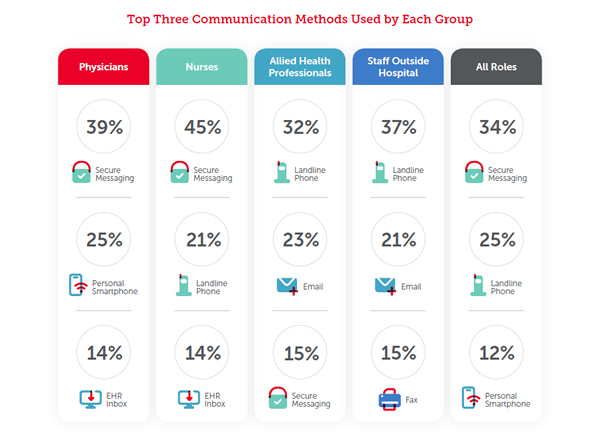
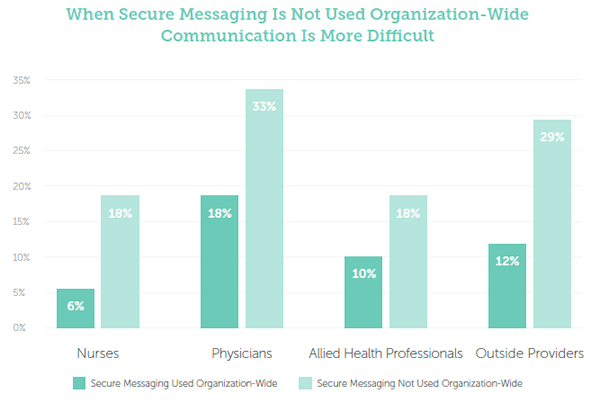
Cyberattacks on healthcare organizations have increased in frequency and severity in the past year, according to recently published research from Malwarebytes.
In its latest report – Cybercrime Tactics and Techniques: The 2019 State of Healthcare – Malwarebytes offers insights into the main threats that have plagued the healthcare industry over the past year and explains how hackers are penetrating the defenses of healthcare organizations to gain access to sensitive healthcare data.
Cyberattacks on healthcare organizations can have severe consequences. As we have seen on several occasions this year, attacks can cause severe disruption to day to day operations at hospitals often resulting in delays in healthcare provision. In at least two cases, cyberattacks have resulted in healthcare organizations permanently closing their doors and a recent study has shown that cyberattacks contribute to an increase in heart attack mortality rates. Even though the attacks can cause considerable harm to patients, attacks are increasing in frequency and severity.
Malwarebytes data shows the healthcare industry was the seventh most targeted industry sector from October 2018 to September 2019, but if the current attack trends continue, it is likely to be placed even higher next year.
Healthcare organizations are an attractive target for cybercriminals as they store a large volume of valuable data in EHRs which is combined, in many cases, with the lack of a sophisticated security model. Healthcare organizations also have a large attack surface to defend, with large numbers of endpoints and other vulnerable networked devices. Given the relatively poor defenses and high value of healthcare data on the black market it is no surprise that the industry is so heavily targeted.
Detection of threats on healthcare endpoints were up 45% in Q3, 2019, increasing from 14,000 detections in Q2 to 20,000 in Q3. Threat detections are also up 60% in the first three quarters of 2019 compared to all of 2018.
Many of the detections in 2019 were Trojans, notably Emotet in early 2019 followed by TrickBot in Q3. TrickBot is currently the biggest malware threat in the healthcare industry. Overall, Trojan detections were up 82% in Q3 from Q2, 2019. These Trojans give attackers access to sensitive data but also download secondary malware payloads such as Ryuk ransomware. Once data has been stolen, ransomware is often deployed.
Trojan attacks tend to be concentrated on industry sectors with large numbers of endpoints and less sophisticated security models, such as education, the government, and healthcare. Trojans are primarily spread through phishing and social engineering attacks, exploits of vulnerabilities on unpatched systems, and as a result of system misconfigurations. Trojans are by far the biggest threat, but there have also been increases in detections of hijackers, which are up 98% in Q3, riskware detections increased by 85%, adware detections were up 34%, and ransomware detections increased by 15%.
Malwarebytes identified three key attack vectors that have been exploited in the majority of attacks on the healthcare industry in the past year: Phishing, negligence, and third-party supplier vulnerabilities.
Due to the high volume of email communications between healthcare organizations, doctors, and other healthcare staff, email is one of the main attack vectors and phishing attacks are rife. Email accounts also contain a considerable amount of sensitive data, all of which can be accessed following a response to a phishing email. These attacks are easy to perform as they require no code or hacking skills. Preventing phishing attacks is one of the key challenges faced by healthcare organizations.
The continued use of legacy systems, that are often unsupported, is also making attacks far too easy. Unfortunately, upgrading those systems is difficult and expensive and some machines and devices cannot be upgraded. The problem is likely to get worse with support for Windows 7 coming to an end in January 2020. The sow rate of patching is why Malwarebytes is still detecting WannaCry ransomware infections in the healthcare industry. Many organizations have still not patched the SMB vulnerability that WannaCry exploits, even though a patch was released in March 2017.
Negligence is also a key problem, often caused by the failure to prioritize cybersecurity at all levels of the organization and provide appropriate cybersecurity training to employees. Malwarebytes notes that investment in cybersecurity is increasing, but it often doesn’t extend to brining in new IT staff and providing security awareness training.
As long as unsupported legacy systems remain unpatched and IT departments lack the appropriate resources to address vulnerabilities and provide end user cybersecurity training, cyberattacks will continue and the healthcare industry will continue to experience high numbers of data breaches.
The situation could also get a lot worse before it gets better. Malwarebytes warns that new innovations such as cloud-based biometrics, genetic research, advances in prosthetics, and a proliferation in the use of IoT devices for collecting healthcare information will broaden the attack surface even further. That will make it even harder for healthcare organizations to prevent cyberattacks. It is essential for these new technologies to have security baked into the design and implementation or vulnerabilities will be found and exploited.
The post Healthcare Threat Detections Up 45% in Q3 and 60% Higher Than 2018 appeared first on HIPAA Journal.