceptable and appropriate level.
Insiders continue to be a major threat in healthcare. The value of data on the black market is high, and cash-strapped healthcare employees can be tempted to steal data to sell to identity thieves. Healthcare organizations can hammer the message home that data theft will be discovered and reported to law enforcement, but it is the responsibility of healthcare organizations to ensure policies and technologies are implemented to ensure that the unauthorized accessing of records – theft or snooping – is identified rapidly. That means frequent audits of access logs and the use of automated monitoring solutions and user behavior analytics.
2017 was a bad year for ransomware attacks and extortion attempts on healthcare organizations. There is no sign that these attacks will slow in 2018, and if anything, they are likely to increase. Ensuring data is backed up will allow organizations to recover files in the event of an attack without having to pay a ransom. The rise in sabotage attacks – NotPetya for example – mean data loss is a real possibility if backups are not created.
By getting the basics right and investing in new technologies, it will be possible for the year on year rise in data breaches to be stopped. But until healthcare organizations get the basics right and comply with HIPAA Rules, healthcare data breaches are likely to continue to rise.
The post Largest Healthcare Data Breaches of 2017 appeared first on HIPAA Journal.



